Abstract
We present a ubiquitous system that combines context information, security mechanisms and a transport infrastructure to provide authentication and secure transport of works of art. Authentication is provided for both auctions and exhibitions, where users can use their own mobile devices to authenticate works of art. Transport is provided by a secure protocol that makes use of position–time information and wireless sensors providing context information. The system has been used in several real case studies in the context of the CUSPIS project and continues to be used as a commercial product for the transportation and exhibition of cultural assets in Italy.











Similar content being viewed by others
Notes
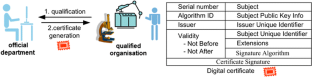
In the CUSPIS project, the private keys are generated by the certification authorities and sealed into a tamper-proof device which is delivered securely to the organisations.
We used RFID tags with 128 KB of memory that maintain full compatibility with the EPC standard [11].
Small fluctuations may be consequence of hardware imprecision.
The search inside the revocation lists is performed based on the GD digital signature S, the UC code and the owner.
References
Mostarda L, Dong C, Dulay N (2008) Place and time authentication of cultural assets. In: 2nd Joint ITRUST and PST conferences on privacy, trust and security (IFIPTM 2008)
Center of Study TCI: Dossier of MUSEUM (2006) http://www.touringclub.it/ricerca/pdf/DOSSIER_MUSEI_2007.pdf
Artprice: 2006 Art Market Trends, Tendances du marche’ de l’art (2006) http://img1.artprice.com/pdf/trends2006.pdf
Jacob J (2002) Counterfeit art—how to keep it out of your collection. Chubb Collectors
Mostarda L, Tocchio A, Inverardi P, Costantini S (2007) A geo time authentication system. In: Proceeding of IFIPTM 2007
Radiocarbon Dating (2002) BBC on line resource. http://www.bbc.co.uk/dna/h2g2/A637418
Thermoluminescence (2002) Minnesota State University. http://www.mnsu.edu/emuseum/archaeology/dating/thermoluminescence.html
Klarreich E (2004) Con artists: Scanning program can discern true art. science news 166:340
CUSPIS demonstration and performance evaluation report (2007) CUSPIS official home page. http://www.cuspis-project.info/demonstrations.htm
Stallings W (2006) Cryptography and network security: principles and practice, 4th edn. Prentice Hall
Web page on EPC global organization (2008) http://www.epcglobalinc.org/home
Buchanan JDR, Cowburn RP, Jausovec AV, Petit D, Seem P, Xiong G, Atkinson D, Fenton K, Allwood DA, Bryan MT (2005) ‘Fingerprinting’ documents and packaging. Nature 436:475
Pozzobon O, Wullems C, Kubic K (2004) Secure tracking using trusted GNSS receivers and Galileo authentication services. J Glob Position Syst 3:200–207
Cultural Heritage Space Identification System (CUSPIS) (2007) European Commission 6th framework program—2nd call Galileo joint undertaking. http://www.epcglobalinc.org/home
Next SpA company (2008) http://www.next.it/site/Home.aspx?content=trasporti
Official web page of Galileo (2008) http://www.galileoju.com
Augello A, Santangelo A, Sorce S, Pilato G, Gentile A, Genco A, Gaglio S (2006) Maga: a mobile archaeological guide at Agrigento. University of Palermo, ICAR_CNR
Pilato G, Augello A, Santangelo A, Gentile A, Gaglio S (2006) An intelligent multimodal site-guide for the “parco archeologico della valle dei templi” in Agrigento. In: Proceedings of first European workshop on intelligent technologies for cultural heritage exploitation, at the 17th European conference on artificial intelligence
Park D, Nam T, Shi C, Golub G, Loan CV (2006) Designing an immersive tour experience system for cultural tour sites. In: Chi ’06 extended abstracts on human factors in computing systems edition, April 22–27. ACM Press, Montréal, Québec, Canada, pp 1193–1198
Vicenzaoro winter: Traceability and guarantee label (2007) http://www.vicenzafiera.it/uk/rassegna/vioro1_2007/crapanzano_en.doc
Juels A (2006) Rfid security and privacy: a research survey. IEEE J Sel Areas Commun
Caputo T (2005) Rfid technology beyond wal-mart. WinesandVines
Web page of the TagStream Company (2008) http://www.tagstreaminc.com
Texas Instruments and VeriSign, Inc. (2007) Securing the pharmaceutical supply chain with RFID and public-key infrastructure technologies
Juels A, Weis SA (2005) Authenticating pervasive devices with human protocols. In: Shoup V (ed) CRYPTO. Volume 3621 of lecture notes in computer science. Springer, pp 293–308
Tuyls P, Batina L (2006) Rfid-tags for anti-counterfeiting. In: Pointcheval D (ed) CT-RSA. Volume 3860 of lecture notes in computer science. Springer, pp 115–131
EPC global standard powered by GS1: Object Naming Service (ONS) 5 Version 1.0 (2005)
Mirowski L (2006) Detecting clone radio frequency identifications tags. Bachelor’s Thesis, School of Computing, University of Tasmania
Lehtonen M, Michahelles F, Fleisch E (2007) Probabilistic approach for location-based authentication. In: 1st International workshop on security for spontaneous interaction IWSSI 2007
Anderson RJ (1998) On the security of digital tachographs. In: ESORICS ’98: proceedings of the 5th European symposium on research in computer security. Springer-Verlag, London, UK, pp 111–125
A GPS based monitoring system (2008) http://www.vehiclegpstrackingsystem.com/
Acknowledgments
This research was supported by UK EPSRC research grants EP/D076633/1 (UBIVAL) and EP/C537181/1 (CAREGRID). We would also like to thank the members of the Policy Research Group at Imperial College, and the CUSPIS partners: the Next S.p.A. research group, Vodafone, and the Italian and Greek ministries who supported our case studies.
Author information
Authors and Affiliations
Corresponding author
Additional information
This article is a revised and extended version of a paper that was presented at the IFIPTM 2008 conference [1].
Rights and permissions
About this article
Cite this article
Mostarda, L., Dong, C. & Dulay, N. Context-based authentication and transport of cultural assets. Pers Ubiquit Comput 14, 321–334 (2010). https://doi.org/10.1007/s00779-009-0233-8
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00779-009-0233-8


