Abstract
Proof-of-burn has been used as a mechanism to destroy cryptocurrency in a verifiable manner. Despite its well known use, the mechanism has not been previously formally studied as a primitive. In this paper, we put forth the first cryptographic definition of what a proof-of-burn protocol is. It consists of two functions: First, a function which generates a cryptocurrency address. When a user sends money to this address, the money is irrevocably destroyed. Second, a verification function which checks that an address is really unspendable. We propose the following properties for burn protocols. Unspendability, which mandates that an address which verifies correctly as a burn address cannot be used for spending; binding, which allows associating metadata with a particular burn; and uncensorability, which mandates that a burn address is indistinguishable from a regular cryptocurrency address. Our definition captures all previously known proof-of-burn protocols. Next, we design a novel construction for burning which is simple and flexible, making it compatible with all existing popular cryptocurrencies. We prove our scheme is secure in the Random Oracle model. We explore the application of destroying value in a legacy cryptocurrency to bootstrap a new one. The user burns coins in the source blockchain and subsequently creates a proof-of-burn, a short string proving that the burn took place, which she then submits to the destination blockchain to be rewarded with a corresponding amount. The user can use a standard wallet to conduct the burn without requiring specialized software, making our scheme user friendly. We propose burn verification mechanisms with different security guarantees, noting that the target blockchain miners do not necessarily need to monitor the source blockchain. Finally, we implement the verification of Bitcoin burns as an Ethereum smart contract and experimentally measure that the gas costs needed for verification are as low as standard Bitcoin transaction fees, illustrating that our scheme is practical.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
Notes
- 1.
The Bitcoin address 1111111111111111111114oLvT2 encodes the all-zeros string and has received more than 50, 000 transactions dating back to Aug 2010.
- 2.
References
Counterparty. https://counterparty.io/
Developer guide - bitcoin. https://bitcoin.org/en/developer-guide
summa-tx/bitcoin-spv: utilities for Bitcoin SPV proof verification on other chains. https://github.com/summa-tx/bitcoin-spv/
Andresen, G.: BIP 0016: Pay to Script Hash, January 2012. https://github.com/bitcoin/bips/blob/master/bip-0016.mediawiki
Bartoletti, M., Pompianu, L.: An analysis of bitcoin OP\(\_\)RETURN metadata. In: Brenner, M., et al. (eds.) FC 2017. LNCS, vol. 10323, pp. 218–230. Springer, Cham (2017). https://doi.org/10.1007/978-3-319-70278-0_14
Bellare, M., Rogaway, P.: Random oracles are practical: a paradigm for designing efficient protocols. In: Ashby, V. (ed.) ACM CCS 1993, pp. 62–73. ACM Press, November 1993
Bonneau, J., Miller, A., Clark, J., Narayanan, A., Kroll, J.A., Felten, E.W.: SoK: research perspectives and challenges for bitcoin and cryptocurrencies. In: 2015 IEEE Symposium on Security and Privacy, pp. 104–121. IEEE Computer Society Press, May 2015
Brook, C.: K Foundation Burn a Million Quid. Ellipsis Books, London (1997)
Bünz, B., Kiffer, L., Luu, L., Zamani, M.: Flyclient: super-light clients for cryptocurrencies. IACR Cryptology ePrint Archive, 2019:226 (2019)
Buterin, V., et al.: A next-generation smart contract and decentralized application platform. White paper (2014)
Cicero, M.T.: De Inventione (85 BC)
Clark, J., Essex, A.: CommitCoin: carbon dating commitments with bitcoin. In: Keromytis, A.D. (ed.) FC 2012. LNCS, vol. 7397, pp. 390–398. Springer, Heidelberg (2012). https://doi.org/10.1007/978-3-642-32946-3_28
Garay, J.A., Kiayias, A., Leonardos, N.: The bitcoin backbone protocol: analysis and applications. In: Oswald, E., Fischlin, M. (eds.) EUROCRYPT 2015. Part II. LNCS, vol. 9057, pp. 281–310. Springer, Heidelberg (2015). https://doi.org/10.1007/978-3-662-46803-6_10
Garay, J., Kiayias, A., Leonardos, N.: The bitcoin backbone protocol with chains of variable difficulty. In: Katz, J., Shacham, H. (eds.) CRYPTO 2017. Part I. LNCS, vol. 10401, pp. 291–323. Springer, Cham (2017). https://doi.org/10.1007/978-3-319-63688-7_10
Karantias, K.: Enabling NIPoPoW applications on bitcoin cash. Master’s thesis, University of Ioannina, Ioannina, Greece (2019)
Karantias, K., Kiayias, A., Zindros, D.: Compact storage of superblocks for NIPoPoW applications. In: Pardalos, P., Kotsireas, I., Guo, Y., Knottenbelt, W. (eds.) Mathematical Research for Blockchain Economy. SPBE, pp. 77–91. Springer, Cham (2020). https://doi.org/10.1007/978-3-030-37110-4_6
Kiayias, A., Lamprou, N., Stouka, A.-P.: Proofs of proofs of work with sublinear complexity. In: Clark, J., Meiklejohn, S., Ryan, P.Y.A., Wallach, D.S., Brenner, M., Rohloff, K. (eds.) FC 2016. LNCS, vol. 9604, pp. 61–78. Springer, Heidelberg (2016). https://doi.org/10.1007/978-3-662-53357-4_5
Kiayias, A., Miller, A., Zindros, D.: Non-interactive proofs of proof-of-work (2017)
Kiayias, A., Zindros, D.: Proof-of-work sidechains. In: Bracciali, A., Clark, J., Pintore, F., Rønne, P.B., Sala, M. (eds.) FC 2019. LNCS, vol. 11599, pp. 21–34. Springer, Cham (2020). https://doi.org/10.1007/978-3-030-43725-1_3
Laertius, D.: Lives of the Eminent Philosophers, Book II (chap. 8), p. 100. Oxford University Press, Oxford (2018)
Landsburg, S.E.: The Armchair Economist (revised and updated May 2012): Economics & Everyday Life. Simon and Schuster, New York (2007)
Nakamoto, S.: Bitcoin: a peer-to-peer electronic cash system (2008). https://bitcoin.org/bitcoin.pdf
P4Titan. Slimcoin a peer-to-peer crypto-currency with proof-of-burn, May 2014. https://www.doc.ic.ac.uk/~ids/realdotdot/crypto_papers_etc_worth_reading/proof_of_burn/slimcoin_whitepaper.pdf
Patterson, S.: Proof-of-burn and reputation pledges, August 2014. https://www.openbazaar.org/blog/proof-of-burn-and-reputation-pledges/
Ristenpart, T., Yilek, S.: The power of proofs-of-possession: securing multiparty signatures against rogue-key attacks. Cryptology ePrint Archive, Report 2007/264 (2007). http://eprint.iacr.org/2007/264
Stewart, I.: Proof of burn - bitcoin wiki, December 2012. https://en.bitcoin.it/wiki/Proof_of_burn
suppp. Interesting bitcoin address, bitcoin forum post (2013). https://bitcointalk.org/index.php?topic=237143.0
Todd, P.: OpenTimestamps: scalable, trustless, distributed timestamping with bitcoin (2016). https://petertodd.org/2016/opentimestamps-announcement
Van Saberhagen, N.: Cryptonote v2.0 (2013). https://cryptonote.org/whitepaper.pdf
Vogelsteller, F., Buterin, V.: ERC 20 token standard (2015). https://github.com/ethereum/EIPs/blob/master/EIPS/eip-20.md
Wood, G.: Ethereum: a secure decentralised generalised transaction ledger. Ethereum Proj. Yellow Pap. 151, 1–32 (2014)
Zindros, D.: Trust in decentralized anonymous marketplaces. Master’s thesis, National Technical University of Athens, Athens, Greece (2016)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Appendix: Full Proofs
Appendix: Full Proofs
Applying an efficiently computable function to indistinguishable distributions preserves indistinguishability.
Lemma 4
(Indistinguishability preservation). Given two computationally indistinguishable distribution ensembles \(\{X_\kappa \}_{\kappa \in \mathbb {N}}\) and \(\{Y_\kappa \}_{\kappa \in \mathbb {N}}\), let \(\{f_\kappa \}_{\kappa \in \mathbb {N}}\) be a family of efficiently computable functions. Then the distribution ensembles \(X' = \{f_\kappa (X_\kappa )\}_{\kappa \in \mathbb {N}}\) and \(Y' = \{f_\kappa (Y_\kappa )\}_{\kappa \in \mathbb {N}}\) are computationally indistinguishable.
We call a distribution ensemble unpredictable if no polynomial-time adversary can guess its output. We observe that, if each element of a distribution appears with negligible probability, then the distribution must be unpredictable. Public keys generated from secure signature schemes must be unpredictable.
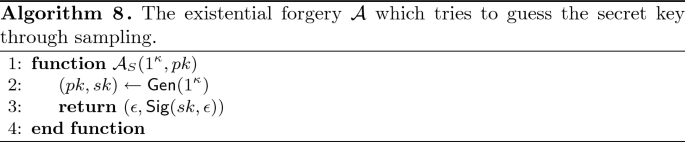
Lemma 2
(Public key unpredictability). Let \(S = (\textsf {Gen}, \textsf {Sig}, \textsf {Ver})\) be a secure signature scheme. Then the distribution ensemble \(X_\kappa = \{(sk, pk) \leftarrow \textsf {Gen}(1^\kappa ); pk\}\) is unpredictable.
Proof
Let \(p = \max _{\widehat{pk} \in [X_\kappa ]}\Pr _{pk \leftarrow X_\kappa }[pk = \widehat{pk}]\). Consider the existential forgery adversary \(\mathcal {A}\) illustrated in Algorithm 8 which works as follows. It receives pk as its input from the challenger, but ignores it and generates a new key pair \((pk', sk') \leftarrow \textsf {Gen}(1^\kappa )\). Since the two invocations of \(\textsf {Gen}\) are independent,
The adversary checks whether \(pk = pk'\). If not, it aborts. Otherwise, it uses \(sk'\) to sign the message \(m = \epsilon \) and returns the forgery \(\sigma = \textsf {Sig}(sk, m)\). From the correctness of the signature scheme, if \(pk = pk'\), then \(\textsf {Ver}(pk, \textsf {Sig}(sk, m)) = \mathsf {true}\) and the adversary is successful. Since the signature scheme is secure, \(\Pr [\textsf {Sig-forge}^{cma}_{\mathcal {A},S}] = \textsf {negl}(\kappa )\). But \(\Pr [pk = pk'] \le \Pr [\textsf {Sig-forge}^{cma}_{\mathcal {A},S}]\) and therefore \(p \le \sqrt{\Pr [pk = pk']} \le \textsf {negl}(\kappa )\). From this, we deduce that the distribution ensemble \(X_\kappa \) is unpredictable. \(\square \)
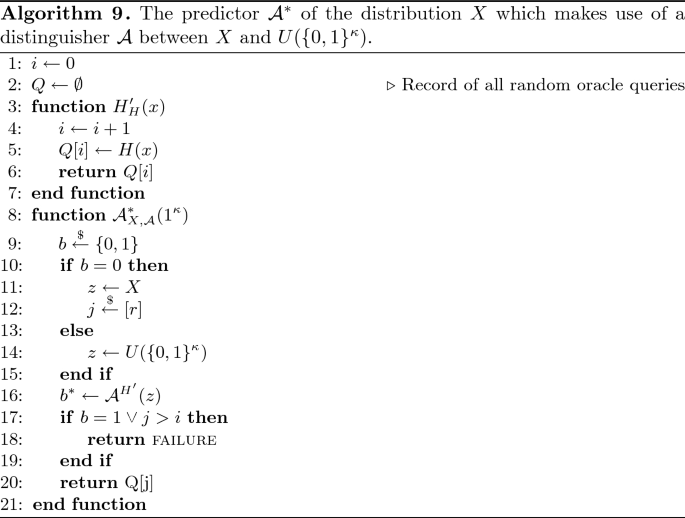
Lemma 3
(Random Oracle unpredictability). Let \(\mathcal {T}\) be an unpredictable distribution ensemble and H be a Random Oracle. The distribution ensemble \(X = \{t \leftarrow \mathcal {T}; H(t)\}\) is indistinguishable from the uniform distribution ensemble \(\mathcal {U}(\{0,1\}^\kappa )\).
Proof
Let \(\mathcal {A}\) be an arbitrary polynomial distinguisher between X and \(\mathcal {U}(\{0, 1\}^\kappa )\). We construct an adversary \(\mathcal {A}^*\) against \(\textsc {predict}_{\mathcal {T}}\). Let r denote the (polynomial) maximum number of random oracle queries of \(\mathcal {A}\). The adversary \(\mathcal {A}^*\) is illustrated in Algorithm 9 and works as follows. Initially, it chooses a random bit \(b {\mathop {\leftarrow }\limits ^{\$}} \{0, 1\}\) and sets \(Z = X\) if \(b = 0\), otherwise sets \(Z = \mathcal {U}(\{0,1\}^\kappa )\). It samples \(z \leftarrow Z\). If \(b = 0\), then z is chosen by applying \(\mathsf {GenAddr}\) which involves calling the random oracle H with some input pk. It then chooses one of \(\mathcal {A}\)’s queries \(j {\mathop {\leftarrow }\limits ^{\$}} [r]\) uniformly at random. Finally, it outputs the input received by the random oracle during the \(j^\text {th}\) query of \(\mathcal {A}\).
We will consider two cases. Either \(\mathcal {A}\) makes a random oracle query containing pk, or it does not. We will argue that, if \(\mathcal {A}\) makes a random oracle query containing pk with non-negligible probability, then \(\mathcal {A}^*\) will be successful with non-negligible probability. However, we will argue that, if \(\mathcal {A}\) does not make the particular random oracle query, it will be unable to distinguish X from \(\mathcal {U}(\{0,1\}^\kappa )\).
Let \(\textsc {qry}\) denote the event that \(b = 0\) and \(\mathcal {A}\) asks a random oracle query with input pk. Let x denote the random variable sampled by the challenger in the predictability game of \(\mathcal {A}^*\). Let \(\textsc {exqry}\) denote the event that \(b = 0\) and \(\mathcal {A}\) asks a random oracle query with input equal to x. Observe that, since the input to \(\mathcal {A}\) does not depend on x, we have that \(\Pr [\textsc {exqry}] = \Pr [\textsc {qry}]\). As j is chosen independently of the execution of \(\mathcal {A}\), conditioned on \(\textsc {exqry}\) the probability that \(\mathcal {A}^*\) is able to correctly guess which query caused \(\textsc {exqry}\) will be \(\frac{1}{r}\). Therefore we obtain that \(\Pr [\textsc {predict}_{\mathcal {A}^*,\mathcal {T}}(\kappa ) = \mathsf {true}] = \frac{1}{r}\Pr [\textsc {exqry}] = \frac{1}{r}\Pr [\textsc {qry}]\). As \(\Pr [\textsc {predict}_{\mathcal {A}^*,\mathcal {T}}(\kappa ) = \mathsf {true}] \le \textsf {negl}(\kappa )\) and r is polynomial in \(\kappa \), we deduce that \(\Pr [\textsc {qry}] \le \textsf {negl}(\kappa )\).
Consider the computational indistinguishability game in which the distinguisher gives a guess \(b^*\) attempting to identify the origin b of its input (with \(b = 0\) indicating that the first distribution was sampled, and \(b = 1\) indicating that the second distribution was sampled). If \(b = 0\), then the distinguisher \(\mathcal {A}\) receives a truly random input \(pkh = H(pk)\). If the distinguisher does not query the random oracle with input pk, the input of the distinguisher is truly random and therefore \(\Pr [b^* = 0|b = 0|\lnot \textsc {qry}] = \Pr [b^* = 0|b = 1]\).
Consider the case where \(b = 0\) and apply total probability to obtain
Then \( \Pr [\textsc {dist}\text {-}\textsc {game}_{\mathcal {A},X,\mathcal {U}(\{0,1\}^\kappa )} = \mathsf {true}] = \Pr [b = b^*] \) is the probability of success of the distinguisher. Applying total probability we obtain
\(\square \)
Rights and permissions
Copyright information
© 2020 International Financial Cryptography Association
About this paper
Cite this paper
Karantias, K., Kiayias, A., Zindros, D. (2020). Proof-of-Burn. In: Bonneau, J., Heninger, N. (eds) Financial Cryptography and Data Security. FC 2020. Lecture Notes in Computer Science(), vol 12059. Springer, Cham. https://doi.org/10.1007/978-3-030-51280-4_28
Download citation
DOI: https://doi.org/10.1007/978-3-030-51280-4_28
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-51279-8
Online ISBN: 978-3-030-51280-4
eBook Packages: Computer ScienceComputer Science (R0)

