Abstract
As low-latency designs tend to have a small number of rounds to decrease latency, the differential-type cryptanalysis can become a significant threat to them. In particular, since a multiple-branch-based design, such as Orthros can have the strong clustering effect on differential attacks due to its large internal state, it is crucial to investigate the impact of the clustering effect in such a design. In this paper, we present a new SAT-based automatic search method for evaluating the clustering effect in the multiple-branch-based design. By exploiting an inherent trait of multiple-branch-based designs, our method enables highly efficient evaluations of clustering effects on this-type designs. We apply our method to the low-latency PRF Orthros, and show a best differential distinguisher reaching up to 7 rounds of Orthros with \(2^{116.806}\) time/data complexity and 9-round distinguisher for each underlying permutation which is 2 more rounds than known longest distinguishers. Besides, we update the designer’s security bound for differential attacks based on the lower bounds for the number of active S-boxes, and obtain the optimal differential characteristic of Orthros, Branch 1, and Branch 2 for the first time. Consequently, we improve the designer’s security bound from 9/12/12 to 7/10/10 rounds for Orthros/Branch 1/Branch 2 based on a single differential characteristic.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
Notes
- 1.
- 2.
The number of clauses and variables in our method is smaller than those in the general method, since our method essentially evaluate the clustering effect on each branch not an entire design while the general method evaluate it on an entire design. Therefore, a practical run-time can be short in our method even if the number of solved SAT problems is the same as that of the general method.
- 3.
In practical, \(\# SAT\) in each branch is different since it depends on various factors, such as their structure. We here assume \(\# SAT\) in each branch is the same for the sake of argument.
- 4.
Strictly speaking, A differential characteristic do not need to be optimal, but the optimal one is the best choice for our method.
References
Ankele, R., Kölbl, S.: Mind the gap - a closer look at the security of block ciphers against differential cryptanalysis. In: Cid, C., Jacobson Jr., M. (eds.) SAC 2018. LNCS, vol. 11349, pp. 163–190. Springer, Cham (2018). https://doi.org/10.1007/978-3-030-10970-7_8
Avanzi, R.: The QARMA block cipher family. Almost MDS matrices over rings with zero divisors, nearly symmetric even-mansour constructions with non-involutory central rounds, and search heuristics for low-latency s-boxes. IACR Trans. Symmetric Cryptol. 2017(1), 4–44 (2017)
Bailleux, O., Boufkhad, Y.: Efficient CNF encoding of Boolean cardinality constraints. In: Rossi, F. (ed.) CP 2003. LNCS, vol. 2833, pp. 108–122. Springer, Heidelberg (2003). https://doi.org/10.1007/978-3-540-45193-8_8
Banik, S., et al.: Midori: a block cipher for low energy. In: Iwata, T., Cheon, J.H. (eds.) ASIACRYPT 2015. LNCS, vol. 9453, pp. 411–436. Springer, Heidelberg (2015). https://doi.org/10.1007/978-3-662-48800-3_17
Banik, S., Isobe, T., Liu, F., Minematsu, K., Sakamoto, K.: Orthros: a low-latency PRF. IACR Trans. Symmetric Cryptol. 2021(1), 37–77 (2021)
Beierle, C., et al.: The SKINNY family of block ciphers and its low-latency variant MANTIS. In: Robshaw, M., Katz, J. (eds.) CRYPTO 2016. LNCS, vol. 9815, pp. 123–153. Springer, Heidelberg (2016). https://doi.org/10.1007/978-3-662-53008-5_5
Biham, E., Shamir, A.: Differential cryptanalysis of des-like cryptosystems. J. Cryptol. 4(1), 3–72 (1991)
Bogdanov, A., et al.: PRESENT: an ultra-lightweight block cipher. In: Paillier, P., Verbauwhede, I. (eds.) CHES 2007. LNCS, vol. 4727, pp. 450–466. Springer, Heidelberg (2007). https://doi.org/10.1007/978-3-540-74735-2_31
Borghoff, J., et al.: PRINCE – a low-latency block cipher for pervasive computing applications. In: Wang, X., Sako, K. (eds.) ASIACRYPT 2012. LNCS, vol. 7658, pp. 208–225. Springer, Heidelberg (2012). https://doi.org/10.1007/978-3-642-34961-4_14
Boura, C., David, N., Boissier, R.H., Naya-Plasencia, M.: Better steady than speedy: full break of SPEEDY-7-192. IACR Cryptol. ePrint Arch., p. 1351 (2022)
Cook, S.A.: The complexity of theorem-proving procedures. In: STOC, pp. 151–158. ACM (1971)
Dobraunig, C., Eichlseder, M., Kales, D., Mendel, F.: Practical key-recovery attack on MANTIS5. IACR Trans. Symmetric Cryptol. 2016(2), 248–260 (2016)
Kölbl, S., Leander, G., Tiessen, T.: Observations on the SIMON block cipher family. In: Gennaro, R., Robshaw, M. (eds.) CRYPTO 2015. LNCS, vol. 9215, pp. 161–185. Springer, Heidelberg (2015). https://doi.org/10.1007/978-3-662-47989-6_8
Lai, X., Massey, J.L., Murphy, S.: Markov ciphers and differential cryptanalysis. In: Davies, D.W. (ed.) EUROCRYPT 1991. LNCS, vol. 547, pp. 17–38. Springer, Heidelberg (1991). https://doi.org/10.1007/3-540-46416-6_2
Leander, G., Moos, T., Moradi, A., Rasoolzadeh, S.: The SPEEDY family of block ciphers engineering an ultra low-latency cipher from gate level for secure processor architectures. IACR Trans. Cryptogr. Hardw. Embed. Syst. 2021(4), 510–545 (2021)
Mouha, N., Preneel, B.: Towards finding optimal differential characteristics for ARX: application to Salsa20. Cryptology ePrint Archive, Paper 2013/328 (2013)
Mouha, N., Wang, Q., Gu, D., Preneel, B.: Differential and linear cryptanalysis using mixed-integer linear programming. In: Wu, C.-K., Yung, M., Lin, D. (eds.) Inscrypt 2011. LNCS, vol. 7537, pp. 57–76. Springer, Heidelberg (2012). https://doi.org/10.1007/978-3-642-34704-7_5
Sun, L., Wang, W., Wang, M.: More accurate differential properties of LED64 and Midori64. IACR Trans. Symmetric Cryptol. 2018(3), 93–123 (2018)
Sun, L., Wang, W., Wang, M.: Accelerating the search of differential and linear characteristics with the SAT method. IACR Trans. Symmetric Cryptol. 2021(1), 269–315 (2021)
Sun, S., et al.: Towards finding the best characteristics of some bit-oriented block ciphers and automatic enumeration of (related-key) differential and linear characteristics with predefined properties. Cryptology ePrint Archive, Paper 2014/747 (2014)
Teh, J.S., Biryukov, A.: Differential cryptanalysis of WARP. IACR Cryptol. ePrint Arch., p. 1641 (2021)
Vallade, V., et al.: New concurrent and distributed painless solvers: p-mcomsps, p-mcomsps-com, p-mcomsps-mpi, and p-mcomsps-com-mpi. SAT COMPETITION, p. 40 (2021)
Acknowledgments
Takanori Isobe is supported by JST, PRESTO Grant Number JPMJPR2031. These research results were also obtained from the commissioned research (No. 05801) by National Institute of Information and Communications Technology (NICT), Japan. Kosei Sakamoto is supported by Grant-in-Aid for JSPS Fellows (KAKENHI 20J23526) for Japan Society for the Promotion of Science.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Detailed Explanation of Branch 1 and Branch 2
Detailed Explanation of Branch 1 and Branch 2
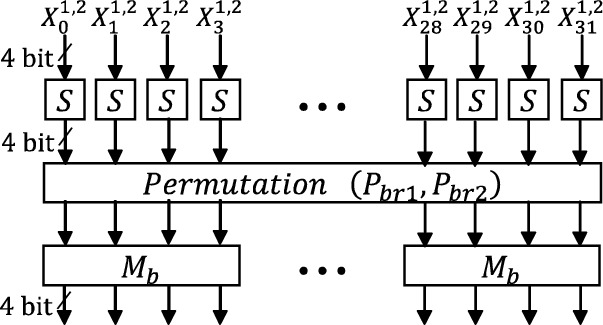
Orthros is a two-branch-based design in which the underlying components are SPN-based PRPs as shown in Fig. 7. The underlying two keyed permutations consist of S-box (SB), bit-permutation (\(P_{brN}\)), nibble-permutation \((P_{nN}\)), MixColumn (MC), AddRoundKey (AK) and AddConstant (AC). We provide the detailed explanation of those function. Note that we do not give the explanation of a key scheduling because our evaluation does not consider the impact of the round keys.
- SB:
-
A 4-bit S-box will be applied to each nibbles in parallel for Branch1 and Branch2. The specification of the 4-bit S-box is given in Table 8.
- \(P_{brN}\),\(P_{nN}\):
-
For the first 4 rounds of Branch1 and Branch2, \(P_{br1}\) and \(P_{br2}\) will be applied, respectively. From the 5th round to the 11th round, the nibble permutations \(P_{n1}\) and \(P_{n2}\) will be adopted in each branch respectively. The details of the permutation \(P_{brN}\) and \(P_{nN}\), where \(N \in \{1, 2\}\), are shown in Table 9 and Table 10, respectively.
- MC :
-
Let \(M_{b}\) be \(4\times 4\) binary matrix over nibbles defined as
$$ M_b = \begin{pmatrix} 0 &{} 1 &{} 1 &{} 1 \\ 1 &{} 0 &{} 1 &{} 1 \\ 1 &{} 1 &{} 0 &{} 1 \\ 1 &{} 1 &{} 1 &{} 0 \end{pmatrix}. $$Four nibbles \((a_0, a_1, a_2, a_3)\) will be updated as follows:
$$ (a_0, a_1, a_2, a_3)^T \leftarrow M_b\cdot (a_0, a_1, a_2, a_3)^T. $$ - \(\boldsymbol{R}_{\boldsymbol{f_N}}\) :
-
Figure 8 and 9 show the first four and remaining rounds of each branch. Note that MC and NP are not applied in the final round.
Rights and permissions
Copyright information
© 2023 The Author(s), under exclusive license to Springer Nature Switzerland AG
About this paper
Cite this paper
Taka, K., Ishikawa, T., Sakamoto, K., Isobe, T. (2023). An Efficient Strategy to Construct a Better Differential on Multiple-Branch-Based Designs: Application to Orthros. In: Rosulek, M. (eds) Topics in Cryptology – CT-RSA 2023. CT-RSA 2023. Lecture Notes in Computer Science, vol 13871. Springer, Cham. https://doi.org/10.1007/978-3-031-30872-7_11
Download citation
DOI: https://doi.org/10.1007/978-3-031-30872-7_11
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-031-30871-0
Online ISBN: 978-3-031-30872-7
eBook Packages: Computer ScienceComputer Science (R0)