Abstract
Recovering superpoly for a given cube is the key step in cube attacks - an algebraic cryptanalysis method for symmetric ciphers. Since 2015, division property, monomial prediction, and enhanced techniques have been proposed to recover the exact superpoly by converting the problem into Mixed Integer Linear Programming (MILP) model, whose feasible solutions should be enumerated exactly. To penetrate more rounds, cryptanalysts try their best to reduce the scale of deduced MILP model to alleviate the bottleneck of computational cost for solving the model. In this paper, we investigate the graph-based modeling approach proposed in SAC 2021 to further reduce the number of feasible solutions for the model to handle and reduce the model’s scale in cube attacks on Trivium. Specifically, we develop an algorithm to search for pruning patterns and reveal a budget way to add the constraints concerning pruning patterns, thus eliminating a large number of solutions by adding fewer additional constraints. Under our measurement method, the pruning efficiency of added constraints is improved by 7 to 10 times more effective than in previous work. We also embed this modified graph-based model to the nested superpoly recovery framework proposed in ASIACRYPT 2021 and improve graph-based cube attack on Trivium by one round. The improved graph-based model performs better than monomial prediction with nested framework on 842- and 843-round cube attack of Trivium.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
Notes
- 1.
- 2.
Our work is parallel to an improvement of the monomial prediction in ASIACRYPT 2022 [9]. We leave the comparison with the latter for future work.
References
Bao, Z., et al.: Automatic search of meet-in-the-middle preimage attacks on AES-like hashing. In: Canteaut, A., Standaert, F.-X. (eds.) EUROCRYPT 2021. LNCS, vol. 12696, pp. 771–804. Springer, Cham (2021). https://doi.org/10.1007/978-3-030-77870-5_27
Cannière, C.D., Preneel, B.: Trivium. In: Robshaw, M., Billet, O. (eds.) New Stream Cipher Designs. LNCS, vol. 4986, pp. 244–266. Springer, Berlin, Heidelberg (2008). https://doi.org/10.1007/978-3-540-68351-3_18
Canteaut, A., et al.: Stream ciphers: a practical solution for efficient homomorphic-ciphertext compression. J. Cryptol. 31(3), 885–916 (2018)
Delaune, S., Derbez, P., Gontier, A., Prud’homme, C.: A simpler model for recovering superpoly on Trivium. In: AlTawy, R., Hülsing, A. (eds.) SAC 2021. LNCS, vol. 13203, pp. 266–285. Springer, Cham (2022). https://doi.org/10.1007/978-3-030-99277-4_13
Dinur, I., Shamir, A.: Cube attacks on tweakable black box polynomials. In: Joux, A. (ed.) EUROCRYPT 2009. LNCS, vol. 5479, pp. 278–299. Springer, Heidelberg (2009). https://doi.org/10.1007/978-3-642-01001-9_16
Dong, X., Zhang, Z., Sun, S., Wei, C., Wang, X., Hu, L.: Automatic classical and quantum rebound attacks on AES-like hashing by exploiting related-key differentials. In: Tibouchi, M., Wang, H. (eds.) ASIACRYPT 2021. LNCS, vol. 13090, pp. 241–271. Springer, Cham (2021). https://doi.org/10.1007/978-3-030-92062-3_9
Gurobi Optimization, LLC: Gurobi Optimizer Reference Manual (2022). https://www.gurobi.com
Hao, Y., Leander, G., Meier, W., Todo, Y., Wang, Q.: Modeling for three-subset division property without unknown subset. In: Canteaut, A., Ishai, Y. (eds.) EUROCRYPT 2020. LNCS, vol. 12105, pp. 466–495. Springer, Cham (2020). https://doi.org/10.1007/978-3-030-45721-1_17
He, J., Hu, K., Preneel, B., Wang, M.: Stretching cube attacks: improved methods to recover massive superpolies. In: Agrawal, S., Lin, D. (eds.) Advances in Cryptology – ASIACRYPT 2022. ASIACRYPT 2022. LNCS, vol. 13794, pp. 537–566. Springer, Cham (2022). https://doi.org/10.1007/978-3-031-22972-5_19
Hell, M., Johansson, T., Maximov, A., Meier, W., Sönnerup, J., Yoshida, H.: Grain-128AEADv2-A lightweight AEAD stream cipher. NIST Lightweight Cryptography, Finalists (2021)
Hu, K., Sun, S., Todo, Y., Wang, M., Wang, Q.: Massive superpoly recovery with nested monomial predictions. In: Tibouchi, M., Wang, H. (eds.) ASIACRYPT 2021. LNCS, vol. 13090, pp. 392–421. Springer, Cham (2021). https://doi.org/10.1007/978-3-030-92062-3_14
Hu, K., Sun, S., Wang, M., Wang, Q.: An algebraic formulation of the division property: revisiting degree evaluations, cube attacks, and key-independent sums. In: Moriai, S., Wang, H. (eds.) ASIACRYPT 2020. LNCS, vol. 12491, pp. 446–476. Springer, Cham (2020). https://doi.org/10.1007/978-3-030-64837-4_15
Knudsen, L., Wagner, D.: Integral cryptanalysis. In: Daemen, J., Rijmen, V. (eds.) FSE 2002. LNCS, vol. 2365, pp. 112–127. Springer, Heidelberg (2002). https://doi.org/10.1007/3-540-45661-9_9
Mroczkowski, P., Szmidt, J.: The cube attack on stream cipher Trivium and quadraticity tests. Fund. Inform. 114(3–4), 309–318 (2012)
Sasaki, Yu., Todo, Y.: New impossible differential search tool from design and cryptanalysis aspects. In: Coron, J.-S., Nielsen, J.B. (eds.) EUROCRYPT 2017. LNCS, vol. 10212, pp. 185–215. Springer, Cham (2017). https://doi.org/10.1007/978-3-319-56617-7_7
Shi, D., Sun, S., Derbez, P., Todo, Y., Sun, B., Hu, L.: Programming the Demirci-Selçuk meet-in-the-middle attack with constraints. In: Peyrin, T., Galbraith, S. (eds.) ASIACRYPT 2018. LNCS, vol. 11273, pp. 3–34. Springer, Cham (2018). https://doi.org/10.1007/978-3-030-03329-3_1
Sun, S., et al.: Towards finding the best characteristics of some bit-oriented block ciphers and automatic enumeration of (related-key) differential and linear characteristics with predefined properties. Cryptology ePrint Archive, Report 2014/747 (2014). https://eprint.iacr.org/2014/747
Todo, Y.: Structural evaluation by generalized integral property. In: Oswald, E., Fischlin, M. (eds.) EUROCRYPT 2015. LNCS, vol. 9056, pp. 287–314. Springer, Heidelberg (2015). https://doi.org/10.1007/978-3-662-46800-5_12
Todo, Y., Isobe, T., Hao, Y., Meier, W.: Cube attacks on non-blackbox polynomials based on division property. In: Katz, J., Shacham, H. (eds.) CRYPTO 2017. LNCS, vol. 10403, pp. 250–279. Springer, Cham (2017). https://doi.org/10.1007/978-3-319-63697-9_9
Wang, J., Wu, B., Liu, Z.: Improved degree evaluation and superpoly recovery methods with application to trivium. arXiv preprint arXiv:2201.06394 (2022)
Wang, Q., Hao, Y., Todo, Y., Li, C., Isobe, T., Meier, W.: Improved division property based cube attacks exploiting algebraic properties of superpoly. In: Shacham, H., Boldyreva, A. (eds.) CRYPTO 2018. LNCS, vol. 10991, pp. 275–305. Springer, Cham (2018). https://doi.org/10.1007/978-3-319-96884-1_10
Wang, S., Hu, B., Guan, J., Zhang, K., Shi, T.: MILP-aided method of searching division property using three subsets and applications. In: Galbraith, S.D., Moriai, S. (eds.) ASIACRYPT 2019. LNCS, vol. 11923, pp. 398–427. Springer, Cham (2019). https://doi.org/10.1007/978-3-030-34618-8_14
Xiang, Z., Zhang, W., Bao, Z., Lin, D.: Applying MILP method to searching integral distinguishers based on division property for 6 lightweight block ciphers. In: Cheon, J.H., Takagi, T. (eds.) ASIACRYPT 2016. LNCS, vol. 10031, pp. 648–678. Springer, Heidelberg (2016). https://doi.org/10.1007/978-3-662-53887-6_24
Ye, C.D., Tian, T.: Revisit division property based cube attacks: key-recovery or distinguishing attacks? IACR Trans. Symmetric Cryptol. 2019(3), 81–102 (2019). https://tosc.iacr.org/index.php/ToSC/article/view/8358
Ye, C.D., Tian, T.: Algebraic method to recover superpolies in cube attacks. IET Inf. Secur. 14(4), 430–441 (2020)
Ye, C.-D., Tian, T.: A practical key-recovery attack on 805-round trivium. In: Tibouchi, M., Wang, H. (eds.) ASIACRYPT 2021. LNCS, vol. 13090, pp. 187–213. Springer, Cham (2021). https://doi.org/10.1007/978-3-030-92062-3_7
Ye, C., Tian, T.: A new framework for finding nonlinear superpolies in cube attacks against trivium-like ciphers. In: Susilo, W., Yang, G. (eds.) ACISP 2018. LNCS, vol. 10946, pp. 172–187. Springer, Cham (2018). https://doi.org/10.1007/978-3-319-93638-3_11
Acknowledgment
We thank the anonymous reviewers for their insightful comments in improving the quality of this paper. This research was funded by National Natural Science Foundation of China (grant number 62102025), Beijing Natural Science Foundation (grant number 4222035), Beijing Institute of Technology Research Fund Program for Young Scholars (grant number XSQD-202024003), and the Open Project Program of the State Key Laboratory of Cryptology.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Appendices
A Discussion About Delaune et al. ’s Work
1.1 A.1 Pruning Patterns
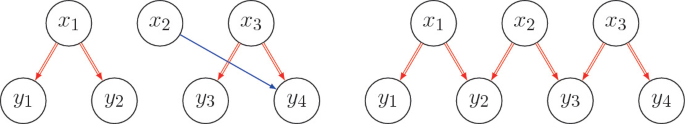
Delaune et al. [4] presented four pruning patterns but they only apply the three consecutive bits pattern shown in Fig. 9 in the MILP model. The nodes and edges in Fig. 9 can be described as :
-
\(V = \{x_1, x_2, x_3, y_1, y_2, y_3, y_4\}\),
-
\(E = \{\langle x_1, y_1 \rangle , \langle x_1, y_2 \rangle , \langle x_2, y_2 \rangle , \langle x_2, y_3 \rangle , \langle x_2, y_4 \rangle , \langle x_3, y_3 \rangle , \langle x_3, y_4 \rangle \}\).
In Fig. 9, three adjacent nodes in register C point to four adjacent nodes in B through the long edge and red edges. If the left subgraph of Fig. 9 appears as a part of a trail \(\mathcal {T}\), the right subgraph must appear in the same part in another trail \(\mathcal {T}'\) that indicates the same monomial with \(\mathcal {T}\). So we can utilize extra constraints to discard both \(\mathcal {T}\) and \(\mathcal {T}'\).
Since the equality of doubling edges, we can simplify the E as:
-
\(E = \{\langle x_1, y_2 \rangle , \langle x_2, y_2 \rangle , \langle x_2, y_4 \rangle , \langle x_3, y_4 \rangle \}\).
Let \(X_{(x, y)} \in \{0, 1\}\) be the indicator variable for whether an edge from x to y appears in a trail. Then, by imposing
the two patterns Fig. 9 are eliminated simultaneously.
However, if the constraint in Eq. (11) is imposed on consecutive bits odd number of trails will be eliminated which is disastrous for recovering the exact ANF of superpoly. Figure 10 shows a situation that when the constraint is imposed on two consecutive groups of nodes (indicated by red shade and green shade respectively), three trails are eliminated. The reason is that when all 9 nodes are active in a feasible trail and \(x_4\) takes the quadratic term edges, subgraphs eliminated by the first inequation and the second inequation have an intersection - subfigure denoted by  . A more complex example that involves 11 nodes is given in Fig 11. The solution of Delaune et al. is to enable the intersection pattern to be feasible. Accordingly, the constraint should be modified to
. A more complex example that involves 11 nodes is given in Fig 11. The solution of Delaune et al. is to enable the intersection pattern to be feasible. Accordingly, the constraint should be modified to
The modified constraint will retain subgraphs denoted by  .
.
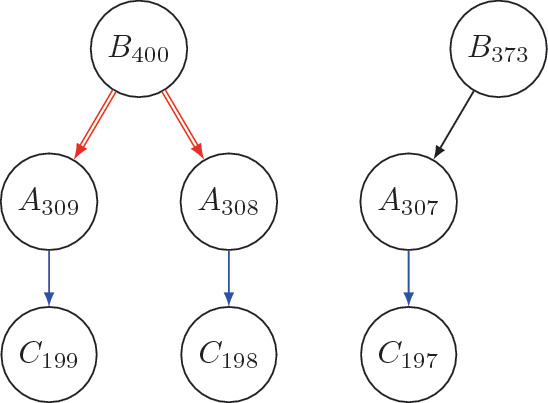
1.2 A.2 Discussion on Patterns with 3 Layers
Delaune mentioned that they faced many problems while coding the four pruning patterns and decided to take pattern 2 (the three consecutive bits pattern) only. They also mentioned that we have to take care \(A_{309}\), \(A_{308}\), and \(A_{307}\) in Fig. 12 are not used in any other part of the trail. Once the intermediate nodes are used, we may cut odd number of trails. We show an example in Fig. 13 to explain the problem in more detail. The right part of Fig. 12 will never work if the edge \(\langle A_{307}, C_{197} \rangle \) must be activated. That means this pattern can only prune odd trails but not even.
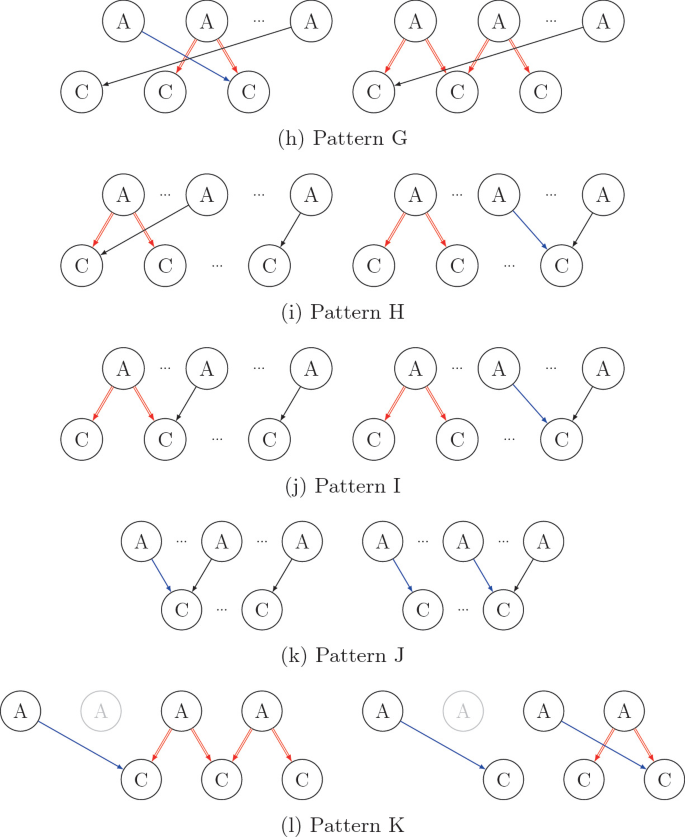
B 2-Layer Patterns Discovered
Figure 14 shows all 2-layer patterns discovered by Algorithm 2. We label these patterns with A through K, except for 3CBP, which is the same as Pattern 2 in [4].
C Data About All Patterns on 839- to 841-Round Cube Attack
(See Table 3).
Rights and permissions
Copyright information
© 2023 The Author(s), under exclusive license to Springer Nature Switzerland AG
About this paper
Cite this paper
Cheng, J., Qiao, K. (2023). Improved Graph-Based Model for Recovering Superpoly on Trivium. In: Rosulek, M. (eds) Topics in Cryptology – CT-RSA 2023. CT-RSA 2023. Lecture Notes in Computer Science, vol 13871. Springer, Cham. https://doi.org/10.1007/978-3-031-30872-7_9
Download citation
DOI: https://doi.org/10.1007/978-3-031-30872-7_9
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-031-30871-0
Online ISBN: 978-3-031-30872-7
eBook Packages: Computer ScienceComputer Science (R0)