Abstract
At CT-RSA 2022, a new infective countermeasure to protect both the deterministic ECDSA and EdDSA signature schemes was introduced to withstand the threat of fault attacks. A few months later, another infective countermeasure for deterministic ECDSA was presented at CHES 2022 in the context of White-Box implementation. In this article we show that these two countermeasures do not achieve their objective by introducing several attacks combining fault injection and lattice reduction techniques. With as few as two faulty signatures, we succeed in recovering the corresponding private key. These results prove, once again, that the design of infective countermeasures is a very challenging task, especially in the case of asymmetric cryptography.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Ambrose, C., Bos, J.W., Fay, B., Joye, M., Lochter, M., Murray, B.: Differential attacks on deterministic signatures. In: Smart, N.P. (ed.) CT-RSA 2018. LNCS, vol. 10808, pp. 339–353. Springer, Cham (2018). https://doi.org/10.1007/978-3-319-76953-0_18
Anderson, R., Kuhn, M.: Improved differential fault analysis. Manuscrit, Nov. 12 (1996)
Aranha, D.F., Novaes, F.R., Takahashi, A., Tibouchi, M., Yarom, Y.: LadderLeak: breaking ECDSA with less than one bit of nonce leakage. In: Ligatti, J., Ou, X., Katz, J., Vigna, G. (eds.) ACM CCS 2020, pp. 225–242. ACM Press (2020)
Bao, F., Deng, R., Han, Y., Jeng, A., Narasimhalu, A.D., Ngair, T.H.: A method to counter another new attack to RSA on tamperproof devices. Manuscrit, Oct. 24 (1996)
Bao, F., Deng, R., Han, Y., Jeng, A., Narasimhalu, A.D., Ngair, T.-H.: A new attack to RSA on tamperproof devices. Manuscrit, Oct. 13 (1996)
Bao, F., Deng, R., Han, Y., Jeng, A., Narasimhalu, D., Nagir, T.H.: New attacks to public key cryptosystems on tamperproof devices. Manuscrit, Oct. 29 (1996)
Bar-El, H., Choukri, H., Naccache, D., Tunstall, M., Whelan, C.: The Sorcerer’s apprentice guide to fault attacks. Proc. IEEE 94(2), 370–382 (2006)
Barbu, G., et al.: Combined attack on CRT-RSA: why public verification must not be public? In: Kurosawa, K., Hanaoka, G. (eds.) PKC 2013. LNCS, vol. 7778, pp. 198–215. Springer, Heidelberg (2013). https://doi.org/10.1007/978-3-642-36362-7_13
Barbu, G., et al.: ECDSA white-box implementations: attacks and designs from CHES 2021 challenge. IACR Trans. Cryptogr. Hardw. Embed. Syst. 2022(4), 527–552 (2022)
Barenghi, A., Pelosi, G.: A note on fault attacks against deterministic signature schemes. In: Ogawa, K., Yoshioka, K. (eds.) IWSEC 2016. LNCS, vol. 9836, pp. 182–192. Springer, Cham (2016). https://doi.org/10.1007/978-3-319-44524-3_11
Barker, E., Kelsey, J.: Recommendation for random number generation using deterministic random bit generators. Technical report, NIST (2015). https://doi.org/10.6028/NIST.SP.800-90Ar1
Battistello, A., Giraud, C.: Fault analysis of infective AES computations. In: Fischer, W., Schmidt, J.-M. (eds.) FDTC 2013, pp. 101–107. IEEE (2013)
Battistello, A., Giraud, C.: Lost in translation: fault analysis of infective security proofs. In: Homma, N., Lomné, V. (eds.) FDTC 2015, pp. 45–53. IEEE Computer Society (2015)
Battistello, A., Giraud, C.: A note on the security of CHES 2014 symmetric infective countermeasure. In: Standaert, F.-X., Oswald, E. (eds.) COSADE 2016. LNCS, vol. 9689, pp. 144–159. Springer, Cham (2016). https://doi.org/10.1007/978-3-319-43283-0_9
Bauer, S., Drexler, H., Gebhardt, M., Klein, D., Laus, F., Mittmann, J.: Attacks against white-box ECDSA and discussion of countermeasures - a report on the WhibOx contest 2021. Cryptology ePrint Archive, Report 2022/448 (2022). https://ia.cr/2022/448
Bauer, S., Drexler, H., Gebhardt, M., Klein, D., Laus, F., Mittmann, J.: Attacks against white-box ECDSA and discussion of countermeasures a report on the WhibOx contest 2021. IACR Trans. Cryptogr. Hardw. Embed. Syst. 2022(4), 25–55 (2022)
Bellcore: New threat model breaks crypto codes. Press Release (1996)
Bernstein, D.J., Duif, N., Lange, T., Schwabe, P., Yang, B.Y.: High-speed high-security signatures. In: Cryptographic Hardware and Embedded Systems (CHES 2011): 13th International Workshop, Nara, Japan, 28 September–1 October 2011. Proceedings 13, pp. 124–142. Springer, Heidelberg (2011)
Berzati, A., Canovas, C., Goubin, L.: (In)security against fault injection attacks for CRT-RSA implementations. In: Breveglieri, L., Gueron, S., Koren, I., Naccache, D., Seifert, J.-P. (eds.) FDTC 2008, pp. 101–107. IEEE Computer Society (2008)
Biehl, I., Meyer, B., Müller, V.: Differential fault attacks on elliptic curve cryptosystems. In: Bellare, M. (ed.) CRYPTO 2000. LNCS, vol. 1880, pp. 131–146. Springer, Heidelberg (2000). https://doi.org/10.1007/3-540-44598-6_8
Biham, E., Shamir, A.: A new cryptanalytic attack on DES. Manuscrit, Oct. 18 (1996)
Biham, E., Shamir, A.: Differential fault analysis: identifying the structure of unknown ciphers sealed in tamper-proof devices. Manuscrit, Nov. 10 (1996)
Biham, E., Shamir, A.: Differential fault analysis of secret key cryptosystems. In: Kaliski, B.S. (ed.) CRYPTO 1997. LNCS, vol. 1294, pp. 513–525. Springer, Heidelberg (1997). https://doi.org/10.1007/BFb0052259
Blömer, J., Otto, M., Seifert, J.-P.: A new CRT-RSA algorithm secure against Bellcore attacks. In: Jajodia, S., Atluri, V., Jaeger, T. (eds.) ACM CCS 2003, pp. 311–320. ACM Press (2003)
Boneh, D., DeMillo, R.A., Lipton, R.J.: On the importance of checking cryptographic protocols for faults. In: Fumy, W. (ed.) EUROCRYPT 1997. LNCS, vol. 1233, pp. 37–51. Springer, Heidelberg (1997). https://doi.org/10.1007/3-540-69053-0_4
Boneh, D., Venkatesan, R.: Hardness of computing the most significant bits of secret keys in Diffie-Hellman and related schemes. In: Koblitz, N. (ed.) CRYPTO 1996. LNCS, vol. 1109, pp. 129–142. Springer, Heidelberg (1996). https://doi.org/10.1007/3-540-68697-5_11
Breitner, J., Heninger, N.: Biased nonce sense: lattice attacks against weak ECDSA signatures in cryptocurrencies. In: Goldberg, I., Moore, T. (eds.) FC 2019. LNCS, vol. 11598, pp. 3–20. Springer, Cham (2019). https://doi.org/10.1007/978-3-030-32101-7_1
Bruinderink, L.G., Pessl, P.: Differential fault attacks on deterministic lattice signatures. IACR TCHES 2018(3), 21–43 (2018). https://tches.iacr.org/index.php/TCHES/article/view/7267
Cao, W., et al.: Two lattice-based differential fault attacks against ECDSA with wNAF Algorithm. In: Kwon, S., Yun, A. (eds.) ICISC 2015. LNCS, vol. 9558, pp. 297–313. Springer, Cham (2016). https://doi.org/10.1007/978-3-319-30840-1_19
Cao, W., Shi, H., Chen, H., Chen, J., Fan, L., Wu, W.: Lattice-based fault attacks on deterministic signature schemes of ECDSA and EdDSA. In: Galbraith, S.D. (ed.) CT-RSA 2022. LNCS, vol. 13161, pp. 169–195. Springer, Cham (2022). https://doi.org/10.1007/978-3-030-95312-6_8
Ciet, M., Joye, M.: Elliptic curve cryptosystems in the presence of permanent and transient faults. Des. Codes Crypt. 36(1), 33–43 (2005)
T. F. Development Team: fpylll, a Python wraper for the fplll lattice reduction library, Version: 0.4.1 (2018). https://github.com/fplll/fpylll
Dottax, E., Giraud, C., Houzelot, A.: White-box ECDSA: challenges and existing solutions. In: Bhasin, S., De Santis, F. (eds.) COSADE 2021. LNCS, vol. 12910, pp. 184–201. Springer, Cham (2021). https://doi.org/10.1007/978-3-030-89915-8_9
Feix, B., Venelli, A.: Defeating with fault injection a combined attack resistant exponentiation. In: Prouff, E. (ed.) COSADE 2013. LNCS, vol. 7864, pp. 32–45. Springer, Heidelberg (2013). https://doi.org/10.1007/978-3-642-40026-1_3
Feng, J., Chen, H., Li, Y., Jiao, Z., Xi, W.: A framework for evaluation and analysis on infection countermeasures against fault attacks. IEEE Trans. Inf. Forensics Secur. 15, 391–406 (2020)
FIPS PUB 186-5 (Draft). Digital Signature Standard. National Institute of Standards and Technology, Oct. 31 (2019)
Gierlichs, B., Schmidt, J.-M., Tunstall, M.: Infective computation and dummy rounds: fault protection for block ciphers without check-before-output. In: Hevia, A., Neven, G. (eds.) LATINCRYPT 2012. LNCS, vol. 7533, pp. 305–321. Springer, Heidelberg (2012). https://doi.org/10.1007/978-3-642-33481-8_17
Giraud, C.: DFA on AES. In: Dobbertin, H., Rijmen, V., Sowa, A. (eds.) AES 2004. LNCS, vol. 3373, pp. 27–41. Springer, Heidelberg (2005). https://doi.org/10.1007/11506447_4
Giraud, C., Knudsen, E.W.: Fault attacks on signature schemes. In: Wang, H., Pieprzyk, J., Varadharajan, V. (eds.) ACISP 2004. LNCS, vol. 3108, pp. 478–491. Springer, Heidelberg (2004). https://doi.org/10.1007/978-3-540-27800-9_41
Giraud, C., Knudsen, E.W., Tunstall, M.: Improved fault analysis of signature schemes. In: Gollmann, D., Lanet, J.-L., Iguchi-Cartigny, J. (eds.) CARDIS 2010. LNCS, vol. 6035, pp. 164–181. Springer, Heidelberg (2010). https://doi.org/10.1007/978-3-642-12510-2_12
Giraud, C., Thiebeauld, H.: A survey on fault attacks. In: Quisquater, J.-J., Paradinas, P., Deswarte, Y., El Kalam, A.A. (eds.) CARDIS 2004. IIFIP, vol. 153, pp. 159–176. Springer, Boston, MA (2004). https://doi.org/10.1007/1-4020-8147-2_11
Jancar, J., Sedlacek, V., Svenda, P., Sys, M.: Minerva: the curse of ECDSA nonces. In: IACR Transactions on Cryptographic Hardware and Embedded Systems, pp. 281–308 (2020)
Joye, M., Quisquater, J.-J.: Attacks on systems using Chinese remaindering. Technical Report CG-1996/9, UCL (1996). http://www.dice.ucl.ac.be/crypto/techreports.html
Lenstra, A.: Memo on RSA signature generation in the presence of faults. Manuscript (1996). http://cm.bell-labs.com/who/akl/rsa.doc
Lenstra, A.K., Lenstra, H.W., Lovasz, L.: Factoring polynomials with rational coefficients. Math. Ann. 261, 515–534 (1982)
Lomné, V., Roche, T., Thillard, A.: On the need of randomness in fault attack countermeasures - application to AES. In: Bertoni, G., Gierlichs, B. (eds.) FDTC 2012, pp. 85–94. IEEE Computer Society (2012)
Naccache, D., Nguyên, P.Q., Tunstall, M., Whelan, C.: Experimenting with faults, lattices and the DSA. In: Vaudenay, S. (ed.) PKC 2005. LNCS, vol. 3386, pp. 16–28. Springer, Heidelberg (2005). https://doi.org/10.1007/978-3-540-30580-4_3
Nguyen, P.Q., Shparlinski, I.: The insecurity of the digital signature algorithm with partially known nonces. J. Cryptol. 15(3), 151–176 (2002). https://doi.org/10.1007/s00145-002-0021-3
Nguyen, P.Q., Shparlinski, I.E.: The insecurity of the elliptic curve digital signature algorithm with partially known nonces. Des. Codes Cryptogr. 30(2), 201–217 (2003). https://doi.org/10.1023/A:1025436905711
Nguyen, P.Q., Tibouchi, M.: Lattice-based fault attacks on signatures. In: Joye, M., Tunstall, M. (eds.) Fault Analysis in Cryptography. ISC, pp. 201–220. Springer, Heidelberg (2012). https://doi.org/10.1007/978-3-642-29656-7_12
Piret, G., Quisquater, J.-J.: A differential fault attack technique against SPN structures, with application to the AES and Khazad. In: Walter, C.D., Koç, Ç.K., Paar, C. (eds.) CHES 2003. LNCS, vol. 2779, pp. 77–88. Springer, Heidelberg (2003). https://doi.org/10.1007/978-3-540-45238-6_7
Poddebniak, D., Somorovsky, J., Schinzel, S., Lochter, M., Rösler, P.: Attacking deterministic signature schemes using fault attacks. In: EuroS &P 2018, pp. 338–352. IEEE (2018)
Pornin, T.: Deterministic usage of the digital signature algorithm (DSA) and elliptic curve digital signature algorithm (ECDSA). RFC 6979 (2013). https://www.rfc-editor.org/info/rfc6979
Quisquater, J.-J.: Short cut for exhaustive search using fault analysis: applications to DES, MAC, keyed hash function, identification protocols, ... Manuscrit Oct. 23 (1996)
Rauzy, P., Guilley, S.: Countermeasures against high-order fault-injection attacks on CRT-RSA. In: Tria, A., Choi, D. (eds.) FDTC 2014, pp. 68–82. IEEE Computer Society (2014)
Rivain, M.: Differential fault analysis on DES middle rounds. In: Clavier, C., Gaj, K. (eds.) CHES 2009. LNCS, vol. 5747, pp. 457–469. Springer, Heidelberg (2009). https://doi.org/10.1007/978-3-642-04138-9_32
Roche, T., Lomné, V., Mutschler, C., Imbert, L.: A side journey to Titan. In: Bailey, M., Greenstadt, R. (eds.) USENIX Security 2021, pp. 231–248. USENIX Association (2021)
Romailler, Y., Pelissier, S.: Practical fault attack against the Ed25519 and EdDSA signature schemes. In: FDTC 2017, pp. 17–24. IEEE Computer Society (2017)
Samwel, N., Batina, L.: Practical fault injection on deterministic signatures: the case of EdDSA. In: Joux, A., Nitaj, A., Rachidi, T. (eds.) AFRICACRYPT 2018. LNCS, vol. 10831, pp. 306–321. Springer, Cham (2018). https://doi.org/10.1007/978-3-319-89339-6_17
Schmidt, J., Medwed, M.: A fault attack on ECDSA. In: Breveglieri, L., Koren, I., Naccache, D., Oswald, E., Seifert, J. (eds.) FDTC 2009, pp. 93–99. IEEE Computer Society (2009)
Schmidt, J.-M., Tunstall, M., Avanzi, R., Kizhvatov, I., Kasper, T., Oswald, D.: Combined implementation attack resistant exponentiation. In: Abdalla, M., Barreto, P.S.L.M. (eds.) LATINCRYPT 2010. LNCS, vol. 6212, pp. 305–322. Springer, Heidelberg (2010). https://doi.org/10.1007/978-3-642-14712-8_19
Schnorr, C.P., Euchner, M.: Lattice basis reduction: improved practical algorithms and solving subset sum problems. In: Budach, L. (ed.) FCT 1991. LNCS, vol. 529, pp. 68–85. Springer, Heidelberg (1991). https://doi.org/10.1007/3-540-54458-5_51
Sun, C., Espitau, T., Tibouchi, M., Abe, M.: Guessing bits: improved lattice attacks on (EC)DSA with nonce leakage. IACR Trans. Cryptographic Hardware Embed. Syst. 2022(1), 391–413 (2022)
Tupsamudre, H., Bisht, S., Mukhopadhyay, D.: Destroying fault invariant with randomization. In: Batina, L., Robshaw, M. (eds.) CHES 2014. LNCS, vol. 8731, pp. 93–111. Springer, Heidelberg (2014). https://doi.org/10.1007/978-3-662-44709-3_6
Vanstone, S.: Responses to NIST’s proposal. Commun. ACM 35, 50–52 (1992)
Wagner, D.: Cryptanalysis of a provably secure CRT-RSA algorithm. In: Atluri, V., Pfitzmann, B., McDaniel, P. (eds.) ACM CCS 2004, pp. 92–97. ACM Press (2004)
Yen, S.-M., Kim, D., Moon, S.J.: Cryptanalysis of two protocols for RSA with CRT based on fault infection. In: Breveglieri, L., Koren, I., Naccache, D., Seifert, J.-P. (eds.) FDTC 2006. LNCS, vol. 4236, pp. 53–61. Springer, Heidelberg (2006). https://doi.org/10.1007/11889700_5
Sung-Ming, Y., Kim, S., Lim, S., Moon, S.: RSA speedup with residue number system immune against hardware fault cryptanalysis. In: Kim, K. (ed.) ICISC 2001. LNCS, vol. 2288, pp. 397–413. Springer, Heidelberg (2002). https://doi.org/10.1007/3-540-45861-1_30
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
More Experimental Results
More Experimental Results
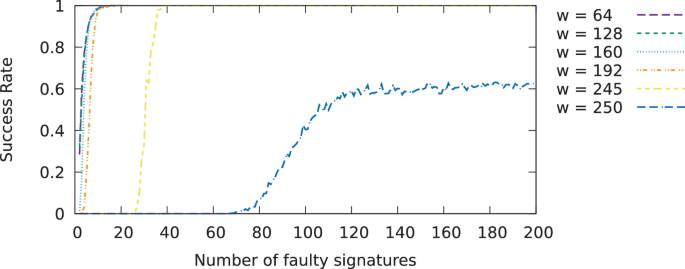
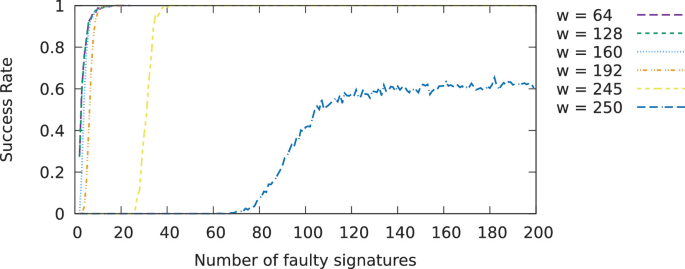
We give below the experimental results for the all the attacks described in Sect. 3 and Sect. 4 (Figs. 7, 8, 9, 10, 11 and 12).
Success rate of the lattice-based FA on dECDSA protected with the infective scheme of [30] – Attack 2.
Success rate of the lattice-based FA on dECDSA protected with the infective scheme of [30] – Attack 3.1.
Success rate of the lattice-based FA on dECDSA protected with the infective scheme of [30] – Attack 3.2.
Success rate of the lattice-based FA on dECDSA protected with the infective scheme of [30] – Attack 4.1.
Success rate of the lattice-based FA on dECDSA protected with the infective scheme of [30] – Attack 4.2.
Success rate of the lattice-based FA on EdDSA protected with the infective scheme of [30] – Attack 2.
Rights and permissions
Copyright information
© 2023 The Author(s), under exclusive license to Springer Nature Switzerland AG
About this paper
Cite this paper
Barbu, G., Giraud, C. (2023). All Shall FA-LLL: Breaking CT-RSA 2022 and CHES 2022 Infective Countermeasures with Lattice-Based Fault Attacks. In: Rosulek, M. (eds) Topics in Cryptology – CT-RSA 2023. CT-RSA 2023. Lecture Notes in Computer Science, vol 13871. Springer, Cham. https://doi.org/10.1007/978-3-031-30872-7_17
Download citation
DOI: https://doi.org/10.1007/978-3-031-30872-7_17
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-031-30871-0
Online ISBN: 978-3-031-30872-7
eBook Packages: Computer ScienceComputer Science (R0)