Abstract
Recently, there has been great interest towards constructing efficient zero-knowledge proofs for practical languages. In this work, we focus on proofs for threshold relations, in which the prover is required to prove knowledge of witnesses for k out of \(\ell \) statements.
The main contribution of our work is an efficient and modular transformation that starting from a large class of \(\varSigma \)-protocols and a corresponding threshold relation \(\mathcal {R}_\mathsf {k,\ell }\), provides an efficient \(\varSigma \)-protocol for \(\mathcal {R}_\mathsf {k,\ell }\) with improved communication complexity w.r.t. prior results. Our transformation preserves statistical/perfect honest-verifier zero knowledge.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
Notes
- 1.
The result of [12] instead works only for \(k=1\), but it just requires 3 rounds.
- 2.
For ease of presentation, in this work we will use the term PTR even when the soundness property holds only against a computationally bounded adversarial prover. We will do the same for computational \(\varSigma \)-protocols which only satisfy a weaker version of special soundness called computational special soundness (cfr., Appendix A).
- 3.
We will be more precise later making the impact of the security parameter explicit.
- 4.
For each proof there are two sequences of \(\log \ell \) pairs of parameters.
- 5.
- 6.
Sec. 9.1 and App. F of [10].
- 7.
For this composition to work and to compress the communication complexity down to logarithmic, the size of the equivocal commitment must be independent of the size of the committed value. To solve this issue, committed values have to be compressed down to a constant size with the aid of a collision-resistant hash function.
- 8.
The statement for \(\mathcal {R}_{T}\) may also depend from \(\textsf{pp}\). We will omit this dependence to simplify the notation.
- 9.
Our definition slightly differs from the one in [10]. In particular, our fixed equivocation property implies the partial binding of [10]. We need this slightly stronger property to prove the soundness of our \((k,\ell )\)-PTR. Natural instantiations such as \(\textsf{GGHK}\) enjoy the fixed equivocation property. The remaining properties are just a restatement of the minimal requirements for a 1-out-of-2 commitment scheme in [10].
- 10.
For consistency reasons, we assign the index 1 to the first position within the string and we say that \(s_i[0]=0\).
- 11.
In the following formula the AND ranging from \(j=0\) to \(j=i-1\) is evaluated as true for \(j=0\). Indeed, according to the notation used in this paper, there are no parameters pair in the position 0 of the vector.
- 12.
All witnesses extracted from the same composition tree are related to different statements by construction. Thus, in this case we would not need to show any reduction.
- 13.
For convenience, we omit the security parameter in unary from the inputs.
References
Attema, T., Cramer, R., Fehr, S.: Compressing proofs of k-Out-Of-n partial knowledge. In: Malkin, T., Peikert, C. (eds.) CRYPTO 2021. LNCS, vol. 12828, pp. 65–91. Springer, Cham (2021). https://doi.org/10.1007/978-3-030-84259-8_3
Attema, T., Cramer, R., Rambaud, M.: Compressed \(\varSigma \)-protocols for bilinear group arithmetic circuits and application to logarithmic transparent threshold signatures. In: Tibouchi, M., Wang, H. (eds.) ASIACRYPT 2021. LNCS, vol. 13093, pp. 526–556. Springer, Cham (2021). https://doi.org/10.1007/978-3-030-92068-5_18
Avitabile, G., Botta, V., Friolo, D., Visconti, I.: Efficient proofs of knowledge for threshold relations. Cryptology ePrint Archive, Report 2022/746 (2022)
Baum, C., Malozemoff, A.J., Rosen, M.B., Scholl, P.: \(\sf Mac^{\prime }n^{\prime }Cheese\): zero-knowledge proofs for Boolean and arithmetic circuits with nested disjunctions. In: Malkin, T., Peikert, C. (eds.) CRYPTO 2021. LNCS, vol. 12828, pp. 92–122. Springer, Cham (2021). https://doi.org/10.1007/978-3-030-84259-8_4
Ben-Sasson, E., Bentov, I., Horesh, Y., Riabzev, M.: Scalable zero knowledge with no trusted setup. In: Boldyreva, A., Micciancio, D. (eds.) CRYPTO 2019. LNCS, vol. 11694, pp. 701–732. Springer, Cham (2019). https://doi.org/10.1007/978-3-030-26954-8_23
Bresson, E., Stern, J., Szydlo, M.: Threshold ring signatures and applications to ad-hoc groups. In: Yung, M. (ed.) CRYPTO 2002. LNCS, vol. 2442, pp. 465–480. Springer, Heidelberg (2002). https://doi.org/10.1007/3-540-45708-9_30
Chen, J., Hu, Y., Gao, W., Li, H.: Lattice-based threshold ring signature with message block sharing. KSII 13(2), 1003–1019 (2019). https://doi.org/10.3837/tiis.2019.02.028
Ciampi, M., Persiano, G., Scafuro, A., Siniscalchi, L., Visconti, I.: Online/Offline OR composition of sigma protocols. In: Fischlin, M., Coron, J.-S. (eds.) EUROCRYPT 2016. LNCS, vol. 9666, pp. 63–92. Springer, Heidelberg (2016). https://doi.org/10.1007/978-3-662-49896-5_3
Cramer, R., Damgård, I., Schoenmakers, B.: Proofs of partial knowledge and simplified design of witness hiding protocols. In: Desmedt, Y.G. (ed.) CRYPTO 1994. LNCS, vol. 839, pp. 174–187. Springer, Heidelberg (1994). https://doi.org/10.1007/3-540-48658-5_19
Goel, A., Green, M., Hall-Andersen, M., Kaptchuk, G.: Stacking sigmas: a Framework to Compose \(\varSigma \)-protocols for disjunctions. Cryptology ePrint Archive, Report 2021/422 (2021). version accessed 09 November 2021
Goel, A., Green, M., Hall-Andersen, M., Kaptchuk, G.: Stacking sigmas: a framework to compose \(\varSigma \)-protocols for disjunctions. In: Dunkelman, O., Dziembowski, S. (eds) , vol. 13276, pp. 458–487. Springer, Cham (2022). https://doi.org/10.1007/978-3-031-07085-3_16
Groth, J., Kohlweiss, M.: One-out-of-many proofs: or how to leak a secret and spend a coin. In: Oswald, E., Fischlin, M. (eds.) EUROCRYPT 2015. LNCS, vol. 9057, pp. 253–280. Springer, Heidelberg (2015). https://doi.org/10.1007/978-3-662-46803-6_9
Haque, A., Scafuro, A.: Threshold ring signatures: new definitions and post-quantum security. In: Kiayias, A., Kohlweiss, M., Wallden, P., Zikas, V. (eds.) PKC 2020. LNCS, vol. 12111, pp. 423–452. Springer, Cham (2020). https://doi.org/10.1007/978-3-030-45388-6_15
Heath, D., Kolesnikov, V.: Stacked garbling for disjunctive zero-knowledge proofs. In: Canteaut, A., Ishai, Y. (eds.) EUROCRYPT 2020. LNCS, vol. 12107, pp. 569–598. Springer, Cham (2020). https://doi.org/10.1007/978-3-030-45727-3_19
Heath, D., Kolesnikov, V., Peceny, S.: Garbling, stacked and staggered. In: Tibouchi, M., Wang, H. (eds.) ASIACRYPT 2021. LNCS, vol. 13091, pp. 245–274. Springer, Cham (2021). https://doi.org/10.1007/978-3-030-92075-3_9
Munch-Hansen, A., Orlandi, C., Yakoubov, S.: Stronger notions and a more efficient construction of threshold ring signatures. In: Longa, P., Ràfols, C. (eds.) LATINCRYPT 2021. LNCS, vol. 12912, pp. 363–381. Springer, Cham (2021). https://doi.org/10.1007/978-3-030-88238-9_18
Nitulescu, A.: zk-SNARKs: a gentle introduction. https://www.di.ens.fr/~nitulesc/files/Survey-SNARKs.pdf (2020)
Okamoto, T., Tso, R., Yamaguchi, M., Okamoto, E.: A \(k\)-out-of-\(n\) Ring Signature with Flexible Participation for Signers. Cryptology ePrint Archive, Report 2018/728 (2018)
Yuen, T.H., Liu, J.K., Au, M.H., Susilo, W., Zhou, J.: Efficient linkable and/or threshold ring signature without random oracles. Comput. J. 56(4), 407–421 (2013). https://doi.org/10.1093/comjnl/bxs115
Zhou, G., Zeng, P., Yuan, X., Chen, S., Choo, K.K.R.: An efficient code-based threshold ring signature scheme with a leader-participant model. Secur. Commun. Networks 2017, 1–7 (2017). https://doi.org/10.1155/2017/1915239
Acknowledgements
We thank all the anonymous reviewers for their insightful comments. The work of the third author was supported by SPECTRA from Sapienza University of Rome.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
A A \(\varSigma \)-Protocols
A A \(\varSigma \)-Protocols
We consider a 3-round public-coin protocol \(\varPi \) for an NP language \(\mathcal {L}\) with a poly-time relation \(\mathcal {R}_\mathcal {L}\). \(\varPi =(\textsf{P}_0,\textsf{P}_1,\textsf{V})\) is run by a prover running auxiliary algorithms \(\textsf{P}_0,\textsf{P}_1\) and a verifier running an auxiliary algorithm \(\textsf{V}\). The prover and the verifier receive common input \(x\) and the security parameter \(1^\lambda \). The prover receives as an additional private input a witness \(w\) for \(x\). Prover and verifier use the auxiliary algorithms \(\textsf{P}_0, \textsf{P}_1,\textsf{V}\)Footnote 13 in the following way:
-
1.
The prover runs \(\textsf{P}_0\) on common input \(x\), private input \(w\), randomness R, and outputs a message a. The prover sends a to the verifier;
-
2.
The verifier samples a random challenge
 and sends c to the prover;
and sends c to the prover; -
3.
The prover runs \(\textsf{P}_1\) on common input \(x\), private input \(w\), first-round message a, randomness R, and challenge c, and outputs the third-round message z, which is then sent to the verifier;
-
4.
The verifier outputs 1 if \(\textsf{V}(x,a,c,z)=1\), and rejects otherwise.
The transcript (a, c, z) for the protocol \(\varPi =(\textsf{P}_0,\textsf{P}_1,\textsf{V})\), and common statement \(x\) is called accepting if \(\textsf{V}(x,a,c,z)=1\).
Definition 1
A 3-round public-coin protocol \(\varPi =(\textsf{P}_0,\textsf{P}_1,\textsf{V})\), is a \(\varSigma \)-protocol for an NP language \(\mathcal {L}\) with a poly-time relation \(\mathcal {R}_\mathcal {L}\) iff the following holds
-
Completeness: For all \(x\in \mathcal {L}\) and \(w\) such that \((x,w)\in \mathcal {R}_\mathcal {L}\) it holds that:
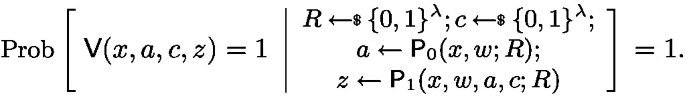
-
Special Soundness: \(\exists \;PPT\;\textsf{Extract}\), such that on input \(x\) and two accepting transcripts \((a,c_0,z_0)\) and \((a,c_1,z_1)\) for \(x\), where \(c_0\ne c_1\), it holds that
$$ \text{ Prob }\left[ \;(x,w)\in \mathcal {R}_\mathcal {L}|w\leftarrow \textsf{Extract}(x,a,c_0,c_1,z_0,z_1)\;\right] =1. $$ -
Special HVZK (SHVZK): There exists a PPT simulator \(\mathcal {S}\) that, on input an instance \(x\in \mathcal {L}\) and challenge c, outputs (a, z) such that (a, c, z) is an accepting transcript for \(x\). Moreover, the distribution of the output of \(\mathcal {S}\) on input \((x,c)\) is computationally/statistically/perfectly indistinguishable from the distribution obtained when the verifier sends c as challenge and the prover runs on common input \(x\) and any private input \(w\) such that \((x,w) \in \mathcal {R}_\mathcal {L}\).
-
Computational Special Soundness: \(\exists \; PPT\;\textsf{Extract}\ s.t.\; \forall \;PPT\;\textsf{P}^*\;\exists \) a negl. function \(\nu (\cdot )\) such that \(\forall x\in \mathcal {L}\), \(\text{ Prob }\left[ \;\textsf{ExpExt}_{\textsf{P}^*,\textsf{Extract}}(x)=1\;\right] \le \nu (|x|). \)
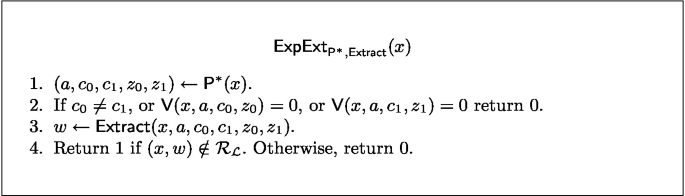
1.1 A.1 A.1 Stackable \(\varSigma \)-protocols
Definition 2
(Computational/Statistical EHVZK). Let \(\varSigma = (\textsf{P}_0,\textsf{P}_1, \textsf{V})\), be a \(\varSigma \)-protocol for an NP language \(\mathcal {L}\). \(\varSigma \) is EHVZK if there exists a PPT algorithm \(\mathcal {S}^\textsf{EHVZK}\) such that for all PPT/unbounded \({\mathcal {D}}\), and \(c\in \{0,1\}^\lambda \), there exists an efficiently samplable distribution \(D^{(z)}_{x,c}\) and a negligible function \(\nu (\cdot )\) such that for all \(x\in \mathcal {L}\)
We say instead that a \(\varSigma \)-protocol is perfect EHVZK if the difference between the probabilities is exactly 0. The experiment \(\textsf{ExpEHVZK}\) for EHVZK follows.
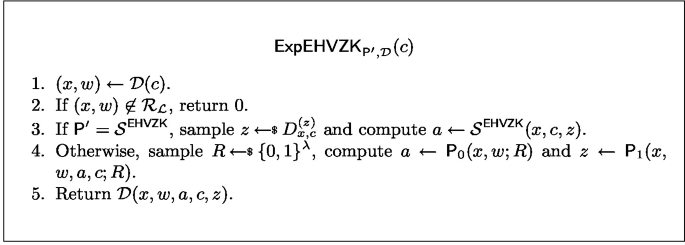
Definition 3
(\(\varSigma \)-protocol with recyclable third messages). Let \(\varSigma =(\textsf{P}_0,\textsf{P}_1,\textsf{V})\) be a \(\varSigma \)-protocol for an NP language \(\mathcal {L}\), \(\varSigma \) has recyclable third messages if for every \(c\in \{0,1\}^\lambda \), there exists an efficiently samplable distribution \(D^{(z)}_c\), such that for all \((x, w)\in \mathcal {R}_\mathcal {L}\), it holds that

Definition 4
(Stackable \(\varSigma \)-protocol). We say that a \(\varSigma \)-protocol \(\varSigma =(\textsf{P}_0,\textsf{P}_1,\textsf{V})\), is stackable, if it is a EHVZK \(\varSigma \)-protocol and has recyclable third messages.
Rights and permissions
Copyright information
© 2022 The Author(s), under exclusive license to Springer Nature Switzerland AG
About this paper
Cite this paper
Avitabile, G., Botta, V., Friolo, D., Visconti, I. (2022). Efficient Proofs of Knowledge for Threshold Relations. In: Atluri, V., Di Pietro, R., Jensen, C.D., Meng, W. (eds) Computer Security – ESORICS 2022. ESORICS 2022. Lecture Notes in Computer Science, vol 13556. Springer, Cham. https://doi.org/10.1007/978-3-031-17143-7_3
Download citation
DOI: https://doi.org/10.1007/978-3-031-17143-7_3
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-031-17142-0
Online ISBN: 978-3-031-17143-7
eBook Packages: Computer ScienceComputer Science (R0)
