Abstract
People have personal and/or business need to share private and confidential documents; however, often at the expense of privacy. Privacy aware users demand that their data is secure during the entire life cycle, and not residing in clouds indefinitely. A trending feature in industry is to set download constraints of shared files - a file can be downloaded for a restricted number of times and/or within a limited time framework. Metadata privacy becomes concerning with web services and applications providing such additional level of security control but not hiding the metadata. There is no prior research focusing on privacy-preserving expiration control, hence we propose OblivShare, a privacy-preserving file sharing scheme to proactively fill the gap. The scheme is based on ORAM for secure computation that 1) supports file expiration at users’ control, 2) hides expiration metadata from the server, 3) server is fully oblivious of file access pattern and expiration state of a file. We demonstrate that our protocol has a complexity poly-logarithmic to the number of files while achieving privacy of metadata.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Backes, M., Herzberg, A., Kate, A., Pryvalov, I.: Anonymous RAM. In: Askoxylakis, I., Ioannidis, S., Katsikas, S., Meadows, C. (eds.) ESORICS 2016. LNCS, vol. 9878, pp. 344–362. Springer, Cham (2016). https://doi.org/10.1007/978-3-319-45744-4_17
Bogdanov, D., Niitsoo, M., Toft, T., Willemson, J.: High-performance secure multi-party computation for data mining applications. Int. J. Inf. Secur. 11(6), 403–418 (2012). https://doi.org/10.1007/s10207-012-0177-2
Chen, W., Popa, R.A.: Metal: a metadata-hiding file-sharing system. IACR Cryptology ePrint Archive 2020/83 (2020)
Dingledine, R., Mathewson, N., Syverson, P.: Tor: the second-generation onion router. Technical report, Naval Research Lab Washington DC (2004)
Doerner, J., Shelat, A.: Scaling ORAM for secure computation. In: Proceedings of the 2017 ACM SIGSAC Conference on Computer and Communications Security, pp. 523–535 (2017)
Dropbox: Dropbox Business Security: A Dropbox whitepaper. Technical report, Dropbox (2019)
DropSecure: Enabling True File Transfer Security: How DropSecure safeguards your confidential data. Technical report, DropSecure (2019)
Fitzpatrick, K.: Password protect files with Digify passkey encryption (2019). https://help.digify.com/en/articles/747136-password-protect-files-with-digify-passkey-encryption
Fu, Z., Ren, K., Shu, J., Sun, X., Huang, F.: Enabling personalized search over encrypted outsourced data with efficiency improvement. IEEE Trans. Parallel Distrib. Syst. 27(9), 2546–2559 (2015)
Goldreich, O.: Towards a theory of software protection and simulation by oblivious RAMs. In: Proceedings of the Nineteenth Annual ACM Symposium on Theory of Computing, pp. 182–194 (1987)
Hamlin, A., Ostrovsky, R., Weiss, M., Wichs, D.: Private anonymous data access. In: Ishai, Y., Rijmen, V. (eds.) EUROCRYPT 2019. LNCS, vol. 11477, pp. 244–273. Springer, Cham (2019). https://doi.org/10.1007/978-3-030-17656-3_9
Liang, K., Liu, J.K., Lu, R., Wong, D.S.: Privacy concerns for photo sharing in online social networks. IEEE Internet Comput. 19(2), 58–63 (2015)
Liu, W., Wang, Y.B., Jiang, Z.T., Cao, Y.Z.: A protocol for the quantum private comparison of equality with \(\chi \)-type state. Int. J. Theor. Phys. 51(1), 69–77 (2012). https://doi.org/10.1007/s10773-011-0878-8
Maffei, M., Malavolta, G., Reinert, M., Schröder, D.: Privacy and access control for outsourced personal records. In: 2015 IEEE Symposium on Security and Privacy, pp. 341–358. IEEE (2015)
Maffei, M., Malavolta, G., Reinert, M., Schröder, D.: Maliciously secure multi-client ORAM. In: Gollmann, D., Miyaji, A., Kikuchi, H. (eds.) ACNS 2017. LNCS, vol. 10355, pp. 645–664. Springer, Cham (2017). https://doi.org/10.1007/978-3-319-61204-1_32
McMillan, R., Knutson, R.: Yahoo triples estimate of breached accounts to 3 billion (2017). https://www.wsj.com/articles/yahoo-triples-estimate-of-breached-accounts-to-3-billion-1507062804
Nguyen, N.: Introducing Firefox send, providing free file transfers while keeping your personal information private (2019). https://blog.mozilla.org/blog/2019/03/12/introducing-firefox-send-providing-free-file-transfers-while-keeping-your-personal-information-private/
Pinkas, B., Reinman, T.: Oblivious RAM revisited. In: Rabin, T. (ed.) CRYPTO 2010. LNCS, vol. 6223, pp. 502–519. Springer, Heidelberg (2010). https://doi.org/10.1007/978-3-642-14623-7_27
Regulation, G.D.P.: Regulation (EU) 2016/679 of the European parliament and of the council of 27 April 2016 on the protection of natural persons with regard to the processing of personal data and on the free movement of such data, and repealing directive 95/46. Off. J. Eur. Union (OJ) 59(1–88), 294 (2016)
Roche, D.S., Aviv, A., Choi, S.G.: A practical oblivious map data structure with secure deletion and history independence. In: 2016 IEEE Symposium on Security and Privacy (SP), pp. 178–197. IEEE (2016)
Rösler, P., Mainka, C., Schwenk, J.: More is less: on the end-to-end security of group chats in Signal, WhatsApp, and Threema. In: 2018 IEEE European Symposium on Security and Privacy (EuroS&P), pp. 415–429. IEEE (2018)
Rusbridger, A.: The Snowden leaks and the public (2013)
Schneier, B.: Data and Goliath: The Hidden Battles to Collect Your Data and Control Your World. WW Norton & Company, New York (2015)
SendSafely: Powerful security that’s simple to use (2019). https://www.sendsafely.com/howitworks/
Shi, E., Chan, T.-H.H., Stefanov, E., Li, M.: Oblivious RAM with O((logN)3) worst-case cost. In: Lee, D.H., Wang, X. (eds.) ASIACRYPT 2011. LNCS, vol. 7073, pp. 197–214. Springer, Heidelberg (2011). https://doi.org/10.1007/978-3-642-25385-0_11
Shundong, L., Chunying, W., Daoshun, W., Yiqi, D.: Secure multiparty computation of solid geometric problems and their applications. Inf. Sci. 282, 401–413 (2014)
Silverstein, J.: Hundreds of millions of Facebook user records were exposed on amazon cloud server (2019). https://www.cbsnews.com/news/millions-facebook-user-records-exposed-amazon-cloud-server/
Stefanov, E., et al.: Path ORAM: an extremely simple oblivious RAM protocol. In: Proceedings of the 2013 ACM SIGSAC Conference on Computer & Communications Security, pp. 299–310 (2013)
Telegram: What is a secret chat in Telegram (2019). https://telegramguide.com/secret-chat-telegram/
Toft, T.: Secure data structures based on multi-party computation. In: Proceedings of the 30th Annual ACM SIGACT-SIGOPS Symposium on Principles of Distributed Computing, pp. 291–292 (2011)
de la Torre, L.: A guide to the California consumer privacy act of 2018. SSRN 3275571 (2018)
Wang, X., Chan, H., Shi, E.: Circuit ORAM: on tightness of the Goldreich-Ostrovsky lower bound. In: Proceedings of the 22nd ACM SIGSAC Conference on Computer and Communications Security, pp. 850–861 (2015)
Wang, X.S., Huang, Y., Chan, T.H., Shelat, A., Shi, E.: SCORAM: oblivious RAM for secure computation. In: Proceedings of the 2014 ACM SIGSAC Conference on Computer and Communications Security, pp. 191–202 (2014)
WhatsApp: WhatsApp encryption overview: technical white paper. Technical report, WhatsApp (2017)
Yao, A.C.C.: How to generate and exchange secrets. In: 27th Annual Symposium on Foundations of Computer Science (SFCS 1986), pp. 162–167. IEEE (1986)
Zahur, S., et al.: Revisiting square-root ORAM: efficient random access in multi-party computation. In: 2016 IEEE Symposium on Security and Privacy (SP), pp. 218–234. IEEE (2016)
Zuo, C., Shao, J., Liu, J.K., Wei, G., Ling, Y.: Fine-grained two-factor protection mechanism for data sharing in cloud storage. IEEE Trans. Inf. Forensics Secur. 13(1), 186–196 (2018)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
A METAL’s Synchronised Inside-Outside ORAM Trees
A METAL’s Synchronised Inside-Outside ORAM Trees
1.1 A.1 Secret-Shared Doubly Oblivious Transfer
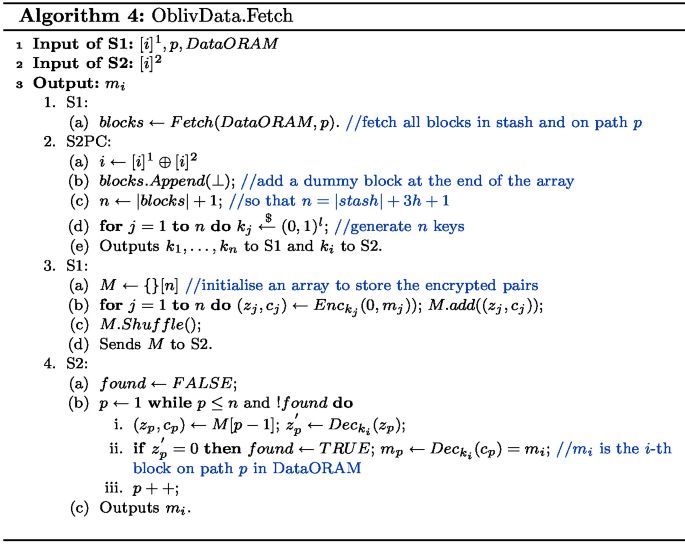
Let N be an array of the blocks in the stash and the 3h blocks on path p:
-
1.
The two servers inside S2PC, generate n keys \({k_1,\ldots ,k_n}\) such that S1 receives as output all these keys, and S2 receives only \(k_i\). \(n = |stash| + 3h + 1\).
-
2.
For each \(j \in {1,\ldots ,n}\), S1 uses \(k_j\) to encrypt 0 and \(m_j\) to obtain cipher-texts \(z_j\) and \(c_j\) respectively. S1 shuffles all the \((z_j, c_j)\) pairs and sends them to S2.
-
3.
S2 uses \(k_i\) to decrypt the first cipher-text of each pair: only one \(z_j\), will decrypt to 0. It then decrypts the corresponding \(c_j\) and hence obtain \(m_i\).
1.2 A.2 Distributed Permutation
Recall that Circuit ORAM selects two paths during eviction, hence we need to track the movement of blocks in the stash and on the two paths, which has \(|stash| = 6h - 3\) blocks.
Before each eviction, OblivShare appends a number tracker from 1 to \(|stash| = 6h - 3\) to each block on the stash and two paths in ExpCtrlORAM inside S2PC. After the ExpCtrlORAM’s stash eviction, the protocol extracts the trackers and construct an array of the numbers. Note that some numbers no longer exist as the attaching blocks are removed during the eviction. In order to generate a permeation of the same \(|stash| = 6h - 3\) elements, OblivShare searches for the missing trackers using a linear scan and fill in the empty slots with unused numbers.

Below, we present how the two servers in secure computation put a block into the DataORAM’s stash before eviction:
-
1.
The S2PC places the following in an array: the blocks in the stash, the block read, and the block to write, which has \((|stash|+2)\) blocks.
-
2.
The S2PC finds that the k-th block of the stash is vacant, then generates a permutation \(\sigma ^{read}\) or \(\sigma ^{write}\), which exchanges the k-th block with the read block for \(\sigma ^{read}\) or the block to write for \(\sigma ^{write}\). As a result, the correct block is inserted into the stash (i.e. the first |stash| blocks of the permuted array).
-
3.
The S2PC secret shares the permutation (\(\sigma ^{read}\) or \(\sigma ^{write}\)) into two permutations \(\sigma ^1\) and \(\sigma ^2\), when \(\sigma ^2 = \sigma \circ (\sigma ^1)^{-1}\). \(\circ \) denotes composition of permutation and \(\sigma \circ (\sigma )^{-1}\) is the identity permutation.
-
4.
S1 re-randomise the blocks, apply the permutations \(\sigma ^1\), and sends the permuted blocks to S2.
-
5.
S2 re-randomise the blocks received, apply the permutations \(\sigma ^2\), and sends the permuted blocks back to S1.
-
6.
S1 stores the permuted blocks in the corresponding location in DataORAM.
Rights and permissions
Copyright information
© 2021 Springer Nature Switzerland AG
About this paper
Cite this paper
Shen, Y., Yuan, X., Sun, SF., Liu, J.K., Nepal, S. (2021). OblivShare: Towards Privacy-Preserving File Sharing with Oblivious Expiration Control. In: Deng, R., et al. Information Security Practice and Experience. ISPEC 2021. Lecture Notes in Computer Science(), vol 13107. Springer, Cham. https://doi.org/10.1007/978-3-030-93206-0_9
Download citation
DOI: https://doi.org/10.1007/978-3-030-93206-0_9
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-93205-3
Online ISBN: 978-3-030-93206-0
eBook Packages: Computer ScienceComputer Science (R0)
