Abstract
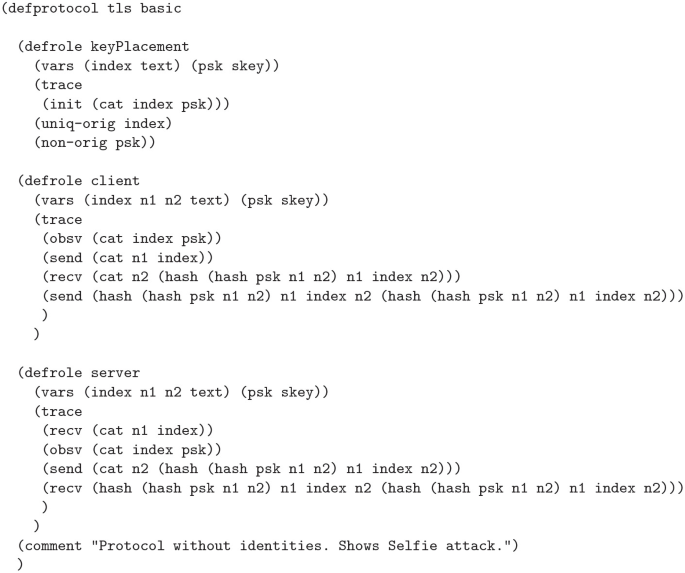
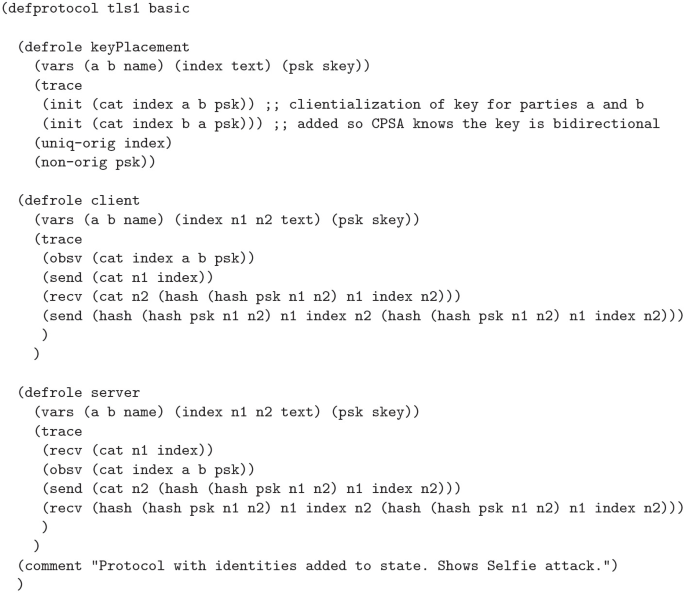
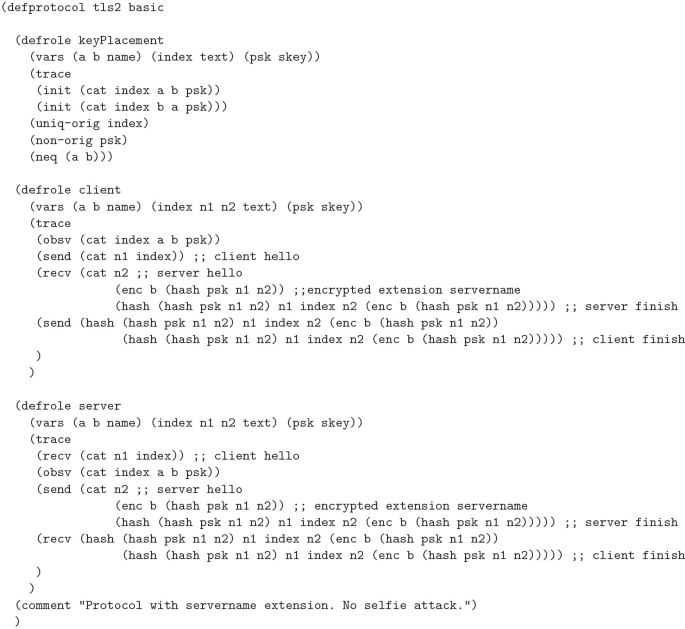
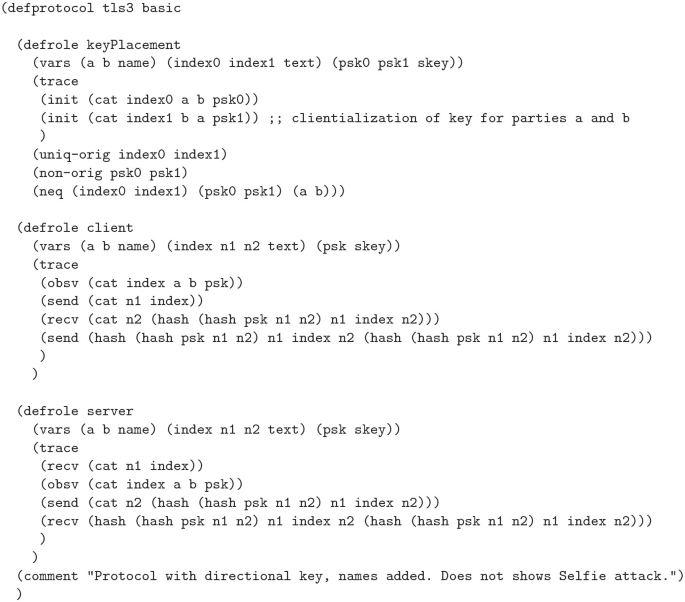
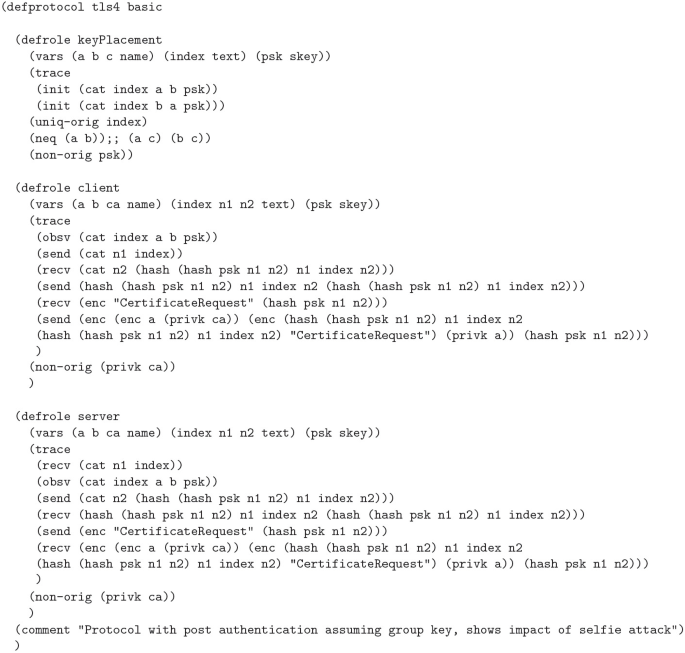
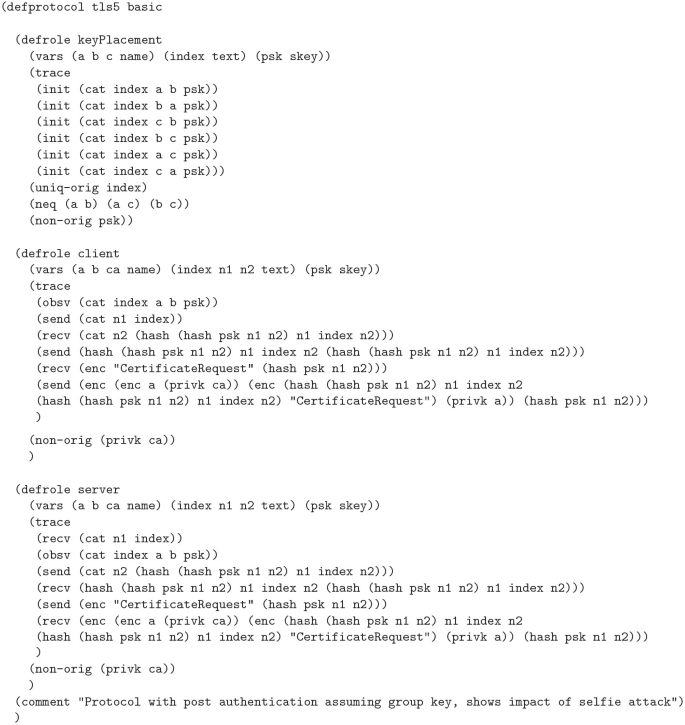
TLS 1.3 was developed in conjunction with several formal analyses and proofs of its security properties. However, in 2019, researchers Drucker and Gueron discovered a reflection attack, they named Selfie, against the pre-shared key (PSK) mode of authentication used by TLS 1.3 by identifying a gap in the proofs. They realized that the proofs ignored the case of external PSKs. They demonstrated that if the PSK was not associated with a particular client and server pairing, such as a single PSK between a pair of hosts which could use the key as either a client or server, implicit authentication implied by the use of the PSK would fail in a reflection attack. The proofs and tools used did not account for this, so we set out to determine if it was possible to identify this attack with the Cryptographic Protocol Shapes Analyzer (CPSA). Using CPSA, which attempts to enumerate all equivalence classes of a protocol’s executions, we were able to uncover the attack and verify two proposed mitigations. We were also able to identify a previously discovered impersonation attack against the use of post handshake authentication in scenarios where a PSK is used as a network key.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Adrian, D., et al.: Imperfect forward secrecy: how Diffie-Hellman fails in practice. In: 22nd ACM Conference on Computer and Communications Security (Oct 2015)
Akhmetzyanova, L., Alekseev, E., Smyshlyaeva, E., Sokolov, A.: On post-handshake authentication and external psks in tls 1.3. J. Comput. Virology Hacking Tech. 16(4), 269–274 (2020)
Al Fardan, N.J., Paterson, K.G.: Lucky thirteen: breaking the TLS and DTLS record protocols. In: 2013 IEEE Symposium on Security and Privacy, pp. 526–540 (2013). https://doi.org/10.1109/SP.2013.42
Beurdouche, B., et al.: A messy state of the union: taming the composite state machines of TLS. In: 2015 IEEE Symposium on Security and Privacy, pp. 535–552 (2015). https://doi.org/10.1109/SP.2015.39
Bhargavan, K., Blanchet, B., Kobeissi, N.: Verified Models and Reference Implementations for the TLS 1.3 Standard Candidate. Research Report RR-9040, Inria Paris, May 2017. https://hal.inria.fr/hal-01528752
Bhargavan, K., Lavaud, A.D., Fournet, C., Pironti, A., Strub, P.Y.: Triple handshakes and cookie cutters: breaking and fixing authentication over TLS. In: 2014 IEEE Symposium on Security and Privacy, pp. 98–113 (2014). https://doi.org/10.1109/SP.2014.14
Cremers, C., Horvat, M., Hoyland, J., Scott, S., van der Merwe, T.: A comprehensive symbolic analysis of TLS 1.3. In: Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security, CCS 2017, pp. 1773–1788. Association for Computing Machinery, New York (2017). https://doi.org/10.1145/3133956.3134063, https://doi.org/10.1145/3133956.3134063
Cremers, C., Horvat, M., Scott, S., van der Merwe, T.: Automated analysis and verification of TLS 1.3: 0-rtt, resumption and delayed authentication. In: 2016 IEEE Symposium on Security and Privacy (SP), pp. 470–485 (2016). https://doi.org/10.1109/SP.2016.35
Doghmi, S.F., Guttman, J.D., Thayer, F.J.: Searching for shapes in cryptographic protocols. In: Grumberg, O., Huth, M. (eds.) TACAS 2007. LNCS, vol. 4424, pp. 523–537. Springer, Heidelberg (2007). https://doi.org/10.1007/978-3-540-71209-1_41
Dowling, B., Fischlin, M., Günther, F., Stebila, D.: A cryptographic analysis of the TLS 1.3 draft-10 full and pre-shared key handshake protocol. Cryptology ePrint Archive, Report 2016/081 (2016). https://eprint.iacr.org/2016/081
Drucker, N., Gueron, S.: Selfie: reflections on TLS 1.3 with PSK. Cryptology ePrint Archive, Report 2019/347 (2019). https://eprint.iacr.org/2019/347
Fabrega, F.J.T., Herzog, J.C., Guttman, J.D.: Strand spaces: why is a security protocol correct? In: Proceedings of the 1998 IEEE Symposium on Security and Privacy (Cat. No.98CB36186), pp. 160–171, May 1998. https://doi.org/10.1109/SECPRI.1998.674832
Fischlin, M., Günther, F.: Replay attacks on zero round-trip time: the case of the TLS 1.3 handshake candidates. Cryptology ePrint Archive, Report 2017/082 (2017). https://eprint.iacr.org/2017/082
Fischlin, M., Günther, F., Schmidt, B., Warinschi, B.: Key confirmation in key exchange: a formal treatment and implications for TLS 1.3. In: 2016 IEEE Symposium on Security and Privacy (SP), pp. 452–469 (2016). https://doi.org/10.1109/SP.2016.34
Guttman, J.D., Liskov, M.D., Ramsdell, J.D., Rowe, P.D.: The Cryptographic Protocol Shapes Analyzer (CPSA). https://github.com/mitre/cpsa
Housley, R., Hoyland, J., Sethi, M., Wood, C.: Guidance for External PSK Usage in TLS, draft-ietf-tls-external-psk-guidance-02, August 2021
Krawczyk, H., Wee, H.: The optls protocol and TLS 1.3. In: 2016 IEEE European Symposium on Security and Privacy (EuroS P), pp. 81–96 (2016). https://doi.org/10.1109/EuroSP.2016.18
Li, X., Xu, J., Zhang, Z., Feng, D., Hu, H.: Multiple handshakes security of TLS 1.3 candidates. In: 2016 IEEE Symposium on Security and Privacy (SP), pp. 486–505 (2016). https://doi.org/10.1109/SP.2016.36
Liskov, M.D., Ramsdell, J.D., Guttman, J.D., Rowe, P.D.: The Cryptographic Protocol Shapes Analyser: A Manual. Manual, The MITRE Corporation, May 2020. https://github.com/mitre/cpsa
Paterson, K.G., van der Merwe, T.: Reactive and proactive standardisation of TLS. In: Chen, L., McGrew, D., Mitchell, C. (eds.) SSR 2016. LNCS, vol. 10074, pp. 160–186. Springer, Cham (2016). https://doi.org/10.1007/978-3-319-49100-4_7
Rescorla, E.: The Transport Layer Security (TLS) Protocol Version 1.3, RFC 8446, August 2018
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2021 Springer Nature Switzerland AG
About this chapter
Cite this chapter
Bhandary, P., Zieglar, E., Nicholas, C. (2021). Searching for Selfie in TLS 1.3 with the Cryptographic Protocol Shapes Analyzer. In: Dougherty, D., Meseguer, J., Mödersheim, S.A., Rowe, P. (eds) Protocols, Strands, and Logic. Lecture Notes in Computer Science(), vol 13066. Springer, Cham. https://doi.org/10.1007/978-3-030-91631-2_3
Download citation
DOI: https://doi.org/10.1007/978-3-030-91631-2_3
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-91630-5
Online ISBN: 978-3-030-91631-2
eBook Packages: Computer ScienceComputer Science (R0)