Abstract
Secret-key authentication protocols have recently received a considerable amount of attention, and a long line of research has been devoted to devising efficient protocols with security based on the hardness of the learning-parity with noise (LPN) problem, with the goal of achieving low communication and round complexities, as well as highest possible security guarantees.
In this paper, we construct 2-round authentication protocols that are secure against sequential man-in-the-middle (MIM) attacks with tight reductions to LPN, Field-LPN, or other problems. The best prior protocols had either loose reductions and required 3 rounds (Lyubashevsky and Masny, CRYPTO’13) or had a much larger key (Kiltz et al., EUROCRYPT’11 and Dodis et al., EUROCRYPT’12). Our constructions follow from a new generic deterministic and round-preserving transformation enhancing actively-secure protocols of a special form to be sequentially MIM-secure while only adding a limited amount of key material and computation.
You have full access to this open access chapter, Download conference paper PDF
Similar content being viewed by others
Keywords
1 Introduction
This paper constructs efficient provably-secure protocols for secret-key authentication, i.e., for the basic cryptographic task where one party, called the prover, proves to another – the verifier – that they share the same key. Theoretical constructions of such protocols (with strong security, to be defined below) exist from any one-way function. Moreover, practical two-round protocols can be built from any message-authentication code (MAC) by having one party authenticate a random challenge, and can be instantiated efficiently for example assuming AES-128 is unpredictable.
In contrast, this paper contributes to a line of work [10, 13, 15, 16, 18–20, 22] on building provably-secure authentication protocols with security reductions to the learning parity with noise (LPN) and related problems that are as efficient as possible, meaning that key-size, communication, and rounds are minimized. LPN problem provides confidence in security due to the failure to find polynomial-time algorithms for it and its variants, despite wide interest [5, 7, 21], and finding constructions of cryptographic primitives based on LPN has given rise to a substantial body of works [2, 6, 14, 17].
The motivation behind LPN-based authentication protocols is their potential to be implemented with different efficiency characteristics from protocols with security reductions to blockcipher security or to problems from number theory and related fields. For instance, the parallel nature of LPN-based protocols seems difficult to achieve with factoring or discrete-log type assumption. The potential efficiency benefits of LPN-based implementations are a subject of ongoing research, which has identified some advantageous scenarios [15] but also invented faster attacks [21]. We thus focus on developing techniques for protocol design and theoretical analysis that beat previous asymptotic runtimes, key sizes, and round complexity of protocols with similar security reductions. We make no specific claims of more efficient protocols in specific deployment scenarios.
Concurrently to the above, the recent interest on secret-key authentication has also motivated attempts to develop a better understanding of its foundations, providing theoretical constructions based on concrete number-theoretic assumptions like the Decisional Diffie-Hellman (DDH) assumption, or general assumptions like weak pseudorandom functions [10, 22]. We will also contribute to these lines of work with new constructions.
But before we turn to describing our contributions in detail, we first give an overview of different security notions for secret-key authentication, as well as of previous works.
Security notions. Several security notions for secret-key authentication protocols have been considered, inspired by corresponding notions for the task of public-key authentication [12]. The weakest, passive security, says that an attacker should not be able to fool the verifier after observing several sessions between an honest prover and an honest verifier. This seems unreasonably weak for most settings, so the stronger man-in-the-middle (MIM) security notion says that no attacker should be able to cause the verifier to accept in any session where a message has been changed. Realizing that MIM security from LPN seems difficult to achieve efficiently, several works instead targeted an intermediate notion called active security which says that the attacker cannot fool the verifier after interacting with the prover arbitrarily and observing sessions passively.
The LPN Assumption (and its variants). Recall that for parameters \(\ell \in \mathbb {N}\) and \(0 \le \gamma \le \frac{1}{2}\), the (decisional) Learning Parity with Noise (LPN) problem \(\mathsf {LPN}_{\ell , \gamma }\) is the problem of distinguishing a polynomial number of samples of the form \((\mathbf {r}_i, \mathbf {r}_i^T \mathbf {s}+ e_i)\), for a common random secret \(\mathbf {s}\in \{0,1\}^\ell \), random vector \(\mathbf {r}_i \in \{0,1\}^{\ell }\), and random bit \(e_i\) (taking value one with probability \(\gamma \)), from samples of the form \((\mathbf {r}_i, b_i)\), where \(b_i\) is a random bit. The corresponding \(\mathsf {LPN}_{\ell , \gamma }\) assumption is that no efficient (i.e., polynomial-time) attacker can distinguish between the two distributions, except with negligible advantage. Ignoring the obvious differences in the error distributions, this is the modulo 2 variant of the learning with error problem introduced in [27].
We are also going to consider a variant of the LPN problem, introduced and studied in [15], called Field LPN. The \(\mathsf {Field\hbox {-}LPN}_{\ell , \gamma }\) problem is very similar, however samples have the form \((\mathbf {r}_i, \mathbf {r}_i \circ \mathbf {s}+ \mathbf {e}_i)\) or \((\mathbf {r}_i, \mathbf {r}_i')\), where \(\circ \) denotes multiplication of \(\ell \)-bit vectors interpreted as elements of the extension field \(\mathbb {F}_{2^{\ell }}\), \(\mathbf {e}_i\) is a random vector where each component is 1 independently with probability \(\gamma \), and \(\mathbf {r}_i'\) is uniform.
Prior constructions. Let us briefly outline the landscape of earlier works on secret-key authentication. Table 1 summarizes some of these results.
Juels and Weis [18] first pointed out that a very simple two-round secret-key authentication protocol by Hopper and Blum [16], called the HB protocol, enjoys very low hardware complexity, and is hence amenable to implementations on RFID tags. Moreover, they proved that it is passively secure under the LPN assumption. Also in [18], they proposed a further three-round protocol, called \(\mathrm {HB}^+\), which was proven actively secure in its sequential version under the LPN assumption, and later the proof was extended to its parallel version by Katz et al. [19]. The round complexity was then reduced to two rounds by a new protocol of Kiltz et al. [20], and in contrast to \(\mathrm {HB}^+\), this latter protocol enjoys a tight reduction to the hardness of LPN. Heyse et al. [15] then proposed an even more efficient two-round protocol, called Lapin, based on the hardness of the field LPN problem. We stress that three-round protocols are less attractive than two-round ones since the prover needs to keep a state (beyond the secret key), which is problematic on lightweight devices like RFID tags.
In contrast, progress has been significantly harder in the context of MIM security. On the one hand, researchers have attempted to design multiple HB-like protocols with MIM security [8, 11, 13, 25] without or only partial security proofs. Otherwise, provably MIM-secure constructions all in fact provide a full message-authentication code (MAC) secure under LPN or Field LPN [10, 15, 20]. Unfortunately, these constructions are significantly less efficient than the existing actively secure protocols mentioned above.
While following [3] the notion of MIM security traditionally allows an attacker to interact with arbitrarily many instances of the prover and the verifier concurrently, Lyubashevky and Masny [22] recently considered the notion of sequential MIM (sMIM) security, which slightly weakens MIM to only allow the attacker to interfere with non-overlapping sequential sessions. They argue this notion is sufficient for situations in which keys are managed to never allow parallel session, and the sMIM notion is an interesting technical step towards improving authentication protocol security beyond active security while maintaining efficiency. Moreover, existing MIM attacks against actively secure protocols are often sequential (e.g., [26]). They give new protocols based on LPN and field-LPN that nearly match the complexities of actively-secure ones, but all require three rounds and suffer from a non-tight reduction to the underlying problem.
With respect to other assumptions, we also note that efficient three-round constructions from DDH and weak pseudorandom functions have also been given, achieving both active security [10] and sMIM security [22]. Two-round MIM secure protocols from PRGs have recently been proposed [9].
All of our constructions come with reductions running in polynomial time and succeeding with probability polynomially proportional to that of a given attack. One may consider looser reductions via so-called complexity leveraging where the reduction loses an exponential factor, with the view that one can enlarge the security parameter to compensate for the loss. Indeed one can prove (say) the AUTH\(_2\) protocol from [20] as a fully-secure MAC with an exponential loss of security. A concrete instantiation of the result (assuming the BKW attack complexity is optimal [7]) will be more efficient than the other approaches we have outlined.
Polynomial reductions, however, are preferred as they are more robust to algorithmic advances against the underlying problems. Achieving them is, in our view, an interesting theoretical challenge that requires new techniques. In an implementation it is not clear to the authors if either approach (leveraging or polynomial reductions) is necessarily more secure given the many factors one must consider.
Our contributions. We provide the to-date most efficient constructions of sMIM-secure authentication protocols based on the hardness of LPN, as well as on other assumptions. Our constructions are two rounds and the first message consists of a truly random challenge, and enjoy tight security reduction to the underlying assumption.
We improve upon the round complexity of existing sMIM-secure protocols without increasing key length and communication complexity, and without resorting to complexity leveraging. See Table 1 for a comparison of two of our new protocols to prior work. Note that our protocols are only a small constant factor less efficient than the best known actively (or even passively) secure protocols.
At the high level, our constructions follow from a generic transformation that upgrades a two round protocol of a special form to be sMIM-secure without introducing significant overhead. The required form is not especially contrived, but requires some care in its formalization and we present examples of such protocols to obtain our instantiations. We note that our reduction does not employ rewinding or forking lemmas like [22], and is tighter and (arguably, to our taste) simpler as a result.
Our first construction achieves sMiM security with a tight reduction to LPN, two rounds of communication, and only a modest increase in either key size or communication over [22]. Our second construction, from Field LPN, matches the key size and communication of prior work in two rounds instead of three and has a tight reduction. In fact, for an appropriate choice of components, the second construction can be understood as a two-round version of the three-round protocol from [22], though their proof does not cover the two round version.
We also provide a simple construction of a two-round sMIM secure authentication protocol based on the DDH assumption, where the prover response consists of two group elements. Interestingly, the same construction was proven MIM secure under the (less standard) Gap-CDH assumption in [10].
Our last construction is based on an arbitrary weak PRF. The complexity of the construction is comparable to the one building a MAC from a weak PRF, using for example the constructions in [1, 23, 24]. However, our new protocols enjoy much better parallelism when compared to the naive approach, and is hence interesting on its own right. It is also fair to point out that [22] accomplishes in three rounds the harder task of finding a generic construction from a (randomized) weak PRF. We observe however that the only known concrete instantiations of weak PRFs are based on LPN/LWE-type assumptions as well as on DDH, and for all these concrete instantiations our constructions are more efficient.
We remark that it is not hard to see that our proofs do not show (full) MIM security, but we are not aware of an explicit MIM attack against the protocols.
Organization. Section 2 contains basic definitions used below. In Sect. 3 we describe our transformation from weaker protocols of a special form, and in Sect. 4 we give several instantiations of the transformation.
2 Preliminaries
For a set \(\mathcal{X}\), \(x \mathop {\leftarrow }\limits ^{{\scriptscriptstyle \$}}\mathcal{X}\) denotes sampling x from \(\mathcal{X}\) according to the uniform distribution. We use bold lowercase letters for vectors and bold uppercase letters for matrices, e.g., \(\mathbf {x}\in \mathbb {F}_2^\ell \), \(\mathbf {X}\in \mathbb {F}_2^{\ell \times n}\). For \(\mathbf {c}\in \mathbb {F}_2^\ell \), let \(\mathbf {M}_\mathbf {c}\) denote the matrix of the linear map \(l_\mathbf {c}\) implementing the finite field multiplication with \(\mathbf {c}\) when interpreted as an element in \(\mathbb {F}_{2^\ell }\).Footnote 1
Symmetric authentication syntax. We are going to consider secret-key authentication protocols, where a prover proves to a verifier that they hold the same secret key over two or more rounds.
More formally, an r -round symmetric authentication protocol with associated key space \(\mathcal{K}\) is a triple of algorithms \(\mathsf {Auth}= (\mathsf {Gen}, \mathsf {P}, \mathsf {V})\) with the following properties:
-
Key Generation. The probabilistic key-generation algorithm \(K \leftarrow \mathsf {Gen}(1^k)\) takes as input a security parameter \( k \in {{\mathbb N}}\) (in unary) and outputs a secret key \(K\in \mathcal{K}\).
-
Interactive Execution. The probabilistic interactive algorithms \(\mathsf {P}\) and \(\mathsf {V}\), which we refer to as the prover and the verifier, take both as input a secret key \(K \in \mathcal{K}\), synchronously interact with each other over r rounds, and finally \(\mathsf {V}\) always receives the last message and outputs a decision \(\mathsf {out}(\mathsf {P}_K, \mathsf {V}_K) \in \{\mathsf {accept}, \mathsf {reject}\}\).
We say that \(\mathsf {Auth}\) has completeness error \(\alpha \) if for all \(k\in {{\mathbb N}}\), \(\Pr [\mathsf {out}(\mathsf {P}_K, \mathsf {V}_K) =\mathsf {reject}; K \leftarrow \mathsf {Gen}(1^ k )] \le \alpha \). In this paper, we will focus on the simpler case of two-round protocols, where additionally the first message is a random challenge \(c \in \mathcal{C}\) for some set \(\mathcal{C}\). We call such protocols two-round random-challenge secret-key authentication protocols. In particular, in such protocols the prover simplifies to a probabilistic algorithm \(\mathsf {P}_K\), taking the challenge and the secret key K, and producing the message t to be sent back to the adversary. Moreover, for a challenge \(c \in \mathcal{C}\) and response t from the prover, the verifier is fully specified by an algorithm \(\mathsf {V}_K(c, t) \in \{\mathsf {accept}, \mathsf {reject}\}\).
Security. Several security notions for symmetric-key authentication protocols have been considered in the literature. The weakest one, passive security, says that an attacker should not be able to fool the verifier after observing several sessions between a honest prover and a honest verifier. The stronger notion called active security says that the attacker cannot fool the verifier after interacting with the prover arbitrarily and observing sessions passively.
This paper targets the security notion of (sequential) security against man-in-the-middle attacks (or \(\mathsf {s{\hbox {-}}mim}\) security, for short). Here, the adversary acts as a man-in-the middle in a sequence of independent sessions between the prover and the verifier, all with the same secret key. The adversary wins whenever it manages to let the verifier accept in some session and has changed at least one of the messages sent by the prover or the verifier. We are going to formalize this notion for the relevant case of two-round protocols with random challenge.
Concretely, we describe this security notion via the following game \(\mathsf {S{\hbox {-}}MIM}\) for an attacker \(A\) and a two-round random-challenge authentication protocol \(\mathsf {Auth}= (\mathsf {Gen}, \mathsf {P}, \mathsf {V})\) with challenge set \(\mathcal{C}\).
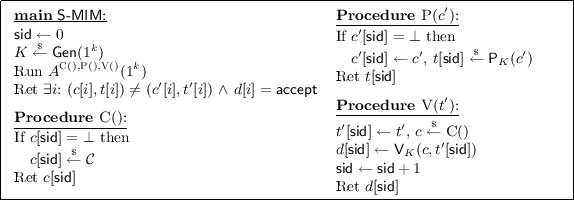
In the game, the attacker makes calls to three oracles, \(\textsc {C}(\cdot ), \textsc {P}(\cdot )\) and \(\textsc {V}(\cdot )\). All oracles use a global variable \(\mathsf {sid}\) to “synchronize” the sessions being simulated. The first oracle returns, for every session, a new random challenge. The oracle \(\textsc {P}(c')\) runs the prover on input \(c'\) and returns the response t. Oracle \(\textsc {V}(t')\) checks that \(t'\) is a valid response for the current session challenge \(c[\mathsf {sid}]\) (obtained by calling \(\textsc {C}()\)), and increases the session number. Note that there is a unique value \(c[\mathsf {sid}]\) defined in every session, and \(\textsc {P}\) only provides (at most) one valid challenge-tag pair \((c', t)\) per session. The \(\mathsf {s{\hbox {-}}mim}\) advantage is \(\mathbf {Adv}^{\mathsf {s{\hbox {-}}mim}}_{\mathsf {Auth}}(A) = {\Pr \left[ \,{\mathsf {S{\hbox {-}}MIM}^{A}_{\mathsf {Auth}} \Rightarrow \mathsf {true}}\,\right] }\), and we say that \(\mathsf {Auth}\) is \((t, r, \epsilon )\)-\(\mathsf {s{\hbox {-}}mim}\)-secure if for all attackers \(A\) with time complexity t and running at most r sessions, we have \(\mathbf {Adv}^{\mathsf {s{\hbox {-}}mim}}_{\mathsf {Auth}}(A) \le \epsilon \).
Hash functions. Our constructions rely on almost pairwise-independent hash functions.
Definition 1
(Almost pairwise-independent hash functions). For \(\delta \ge 1\), a function \(\mathsf {H}: {\mathcal{K}}_{\mathsf {H}}\times \mathcal {X} \rightarrow \mathcal Y\) is \(\delta \) -almost pairwise-independent if
for all distinct \(x, x' \in \mathcal {X}\) and all \(y, y' \in \mathcal Y\), and where \(K_{\mathsf {H}}\mathop {\leftarrow }\limits ^{{\scriptscriptstyle \$}}{\mathcal{K}}_{\mathsf {H}}\). Moreover, by itself, \(\mathsf {H}_{K_{\mathsf {H}}}(x)\) is uniformly distributed over \(\mathcal{Y}\).
The requirement that a single input has uniformly distributed output is not common, but will be useful in applications and satisfied by the construction given below. Moreover, Definition 1 implies adaptive security, i.e., when given x, \(\mathsf {H}_{K_{\mathsf {H}}}(x) = y\), for any \(x'\) and \(y'\) chosen adaptively depending on y, the probability that \(\mathsf {H}_{K_{\mathsf {H}}}(x') = y'\) is at most \(\delta / |\mathcal{Y}|\).
Lemma 2
If \(\mathsf {H}\) is \(\delta \)-almost pairwise-independent, then for every (unbounded) adversary \(A\) and every \(x \in \mathcal X\), we have
Proof
Assume wlog that \(A\) is deterministic, and let \(x'(x,y)\) and \(y'(x,y)\) be the values of \(x'\) and \(y'\) output by \(A\) on inputs y, x, where \(x'(x,y) \ne x\) by assumption. Then,
which is smaller than \(|\mathcal{{Y}}| \cdot \frac{\delta }{|{\mathcal{Y}}|^2} = \frac{\delta }{|\mathcal {Y}|}\). \(\square \)
A construction. We will make use of the following key-length efficient construction of a \(\delta \)-almost-pairwise independent function, where \({\mathcal{K}}_{\mathsf {H}}= \mathbb {F}^2\), \(\mathcal Y = \mathbb {F}\) and \(\mathcal X = \mathbb {F}^\ell \) for some finite field \(\mathbb {F}\). The function, given \(K_{\mathsf {H}}= (a, b) \in \mathbb {F}^2\) and input \(x = (x_0, \ldots , x_{\ell - 1}) \in \mathbb {F}^{\ell }\), outputs \( \mathsf {H}_{a, b}(x) = \sum _{i = 0}^{\ell -1} x_i \circ a^i + b \;.\)
Lemma 3
The function \(\mathsf {H}\) above is \(\delta \)-almost pairwise independent for \(\delta = \ell - 1\).
The folklore proof is given for completeness.
Proof
Fix \(x = (x_0, x_1, \ldots , x_{\ell - 1})\) and \(x' = (x'_0, x'_1, \dots , x'_{\ell - 1})\). Also, we define the polynomial \(p_{x}(a) = \sum _{i = 0}^{\ell - 1} x_i \circ a^i\), and analogously, define \(p_{x'}(a)\). Given two \(y, y' \in \mathbb {F}\), we look at the number of keys (a, b) such that \(p_{x}(a) + b = y\) and \(p_{x'}(a) + b = y'\). This in particular implies that a needs to satisfy
and since there exists i with \(x_i \ne x_i'\), note that by the Schwartz-Zippel lemma there are at most \(\ell - 1\) solutions a with the above property, since \(p_{x}(a) - p_{x'}(a)\) is a polynomial of degree at most \(\ell - 1\). Each such a defines a unique b, and thus there are overall at most \(\ell - 1\) solutions, and each one of them is taken with probability \(|\mathbb {F}|^2\).
Finally, note that the distribution of \(\mathsf {H}_{a, b}(x)\) is, by itself, uniform, because the term b is uniform, and thus completely blinds the output. \(\square \)
3 Generic Construction
This section presents our main result, a generic construction of a two-round sequential MIM-secure authentication protocol \(\mathsf {Auth}\). Our construction relies on a simpler two-round symmetric authentication protocol \(\mathsf {Auth}'\) used as a component and which satisfies a particular form of security, in addition to having a structured tag space, as we discuss next. Later below, we will provide several instantiations of this generic construction in Sect. 4 via constructions of \(\mathsf {Auth}'\) based on a set of different assumptions.
3.1 Tools
Our construction is going to rely on an authentication protocol \(\mathsf {Auth}= (\mathsf {Gen}, \mathsf {P}, \mathsf {V})\) whose responses given by the prover (which we call tags, following existing conventions in the literature) \(\tau \mathop {\leftarrow }\limits ^{{\scriptscriptstyle \$}}\mathsf {P}_{K}(c)\) are composed of two distinct components \(\tau = (\tau _1, \tau _2) \in {\mathcal{T}}_1\times {\mathcal{T}}_2\). We refer to \(\tau _1\) and \(\tau _2\) as the left and right tag, respectively. In addition to this, we are going to require that the protocol satisfies two new properties which we now introduce and discuss.
Tag sparsity. The first property is a combinatorial property on the tag space of \(\mathsf {Auth}\). We are going to require that given any challenge c, any secret key K, and any left component of the tag \(\tau _1\), there are only few right components \(\tau _2\) such that \(\tau = (\tau _1, \tau _2)\) is a valid tag for challenge c and key K. This is captured formally by the following definition.
Definition 4
(Right tag-sparsity). For an \(\epsilon = \epsilon ( k )\), we say that \(\mathsf {Auth}= (\mathsf {Gen}, \mathsf {P}, \mathsf {V})\) with tags in \({\mathcal{T}}_1\times {\mathcal{T}}_2\), challenge space \(\mathcal{C}\), and key space \(\mathcal{K}\) has \(\epsilon \) -sparse right tags (or alternatively, \(\mathsf {Auth}\) has \(\epsilon \) -right tag sparsity) if
for all \(c \in \mathcal{C}\), \(K \in \mathcal{K}\), and \(\tau _1\in {\mathcal{T}}_1\).
Note that one equivalent formulation is that for all K, c, and \(\tau _1\), there are at most \(\epsilon \cdot |{\mathcal{T}}_2|\) valid \(\tau _2\).
ROR-CMA security. We also consider a new property called real-or-random right-tag chosen-message security (or \(\mathsf {ror\hbox {-}cma}\) security, for short), which is specific to protocols as above with tag space \({\mathcal{T}}_1\times {\mathcal{T}}_2\). It considers a game where an attacker first receives a challenge \(c^*\), then can obtain prover tags for arbitrary challenges of its choice, and at the end can issue exactly one verification query for the challenge \(c^*\). The notion demands that the attacker cannot distinguish this game from another game where queries for challenges \(c \ne c^*\) have the right tag \(\tau _2\) replaced by a random element from the same set. Formally, we introduce the following two games – denoted \(\mathsf {ROR{\hbox {-}}CMA}(0), \mathsf {ROR{\hbox {-}}CMA}(1)\) – involving \(\mathsf {Auth}\) as well as an adversary \(A\) which outputs a decision value in \(\{\mathsf {true}, \mathsf {false}\}\) at the end of the game:

Then, for an attacker \(A\) and a two-round protocol \(\mathsf {Auth}\), we define the \(\mathsf {ror\hbox {-}cma}\) advantage as
Accordingly, we say that \(\mathsf {Auth}\) is \((t, q, \epsilon )\)-\(\mathsf {ror\hbox {-}cma}\)-secure if for all t-time attackers \(A\) issuing at most q queries to oracle \(\textsc {T}(\cdot )\), we have \(\mathbf {Adv}^{\mathsf {ror\hbox {-}cma}}_{\mathsf {Auth}}(A) \le \epsilon \).
Relation to active security. We stress that \(\mathsf {ror\hbox {-}cma}\) security and negligible right-tag sparsity, when achieved simultaneously, do not even imply passive security. Indeed, it is easy to modify any protocol with these two properties into one accepting tags of the form \((\tau _1, 0)\) for every K and c (and hence becoming completely insecure) without invalidating these two properties. However, any such protocol can easily be enhanced to be secure against active adversaries by blinding \(\tau _2\) with a secret field element K, either via addition or multiplication. (Note that negligible right-tag sparsity implies that the set of right tags has overwhelming size.)
Nonetheless, in order to better understand our construction below, it is important to observe why the resulting protocol is not necessarily \(\mathsf {s{\hbox {-}}mim}\) secure. Consider e.g. the protocol such that \(\mathsf {P}_K(c) = (\tau _1, \tau _2 = \mathsf {PRF}_K(\tau _1\Vert c))\) for a random \(\tau _1\) and pseudorandom function \(\mathsf {PRF}\) with key K and n-bit output, and for which \(\mathsf {V}_K\) accepts \((\tau _1, \tau _2)\) on input c if and only if \(\mathsf {PRF}_K(\tau _1\Vert c)\) has Hamming distance at most 1 from \(\tau _2\). One can verify that this protocol is \(\mathsf {ror\hbox {-}cma}\) secure and has negligible right-tag sparsity. But when the above tranformation is applied, resulting in tags \((\tau _1, \tau _2 = \mathsf {PRF}_K(\tau _1\Vert c) + K')\), an attacker can easily derive a new valid tag for c as \((\tau _1, \tau _2 + \varDelta )\) for any weight-one \(\varDelta \) – hence breaking \(\mathsf {s{\hbox {-}}mim}\) security. (Similar counterexamples can be built when blinding via multiplication.)
3.2 The Generic Construction
We now turn to describing our generic construction transforming a \(\mathsf {ror\hbox {-}cma}\)-secure two-round random challenge authentication protocol \(\mathsf {Auth}'\) with \(\epsilon \)-right tag sparsity (for a small \(\epsilon \)) into a sequential MIM secure two-round authentication protocol.
Description. Let \(\mathsf {Auth}'=(\mathsf {Gen}',\mathsf {P}',\mathsf {V}')\) be two-round authentication protocol with associated key space \(\mathcal{K}\), challenge space \(\mathcal{C}\), and split tag space \(\mathcal{T}=\mathcal{T}_1 \times \mathcal{T}_2\), where we assume that \(\mathcal{T}_2=\mathbb {F}\) is a finite field.Footnote 2 We will use \(+\) and \(\circ \) to denote addition and multiplication of field elements, respectively. Let \(\mathsf {H}: {\mathcal{K}}_{\mathsf {H}}\times \mathcal{T}_1 \rightarrow \mathbb {F}\) be a hash function. We build a 2-round symmetric authentication protocol \(\mathsf {Auth}= (\mathsf {Gen}, \mathsf {P}, \mathsf {V})\) as follows. (The protocol \(\mathsf {Auth}\) inherits the completeness error of \(\mathsf {Auth}'\).)
-
Key Generation. The key-generation algorithm \(\mathsf {Gen}(1^k)\) picks a key \({K_\mathsf {H}}\mathop {\leftarrow }\limits ^{{\scriptscriptstyle \$}}{\mathcal{K}}_{\mathsf {H}}\) for \(\mathsf {H}\), an element \({K_\mathbb {F}}\mathop {\leftarrow }\limits ^{{\scriptscriptstyle \$}}\mathbb {F}\setminus \{0\}\), and generates a key \({K'}\mathop {\leftarrow }\limits ^{{\scriptscriptstyle \$}}\mathsf {Gen}'(1^k)\) for \(\mathsf {Auth}'\). The key is \(K=({K'},{K_\mathsf {H}},{K_\mathbb {F}})\).
-
Challenge. The challenge is generated by the verifier \(\mathsf {V}\) as \(c \mathop {\leftarrow }\limits ^{{\scriptscriptstyle \$}}\mathcal{C}\).
-
Response. The response \(\sigma =(\sigma _1,\sigma _2)\) to challenge \(c \in \mathcal{C}\) is computed by the prover \(\mathsf {P}\) by first running \(\tau =(\tau _1, \tau _2) \mathop {\leftarrow }\limits ^{{\scriptscriptstyle \$}}\mathsf {P}'_{{K'}}(c)\) and
$$\begin{aligned} \sigma =(\sigma _1, \sigma _2 ) = (\tau _1, \tau _2 \circ {K_\mathbb {F}}+ \mathsf {H}_{K_\mathsf {H}}(\tau _1)) \in \mathcal{T}_1 \times \mathbb {F}. \end{aligned}$$ -
Verify. Given challenge c and response \(\sigma =(\sigma _1,\sigma _2)\), the verifier \(\mathsf {V}\) reconstructs
$$\begin{aligned} \tau =(\tau _1,\tau _2) = (\sigma _1, \ (\sigma _2 - \mathsf {H}_{K_\mathsf {H}}(\sigma _1)) \circ {K_\mathbb {F}}^{-1}) \end{aligned}$$and returns the decision \(\{\mathsf {accept},\mathsf {reject}\} \leftarrow \mathsf {V}'_{K'}(c,\tau )\).
Overhead. We note that our transformation does not increase the tag size of the underlying protocol \(\mathsf {Auth}'\), and thus retains its communication complexity. Moreover, the key length increases by adding \(K_{\mathbb {F}}\) and \(K_{\mathsf {H}}\). Below, we will show that \(\mathsf {H}\) can be instantiated with the hash-function construction given in Sect. 2, and thus these two additional keys consist overall of three field elements.
3.3 Security
The following theorem establishes the concrete security of our generic construction. In particular, it says that as long as for sufficiently small \(\delta \) and \(\epsilon \), \(\mathsf {H}\) is \(\delta \)-almost pairwise independent and \(\mathsf {Auth}'\) has both \(\epsilon \)-right-tag sparsity and is \(\mathsf {ror\hbox {-}cma}\)-secure, then the construction is \(\mathsf {s{\hbox {-}}mim}\)-secure.
Theorem 5
(Security of the generic construction). Assume that \(\mathsf {H}\) is \(\delta \)-almost universal and that \(\mathsf {Auth}'\) satisfies \(\epsilon \)-right tag sparsity and has completeness error \(\alpha \). Then, for all \(\mathsf {s{\hbox {-}}mim}\)-attackers \(A\) invoking at most r sessions, there exists a \(\mathsf {ror\hbox {-}cma}\)-attack \(B\) such that
where \(B\) has running time approximately equal to that of \(A\), and makes at most r queries to its oracle. In other words, if \(\mathsf {Auth}'\) is \((t, r, \epsilon )\)-\(\mathsf {ror\hbox {-}cma}\)-secure, then \(\mathsf {Auth}\) is \((t', r, r \cdot (\epsilon + {r}/{|\mathcal{C}|} + \epsilon \delta |\mathbb {F}|/(|\mathbb {F}| - 1)))\)-\(\mathsf {s{\hbox {-}}mim}\)-secure, where \(t' \approx t\).
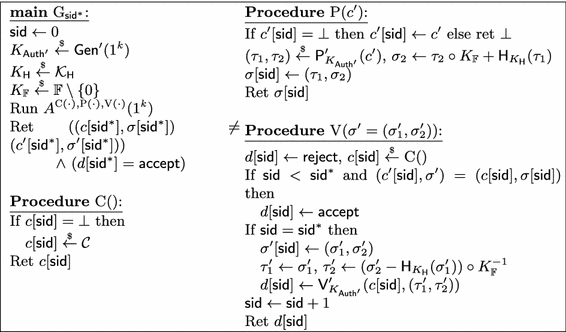
Game \(\mathrm {G}_{\mathsf {sid}^*}\) for \(\mathsf {sid}^*\in \{1, \ldots , r\}\) in the proof of Theorem 5. All oracles return \(\bot \) if \(\mathsf {sid}> \mathsf {sid}^*\).
Proof
Let \(A\) be an attacker for game \(\mathsf {S{\hbox {-}}MIM}\) which calls its oracles for at most r sessions. In the following, we are going to upper bound \(\mathbf {Adv}^{\mathsf {s{\hbox {-}}mim}}_{\mathsf {Auth}}(A) = {\Pr \left[ \,{\mathsf {S{\hbox {-}}MIM}^{A}_{\mathsf {Auth}} \Rightarrow \mathsf {true}}\,\right] }\). The proof proceeds via a sequence of games.
As our first step, we prove that it is sufficient to consider the first round where the attacker alters the communication between prover and verifier, and the latter still accepts. Formally, for all \(\mathsf {sid}^*\in \{1, \ldots , r\}\), let \({\textsc {Win}}_{\mathsf {sid}^*}\) be the event that in the experiment \(\mathsf {S{\hbox {-}}MIM}^{A}_{\mathsf {Auth}}\) session \(\mathsf {sid}^*\) is the first session where the attacker makes the verifier non-trivially accept (and thus \(d[\mathsf {sid}^*] = \mathsf {accept}\)) with \((c'[\mathsf {sid}^*], t'[\mathsf {sid}^*]) \ne (c[\mathsf {sid}^*], t[\mathsf {sid}^*])\). In particular, for all \(\mathsf {sid}< \mathsf {sid}^*\) we either have \((c[\mathsf {sid}], t[\mathsf {sid}]) = (c'[\mathsf {sid}], t'[\mathsf {sid}])\) or \(d[\mathsf {sid}] = \mathsf {reject}\). Moreover, let \({\textsc {Win}}= \bigcup _{\mathsf {sid}^*= 1}^r {\textsc {Win}}_{\mathsf {sid}^*}\) be the event that \(\mathsf {S{\hbox {-}}MIM}^{A}_{\mathsf {Auth}}\) outputs \(\mathsf {true}\) in the first place. Clearly, the r events \({\textsc {Win}}_1, \ldots , {\textsc {Win}}_r\) are disjoint, and therefore
As our first step, we introduce r new games \(\mathrm {G}_1, \ldots , \mathrm {G}_r\), where \(\mathrm {G}_{\mathsf {sid}^*}\) only allows the adversary \(A\) to execute \(\mathsf {sid}^*\) sessions, and the verifier returns \(\mathsf {reject}\) for the first \(\mathsf {sid}^*- 1\) sessions unless the adversary A has been simply forwarding honestly generated messages. A formal description of \(\mathrm {G}_{\mathsf {sid}^*}\) is given in Fig. 1. There, we implicitly assume that all oracles return \(\bot \) whenever \(\mathsf {sid}> \mathsf {sid}^*\). It is easy to see that by construction, \({\Pr \left[ \,{\mathrm {G}_{\mathsf {sid}^*}^{A} \Rightarrow \mathsf {true}}\,\right] } \ge {\Pr \left[ \,{{\textsc {Win}}_{\mathsf {sid}^*}}\,\right] } - (\mathsf {sid}^*- 1) \alpha \). The offset depending on the completeness error \(\alpha \) is due to the fact that \(\mathrm {G}_{\mathsf {sid}^*}^{A}\) always accepts honest executions in sessions \(\mathsf {sid}< \mathsf {sid}^*\), whereas this is not necessarily true in \(\mathsf {S{\hbox {-}}MIM}^{A}_{\mathsf {Auth}}\). Therefore,
In the remainder of this proof, for every \(\mathsf {sid}^*\in \{1, \ldots , r\}\), we are going to prove an upper bound on \({\Pr \left[ \,{\mathrm {G}_{\mathsf {sid}^*}^{A} \Rightarrow \mathsf {true}}\,\right] }\). In particular, we now fix an arbitrary \(\mathsf {sid}^*\in \{1, \ldots , r\}\), and let \(\mathrm {H}_0 = \mathrm {G}_{\mathsf {sid}^*}\).
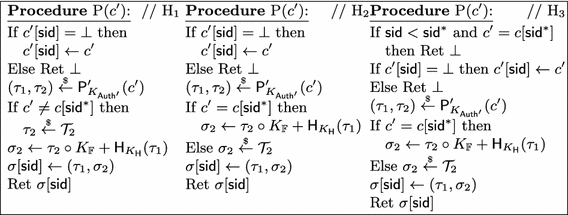
The proof now continues by transitioning from Game \(\mathrm {H}_0\) in turn to games \(\mathrm {H}_1\), \(\mathrm {H}_2\) and \(\mathrm {H}_3\). With respect to \(\mathrm {H}_0\), these games will only differ in the way in which queries to \(\textsc {P}\) are answered, but all games will otherwise inherit the main procedure, as well as \(\textsc {C}\) and \(\textsc {V}\), verbatim from \(\mathrm {G}_{\mathsf {sid}^*} = \mathrm {H}_0\). A formal specification of the respective procedures is given in Fig. 2, and we now discuss them in detail.
We first transition to Game \(\mathrm {H}_1\), where we will use \(\mathsf {ror\hbox {-}cma}\) security of \(\mathsf {Auth}'\) to replace the right half of every tag computed by \(\textsc {P}\) to a random component whenever \(c' \ne c[{\mathsf {sid}^*}]\), i.e., different from the random challenge used in the last round. The proof of the following lemma is given below.
Lemma 6
There exists an attacker \(B\) such that
where \(B\) has running time approximately equal to that of \(A\), and makes at most r queries to its oracle.
Subsequently, in Game \(\mathrm {H}_2\), whenever \(c' \ne c[{\mathsf {sid}^*}]\), instead of generating \(\tau _2\) at random, we directly generate \(\sigma _2\) uniformly at random from the same set. Note that because \(K_{\mathbb {F}}\ne 0\), we have that \(\tau _2\cdot K_{\mathbb {F}}\) is a fresh random value, and thus the two games \(\mathrm {H}_1\) and \(\mathrm {H}_2\) are identical,
In the next game, Game \(\mathrm {H}_3\), the procedure \(\textsc {P}\) replies to a query \(c' = c[{\mathsf {sid}^*}]\) only if it is made in session \(\mathsf {sid}^*\), and otherwise returns \(\bot \). As \(c[{\mathsf {sid}^*}]\) is chosen uniformly at random, and independent of the interaction between the adversary and the oracles in the first \(\mathsf {sid}^*- 1\) sessions, the “fundamental lemma" of game playing [4] yields
Therefore, putting together Eq. (1), Lemma 6, and Eq. (2), we obtain that there exists an attacker \(B\) making at most r oracle queries and with time complexity close to the one of \(A\) such that
In the rest of the proof, we give an upper bound on the probability that the game \(\mathrm {H}_3\) outputs \(\mathsf {true}\). The argument is going to rely on the almost pairwise-independence of \(\mathsf {H}\) and the right-tag sparsity of \(\mathsf {Auth}'\), and is from now on a purely information-theoretic argument. In particular, it does not rely on \(K_{\mathsf {Auth}'}\) being hidden, but only on the fact that all the right tags in sessions prior to \(\mathsf {sid}^*\) are random.
Analysis of winning probability in \(\mathrm {H}_3\). In the following, for notational convenience we let \(\sigma [\mathsf {sid}^*] = (\sigma _1 = \tau _1, \sigma _2)\) and \(\sigma '[\mathsf {sid}^*] = (\sigma _1', \sigma '_2)\) be the original and modified values in the second-round of session \(\mathsf {sid}^*\). Similarly, we simply denote \(c = c[\mathsf {sid}^*]\) and \(c' = c'[\mathsf {sid}^*]\). Concretely, we are going to consider three different cases when analyzing the probability \({\Pr \left[ \,{\mathrm {H}_3^{A} \Rightarrow \mathsf {true}}\,\right] }\) : (1) \(c' \ne c\), (2) \(c' = c\) and \(\sigma _1 = \sigma _1'\), and (3) \(c' = c\) and \(\sigma _1 \ne \sigma _1'\). We now analyze the three individual cases.
Case \(c' \ne c\). Observe first that in session \(\mathsf {sid}^*\), the attacker obtains \((\tau _1, \sigma _2)\), where \((\tau _1, \tau _2) \mathop {\leftarrow }\limits ^{{\scriptscriptstyle \$}}\mathsf {P}'_K(c'_{\mathsf {sid}^*})\) and \(\sigma _2\mathop {\leftarrow }\limits ^{{\scriptscriptstyle \$}}{\mathcal{T}}_2\), and inputs \((\sigma '_1, \sigma '_2)\) to \(\textsc {V}\). It wins if \((\sigma _1', \tau _2')\) is a valid tag, where \(\tau _2' = (\sigma _2' - \mathsf {H}_{K_{\mathsf {H}}}(\sigma _1')) \circ K_{\mathbb {F}}^{-1}\).
The crucial point is that \(K_{\mathbb {F}}\) and \(K_{\mathsf {H}}\) have never been used prior to the computation of \(\tau _2'\), as the oracle \(\textsc {P}\) has only returned random right tags. So we can equivalently think of generating these uniformly at random for the first time at this point independent of the rest of the game, and consider the probability that \( \mathsf {V}'_K(c, (\sigma _1', \tau '_2))\) verifies. Moreover, the value \(Y := \mathsf {H}_{K_{\mathsf {H}}}(\sigma _1')\) is going to be uniform (as we don’t evaluate the function on any other point) by the \(\delta \)-almost pairwise independence of \(\mathsf {H}\). Therefore, for every value \(t \in \mathbb {F}\),
However, by \(\epsilon \)-right tag sparsity, we know that there are at most \(\epsilon |\mathbb {F}|\) possible values t for which \((\sigma _1', t)\) is a valid tag, and thus by the union bound
Case \(c' = c\), \(\sigma _1 = \sigma _1' = \tau _1\) and \(\sigma _2 \ne \sigma _2'\). In this case, in session \(\mathsf {sid}^*\), the attacker obtains \((\tau _1, \sigma _2)\), where \((\tau _1, \tau _2) \mathop {\leftarrow }\limits ^{{\scriptscriptstyle \$}}\mathsf {P}'_K(c)\) and \(\sigma _2\mathop {\leftarrow }\limits ^{{\scriptscriptstyle \$}}\tau _2\circ K_{\mathbb {F}}+ \mathsf {H}_{K_{\mathsf {H}}}(\tau _1)\). Subsequently, it inputs \((\tau _1, \sigma '_2)\) to \(\textsc {V}\). It wins if \(\mathsf {V}'_K(c, (\tau _1, \tau _2')) = \mathsf {accept}\), where \(\tau _2' = (\sigma _2' - \mathsf {H}_{K_{\mathsf {H}}}(\tau _1)) \circ K_{\mathbb {F}}^{-1} \ne \tau _2\). Once again, we evaluate \(\mathsf {H}\) only with one input, and as above \(Y = \mathsf {H}_{K_{\mathsf {H}}}(\tau _1)\) is uniformly distributed.
Now, given \(\sigma _2\), \(\tau _2\), and \(\sigma _2'\), we want to upper bound the probability that \(\tau _2' = t \ne \tau _2\) for some value \(t \in \mathbb {F}\), where the probability is over the choice of \(K_{\mathbb {F}}\) and Y.
Since \(\tau _2 \ne t\), there exists exactly one \(K_{\mathbb {F}}\) such that \((\tau _2 - t) \cdot K_{\mathbb {F}}= \sigma _2 - \sigma _2'\), and moreover, this defines a unique value for Y, which is taken with probability at most \(1/|\mathbb {F}|\), and thus the probability in the numerator is upper bounded by \(1/(|\mathbb {F}| (|\mathbb {F}| - 1))\). Moreover, \(\tau _2 \circ K_{\mathbb {F}}+ Y\) is clearly uniform (because Y is uniform), and thus the denominator is \(1/|\mathbb {F}|\). Putting these together gives us \({\Pr }\left[ \, \tau _2' = t\,\left| \right. \,\sigma _2 = \tau _2 \circ K_{\mathbb {F}}+ Y\,\right] \le 1/(|\mathbb {F}| - 1)\). Now, due to \(\epsilon \)-right tag sparsity, there are at most \(\epsilon \cdot |\mathbb {F}|\) right tags \(\tau _2'\) that verify, and thus
Case \(c' = c\) and \(\sigma _1 \ne \sigma _1'\). For the final case, the attacker obtains \((\tau _1, \sigma _2)\) as in the previous case, but inputs \((\sigma _1' \ne \tau _1, \sigma _2')\) to \(\textsc {V}\), and the latter computes \(\tau _2' = (\sigma _2' - \mathsf {H}_{K_{\mathsf {H}}}(\sigma _1')) \circ K_{\mathbb {F}}^{-1}\).
Here, we indeed evaluate \(\mathsf {H}_{K_{\mathsf {H}}}\) on two inputs. However, by Lemma 2, we see that for every possible values \(\sigma _1'\) and \(y'\), chosen adaptively depending on \(\tau _1\) and \(\mathsf {H}_{K_{\mathsf {H}}}(\tau _1)\), \(\mathsf {H}_{K_{\mathsf {H}}}(\sigma _1') = y'\) with probability at most \(\delta / |\mathbb {F}|\). Therefore, for every possible t such that \(\mathsf {V}'_{K}(c, (\sigma _1', t)) = \mathsf {accept}\), we have
Now, due to \(\epsilon \)-right tag sparsity, there are at most \(\epsilon \cdot |\mathbb {F}|\) such right tags, and thus
Putting things together. To conclude the proof, we observe that all terms in Eqs. (3), (4) and (5) are upper bounded by \(\epsilon \cdot \delta \cdot \frac{|\mathbb {F}|}{|\mathbb {F}| - 1}\), and thus we also have \({\Pr \left[ \,{\mathrm {H}_3^{A} \Rightarrow \mathsf {true}}\,\right] } \le \epsilon \cdot \delta \cdot \frac{|\mathbb {F}|}{|\mathbb {F}| - 1}\). \(\square \)
Proof
(Lemma 6 ). The attacker \(B\) for \(\mathsf {ROR{\hbox {-}}CMA}(b)\) is very simple. It simulates the execution of \(\mathrm {H}_{b}\) to the attacker \(A\). Initially, \(B\) uses its input challenge \(c^*\) as \(c_{\mathsf {sid}^*}\). Then, when simulating queries to \(\textsc {P}\) on input \(c'\), it forwards them to its own oracle \(\textsc {T}\), to obtain a pair \((\tau _1, \tau _2)\). Finally, \(B\) uses the one available verification query to compute \(\textsc {V}\)’s decision bit in session \(\mathsf {sid}^*\). Finally, \(B\) outputs the games \(\mathrm {H}_b\)’s output. By inspection, it is not hard to verify that \({\Pr \left[ \,{\mathsf {ROR{\hbox {-}}CMA}(b)^{B}_{\mathsf {Auth}'} \Rightarrow \mathsf {true}}\,\right] } = {\Pr \left[ \,{\mathrm {H}_b^{A} \Rightarrow \mathsf {true}}\,\right] }\), which concludes the proof of the lemma. \(\square \)
4 Instantiations
In this section, we will provide examples of \(\mathsf {ror\hbox {-}cma}\)-secure authentication protocols. All of them can be transformed to \(\mathsf {s{\hbox {-}}mim}\)-secure authentication protocols using the transformation from Sect. 3. Table 2 summarizes the resulting protocols compactly.
4.1 Instantiations from LPN
Learning Parity with Noise. For a parameter \(0 < \gamma \le 1/2\), we define the Bernoulli distribution \(\mathcal {B}_\gamma \) that assigns \(e \mathop {\leftarrow }\limits ^{{\scriptscriptstyle \$}}\mathcal {B}_\gamma \) the values 1 and 0 with probabilities \(\gamma \) and \(1-\gamma \), respectively. If \(\mathcal {D}\) is a distribution over \(\mathbb {D}\), then \(\mathbf {x}\mathop {\leftarrow }\limits ^{{\scriptscriptstyle \$}}\mathcal {D}^n\) denotes the n-fold distribution where each component of \(\mathbf {x}\in \mathbb {D}^n\) is chosen according to \(\mathcal {D}\).
To define the \(\mathsf {LPN}_{\ell ,\gamma }\) problem in dimension \(\ell \in {{\mathbb N}}\) and Bernoulli parameter \(0 < \gamma \le 1/2\) we introduce the \(\mathsf {LPN}\) advantage as the quantity
where \(\mathbf {s}\mathop {\leftarrow }\limits ^{{\scriptscriptstyle \$}}\mathbb {F}_2^\ell \) and \(\textsc {LPN}_{\mathbf {s},\alpha }\) (\(\alpha \in \{\gamma , 1/2\}\)) returns \((\mathbf {r}, \mathbf {r}^T \cdot \mathbf {s}+ e)\) for \(\mathbf {r}\mathop {\leftarrow }\limits ^{{\scriptscriptstyle \$}}\mathbb {F}_2^{\ell }\) and \(e \mathop {\leftarrow }\limits ^{{\scriptscriptstyle \$}}\mathcal {B}_\alpha \). Note that oracle \(\textsc {LPN}_{\mathbf {s},1/2}\) always returns uniform \((\mathbf {r}, z) \mathop {\leftarrow }\limits ^{{\scriptscriptstyle \$}}\mathbb {F}_2^{\ell } \times \mathbb {F}_2\). We say that the \(\mathsf {LPN}_{\ell ,\gamma }\) is \((t,q,\epsilon )\)-hard if for all attackers \(A\) with time complexity t, making at most q oracle queries, we have \(\mathbf {Adv}^{\mathsf {LPN}}_{}(A) \le \epsilon \).
ROR-CMA secure Protocol. Let \(n=O(\ell )\) denote the number of repetitions, \(\gamma \) the parameter of the Bernoulli distribution, and \(\gamma ':=1/4+\gamma /2\) controls the correctness error. The following authentication protocol \({\mathsf {Auth}}'_\mathsf {LPN}=\{\mathsf {Gen}',\mathsf {P}',\mathsf {V}'\}\) originates from [20]. It has associated key space \(\mathcal{K}=(\mathbb {F}_2^{\ell })^2\), tag space \(\mathcal{T}= \mathcal{T}_1 \times \mathcal{T}_2 = \mathbb {F}_2^{\ell \times n} \times \mathbb {F}_2^n\), and challenge space \(\mathcal{C}=\mathbb {F}_2^{\ell }\).
-
Key Generation. The key-generation algorithm \(\mathsf {Gen}'\) outputs a secret key \(K=(\mathbf {k}_1,\mathbf {k}_2) \mathop {\leftarrow }\limits ^{{\scriptscriptstyle \$}}(\mathbb {F}_2^{\ell })^2\).
-
Challenge. The challenge is generated by the verifier \(\mathsf {V}'\) as \(\mathbf {c}\mathop {\leftarrow }\limits ^{{\scriptscriptstyle \$}}\mathbb {F}_2^\ell \).
-
Response. The response \(\tau =(\tau _1,\tau _2)\) to challenge \(\mathbf {c}\in \mathbb {F}_2^\ell \) is computed by the prover \(\mathsf {P}'\) by sampling \(\mathbf {R}\mathop {\leftarrow }\limits ^{{\scriptscriptstyle \$}}\mathbb {F}_2^{\ell \times n}\) and computing \(\tau = (\mathbf {R}, \mathbf {R}^T \cdot (\mathbf {M}_\mathbf {c}\cdot \mathbf {k}_1 + \mathbf {k}_2) + \mathbf {e})\), where \(\mathbf {e}\mathop {\leftarrow }\limits ^{{\scriptscriptstyle \$}}\mathcal {B}^n_\gamma \). (Recall that \(\mathbf {M}_\mathbf {c}\) is the matrix representation of the finite field multiplication with \(\mathbf {c}\).)
-
Verification. Given challenge \(\mathbf {c}\in \mathbb {F}_2^\ell \) and response \(\tau = (\mathbf {R}, \mathbf {z}) \in \mathbb {F}_2^{\ell \times n} \times \mathbb {F}_2^n\), the verifier \(\mathsf {V}'\) outputs \(\mathsf {accept}\) iff: \( rank (\mathbf {R}) = n\) and \(|\mathbf {R}^T \cdot (\mathbf {M}_\mathbf {c}\cdot \mathbf {k}_1 + \mathbf {k}_2) - \mathbf {z}|\le \gamma ' n\).
With the choice of \(\gamma ' = 1/4+\gamma /2\), \({\mathsf {Auth}}'_\mathsf {LPN}\) has \(2^{-O(n)}\) completeness error [20, Theorem 4]. Further, it has \(\epsilon \)-sparse right tags, where \(\epsilon ={\Pr [\,{\mathbf {z}\le \gamma ' n \mid \mathbf {z}\mathop {\leftarrow }\limits ^{{\scriptscriptstyle \$}}\mathbb {F}_2^n}\,]} \le 2^{-O(n)}\), using the Hoeffding bound.
The proof of the following theorem is postponed to Appendix A.2.
Theorem 7
If \(\mathsf {LPN}_{\ell ,\gamma }\) is \((t,nq,\epsilon )\)-hard, then \({\mathsf {Auth}}'_\mathsf {LPN}\) is \((t', q, \epsilon )\)-\(\mathsf {ror\hbox {-}cma}\)-secure with \(t\approx t'\).
There exists an alternative \(\mathsf {ror\hbox {-}cma}\)-secure authentication protocol [10, 20] which defines \(\tau _2=\mathbf {R}^T \cdot \mathbf {k}_{\downarrow \mathbf {c}}+\mathbf {e}\), where \(\mathbf {k}_{\downarrow \mathbf {c}}\) is the projection of \(\mathbf {k}\) with respect to all \(\ell \) non-zero bits of \(\mathbf {c}\in \mathcal{C}:= \{\mathbb {F}_2^{2\ell }\;:\; |\mathbf {c}|=\ell \}\).
MiM secure Protocol. A \(\mathsf {s{\hbox {-}}mim}\)-secure 2-round authentication protocol \(\mathsf {Auth}_\mathsf {LPN}\) is obtained via the generic transformation from Sect. 3. An example instantiation using the almost pairwise independent hash function from Sect. 2 is given in Table 2.
Trade-off. For all \(\mathsf {LPN}\)-based protocols there exists a natural trade-off between key-size and communication complexity, as we will explain now. In the \(\mathsf {ror\hbox {-}cma}\)-secure protocol \({\mathsf {AuthT}}'_\mathsf {LPN}\) we can chose the key as \((\mathbf {K}_1, \mathbf {K}_2) \mathop {\leftarrow }\limits ^{{\scriptscriptstyle \$}}({{\mathbb Z}}_2^{\ell \times n})^2\) and define the response to a challenge \(\mathbf {c}\in F_2^\ell \) as \((\mathbf {r}, (\mathbf {M}_\mathbf {c}\cdot \mathbf {K}_1 + \mathbf {K}_2) \cdot \mathbf {r}+ \mathbf {e}\in \mathbb {F}_2^{\ell } \times \mathbb {F}_2^{n}\), where \(\mathbf {r}\mathop {\leftarrow }\limits ^{{\scriptscriptstyle \$}}\mathbb {F}_2^\ell \). In the resulting \(\mathsf {s{\hbox {-}}mim}\)-secure protocol we can use the specific pairwise independent hash function \(\mathsf {H}_{\mathbf {S}_1,\mathbf {s}_2}(\mathbf {r}) := \mathbf {S}_1 \mathbf {r}+\mathbf {s}_2\), where \((\mathbf {S}_1,\mathbf {s}_2) \in \mathbb {F}_2^{\ell \times n} \times \mathbb {F}_2^n\). The response to a challenge \(\mathbf {c}\) is computed as \(\sigma = (\mathbf {r}, \mathbf {z})\), where

This can be rewritten as \(\mathbf {z}= (\mathbf {M}_\mathbf {c}\cdot \mathbf {X}_1 + \mathbf {X}_2) \cdot \mathbf {r}+ \mathbf {e}\circ \mathbf {x}_3 +\mathbf {x}_4 \) using the substitutions
The resulting protocol \(\mathsf {AuthT}_\mathsf {LPN}\) is described in Table 2.
4.2 Instantiations from Field-LPN
Field Learning Parity with Noise. To define the \(\mathsf {Field\hbox {-}LPN}_{\ell ,\gamma }\) problem over the extension field \((\mathbb {F}_{2^\ell },\circ ,+)\) and Bernoulli parameter \(0 < \gamma \le 1/2\), we introduce the \(\mathsf {Field\hbox {-}LPN}\) advantage as the quantity
where \(\mathbf {s}\mathop {\leftarrow }\limits ^{{\scriptscriptstyle \$}}\mathbb {F}_{2^\ell }\) and \(\textsc {FLPN}_{\mathbf {s},\alpha }\) returns \((\mathbf {r}, \mathbf {r}\circ \mathbf {s}+ \mathbf {e})\) for \(\mathbf {r}\mathop {\leftarrow }\limits ^{{\scriptscriptstyle \$}}\mathbb {F}_{2^\ell }\) and \(\mathbf {e}\mathop {\leftarrow }\limits ^{{\scriptscriptstyle \$}}\mathcal {B}^\ell _\alpha \). Note that \(\textsc {FLPN}_{\mathbf {s},1/2}\) always returns uniform \((\mathbf {r}, \mathbf {z}) \mathop {\leftarrow }\limits ^{{\scriptscriptstyle \$}}(\mathbb {F}_{2^\ell })^2\). We say that the \(\mathsf {Field\hbox {-}LPN}_{\ell ,\gamma }\) is \((t,q,\epsilon )\)-hard if for all attackers \(A\) with time complexity t making at most q oracle queries, we have \(\mathbf {Adv}^{\mathsf {Field\hbox {-}LPN}}_{}(A) \le \epsilon \).
ROR-CMA secure Protocol. Let \(\gamma \) the parameter of the Bernoulli distribution, and \(\gamma ':=1/4+\gamma /2\) controls the correctness error. We use \(\mathbb {F}=\mathbb {F}_{2^\ell }\) to denote the finite field. The following authentication protocol \({\mathsf {Auth}}'_\mathsf {Field\hbox {-}LPN}=\{\mathsf {Gen}',\mathsf {P}',\mathsf {V}'\}\) originates from [15]. It has associated key space \(\mathcal{K}=\mathbb {F}^2\), split tag space \(\mathcal{T}= \mathcal{T}_1 \times \mathcal{T}_2 = \mathbb {F}\times \mathbb {F}\), and challenge space \(\mathcal{C}=\mathbb {F}\).
-
Key Generation. The key-generation algorithm \(\mathsf {Gen}'\) outputs a secret key \(K=(\mathbf {k}_1,\mathbf {k}_2) \mathop {\leftarrow }\limits ^{{\scriptscriptstyle \$}}\mathbb {F}^2\).
-
Challenge. The challenge is generated by the verifier \(\mathsf {V}'\) as \(\mathbf {c}\mathop {\leftarrow }\limits ^{{\scriptscriptstyle \$}}\mathbb {F}\).
-
Response. The response \(\tau =(\tau _1,\tau _2)\) to challenge \(c \in \mathbb {F}\) is computed by the prover \(\mathsf {P}'\) as \(\tau = (\mathbf {r}, \mathbf {r}\circ (\mathbf {k}_1 \circ \mathbf {c}+ \mathbf {k}_2) + \mathbf {e})\), where \(\mathbf {r}\mathop {\leftarrow }\limits ^{{\scriptscriptstyle \$}}\mathbb {F}\), \(\mathbf {e}\mathop {\leftarrow }\limits ^{{\scriptscriptstyle \$}}\mathcal {B}^\ell _\gamma \).
-
Verification. Given challenge \(c \in \mathbb {F}\) and response \(\tau = (\mathbf {r}, \mathbf {z}) \in \mathbb {F}^2\), the verifier \(\mathsf {V}'\) outputs \(\mathsf {accept}\) iff \(|\mathbf {r}\circ (\mathbf {k}_1 \circ \mathbf {c}+ \mathbf {k}_2) - \mathbf {z}|\le \gamma ' n\).
As in the \(\mathsf {LPN}\) case, \({\mathsf {Auth}}'_\mathsf {Field\hbox {-}LPN}\) has \(2^{-O(\ell )}\) completeness error and \(2^{-O(\ell )}\)-sparse right tags. The proof of the following theorem is similar to that of Theorem 7 and is therefore omitted.
Theorem 8
If \(\mathsf {Field\hbox {-}LPN}_{\ell ,\gamma }\) is \((t,q,\epsilon )\)-hard, then \({\mathsf {Auth}}'_\mathsf {Field\hbox {-}LPN}\) is \((t', q, \epsilon )\)-\(\mathsf {ror\hbox {-}cma}\)-secure with \(t' \approx t\).
MiM secure Protocol. We now apply our generic transformation from Sect. 3 to \({\mathsf {Auth}}'_\mathsf {Field\hbox {-}LPN}\) to obtain a \(\mathsf {s{\hbox {-}}mim}\)-secure protocol. The key consists of \((\mathbf {k}_1, \mathbf {k}_2,{K_\mathbb {F}},\mathbf {s}_1,\mathbf {s}_2)\), where we use the concrete pairwise-independent hash function \(\mathsf {H}_{\mathbf {s}_1, \mathbf {s}_2}(\mathbf {r}) = \mathbf {s}_1 \circ \mathbf {r}+ \mathbf {s}_2\). The response to a challenge \(\mathbf {c}\) is computed as \(\sigma = (\mathbf {r}, \mathbf {z})\), where \(\mathbf {z}= (\mathbf {r}\circ (\mathbf {k}_1' \circ \mathbf {c}+ \mathbf {k}_2') + \mathbf {e}) \circ {K_\mathbb {F}}+ \mathbf {s}_1 \circ \mathbf {r}+ \mathbf {s}_2 = (\mathbf {r}\circ (\mathbf {k}_1' \circ {K_\mathbb {F}}\circ \mathbf {c}+ \mathbf {k}_2' \circ {K_\mathbb {F}}+\mathbf {s}_1) + \mathbf {e}\circ {K_\mathbb {F}}+ \mathbf {s}_2.\) This can be written as \(\mathbf {z}= (\mathbf {r}\circ (\mathbf {x}_1 \circ \mathbf {c}+ \mathbf {x}_2) + \mathbf {e}\circ \mathbf {x}_3 + \mathbf {x}_4\) using the substitutions \(\mathbf {x}_1 := \mathbf {k}_1 \circ {K_\mathbb {F}}, \quad \mathbf {x}_2 := \mathbf {k}_2 \circ {K_\mathbb {F}}+\mathbf {s}_1, \quad \mathbf {x}_3 := {K_\mathbb {F}}, \quad \mathbf {x}_4 := \mathbf {s}_2.\) The resulting simplified protocol \(\mathsf {Auth}_\mathsf {Field\hbox {-}LPN}\) is given in Table 2.
4.3 Instantiations from Weak PRFs
Weak Pseudorandom Function. Let \(\mathcal {F}\) be a function family \(F : \mathbb {K}\times \mathbb {D}\rightarrow \mathbb {F}\). To define the \({\mathsf {wprf}}_{\mathcal {F}}\) assumption over function family \(\mathcal {F}\) we introduce the \({\mathsf {wprf}}\) advantage of an adversary \(A\) as the quantity
where \(x \mathop {\leftarrow }\limits ^{{\scriptscriptstyle \$}}\mathbb {K}\), \(\textsc {F}_{x}\) returns (r, F(x, r)) for \(r \mathop {\leftarrow }\limits ^{{\scriptscriptstyle \$}}\mathbb {D}\), and \(\textsc {U}\) returns uniform \((r,z) \mathop {\leftarrow }\limits ^{{\scriptscriptstyle \$}}\mathbb {D}\times \mathbb {F}\). We say that \(\mathcal {F}\) is a \((t,q,\epsilon )\)-weak PRF if for all attackers \(A\) with time complexity t, making at most q oracle queries, we have \(\mathbf {Adv}^{{\mathsf {wprf}}}_{\mathcal {F}}(A) \le \epsilon \).
ROR-CMA secure Protocol. We define an authentication protocols \({\mathsf {Auth}}'_{\mathsf {wprf}}=\{\mathsf {Gen}',\mathsf {P}',\mathsf {V}'\}\) with associated key space \(\mathcal{K}=\mathbb {K}^\ell \), split tag space \(\mathcal{T}= \mathcal{T}_1 \times \mathcal{T}_2 = \mathbb {D}\times \mathbb {F}\), and challenge space \(\mathcal{C}=\{0,1\}^\ell \).
-
Key Generation. The key-generation algorithm \(\mathsf {Gen}'\) outputs a secret key \(K=(x_{1,0}, \ldots , x_{\ell ,0}, x_{1,1}, \ldots , x_{\ell ,1}) \mathop {\leftarrow }\limits ^{{\scriptscriptstyle \$}}\mathbb {K}^{2 \times \ell }\).
-
Challenge. The challenge is generated by the verifier \(\mathsf {V}'\) as \(c \mathop {\leftarrow }\limits ^{{\scriptscriptstyle \$}}\{0,1\}^\ell \).
-
Response. The response \(\tau =(\tau _1,\tau _2)\) to challenge \(c \in \{0,1\}^\ell \) is computed by the prover \(\mathsf {P}'\) as \(\tau = (r, z=\sum _{i=1}^\ell F(x_{i,c_i},r))\), where \(r \mathop {\leftarrow }\limits ^{{\scriptscriptstyle \$}}\mathbb {D}\).
-
Verification. Given challenge \(c \in \{0,1\}^\ell \) and response \(\tau = (r,z) \in \mathbb {D}\times \mathbb {F}\), the verifier \(\mathsf {V}'\) outputs \(\mathsf {accept}\) iff \(\sum _{i=1}^\ell F(x_{i,c_i},r) = z\).
The protocol has perfect completeness and \(1/|\mathbb {F}|\)-sparse right tags. It is easy to extend \({\mathsf {Auth}}'_{\mathsf {wprf}}\) to randomized weak PRFs (with additive noise), as defined in [22]. This way we obtain protocols from a more general class of assumptions, such as Toeplitz-LPN [22]. The proof of the following theorem is in Appendix A.2.
Theorem 9
If \(\mathcal {F}\) is a \((t,q,\epsilon )\)-weak PRF, then \({\mathsf {Auth}}'_{\mathsf {wprf}}\) is \((t', q, \epsilon /\ell )\)-\(\mathsf {ror\hbox {-}cma}\)-secure with \(t' \approx t\).
4.4 Instantiation from DDH
The DDH Problem. Let \(\mathcal {G}\) be a family of groups with \(\mathcal {G}_n = (\mathbb {G}, g,p)\), where \(\mathbb {G}\) is a cyclic group of prime-order p with \(\lceil \log p \rceil =n\) and g generates \(\mathbb {G}\). To define the \({\mathsf {ddh}}_{\mathcal {G}}\) problem over group family \(\mathcal {G}\) we introduce the \({\mathsf {ddh}}\) advantage as the quantity
where \(x \mathop {\leftarrow }\limits ^{{\scriptscriptstyle \$}}{{\mathbb Z}}_p\) and \(\textsc {DDH}_{x}\) returns \((R, R^x)\) for \(R \mathop {\leftarrow }\limits ^{{\scriptscriptstyle \$}}{{\mathbb Z}}_p\), and \(\textsc {U}\) returns uniform \((R,Z) \mathop {\leftarrow }\limits ^{{\scriptscriptstyle \$}}\mathbb {G}^2\). We say that \({\mathsf {ddh}}_{\mathcal {G}}\) is \((t,q,\epsilon )\)-hard if for all attackers \(A\) with time complexity t making at most q oracle queries, we have \(\mathbf {Adv}^{{\mathsf {ddh}}}_{}(A) \le \epsilon \). Note that classical \({\mathsf {ddh}}\) hardness is exactly \((t',1,\epsilon ')\)-hardness of \({\mathsf {ddh}}_\mathcal {G}\) and by the random self-reducibility of \({\mathsf {ddh}}\) we have that \({\mathsf {ddh}}_{\mathcal {G}}\) is \((t,q,\epsilon )\)-hard iff it is \((t',1,\epsilon ')\)-hard with \(t \approx t'\) and \(\epsilon \approx \epsilon '\).
ROR-CMA secure Protocol. We define an authentication protocol \({\mathsf {Auth}}'_{\mathsf {ddh}}=\{\mathsf {Gen}',\mathsf {P}',\mathsf {V}'\}\) with associated key space \(\mathcal{K}={{\mathbb Z}}_p^2\), split tag space \(\mathcal{T}= \mathcal{T}_1 \times \mathcal{T}_2 = \mathbb {G}\times \mathbb {G}\), and challenge space \(\mathcal{C}={{\mathbb Z}}_p\).
-
Key Generation. The key-generation algorithm \(\mathsf {Gen}'\) outputs a secret key \(K=(y_1,y_2) \mathop {\leftarrow }\limits ^{{\scriptscriptstyle \$}}{{\mathbb Z}}_p^2\).
-
Challenge. The challenge is generated by the verifier \(\mathsf {V}'\) as \(\mathbf {c}\mathop {\leftarrow }\limits ^{{\scriptscriptstyle \$}}{{\mathbb Z}}_p\).
-
Response. The response \(\tau =(\tau _1,\tau _2)\) to challenge \(c \in \mathbb {F}_p\) is computed by the prover \(\mathsf {P}'\) as \(\tau = (R, R^{y_1 \cdot c + y_2})\), where \(R \mathop {\leftarrow }\limits ^{{\scriptscriptstyle \$}}\mathbb {G}\).
-
Verification. Given challenge \(c \in {{\mathbb Z}}_p\) and response \(\tau = (R,Z) \in \mathbb {G}^2\), the verifier \(\mathsf {V}'\) outputs \(\mathsf {accept}\) iff \(R^{y_1 \cdot c + y_2} = Z\).
The protocol \({\mathsf {Auth}}'_{\mathsf {ddh}}\) has perfect completeness and 1 / p-sparse right tags.
Theorem 10
If \({\mathsf {ddh}}_{\mathcal {G}}\) is \((t,q,\epsilon )\)-hard, then \({\mathsf {Auth}}'_{\mathsf {ddh}}\) is \((t', q, \epsilon )\)-\(\mathsf {ror\hbox {-}cma}\)-secure with \(t' \approx t\).
The proof is similar to the one of Theorem 7 and is omitted.
MiM secure Protocol. We now apply our generic transformation from Sect. 3 to \({\mathsf {Auth}}'_{\mathsf {ddh}}\) to obtain a \(\mathsf {s{\hbox {-}}mim}\)-secure protocol. By using the field structure of \({{\mathbb Z}}_p\) in the exponent, we can use the concrete pairwise-independent hash function \(\mathsf {H}_{s_1, S_2}(R) = R^{s_1} \cdot S_2 \in \mathbb {G}\), where \((s_1, S_2) \in {{\mathbb Z}}_p \times \mathbb {G}\). The key of \(\mathsf {Auth}_{\mathsf {ddh}}\) consists of \((y_1, y_2,{K_\mathbb {F}},s_1,S_2)\). We now show that the key of \(\mathsf {Auth}_{\mathsf {ddh}}\) can be shrinked by two elements, see Table 2. The response to a challenge c is computed as \(\sigma = (R, Z)\), where \(Z = (R^{y_1 \cdot c + y_2})^{K_\mathbb {F}}\cdot R^{s_1} S_2 = R^{y_1 {K_\mathbb {F}}\cdot c + y_2 {K_\mathbb {F}}+s_1} S_2.\) This can be written as \(Z = R^{x_1 c + x_2} S_2\) using the substitutions \( x_1:= y_1 {K_\mathbb {F}}, \quad x_2 := y_2 {K_\mathbb {F}}+s_1, \quad X := S_3.\) The resulting simplified protocol \(\mathsf {Auth}_{\mathsf {ddh}}\) is given in Table 2.
Notes
- 1.
This representation is unique once the irreducible polynomial f defining \(\mathbb {F}_{2^n} = \mathbb {F}_2[x]/(f)\) is fixed.
- 2.
This is w.l.o.g., as we can always represent \(\mathcal{T}_2\) as a bit-string \(\{0,1\}^t\) for some \(t \in {{\mathbb N}}\) which we associate with \(\mathbb {F}_{2^t}\).
References
Akavia, A., Bogdanov, A., Guo, S., Kamath, A., Rosen, A.: Candidate weak pseudorandom functions in ac\(^{0}\); mod\(_{2}\). In: ITCS, pp. 251–260 (2014)
Applebaum, B., Cash, D., Peikert, C., Sahai, A.: Fast cryptographic primitives and circular-secure encryption based on hard learning problems. In: Halevi, S. (ed.) CRYPTO 2009. LNCS, vol. 5677, pp. 595–618. Springer, Heidelberg (2009)
Bellare, M., Rogaway, P.: Entity authentication and key distribution. In: Stinson, D.R. (ed.) CRYPTO 1993. LNCS, vol. 773, pp. 232–249. Springer, Heidelberg (1994)
Bellare, M., Rogaway, P.: The security of triple encryption and a framework for code-based game-playing proofs. In: Vaudenay, S. (ed.) EUROCRYPT 2006. LNCS, vol. 4004, pp. 409–426. Springer, Heidelberg (2006)
Bernstein, D.J., Lange, T.: Never trust a bunny. In: Hoepman, J.-H., Verbauwhede, I. (eds.) RFIDSec 2012. LNCS, vol. 7739, pp. 137–148. Springer, Heidelberg (2013)
Blum, A., Furst, M.L., Kearns, M., Lipton, R.J.: Cryptographic primitives based on hard learning problems. In: Stinson, D.R. (ed.) CRYPTO 1993. LNCS, vol. 773, pp. 278–291. Springer, Heidelberg (1994)
Blum, A., Kalai, A., Wasserman, H.: Noise-tolerant learning, the parity problem, and the statistical query model. In: 32nd ACM STOC, pp. 435–440, Portland, Oregon, USA, May 21–23, 2000. ACM Press (2000)
Bringer, J., Chabanne, H., Dottax, E.: HB\(^{++}\): a lightweight authentication protocol secure against some attacks. In: SecPerU, pp. 28–33 (2006)
Damgård, I., Park, S.: Towards optimally efficient secret-key authentication from PRG. Cryptology ePrint Archive, Report 2014/426 (2014). http://eprint.iacr.org/2014/426
Dodis, Y., Kiltz, E., Pietrzak, K., Wichs, D.: Message authentication, revisited. In: Pointcheval, D., Johansson, T. (eds.) EUROCRYPT 2012. LNCS, vol. 7237, pp. 355–374. Springer, Heidelberg (2012)
Duc, D.N., Kim, K.: Securing HB\(^+\) against GRS man-in-the-middle attack. In: SCIS (2007)
Fiat, A., Shamir, A.: How to prove yourself: practical solutions to identification and signature problems. In: Odlyzko, A.M. (ed.) CRYPTO 1986. LNCS, vol. 263, pp. 186–194. Springer, Heidelberg (1987)
Gilbert, H., Robshaw, M., Seurin, Y.: HB\(^{\sharp }\): increasing the security and efficiency of HB\(^{+}\). In: Smart, N.P. (ed.) EUROCRYPT 2008. LNCS, vol. 4965, pp. 361–378. Springer, Heidelberg (2008)
Gilbert, H., Robshaw, M., Seurin, Y.: How to encrypt with the LPN problem. In: Aceto, L., Damgård, I., Goldberg, L.A., Halldórsson, M.M., Ingólfsdóttir, A., Walukiewicz, I. (eds.) ICALP 2008, Part II. LNCS, vol. 5126, pp. 679–690. Springer, Heidelberg (2008)
Heyse, S., Kiltz, E., Lyubashevsky, V., Paar, C., Pietrzak, K.: Lapin: an efficient authentication protocol based on ring-LPN. In: Canteaut, A. (ed.) FSE 2012. LNCS, vol. 7549, pp. 346–365. Springer, Heidelberg (2012)
Hopper, N.J., Blum, M.: Secure human identification protocols. In: Boyd, C. (ed.) ASIACRYPT 2001. LNCS, vol. 2248, pp. 52–66. Springer, Heidelberg (2001)
Jain, A., Krenn, S., Pietrzak, K., Tentes, A.: Commitments and efficient zero-knowledge proofs from learning parity with noise. In: Wang, X., Sako, K. (eds.) ASIACRYPT 2012. LNCS, vol. 7658, pp. 663–680. Springer, Heidelberg (2012)
Juels, A., Weis, S.A.: Authenticating pervasive devices with human protocols. In: Shoup, V. (ed.) CRYPTO 2005. LNCS, vol. 3621, pp. 293–308. Springer, Heidelberg (2005)
Katz, J., Shin, J.S., Smith, A.: Parallel and concurrent security of the HB and HB+ protocols. J. Cryptol. 23(3), 402–421 (2010)
Kiltz, E., Pietrzak, K., Cash, D., Jain, A., Venturi, D.: Efficient authentication from hard learning problems. In: Paterson, K.G. (ed.) EUROCRYPT 2011. LNCS, vol. 6632, pp. 7–26. Springer, Heidelberg (2011)
Levieil, É., Fouque, P.-A.: An improved LPN algorithm. In: De Prisco, R., Yung, M. (eds.) SCN 2006. LNCS, vol. 4116, pp. 348–359. Springer, Heidelberg (2006)
Lyubashevsky, V., Masny, D.: Man-in-the-middle secure authentication schemes from LPN and weak PRFs. In: Canetti, R., Garay, J.A. (eds.) CRYPTO 2013, Part II. LNCS, vol. 8043, pp. 308–325. Springer, Heidelberg (2013)
Maurer, U.M., Sjödin, J.: A fast and key-efficient reduction of chosen-ciphertext to known-plaintext security. In: Naor, M. (ed.) EUROCRYPT 2007. LNCS, vol. 4515, pp. 498–516. Springer, Heidelberg (2007)
Maurer, U.M., Tessaro, S.: Basing PRFs on constant-query weak prfs: minimizing assumptions for efficient symmetric cryptography. In: Pieprzyk, J. (ed.) ASIACRYPT 2008. LNCS, vol. 5350, pp. 161–178. Springer, Heidelberg (2008)
Munilla, J., Peinado, A.: HB-MP: a further step in the hb-family of lightweight authentication protocols. Computer Networks 51(9), 2262–2267 (2007)
Ouafi, K., Overbeck, R., Vaudenay, S.: On the security of HB# against a man-in-the-middle attack. In: Pieprzyk, J. (ed.) ASIACRYPT 2008. LNCS, vol. 5350, pp. 108–124. Springer, Heidelberg (2008)
Regev, O.: On lattices, learning with errors, random linear codes, and cryptography. In: Gabow, H.N., Fagin, R. (eds.) 37th ACM STOC, Baltimore, Maryland, USA, May 22–24, 2005, pp. 84–93. ACM Press
Acknowledgements
David Cash was partially supported by NSF grant CNS-1453132.
Eike Kiltz was supported by a Sofja Kovalevskaja Award of the Alexander von Humboldt Foundation and ERC Project ERCC (FP7/615074).
Stefano Tessaro was partially supported by NSF grants CNS-1423566 and the Glen and Susanne Culler Chair.
This work was done in part while David Cash and Stefano Tessaro were visiting the Simons Institute for the Theory of Computing, supported by the Simons Foundation and by the DIMACS/Simons Collaboration in Cryptography through NSF grant CNS-1523467.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
A Omitted Proofs
A Omitted Proofs
1.1 A.1 Proof of Theorem 7
Proof
Let \(A\) be an adversary in the \(\mathsf {ROR{\hbox {-}}CMA}^{A}_{\mathsf {Auth}'}(b)\) security game. We define an adversary \(B^{\textsc {LPN}_{\mathbf {s},\alpha }()}\) against the \(\mathsf {LPN}_{\ell ,\gamma }\) problem, where \(\alpha \in \{\gamma ,\frac{1}{2} \}\) is unknown.
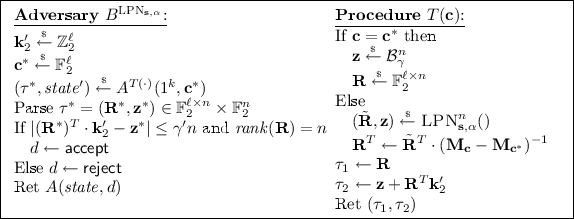
Note that due to the finite field properties of the linear map \(\mathbf {M}_\mathbf {c}\), matrix \(\mathbf {M}_\mathbf {c}-\mathbf {M}_{\mathbf {c}^*}\) is always invertible for \(\mathbf {c}\ne \mathbf {c}^*\). Adversary \(B\) implicitly defines \(\mathbf {k}_1 := \mathbf {s}\) and \(\mathbf {k}_2 := -\mathbf {M}_{\mathbf {c}^*} \cdot \mathbf {k}_1 + \mathbf {k}_2'\), where \(\mathbf {s}\) is the \(\mathsf {LPN}\) secret. As \(\mathbf {k}_2'\) is uniform, the key \(\mathbf {k}=(\mathbf {k}_1,\mathbf {k}_2)\) has the correct distribution. The definition of \(K=(\mathbf {k}_1,\mathbf {k}_2)\) implies that
As \(K(\mathbf {c}^*) = \mathbf {k}_2'\), the bit d is always computed correctly by \(B\). We now consider the distribution of \(\textsc {T}(\mathbf {c})\). First note that \(\tau _1\) is always a uniform matrix in \(\mathbb {F}_2^{\ell \times n}\). For \(\mathbf {c}=\mathbf {c}^*\), \(\mathbf {z}\) is Bernoulli distributed and, using Eq. (6), \(\tau _2 = \mathbf {R}^T \mathbf {k}_2'+\mathbf {z}\) is distributed as computed by prover \(\mathsf {P}'\). Further, for \(\mathbf {c}\ne \mathbf {c}^*\) we have
where \(\mathbf {e}\mathop {\leftarrow }\limits ^{{\scriptscriptstyle \$}}\mathcal {B}_\alpha ^\ell \). If \(\alpha = \frac{1}{2}\), then \(\tau _1\) and \(\tau _2\) are uniformly distributed and
If \(\alpha = \gamma \), then \(\tau =(\tau _1,\tau _2)\) is distributed as computed by prover \(\mathsf {P}'\). Hence \({\Pr \left[ \,{B^{\textsc {LPN}_{\mathbf {s},\gamma }()} \Rightarrow \mathsf {true}}\,\right] } = {\Pr [\,{\mathsf {ROR{\hbox {-}}CMA}^{A}_{\mathsf {Auth}'}(1) \Rightarrow \mathsf {true}}\,]}\). The last two equations provide \(\mathbf {Adv}^{\mathsf {LPN}}_{}(B) = \mathbf {Adv}^{\mathsf {ror\hbox {-}cma}}_{\mathsf {Auth}'}(A)\), where the running time of \(B\) is approximately that of \(A\). \(\square \)
1.2 A.2 Proof of Theorem 9
Proof
Let \(A\) be an attacker in the \(\mathsf {ROR{\hbox {-}}CMA}(1)\) game. We now describe games \(\mathsf {G}_{0}, \ldots , \mathsf {G}_{\ell }\) that are exactly like the \(\mathsf {ROR{\hbox {-}}CMA}(1)\) game, but with modified procedure T(c). For \(j \in \{0,\ldots , \ell -1\}\), let \(S_j : \{0,1\}^j \rightarrow \mathbb {F}\) be a random function, where \(S_0(\varepsilon )\) is defined to be 0. Note that \(S_j\) can be efficiently simulated by lazy evaluation.
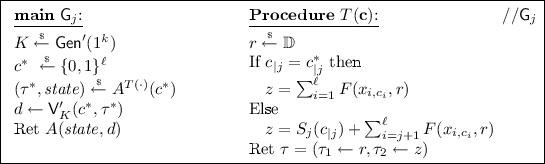
Note that in game \(\mathsf {G}_{0}\) all tags \(\tau \) are computed correctly by \(\textsc {T}\) and hence \(\mathsf {G}_{0} = \mathsf {ROR{\hbox {-}}CMA}(1)\). Furthermore, in game \(\mathsf {G}_{\ell }\), all tags except for challenge \(\mathbf {c}^*\) are uniform and hence \(\mathsf {G}_{\ell } = \mathsf {ROR{\hbox {-}}CMA}(0)\). The following lemma completes the proof of Theorem 9.
Lemma 11
For any \(j \in \{0,\ldots , \ell -1\}\), there exists an attacker \(B_j\) such that
To prove the lemma, we define an adversary \(B=B_j^{\textsc {O}()}\) (\(0 \le j \le \ell -1\)) against \(\mathcal {F}\), where \(\textsc {O} \in \{\textsc {F}_x, \textsc {U} \}\).

Adversary \(B\) knows all secrets \(x_{i,k}\) except \(x_{j+1,1-c^*_j}\) which he defines implicitly as the secret x from the \(\textsc {F}_x\) oracle. In particular, he knows \(x_{i, c_i^*}\) and the bit d is always computed correctly. It remains to analyze the distribution of \(\textsc {T}(\mathbf {c})\). If \(c_{j+1} = c^*_{j+1}\), then the output of \(\textsc {T}(\mathbf {c})\) in games \(\mathsf {G}_{j}\) and \(\mathsf {G}_{j+1}\) is identical. We now analyze the case \(c_{j+1} \ne c^*_{j+1}\). If \(\textsc {O} = \textsc {F}_x\), then \(z = S_j(c_{|j}) + F(x,r)+ \sum _{i=j}^\ell F(x_{i,c_i},r)= S_j(c_{|j}) + \sum _{i=j+1}^\ell F(x_{i,c_i},r)\) and hence \({\Pr [\,{B^{\textsc {F}_x()} \Rightarrow \mathsf {true}}\,]} = {\Pr [\,{\mathsf {G}_{j}^{A} \Rightarrow \mathsf {true}}\,]}\). If \(\textsc {O} = \textsc {U}\), then \(z = S_j(c_{|j}) + z' + \sum _{i=j+1}^\ell F(x_{i,c_i},r)=S_j(c_{|j+1}) + \sum _{i=j+1}^\ell F(x_{i,c_i},r)\) and hence \({\Pr [\,{B^{\textsc {U}()} \Rightarrow \mathsf {true}}\,]} = {\Pr [\,{\mathsf {G}_{j+1}^{A} \Rightarrow \mathsf {true}}\,]}\). \(\square \)
Rights and permissions
Copyright information
© 2016 International Association for Cryptologic Research
About this paper
Cite this paper
Cash, D., Kiltz, E., Tessaro, S. (2016). Two-Round Man-in-the-Middle Security from LPN. In: Kushilevitz, E., Malkin, T. (eds) Theory of Cryptography. TCC 2016. Lecture Notes in Computer Science(), vol 9562. Springer, Berlin, Heidelberg. https://doi.org/10.1007/978-3-662-49096-9_10
Download citation
DOI: https://doi.org/10.1007/978-3-662-49096-9_10
Published:
Publisher Name: Springer, Berlin, Heidelberg
Print ISBN: 978-3-662-49095-2
Online ISBN: 978-3-662-49096-9
eBook Packages: Computer ScienceComputer Science (R0)