Abstract
Fully Homomorphic Encryption schemes (FHEs) and Functional Encryption schemes (FunctEs) have a tremendousimpact in cryptography both for the natural questions that they address and for the wide range of applications in which they have been (sometimes critically) used.
In this work we put forth the notion of a Controllable Homomorphic Encryption scheme (CHES), a new primitive that includes features of both FHEs and FunctEs. In a CHES it is possible (similarly to a FHE) to homomorphically evaluate a ciphertext \(\mathsf{Ct}=\mathsf{Enc}(m)\) and a circuit C therefore obtaining \(\mathsf{Enc}(C(m))\) but only if (similarly to a FunctE) a token for C has been received from the owner of the secret key.
We discuss difficulties in constructing a CHES and then show a construction based on any FunctE.
As a byproduct our CHES also represents a FunctE supporting the re-encryption functionality and in that respect improves existing solutions.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
Notes
- 1.
- 2.
The use of a PRF is needed to allow the use of more than one token for the same ciphertext; otherwise, a simple encryption of C(m) concatenated to R would be sufficient.
- 3.
Note that during the course of this work, we often use the term game when we actually mean a distribution.
- 4.
In the proof, we give details of the impact of the transformation of Sect. 2 in case \({\mathsf {F}}{\mathsf {E}}\) is re-randomizable.
References
Agrawal, S., Gorbunov, S., Vaikuntanathan, V., Wee, H.: Functional encryption: new perspectives and lower bounds. In: Canetti, R., Garay, J.A. (eds.) CRYPTO 2013. LNCS, vol. 8043, pp. 500–518. Springer, Heidelberg (2013). https://doi.org/10.1007/978-3-642-40084-1_28
Alwen, J., Barbosa, M., Farshim, P., Gennaro, R., Gordon, S.D., Tessaro, S., Wilson, D.A.: On the relationship between functional encryption, obfuscation, and fully homomorphic encryption. In: Stam, M. (ed.) IMACC 2013. LNCS, vol. 8308, pp. 65–84. Springer, Heidelberg (2013). https://doi.org/10.1007/978-3-642-45239-0_5
Barbosa, M., Farshim, P.: Delegatable homomorphic encryption with applications to secure outsourcing of computation. In: Dunkelman, O. (ed.) CT-RSA 2012. LNCS, vol. 7178, pp. 296–312. Springer, Heidelberg (2012). https://doi.org/10.1007/978-3-642-27954-6_19
Boneh, D., Sahai, A., Waters, B.: Functional encryption: definitions and challenges. In: Ishai, Y. (ed.) TCC 2011. LNCS, vol. 6597, pp. 253–273. Springer, Heidelberg (2011). https://doi.org/10.1007/978-3-642-19571-6_16
Boneh, D., Segev, G., Waters, B.: Targeted malleability: homomorphic encryption for restricted computations. In: ITCS, pp. 350–366 (2012)
Boyle, E., Chung, K.-M., Pass, R.: On extractability obfuscation. In: Lindell, Y. (ed.) TCC 2014. LNCS, vol. 8349, pp. 52–73. Springer, Heidelberg (2014). https://doi.org/10.1007/978-3-642-54242-8_3
Brakerski, Z., Gentry, C., Vaikuntanathan, V.: (Leveled) fully homomorphic encryption without bootstrapping. In: ITCS, pp. 309–325 (2012)
Brakerski, Z., Vaikuntanathan, V.: Efficient fully homomorphic encryption from (Standard) LWE. In: FOCS, pp. 97–106 (2011)
De Caro, A., Iovino, V.: On the power of rewinding simulators in functional encryption. Des. Codes Crypt. 84, 1–27 (2016)
De Caro, A., Iovino, V., Jain, A., O’Neill, A., Paneth, O., Persiano, G.: On the achievability of simulation-based security for functional encryption. In: Canetti, R., Garay, J.A. (eds.) CRYPTO 2013. LNCS, vol. 8043, pp. 519–535. Springer, Heidelberg (2013). https://doi.org/10.1007/978-3-642-40084-1_29
Desmedt, Y.: Computer security by redefining what a computer is. In: Proceedings on the 1992–1993 Workshop on New Security Paradigms, NSPW 1992–1993, pp. 160–166. ACM, New York (1993)
Dolev, D., Dwork, C., Naor, M.: Non-malleable cryptography. In: 23rd Annual ACM Symposium on Theory of Computing, New Orleans, Louisiana, USA, 6–8 May 1991, pp. 542–552. ACM Press (1991)
Garg, S., Gentry, C., Halevi, S., Raykova, M., Sahai, A., Waters, B.: Candidate indistinguishability obfuscation and functional encryption for all circuits. In: 54th Annual IEEE Symposium on Foundations of Computer Science, FOCS 2013, Berkeley, CA, USA, October 26–29 2013, pp. 40–49. IEEE Computer Society (2013)
Garg, S., Gentry, C., Halevi, S., Zhandry, M.: Functional encryption without obfuscation. In: Kushilevitz, E., Malkin, T. (eds.) TCC 2016. LNCS, vol. 9563, pp. 480–511. Springer, Heidelberg (2016). https://doi.org/10.1007/978-3-662-49099-0_18
Gentry, C.: A fully homomorphic encryption scheme. Ph.D. thesis, Stanford University (2009). crypto.stanford.edu/craig
Gentry, C.: Fully homomorphic encryption using ideal lattices. In: Mitzenmacher, M. (ed.) 41st Annual ACM Symposium on Theory of Computing, Bethesda, Maryland, USA, 31 May–2 June 2009, pp. 169–178. ACM Press (2009)
Gorbunov, S., Vaikuntanathan, V., Wee, H.: Functional encryption with bounded collusions via multi-party computation. In: Safavi-Naini, R., Canetti, R. (eds.) CRYPTO 2012. LNCS, vol. 7417, pp. 162–179. Springer, Heidelberg (2012). https://doi.org/10.1007/978-3-642-32009-5_11
Goyal, V., Jain, A., Koppula, V., Sahai, A.: Functional encryption for randomized functionalities. In: Dodis, Y., Nielsen, J.B. (eds.) TCC 2015. LNCS, vol. 9015, pp. 325–351. Springer, Heidelberg (2015). https://doi.org/10.1007/978-3-662-46497-7_13
Iovino, V., Żebroski, K.: Simulation-based secure functional encryption in the random oracle model. In: Lauter, K., Rodríguez-Henríquez, F. (eds.) LATINCRYPT 2015. LNCS, vol. 9230, pp. 21–39. Springer, Cham (2015). https://doi.org/10.1007/978-3-319-22174-8_2
Naor, M.: On cryptographic assumptions and challenges. In: Boneh, D. (ed.) CRYPTO 2003. LNCS, vol. 2729, pp. 96–109. Springer, Heidelberg (2003). https://doi.org/10.1007/978-3-540-45146-4_6
Pass, R., Shelat, A., Vaikuntanathan, V.: Construction of a non-malleable encryption scheme from any semantically secure one. In: Dwork, C. (ed.) CRYPTO 2006. LNCS, vol. 4117, pp. 271–289. Springer, Heidelberg (2006). https://doi.org/10.1007/11818175_16
Waters, B.: A punctured programming approach to adaptively secure functional encryption. In: Gennaro, R., Robshaw, M. (eds.) CRYPTO 2015. LNCS, vol. 9216, pp. 678–697. Springer, Heidelberg (2015). https://doi.org/10.1007/978-3-662-48000-7_33
Acknowledgements
Vincenzo Iovino is supported by a FNR CORE grant (no. FNR11299247) of the Luxembourg National Research Fund. Part of this work was done while Vincenzo Iovino was at the University of Warsaw and was supported by the WELCOME/2010-4/2 grant funded within the framework of the EU Innovative Economy Operational Programme. Ivan Visconti was supported in part by “GNCS - INdAM” and EU COST Action IC1306.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Appendices
A Syntax and Security of Functional Encryption for Circuits
Definition 3
( FE4C : Functional Encryption Scheme for Circuits). A Functional Encryption scheme for Circuits is a tuple \({\mathsf {F}}{\mathsf {E}}=({\mathsf {F}}{\mathsf {E}}.\mathsf{Setup},{\mathsf {F}}{\mathsf {E}}.\mathsf{KeyGen},{\mathsf {F}}{\mathsf {E}}.\mathsf{Enc},{\mathsf {F}}{\mathsf {E}}.\mathsf{Eval})\) of 4 efficient algorithms with the following syntax:
-
1.
\({\mathsf {F}}{\mathsf {E}}.\mathsf{Setup}(1^\lambda ,1^n)\) outputs public and master secret keys \((\mathsf{Pk},\mathsf{Msk})\) for security parameter \(\lambda \) and length parameter n.
-
2.
\({\mathsf {F}}{\mathsf {E}}.\mathsf{KeyGen}(\mathsf{Msk},C)\), on input a master secret key \(\mathsf{Msk}\) for length parameter n and an n-bit input and n-bit output circuit C, outputs token \(\mathtt{Tok}_{C}\).
-
3.
\({\mathsf {F}}{\mathsf {E}}.\mathsf{Enc}(\mathsf{Pk},M)\), on input public key \(\mathsf{Pk}\) for length parameter n and plaintext \(M\in \{0,1\}^n\), outputs ciphertext \(\mathsf{Ct}\).
-
4.
\({\mathsf {F}}{\mathsf {E}}.\mathsf{Eval}(\mathsf{Pk},\mathsf{Ct},\mathtt{Tok})\) outputs \(B\in \{0,1\}^n\cup \{\perp \}\).
For the correctness condition we require that for all n-bit input and n-bit output circuits C, all \(M\in \{0,1\}^n\), and for \((\mathsf{Pk},\mathsf{Msk})\leftarrow \mathsf{Setup}(1^\lambda ,1^n)\), \(\mathtt{Tok}\leftarrow \mathsf{KeyGen}(\mathsf{Msk},C)\) and \(\mathsf{Ct}\leftarrow \mathsf{Enc}(\mathsf{Pk},M)\), the probability that \(\mathsf{Eval}(\mathsf{Pk},\mathsf{Ct},\mathtt{Tok})\ne C(M)\) is negligible in \(\lambda \).
We formalize security for a FE4C \({\mathsf {F}}{\mathsf {E}}\) by means of the following game \({\textsc {FE-}\textsc {IndCPA}\textsc {-Game}}\) between a challenger \({{\mathcal {F}}}{{\mathcal {E}}}.{\mathcal {C}}\) and an adversary \(\mathcal{A}\) that can issue two types of queries to \({{\mathcal {F}}}{{\mathcal {E}}}.{\mathcal {C}}\), encryption queries and token queries. The definition is essentially the one in [4].

Definition 4
We say that a \({FE4C}\) \({\mathsf {F}}{\mathsf {E}}\) is IND-CPA secure if for all PPT adversaries \(\mathcal{A}\) there exists a negligible function \(\mu \) such that
Tag-Based Non-rerandomizable Functional Encryption. In our main construction we use a special type of FE4C in which ciphertexts cannot be re-randomized. More precisely, we consider tag-based FE4C in which the encryption algorithm for n-bit plaintext m and security parameter \(\lambda \) takes two extra arguments: a tag \(\tau \) from the set \(T_{\lambda }\) of \(\lambda \)-bit tags and an auxiliary message of length \(n_1\). It is easy to see how any FE4C can be modified to accommodate tags and auxiliary messages at the expenses of increasing the length parameter n. In a non-rerandomizable tag-based FE4C, given a ciphertext for an adversarially chosen plaintext m and auxiliary message \({\mathsf {aux}}\) and a random tag \(\tau \), no adversary can produce another ciphertext for the same plaintext m and the same tag. Specifically, we consider the following security game between a challenger \({{\mathcal {F}}}{{\mathcal {E}}}.{\mathcal {C}}\) and and adversary \(\mathcal{A}\) that can issue one single encryption query.
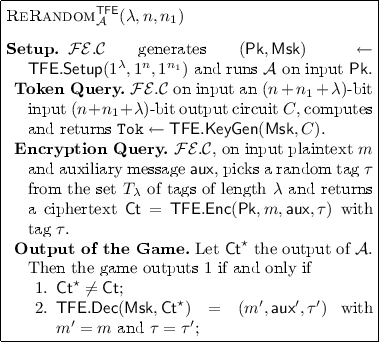
We say that a tag-based FE4C \({\mathsf T}{\mathsf {F}}{\mathsf {E}}\) is non-rerandomizable if for all PPT adversaries \(\mathcal{A}\) and for n and \(n_1\) polynomially bounded in \(\lambda \) there exists a negligible function \(\mu \) such that
It is easy to see that any tag-based FE4C can be transformed into a non-rerandomizable one by using a secure signature scheme. More precisely, we define the encryption algorithm \({\mathsf T}{\mathsf {F}}{\mathsf {E}}.\mathsf{Enc}\) that encrypts plaintext m and \({\mathsf {aux}}\), to pick a random pair of \((\mathsf{vk},\mathsf{sgk})\) of verification and signing key for a secure signature scheme \(({\mathsf {Sig}\mathsf{KeyGen}},{\mathsf {Sign}},{\mathsf {Verify}})\) and \(m,{\mathsf {aux}}\) are encrypted using \(\mathsf{vk}\) as tag obtaining \(\mathsf{Ct}\). Finally, a signature \(\sigma _\mathsf{Ct}\) of \(\mathsf{Ct}\) is computed using the signing key \(\mathsf{sgk}\) and the resulting ciphertext consists of the pair \((\mathsf{Ct},\sigma _\mathsf{Ct})\). Tokens for function C on ciphertext \((\mathsf{Ct},\sigma _\mathsf{Ct})\) first verify \(\sigma _\mathsf{Ct}\) and, if successful, proceed to compute \(C(m,{\mathsf {aux}})\). We observe that \(\mathcal{A}\) either changes the verification key (and thus changes the tag) or keeps the same verification key but then it has to sign a new ciphertext or compute a new signature (which would violate the security of the signature scheme).
B IND-CPA CHES
IND-CPA security of a CHESWe formalize the notion of security equivalent to IND-CPA for a CHES \(\mathsf {CHE}=(\mathsf {CHE}.\mathsf{Setup},\mathsf {CHE}.\mathsf{KeyGen},\mathsf {CHE}.\mathsf{Enc},\mathsf {CHE}.\mathsf{H}{\mathsf{Eval}},\mathsf {CHE}.\mathsf{Dec})\) by means of game CHES- IndCPA -Game between an adversary \({\mathcal {A}}\) and a challenger \(\mathcal {CHE}.{\mathcal {C}}\). The adversary \({\mathcal {A}}\) receives a randomly generated public key of \(\mathsf {CHE}\) and can issue two types of queries to \(\mathcal {CHE}.{\mathcal {C}}\): encryption queries and token queries. Below we formalize how queries are answered by \(\mathcal {CHE}.{\mathcal {C}}\) and what it means for \({\mathcal {A}}\) to win the game.
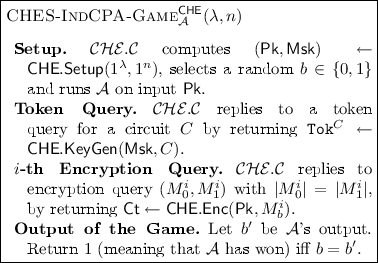
Definition 5
A CHES \(\mathsf {CHE}\) is IND-CPA secure if for every PPT adversary \({\mathcal {A}}\), there exists a negligible function \(\mu (\cdot )\) such that \({\Pr \left[ \,{{\textsc {CHES-}\textsc {IndCPA}\textsc {-Game}}^{\mathsf {CHE}}_{\mathcal {A}}(\lambda ,n)=1}\,\right] }\le 1/2+\mu (\lambda ).\)
A CHES \(\mathsf {CHE}\) is single-message IND-CPA secure if it is IND-CPA secure for all PPT adversaries \({\mathcal {A}}\) asking exactly one encryption query.
1.1 B.1 Implications
IND-CPA CHES from LWE Noticing that any fully homomorphic encryption scheme [16] is also an IND-CPA CHES, we have that the results of [7, 8] prove the following theorem.
Theorem 2
Assuming LWE, there exists an Ind-CPA-secure CHES.
NM-CPA CHES \(\Rightarrow \) IND-CPA CHES Here we show the natural implication that every NM-CPA CHES is also an IND-CPA CHES.
Theorem 3
Any NM-CPA-secure CHES is also Ind-CPA-secure.
Proof
The proof is by contradiction. Assume there exists a PPT adversary \({\mathcal {A}}\) Ind-CPA that is able to guess the challenge bit with probability at least \(1/2+\mathsf{nneg}(\lambda )\), for some non-negligible function \(\mathsf{nneg}(\cdot )\) and consider the following adversary \({\mathcal {A}}'\). \({\mathcal {A}}'\) interacts with a challenger for NM-CPA, runs an internal copy of \({\mathcal {A}}\) and uses the challenger to answer \({\mathcal {A}}\)’s queries. When \({\mathcal {A}}\) outputs b, \({\mathcal {A}}'\) outputs with the triple \((1, ct^{*},C^{*})\), where \(ct^{*}\) is an encryption of \(C^\star (M^{1}_{b})\) and \(C^{\star }\) is a circuit that satisfies the condition of the definition. Specifically, \(C^\star (m)=m+i\) where i is the smallest integer for which \(C^\star \) satisfies the condition of the definition (that is \(C^\star (M^1_0)\ne C^\star (M^1_1)\) and none of the tokens asked by \({\mathcal {A}}\) coincides with \(C^\star \) on messages \(M^1_0\) and \(M^1_1\)). Since the number of token queries is polynomially bounded, the circuit \(C^\star \) can be efficiently found.
Ind-CPA : single message vs many messages Here we show that in order to prove the Ind-CPA and NM-CPA security of a construction for a CHES, it is sufficient to concentrate on the case of an adversary that asks for one encryption query only. Indeed, we prove that any single-message Ind-CPA-secure CHES is also Ind-CPA and similarly for NM-CPA security.
Theorem 4
Any single-message Ind-CPA-secure CHES is also Ind-CPA.
Proof
Consider a single-message Ind-CPA CHES \(\mathsf {CHE}\) and suppose by contradiction that there exists an adversary \({\mathcal {A}}\) against its (many-message) Ind-CPA security that succeeds with probability \(1/2+\mathsf{nneg}(\lambda )\) for some non-negligible function \(\mathsf{nneg}(\cdot )\). We construct an adversary \({\mathcal {A}}'\) against the single-message Ind-CPA security of \(\mathsf {CHE}\) as follows. \({\mathcal {A}}'\) behaves as a proxy between the challenger of single-message Ind-CPA and \({\mathcal {A}}\) except for encryption queries and answers. Specifically, \({\mathcal {A}}'\) selects a random bit \(b'\) and a random index \(j'\) in \(\{1,\ldots ,q\}\), where q is an upper bound on the number of queries of \({\mathcal {A}}\) and will behave as a proxy between \({\mathcal {A}}\) and the challenger for all token queries and for \(j'\)-th encryption query; for the remaining encryption queries \((M_0^i,M_1^i)\) instead, \({\mathcal {A}}'\) replies by computing an encryption of \(M^{i}_{b'}\). Finally, \({\mathcal {A}}'\) outputs the same bit that \({\mathcal {A}}\) outputs.
Observe that the success probability of \({\mathcal {A}}\) is equal to \(1/2(S_{0}+S_{1})\), where we let \(S_{b}\) denote the success probability of \({\mathcal {A}}\) when the challenger chooses bit b. Therefore we have that \(1/2(S_{0}+S_{1})\ge 1/2+\mathsf{nneg}(\lambda )\).
Now consider the probability that \({\mathcal {A}}\) outputs the same bit b chosen by the challenger but in an experiment where for a randomly chosen challenge ciphertext the value \({\bar{b}}\) is used instead of b, and let us denote such a probability by \(T_{b}\). Notice that, for \(b=0,1\), \(T_{b}\ge S_{b}-\mu (\lambda )\) for some negligible function \(\mu \), for otherwise we can trivially break the single-message Ind-CPA security of \(\mathsf {CHE}\).
Noticing that with probability 1/2 it holds that \(b=b'\), we have that the success probability of \({\mathcal {A}}'\) is \(S_{0}+S_{1}\) with probability 1/2, and \(T_{0}+T_{1}\) with probability 1/2.
Summing up, the success probability of \({\mathcal {A}}'\) can be computed as follows: \(\frac{S_{0}+{S_{1}}+T_{0}+{T_{1}}}{2}\ge 1/2+\mathsf{nneg}'(\lambda )\) for some non-negligible function \(\mathsf{nneg}'\).
C Single-Message vs Multi-Message NM-CPA CHES
Theorem 5
Any single-message NM-CPA-secure CHES is also NM-CPA-secure.
Proof
Let \(\mathsf {CHE}\) be a single-message NM-CPA-secure CHES. Assume by contradiction that there exists a successful adversary \({\mathcal {A}}\) for NM-CPA security and an efficient distinguisher \(\mathcal{D}\) that distinguishes
We now reduce \({\mathcal {A}}\) to an adversary \({\mathcal {A}}'\) for single-message NM-CPA security of CHES. The reduction is similar to the one given in [21]. Let \(q>1\) be an upper bound on the the number of encryption queries made by \({\mathcal {A}}\). Consider the game \({\textsc {CHES-}\textsc {NMCPA}\textsc {-Game}}^\mathsf {CHE}_{J,{\mathcal {A}}}(\lambda ,n)\) indexed by vector \(J = (b_1,\ldots ,b_{q})\) that specifies that the j-th encryption query is answered by encrypting \(M^{j}_{b_{j}}\). For \(j=0,\ldots ,q\), we define vector \(J_{j}=(1,\ldots ,1,0,0,\ldots ,0)\) as the vector whose first j components are 1 and the remaining components are 0. We can now run hybrid arguments since \({\textsc {CHES-}\textsc {NMCPA}\textsc {-Game}}^\mathsf {CHE}_{0,{\mathcal {A}}}(\lambda ,n)\) corresponds to \({\textsc {CHES-}\textsc {NMCPA}\textsc {-Game}}^\mathsf {CHE}_{J_{0},{\mathcal {A}}}(\lambda ,n)\) and
\({\textsc {CHES-}\textsc {NMCPA}\textsc {-Game}}^\mathsf {CHE}_{1,{\mathcal {A}}}(\lambda ,n)\) corresponds to \({\textsc {CHES-}}{\textsc {NMCPA-}}{\textsc {Game}}^\mathsf {CHE}_{J_{q},{\mathcal {A}}}(\lambda ,n)\). Since \(\mathcal{D}\) distinguishes
there exists \(j \in \{0,\ldots ,q-1\}\) such that \(\mathcal{D}\) distinguishes between
We can therefore use \(\mathcal{D}\) along with adversary \({\mathcal {A}}\) to contradict single-message NM-CPA security of \(\mathsf {CHE}\) as follows. \({\mathcal {A}}'\) behaves as proxy between the challenger and \({\mathcal {A}}\) for the token queries. Instead encryption queries are handled as follows. \({\mathcal {A}}'\) selects a random \(j' \in \{0,\ldots ,q-1\}\) and forwards to the challenger the \(j'\)-th encryption query \((M_{0}^{j'},M_{1}^{j'})\) received from \({\mathcal {A}}\), and forwards to \({\mathcal {A}}\) the corresponding answer received from the challenger. Instead, for all remaining encryption queries \((M_0^i,M_1^i)\), \({\mathcal {A}}'\) answers on its own by sending an encryption of \(M_{1}^{i}\) when \(i<j'\) and of \(M_{0}^{i}\) when \(i>j'\).
Assume \(j=j'\). Notice that when the challenger encrypts \(M_{0}^{j}\), the above game corresponds to
while when the challenger encrypts \(M_{1}^{j}\), the above game corresponds to
By conditioning on the event that \(j=j'\) we conclude observing that therefore \(\mathcal{D}\) distinguishes \({\textsc {CHES-}\textsc {NMCPA}\textsc {-Game}}^\mathsf {CHE}_{0,{\mathcal {A}}'}(\lambda ',n)\) from \({\textsc {CHES-}}{\textsc {NMCPA-}}{\textsc {Game}}^\mathsf {CHE}_{1,{\mathcal {A}}'}(\lambda ,n)\).
Rights and permissions
Copyright information
© 2017 International Financial Cryptography Association
About this paper
Cite this paper
Desmedt, Y., Iovino, V., Persiano, G., Visconti, I. (2017). Controlled Homomorphic Encryption: Definition and Construction. In: Brenner, M., et al. Financial Cryptography and Data Security. FC 2017. Lecture Notes in Computer Science(), vol 10323. Springer, Cham. https://doi.org/10.1007/978-3-319-70278-0_7
Download citation
DOI: https://doi.org/10.1007/978-3-319-70278-0_7
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-70277-3
Online ISBN: 978-3-319-70278-0
eBook Packages: Computer ScienceComputer Science (R0)
