Abstract
Nowadays, the distribution of huge amounts of medical images through open networks in telemedicine applications has become increasingly faster and easier. Therefore, a number of considerations are introduced related to the risks of the illegal use of these images, as total diagnosis depends on them. Indeed, the patient’s data management, storage, and transmission require a technique for boosting security, integrity and privacy measures in telehealthcare services. In fact, in our previous works, we used polynomial decompositions such as Chebychev orthogonal polynomial transform in medical image watermarking. We then customise our tools for finding the best candidate area for embedding the watermark, always seeking to provide the best solution to this issue. In this research, a variation to medical image watermarking approach based on Hermite transform (HT) is suggested for reliable management of medical data. In this approach, the HT is employed as a preprocessing step so as to extract the texture component of the host medical image. Afterward, a sliding window technique is done to select the most suitable regions for watermark embedding. Lastly, the Arnold transform is utilized for encrypting the watermark to strengthen the security of our scheme. Experiments were conducted on various modalities of medical images. Results indicate that the proposed scheme is robust when subjected to various attacks while preserving a high level of security and invisibility factors. Also, our method preserves the quality of medical images with a good embedding capacity. The obtained results support the use of Hermite Polynomials for the implementation of watermarking in the medical imaging context.
Similar content being viewed by others
Explore related subjects
Find the latest articles, discoveries, and news in related topics.Avoid common mistakes on your manuscript.
1 Introduction
Remote medicine is booming during the critical period of the coronavirus pandemic (COVID-19). The current crisis has prompted the world to investigate the health sector and digital transformation. Technological advances in telehealth services are gaining widespread popularity, due to the benefits accruing to healthcare providers, insurers, and patients [40]. Telemedicine has carried the health professionals nearer to the patients for online consultations in a safer way. It’s also an efficient way to provide care in rural areas at any time. With these advances, the paradigm of medical image management, storage, and transmission is an increasing issue for medical institutions because of the relevance of the medical image since it stores patient’s information for diagnosis purposes [12, 50].
Medical images are generated by various digital imaging equipment of various modalities. These images are stored digitally as information objects composed of pixels on different types of storage media. However, any modification, alteration, or corruption of medical image content lead, in most cases, to misdiagnosis and may also lead to death or severe disability. Thus, preventing patient’s information from identity theft, privacy leakage, and possible risks such as authenticity loss and falsification remains a real challenge to take up. Indeed, updating the laws of telehealth practice is not enough, and may endanger the process of innovation and progress of such field. In other words, one must be careful not to fall into a trap of trying to regulate technology. Instead, care must be taken to the use of medical data, and therefore ensuring patient data security must be taken in mind. Traditionally, digital documents are encrypted in such a way as to make them unreadable from the moment of their creation until they are used. This technique is an effective solution during the transmission and storage of the document since this document is no longer protected and there is no more control on its dissemination once encryption is removed [8]. Thus, encryption is an important technique but it is not efficient in solving all the problems of digital data protection. A promissory method to accomplish the above requirements of security is integrating a new technique based on digital watermarking techniques as a value-added tool for a secured medical image transmission in telehealth services [13]. The purpose of this method is to establish the copyright of the content creator [32]. It consists of embedding a watermark, as an imperceptible and detectable information, into the host image so that it could be extracted later even if the watermarked data underwent modifications. Also, the watermark is intended to strengthen the security of data in a permanent manner [38, 43].
To be effective, several factors need to be borne in mind during the watermarking design, such as robustness, imperceptibility, capacity, false-positive rate, computational cost, security, and reversibility [15]. The robustness factor envisages the preservation of the embedded watermark when the watermarked image is subjected to various intentional and unintentional modifications. That is, the watermark should be robust and hard to be destroyed. The level of robustness for a watermarking algorithm may be different for every application and situation [9, 14]. Imperceptibility is an important requirement for digital watermarking in general and, in particular, for medical watermarking. It envisages to preserve the fidelity of the original data. In other words, it is hard to detect the visual contrast between the watermarked data and the host data by the human eye. The hidden watermark could be detected algorithmically only [1]. Capacity is defined using the largest quantity of watermark information which is used for embedding the watermark while fulfilling the robustness and imperceptibility requirements. However, embedding as much watermark data as possible is a more challenging task in digital watermarking [42]. The false-positive rate examines the quality of the watermark extraction process by stating if a watermark exists in unwatermarked data. For the case of watermarked data precondition, the watermark extraction is done with a minimum false positive rate [34, 42]. Computational cost is an important factor for real-time applications. This property evaluates how much time is needed for the whole watermarking process [32]. Security property ensures that, after the extraction process, the extracted watermark is decrypted only by those persons on procession of a secret key [41]. Reversibility is also another important factor for watermarking methods which is preferable for medical and military applications. It refers to the ability to restore the original content from the watermarked one perfectly. In fact, such property is highly required because any small visual degradation to original content that cannot be recovered could lead to a misdiagnosis that might be fatal and may result in possible legal proceedings [28]. In practice, it is noteworthy that there will be tensions between the above requirements, and it is impossible to satisfy all these evaluation criteria for a watermarking system. Therefore, a compromise between them may be applied and must be chosen with careful analysis of the desired application. In this regard, due to the sensitive nature of medical information, the medical image watermarking methods must ensure reversibility, high invisibility, and strong robustness against various modifications [3, 36].
Basically, two principal categories of medical image watermarking techniques can be distinguished: spatial and transform domain [2, 11]. For the first category, the watermark is introduced by changing the pixel values of the host image. These techniques are considered weak due to the restricted capacity on resisting some image processing attacks (compression, image filtering, etc.). The transform-based schemes provide a wide diversity of image feature details [18]. They are also more robust because the watermark is introduced in a transform of the original image. This transform is obtained by applying mathematical methods to extract information from the original data [10]. It should therefore come as no surprise that many researchers will focus on working in the transform domain to get the optimal compromise of the watermarking scheme parameters. Accordingly, various schemes are developed for the second category, such as Discrete Cosine Transform (DCT), Discrete Wavelet Transform (DWT), and Singular Value Decomposition (SVD) [1, 13, 19, 29]. As a matter of fact, increased attention is now being given to moments-based watermarking techniques. The moments are used as image descriptors, i.e. are used for representing and extracting the global features of an image with different degrees. In particular, the orthogonal moment transformations, such as Legendre moments and Tchebyshev moments, have been widely developed in this field due to their computation efficiency and numerical stability [34, 35].
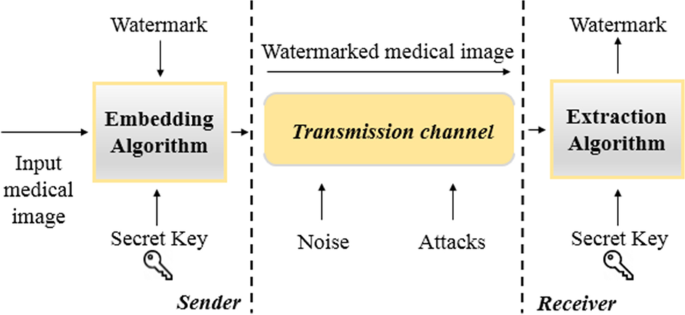
Generally, a secure method of a watermarking in medical applications is processed according to two principal stages, the first being the watermark embedding, the second the watermark extraction. This process is illustrated in Fig. 1 [23]. In the first stage, by the use of an optional secret key, the watermark is introduced into the input medical image so as to generate the watermarked medical image. The introduced watermark should be carefully added with a high level of imperceptibility so as the diagnosis part ought to be kept undistorted and unaffected. After that, the watermarked image may be subjected to various alterations during transmission. In the second stage, the inverse of embedding algorithm is applied to get the watermark from the watermarked medical image.
In our previous works, we exploited Legendre polynomial transform to develop a medical image watermarking technique. This method was subjected to: noise addition, JPEG compression, histogram equalization, and rotation. Two modalities of medical images were used for tests: Ultrasound (US) and Magnetic resonance imaging (MRI). This technique is tested in terms of the PSNR (average PSNR = 59.44 dB) and the NC (average NC = 0.9998). The obtained results are satisfactory as compared to previous works. Also, we previously proposed a watermarking technique for medical image applications based on Chebychev orthogonal polynomial transform [34, 35]. The experimental results demonstrate that this method performs consistently over a set of 120 medical images including 6 modalities (US, X-ray, MRI, PET, CT, and Mammographic). We performed two main experiments: 1) Imperceptibility analysis using the PSNR (63.0151 dB), NC (0.9999), and Local Dissimilarity Map; 2) Robustness analysis against 7 attacks including noise addition, JPEG compression, filtering, rotation, Sharpening, and Histogram Equalization). Therefore, this scheme can be improved to achieve the optimal compromise of watermarking in medical images case.
In this paper, a new and efficient approach has been exploited for a better watermarking method in the case of medical images. This research work has the following objectives:
-
Preparing the medical image for watermark embedding to provide a better region of interest (ROI) selection strategy using another family of polynomial transforms (HT), which represents a good model of the human visual system (HVS), combined with a sliding window technique.
-
Enhancing the security of our scheme by performing the AT. It is used before the embedding step so as to encrypt the watermark, with the ultimate objectives being to provide an additional level of robustness and imperceptibility factors.
This work is structured as follows. Section 2 reviews the related work. Section 3 provides the preliminaries. Section 4 explains the proposed medical image watermarking system design. Section 5 illustrates the experimental results obtained in this study. The final section concludes this work.
2 Related work
A brief literature review of several watermarking techniques is provided below.
2.1 Watermarking schemes for medical images
In the literature, many approaches have been carried out in various applications of medical image watermarking. For instance,
Shehab et al. [37] proposed a fragile watermarking approach based on Arnold transform and SVD to secure the transmission of medical images. The input image is first separated into blocks and the LSB of these blocks is established at zero. After SVD is performed for every block to facilitate the detection of the attacked areas of the watermarked image. The watermark is inserted in two LSBs of each selected block of the original image. The appropriate embedding location is selected using Arnold transform so as to ensure a secure method for hiding image information. Experiments show that this scheme is effective against several attacks such as text addition and copy and past attack.
Rahman et al. [4] suggested a blind reversible watermarking technique for medical images. In that scheme, a chaotic key is employed to determine the location of pixels, from the original host image, to be watermarked by a chaotically generated watermark. The Residue Number System (RNS) is used to transform the rest of the pixels into residues. A polynomial is utilized to addresses the chaotically chosen pixels and a primitive polynomial of degree four is utilized to split these pixels and to get the rest which is added to the watermark image. This technique achieved a high level of invisibility but the capacity of embedding and the robustness against attacks have not been measured. Furthermore, this method does not support the ROI-based medical watermarking strategy.
Ramly et al. [31] conducted a study based on support vector machine (SVM) and spread spectrum (SS) techniques for medical image watermarking technique. In that work, the SVM is used to classify ROI and region of non-interest (RONI) of the host data, whereas SS is applied in the embedding/extraction algorithms within/from the original image pixels located in the RONI part. DCT is applied to the selected part and the watermark, which contains patient medical information, is used for embedding onto the desired DCT coefficients. Furthermore, the robustness of this scheme was not tested against any kind of attack.
Chauhan et al. [13] proposed a secure watermarking technique for medical applications based on the spread-spectrum technique in the wavelet transform domain. First, the DWT and Mexican hat as mother wavelet are used to segment the cover image into four frequency sub-bands. A 50 × 9 binary watermark is inserted into the horizontal (HL) and the vertical (LH) sub-band. This watermark is extracted from the DWT coefficients of the watermarked image. The proposed technique achieved strong robustness for different attacks at the expense of reduced capacity. The experiments were tested on only one medical image modality (CT scan).
Rai et al. [30] designed a hybrid watermarking system for enhanced medical image security using SVM. The inserted data is initially scrambled based on a unique key. The host image is classified into ROI/RONI areas using SVM. The RONI part, which is selected for embedding the scrambled data, is transformed using DWT and then the selected coefficients are subjected to SVD. This work ensures robustness against various attacks and achieves good imperceptibility. This technique demonstrates high level of invisibility and strong robustness against modifications with good embedding capacity. However, the computational complexity of this scheme needs to be improved.
Bamal et al. [5] suggested a hybrid medical watermarking scheme using SVD combined with Slantlet Transform (SLT) and Fast Walsh Transform (FWT). In their work, the Artificial neural networks (ANN) are used for the detection of ROI, and two watermarks are generated. The security of their scheme is strengthened by using a cryptographic technique. This scheme maintains high visual quality of the watermarked image with good levels of robustness and capacity factors.
Khare et al. [24] designed an effective medical image watermarking technique using Homomorphic Transform. This transform is combined with Redundant Discrete Wavelet Transform (RDWT) and Singular Value Decomposition (SVD). The Arnold transform is used for providing more security for the proposed algorithm. The Homomorphic Transform is used to get the reflectance component of the original image. This latter is transformed using SVD and RDWT. The watermark is transformed using RDWT and SVD in a similar manner, and its singular values are chosen for the inserting process. Also, a 2-D chaotic Arnold Transform (AT) is used to scramble the watermarked image and, therefore, increasing the security level of the scheme. Lastly, the experiments show that this scheme is robust as well as imperceptible with the ability to withstand the variation of watermark size.
2.2 Moment based watermarking algorithms
Xiao et al. [49] suggested an image watermarking method using the Fractional Discrete Tchebyshev Moments (FrDTM). The host image is segmented into blocks to compute their FrDTM coefficients. The watermark is scrambled, before the embedding step, utilizing Arnold transform. A secret key is used for watermark extraction to identify ownership and copyright. The orthogonality property of the kernel polynomials provides high noise robustness and the representation of images with minimal information redundancy. Furthermore, the watermark size is fixed in this method and the robustness requires additional test attacks such as rotation.
Xia et al. [48] developed a robust null-watermarking method for color medical images. This work was done by using the Precise Quaternion Polar Harmonic Fourier Moments (PQPHFM). In this work, the low order moments are used for feature image construction and QR code is used to extract the null-watermark image. Experimental results were tested only on MRI medical images and indicate that this scheme is robust to geometric attacks and ensures copyright protection without changing the input medical image. The main shortfall of this paper is the low robustness in resisting median filtering and cropping attacks.
Hu et al. [22] constructed a lossless robust watermarking scheme by using the polar harmonic transform (PHT). In this paper, the watermark is embedded into the low-order PHT moments of the original image. The generated resultant is an intermediate watermarked image, which is converted into a robust watermarked image using one rounding operation. After that, to realize the integrity authentication, the robust watermarked image is hashed to create a hash value. This latter is considered to be part of the compensation information. Lastly, the watermarked image is obtained by embedding the compensation information with a reversible watermarking technique. The experimental results confirm the scheme’s ability on resisting geometric alterations and image processing attacks but remain reversible in attack free cases.
Bastani et al. [7] proposed a secure watermarking technique for medical applications using Tchebichef moments and the conditional quantization method. In this algorithm, the watermark is converted to a binary image and is inserted into the elected quantized moments. The chosen quantization factor provides high robustness against various attacks, except the cropping attack. Lastly, this scheme shows a good visual imperceptibility and zero ratio of false-positive detection.
Hosny et al. [21] proposed an efficient algorithm for watermarking gray-level and color medical images using the orthogonal Polar Complex Exponential Transform (PCET) and its quaternion model (QPCET). In this work, parallel implementation of a watermarking algorithm is performed on multi-core CPUs and GPUs to minimize the watermarking overall time. The experiments of this scheme demonstrate a high level of invisibility and robustness against attacks, which makes it suitable for real-time applications in medical imaging area.
Gomez et al. [20] constructed a novel watermarking technique applied to medical images of COVID-19 patients. In this work, the watermarking system is decomposed into two principal stages. In the first stage, a brightness model is used to construct a perceptive mask to extract the perceptually relevant regions. In the second stage, the host image is decomposed using HT, and the selected high order Hermite coefficients are replaced by the perceptive watermark image. The results show that this scheme preserves the visual information of the image without a change. Elsewhere, the robustness tests show that the extracted watermark is perceptible and the patient information is recovered. Furthermore, it is necessary to compare these findings with other techniques.
The principal weaknesses of the existing medical image watermarking techniques are concerning the difficulty to ensure a balanced trade-off between the common watermarking properties, such that imperceptibility, robustness, capacity, and security. In particular, preserving the visual quality of the medical information while the embedding capacity is increased is a critical issue for a medical image watermarking context. Depending on the advantages and limitations of the watermarking schemes mentioned above, this paper proposes a new reversible watermarking algorithm based on HT and a sliding window technique for extracting the textured regions that are more suitable for embedding areas. This scheme could meet the above-said requirements due to the use of this family of polynomial transforms, which is known for its suitability to the receptive fields of the HVS.
3 Preliminaries
Before designing the tools and techniques for developing a medical image watermarking algorithm, some issues must be clarified. The basic problem in the medical field raises on identifying medical image regions for watermark embedding that will not display any observable alterations in the watermarked image. This is because the medical image has special characteristics and requirements since it contains the patient’s health information for diagnosis. For that reason, the medical image is prepared before the watermark embedding process. Therefore, HT is used in this stage to extract the most suitable component from the input medical image. The choice of this component is motivated by the fact that masking effects are evident in the high contrast image areas according to the HVS. This means that the HVS supports greater distortions in textured areas than in smoothed areas. Consequently, the texture component can tolerate high embedding capacity without any perceptual distortion problem. This component is obtained using the HT. furthermore, to demonstrate the superior performance of our new algorithm, the texture component is segmented into textured and non-textured blocks and only textured blocks are elected for embedding the watermark. We provide below the basic principles and main characteristics of these two techniques.
3.1 Texture extraction using Hermite transform
Before we introduce the HT, it is necessary to provide the mathematical background of polynomial transforms firstly. Polynomial transforms are distinguished by a high level of efficiency computing and known for their capacity to retrieve relevant informations, locally and globally, from the cover image. These transforms are harmoniously adapted to the geometrical forms of images. Also, they allow a good representation of slowly varying surfaces in images which makes these transforms well suitable for medical images since they have largely smooth regions [17]. For those reasons, and many others, the polynomial transforms have been extensively utilized in image processing applications and image analysis procedures.
We seek to approximate M-dimensional signals \(s\left(x\right) , x\in F\) with a combination of orthogonal polynomial basis \({\mathcal{B}}_{\varphi }\). We assume that for the instance of images, as a two-dimensional signal, F is a subset of the 2-dimensional Euclidean space \({\mathbb{R}}^{2}\). Any input signal s(x) can be locally decomposed into windowed signals [25], i.e.:
Where \(P\) is a discrete subset of \(F\), and \(\omega\) is the weight function that determines the polynomial family. We note that \(\omega (x-p)\) is zero except in the neighborhood of the position \(i\in P\).
Each windowed signal \({s}_{ \omega }\left(x\right)\) is approximated by a linear combination of orthogonal polynomials \({\varphi }_{n}(x)\) of degree n with respect to a non-negative weight function \(\omega\). Mathematically we say that these polynomials are orthogonal if they meet the inner product property:
Where \({\delta }_{nm}\) is Kronecker delta function, defined as:
The polynomials are orthonormal if \({k}_{n}=1\) or after normalization by the \({k}_{n}\) factor.
The approximation of the signal \(s\left(x\right)\) may be obtained from these polynomials by minimizing the square error between this signal and its approximation, defined as:
Where \({s}_{ n}\left(i\right), n\in {\mathbb{N}}\) are the polynomial coefficients for which Q is minimized and must converge to zero if \(N\to \infty\). That is, each windowed signal \(s\left(x\right). \omega (x-i)\) can be segmented into a weighted sum of orthonormal basis functions \(\omega \left(x-i\right) {\varphi }_{n}\left(x-i\right), n\in {\mathbb{N}}\), such that:
The equality in (5) means convergence in the mean-square sense [25]. This is equivalent to:
The polynomial coefficients are obtained by using the following inner product:
With \({\varphi }_{n}^{\left(i\right)}= {\varphi }_{n}\left(x-i\right)\) for simplicity.
Moreover, according to (2), the expression (7) is equivalent to:
We consider the following function:
The set of weighted polynomials is a countable basis for \({\mathcal{L}}^{2}({\mathbb{R}})\):
Since \({\varphi }_{n}^{\left(i\right)}\) is orthonormal and accordingly identical to its dual basis vector, this leads to the following simplification:
In order to reconstruct the signal \(s(x)\), we need to consider the expression below:
This implies that if the condition \(\sum_{i\in P}{\omega }^{2}\left(x-i\right)\ne 0\) is satisfied, the signal is completely recovered and stated as:
As a consequence of (5) (8) and (13), the expression above can be rewritten as:
The HT is a particular case of polynomial transforms. It was initially applied, as a mathematical model, for interpreting receptive fields in the early stages of the HVS [16, 27]. This property is of greater importance in image processing, given that it allows an efficient coding of visual information that is relevant to human perception. The HT gained its popularity with the application on different image processing areas, for instance, image compression, image indexing, and image fusion [6, 26]. More specifically, this transform is a workable method for retrieving the image features in the image analysis procedures [33, 45]. However, to the best of our knowledge, the HT did not received increased focus in medical image watermarking schemes. For that reason, our study investigated to improve the effectiveness of this transform in such a field.
The Hermite polynomials \({H}_{n}\left(x\right)\) of order n are orthogonal polynomials and are defined on the interval \([-\infty ,\infty ]\)
They are computed via the following 3-term recurrence relation:
With the initial conditions \({H}_{0}\left(x\right)=1\) and \({H}_{1}\left(x\right)=2x\)
The Hermite polynomials are orthogonal with respect to \({e}^{{x}^{-2}}\). This orthogonality, as expressed in (2), is presented by:
Where \({k}_{n}=n!\sqrt{\pi }\).
The normalized version of Hermite polynomials, which is used in our decomposition process, is scaled and modulated by a Gaussian \(x\to x/\sigma\) and normalized by \(\sqrt{{k}_{n}}\).
Regarding the 2-dimensional signals, the orthonormal Hermite basis functions utilized for the image decomposition are done by considering the Gaussian weight function:
With standard deviation equal to \(\sigma\)
This function has the advantage of constituting a good model for the receptive field profiles of human vision. More specifically, it has been adopted as a template for simple cell responses in the primary visual cortex. Also, it reduces the uncertainty in the spatial and the transform domains [16].
Besides, the derivatives of Gaussian filters are separable, \({\omega }^{2}\left(x,y\right)= {\omega }^{2}\left(x\right) {\omega }^{2}\left(y\right)\), which facilitates their implementation.
The associated orthonormal polynomials to the above weight function are also separable. Hence, their application on images is a direct extension and can be implemented efficiently along the x—and y – directions. They are presented as:
for \(n\ge 0 , m=0,\dots ,n\) and \({H}_{n}\left(x\right)\) indicates the generalized Hermite polynomial of order n.
The polynomial coefficients are performed by using the convolution expressed in (11) between the input image \(\mathrm{s}\left(x,y\right)\) and the function \({\alpha }_{ n}\left(x\right)\) presented in (9), that is:
Applying (14) and (20), it is therefore possible to reconstruct the input image by:
This reconstruction is an approximation of the original image which represents the smooth component (low frequency regions). The texture component (high frequency regions) is deducted by:
The residual image contains the small-scale characteristics of the image. In addition, it represents the high-frequency areas with high randomness due to the detail of the information contained in the image.
3.2 Texture blocks selection using sliding window technique
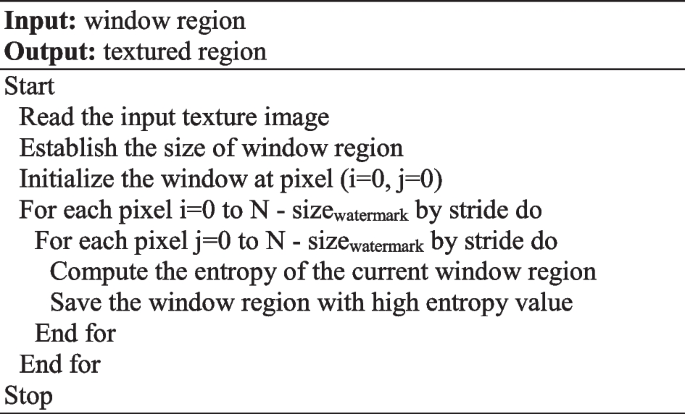
To improve the robustness and imperceptibility factors of our watermarking algorithm, we establish a process to extract textured regions with more precision in the texture component of the original medical image. For this reason, a texture regions selection is done using a sliding window technique. To meet our expectations of the texture region selection, entropy is used as a texture feature criterion. Entropy is a statistical measure used for characterizing the texture of an image. It evaluates the randomness of the distribution of gray-level intensities in an image. The regions with low values represent the smooth regions whereas the higher values represent the textures regions with a great deal of information. The entropy is given as:
Where \({P}_{i}\) is the probability of arising the gray level intensity i in the image, and N is the color level image.
In the light of the HT properties presented above, in particular, its suitability to the receptive fields of the HVS, the regions with higher entropy mean greater information content and randomness, which make it difficult for us to perceive the alterations in those regions. Thus, such regions are best adapted to watermark embedding areas.
Algorithm 1 reported the pseudo-code for the proposed sliding window technique.
3.3 Arnold transform
Arnold transform, also named cat-face transformation, is applied to a digital image with \(N*N\) to shuffle the original configuration of its pixels without changing the value of these pixels [47]. This process is repeated several times to get a scrambled image. In the Arnold transform process, a pixel at point (\(x\),\(y\)) is shifted to another point (\({x}^{\mathrm{^{\prime}}}\),\({y}^{\mathrm{^{\prime}}}\)) by:
Where a and b are scrambling parameters
The inverse of this transform is given by:
By considering the character of periodicity of this transform, the original image reappears after a certain number of iterations. This number is used as a secret key to encrypt and extract the secret image. The period of this process varies according to the size of the image.
In the watermarking context, if the watermark is detected by some hackers, they have to possess the secrete key to recover the original watermark.
4 Proposed medical image watermarking scheme
In this paper, a new approach of medical image watermarking for telemedicine applications based on HT and a sliding window technique is proposed. Our study attempts to determine the most suitable embedding areas to achieve the optimal trade-off among the common watermarking properties, including invisibility, capacity, robustness, and security. Hence, to meet the special requirements of medical images, we exploit the HVS characteristics of the HT to extract the texture component of the host image. Also, the entropy is computed in the sliding window technique in order to select the most textured regions for embedding the watermark, so as the small alterations cannot be identified by human eyes and therefore. Lastly, Arnold transform is used, before the embedding process, to encrypt the watermark as a security enhancement.
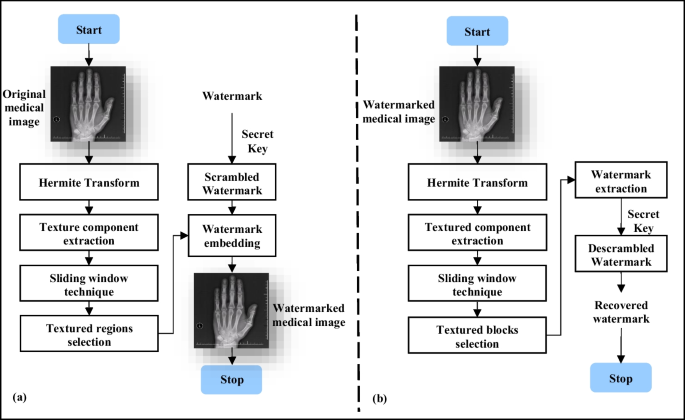
The proposed scheme consists of two major important phases, i.e. watermark embedding and watermark extraction. Details regarding these phases are provided below. The general framework of our scheme is shown in Fig. 2 below.
4.1 The embedding process
First of all, preprocessing is applied to the watermark. We attempt to create a suitable watermark for medical applications in a securing context. E.g. the watermark image that contains the patient information, such as patient name and institution name, is used to demonstrate the reliability (authenticity and integrity) of the watermarked data. In the light of this, and to enhance the robustness of the whole watermarking process, watermark scrambling based on Arnold Transform is used. The idea behind this transform is to make the watermark inaccessible to an unauthorized user without a decryption key. Thus the extraction of the original watermark is extremely difficult, if not impossible without knowing the scrambling algorithm and its parameters. In our watermarking algorithm, the binary watermark image is scrambled from \(W\) to \({W}_{s}\) by using Arnold Transform as presented in the previous section.
The detailed embedding algorithm has been carried out using the following steps.
-
Step 1.
Load the cover medical image \(M\) of dimensions N x N and the binary watermark \(W\).
-
Step 2.
Perform Arnold Transform on the watermark \(W(i,j)\) to obtain the scrambled version of the watermark \({W}_{s}(i,j)\) using n iterations, which will serve as the secret key K.
-
Step 3.
Apply HT on the original image so as to extract the texture component \(T\).
-
Step 4.
Initialize the window size by an 8 × 8 size and compute its entropy. This size is chosen taken into consideration that the input image of this algorithm is the texture component of the original medical image of size N x N.
-
Step 5.
Apply the sliding window technique on the texture image \(T\), and repeat the process as long as the window size is smaller than the watermark size.
-
Step 6.
Select 3 non-overlapping windows \({S}_{k}\) with maximum entropy for embedding the scrambled watermark using the following equation
$${S}_{k }^{*}= {S}_{k}+\alpha *{ W}_{s}$$(26)Where \(\alpha\) is a scale factor that is used to regulate the embedding intensity of the watermark.
-
Step 7.
Combining the image approximation and the watermarked texture to reconstruct the watermarked medical image \({\mathrm{M}}_{\mathrm{W}}\).
4.2 The watermark extraction process
Our process for watermark extraction is a blind watermark extraction process. In that case, it does not need the cover image to retrieve the watermark. On the assumption that \({\mathrm{M}}_{\mathrm{W}}\) is a watermarked image submitted to attacks, the practical procedure for watermark extraction is as follows.
-
Step 1.
Load the watermarked medical image \({M}_{W}\) of dimensions N x N
-
Step 2.
Apply HT on the watermarked medical image \({M}_{W}\) so as to extract the watermarked texture component \({T}_{W}\).
-
Step 3.
Apply the 8 × 8 sliding window technique on the watermarked texture image \({T}_{W}\), and repeat the process as long as the window size is smaller than the watermark size.
-
Step 4.
Select 3 non-overlapping windows \({S}_{x }^{*}\) with maximum entropy and retrieve the scrambled watermark according to the equation below:
$${W}_{s }^{*}=({S}_{k }^{*}-{S}_{k})/\alpha$$(27) -
Step 5.
Recover the original watermark \({W}^{*}\) by applying the inverse AT to \({W}_{s }^{*}\).
5 Experimental results and comparative analysis
The performance analysis of our scheme is investigated in this section. The simulations are conducted in MATLAB. 8 modalities of medical images are used for tests, as depicted in Fig. 4. These images are of the types MRI, US, Barium, X-ray, Fluoroscopy, Angiography, Computed Tomography (CT), and Mammography. Additionally, two watermark are used for embedding process as shown in Fig. 3. The efficiency of the proposed medical watermarking scheme is thoroughly evaluated by subjecting it against several attacks including JPEG Compression, noise addition, filtering, cropping, rotation, Histogram equalization, and other attacks. The embedding strength of our watermarking algorithm is set at 0.1, with a view to achieve the optimal compromise between robustness and imperceptibility. Indeed, the high values of the embedding strength provide lower PSNR but strong robustness against various attacks and vice versa. Moreover, that is why we have selected the strength value so that the PSNR is above 50 dB and high robustness is ensured. The experimental results are segmented into two principal parts: the first evaluates the visual quality while the second evaluates the robustness against various attacks. In addition, compared with other watermarking techniques (based on moments), the time performance, capacity and false positive analysis of our scheme are given in this section.
5.1 Dataset
The simulations are conducted on 200 medical images. To make the comparison easier, all the host images are resized to (512 × 512 pixels) and converted to grayscale. These images are taken from Radiopaedia.org database. Some samples of our image test set with different modalities are shown in Figs. 4 and 5. Additionally, two binary images of size 128 × 128 with different contents are utilized as watermark images as shown in Fig. 3.
5.2 Parameters for performance measure
The performance of our watermarking scheme is mainly evaluated according to its imperceptibility and robustness. The Structural Similarity Index, Peak Signal to Noise Ratio, Bit Error Rate, and Normalized Correlation are used for evaluation of the proposed algorithm. The higher PSNR, NC, SSIM and lower BER indicates the better performance of the watermarking methods. These indicators are described in this subsection.
-
Peak Signal to Noise Ratio (PSNR)
The PSNR is the basic parameter to assess the visual quality of the watermarked image with regard to the original image. The larger the value, the better will be the image quality.
Where MSE (Mean Square Error) contains the cumulative squared error between the cover image \(\mathrm{I}\left(\mathrm{i},\mathrm{j}\right)\) of size \(\mathrm{MxN}\) and the watermarked image \({\mathrm{I}}_{\mathrm{w}}\left(\mathrm{i},\mathrm{j}\right)\).
The MSE is defined as:
lower MSE and Higher PSNR values enhance the quality of watermarking.
-
Normalized correlation (NC)
The NC evaluates the robustness of the proposed medical image watermarking technique within attacks by computing the similarity between the original and extracted watermarks. The higher the NC value, the higher the similarity is and the stronger the scheme robustness.
Where \({W}_{ij}\) and \({W}_{ij}^{^{\prime}}\) are the pixel of cover and extracted watermark of size X*Y.
-
Structural similarity (SSIM)
The SSIM evaluates the structural similarity between cover and watermarked images by considering three parameters: luminance, contrast and structure [46]. The value of such measure must be close to unity. Mathematically, it is stated as:
Where \(\mathrm{I}\) and \({\mathrm{I}}_{\mathrm{w}}\) depicts original and watermarked images.
-
Bit error rate (BER)
The BER evaluates the quality of the extracted watermark. It represents the ratio of the number of error bits received to the total number of bits transmitted and defined as:
The values of BER are in the range of [0–1]. It is obvious that the lower the BER, the more robust the algorithm is.
5.3 Visual quality analysis for medical images
In this subsection, the imperceptibility evaluation of our watermarking scheme is measured using the PSNR. This important factor designates the capacity to hide the watermark into the original data without any perceptible degradation to its visual quality.
Table 1 shows the visual outcome of resultant components using our scheme. For better understanding, the first column is assigned to the results of the selected embedding regions in the extracted texture component of two medical images on each modality using HT and the sliding window technique. The second column depicts the obtained watermarked medical images and in the last column, the result of the extracted watermarks is represented. It can be observed that our embedding technique does not display any observable modifications in the visual quality of the watermarked images. Also, the extracted watermarks are similar to their original versions.
In Table 2, the PSNR is computed for the watermarked medical images which are illustrated in Table 1. In addition, the NC, SSIM and BER values are computed for the extracted watermarks referring to the same table. It can be observed from these tables that all the PSNR performances of the watermarked medical images are superior to 61 dB. Take Angiography images as an example, our scheme achieved the highest PSNR value 72.3073 dB. The average SSIM obtained is about 0.9975 while the NC and BER values computed between the host and the extracted watermarks are equal to their ideal values in attack-free cases. This indicates that our scheme has good imperceptibility and complete extraction of the watermark.
The obtained results of the suggested scheme are compared to [5, 7, 24, 34] in Table 3 in terms of PSNR and NC values. The average value of PSNR of our scheme is 66,4499 dB as compared to 61,3463 in [34], 58.3587 in [24], 53,7602 in [5] and 60.8950 in [7]. Moreover, the average value of NC is 1 as compared to the same methods. However, our scheme absolutely outperforms similar methods. The obtained values show that a complete extraction of all the watermark bits is achieved on the one hand, and a high level of imperceptibility is guaranteed on the other.
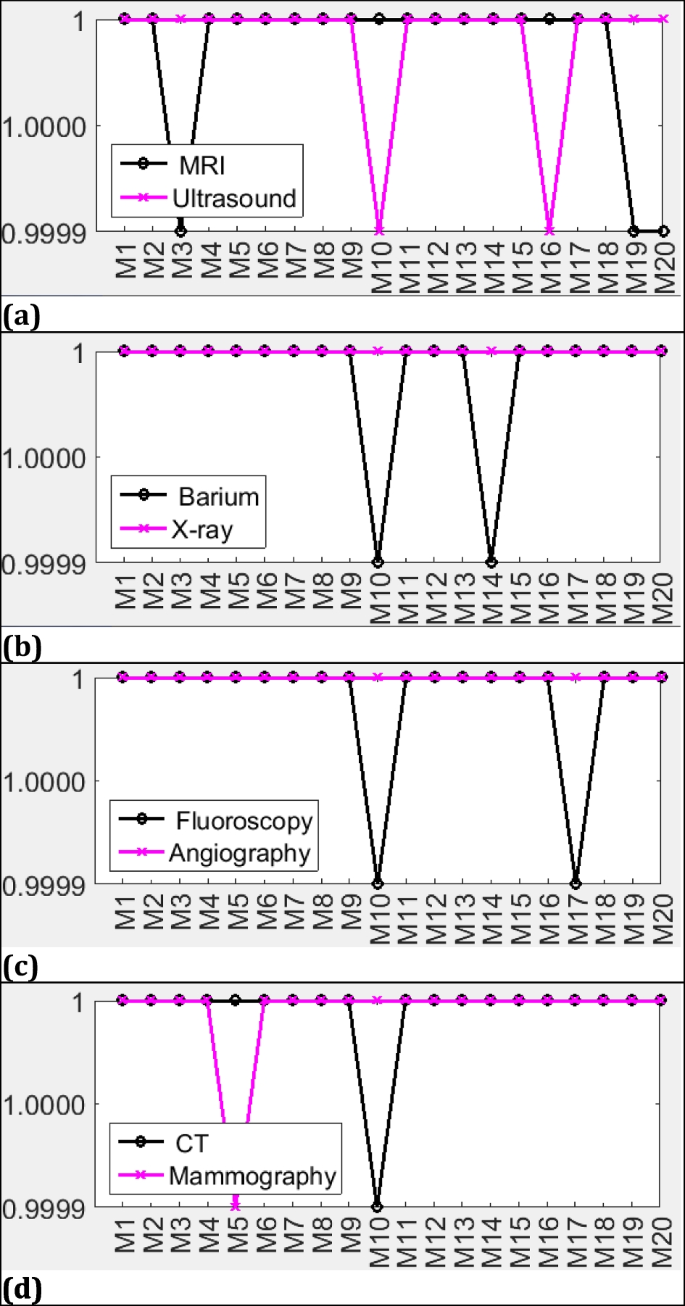
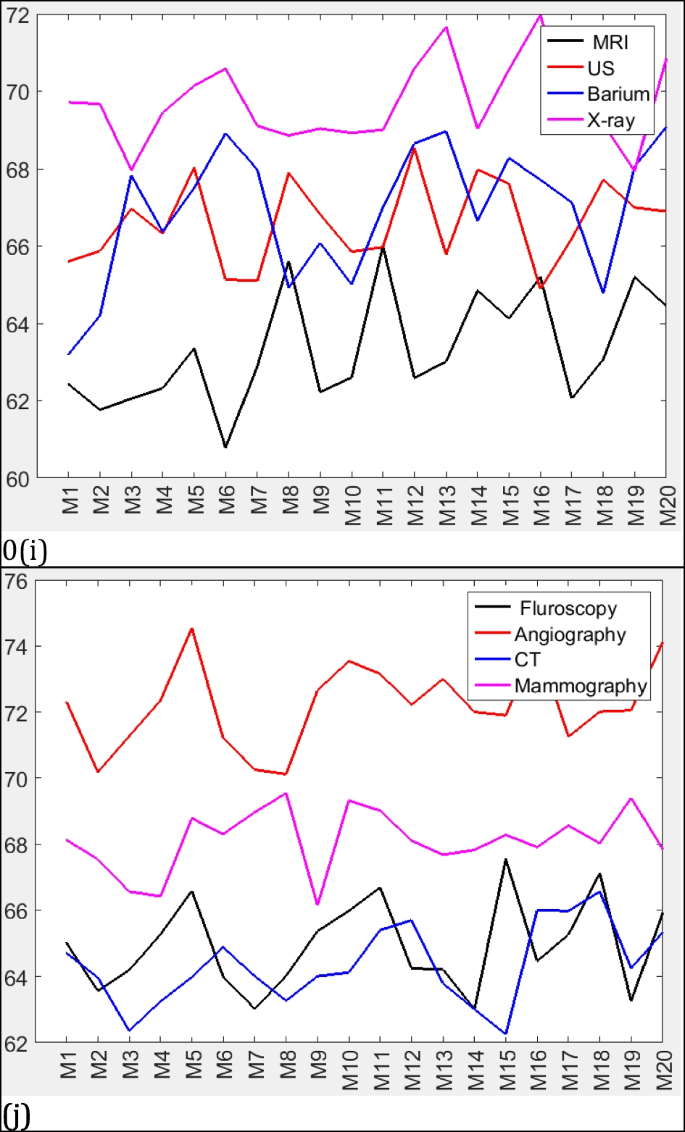
Extensive experiments have been implemented on 160 medical images under no attack. Figures 5 and 6 display these experiments in terms of NC and PSNR respectively. These figures illustrate the complete results of checking imperceptibility on the database for the proposed method. As illustrated in Fig. 5, the NC values are close to the ideal value. This implies that the original and extracted watermarks are similar and can totally be retrieved in case of no attacks. Moreover, it is observed from Fig. 6 that the PSNR ranges from 61 to 75 dB. It is worth noting that the overall performance of our scheme varies with satisfactory results on each medical image modality.
Experimental results are also provided by changing the size of the hidden watermark. Table 4 tabulates performance metrics for the proposed scheme in terms of PSNR, NC, and SSIM. It can be examined from this table that the obtained results, which are compared to [24], attain better values and our scheme is imperceptible as well as robust.
5.4 Robustness against attacks
In this subsection, the robustness of our scheme is evaluated on different medical images and is compared with other recent existing methods. 15 various attacks are applied on MRI medical images, including JPEG compression, noise addition, Filtering, geometric, sharpening, HE, Sobel and blurring attacks. These attacks intend to extract and/or to distort the watermark voluntary or involuntary. The quality of the retrieved watermarks is evaluated through computing the SSIM, NC and BER values as depicted in Tables 10, 11, and 12. The image manipulation attacks performed on test images are as follows: (Fig. 7):
-
JPEG compression
In the first experiment, our approach is evaluated against JPEG compression by using different quality factors. Generally, the JPEG compression attack occurs frequently in multimedia applications. Practically all the medical images that are currently being distributed via Internet have been compressed. In theory, this attack tends to decrease the high frequency regions of the images, which inevitably will influence the visual quality and the pixel values of the medical image. The test image is JPEG compressed using different quality factors QF. Table 5 depicts the extracted watermarks and their NC values. It is noticed that our scheme performs good robustness even if the quality factor of JPEG compression decreases. Tables 10, 11, and 12 present the comparison of SSIMs, NCs and BERs respectively under different compression ratios. From Table 11 it is deducted that the average of NC values for both watermarks are greater than 0.9 under different quality factors of the JPEG compression attack. However, the SSIM and BER are estimated nearly the same with little difference for various QF. These results perform better performance than the existing scheme except in the case of QF = 90 presented in [21]. Our scheme has stronger robustness against this kind of attack even at low compression quality factors.
-
Noise addition
The success of a watermarking scheme is also depending on its capacity to withstand noise addition. In the second test, we investigated the effect of noising attacks to the proposed scheme. For this purpose, Table 6 depicts the retrieved watermarks and their NC values with the addition of four types of noises including Salt & pepper with variance V = 0.01, Gaussian with variance V = 0.01, Poisson, and Speckle noises. Referring to Table 11, average NCs for both watermarks of our scheme is compared to other techniques with different variances of noises. The SSIM values range from 0.9465 to 0.9952 as shown in Table 10. The BER values are less than 10% when attacked by the various variance of noises as shown in Table 12. For most cases, increasing the amount of noise increases the distortion in the watermarked images. Lastly, robustness results were also satisfactory for noise addition attacks.
-
Filtering attack
In the third experiment, we investigated the robustness against filtering attacks including Median, Gaussian, and Wiener filtering. From the results of Table 7, W2 resists better than W1 when exposed to filtering attack with window size 3 × 3. Tables 10 and 11 show the average of NCs and SSIMs for W1 and W2 versus different sizes of windows are compared to [5, 7, 21, 24]. From Table 12, The BER values are less than 10% when attacked by various filtering attacks. For most cases, our method provides a successful extraction of the watermark.
-
Geometric attacks
The geometric alterations destroy the synchronization in the watermarked bitstream and directly alter the pixel’s orientation of the cover. In the next experiments, the watermarked images are subjected to cropping, which consists of removing selected pixels from the watermarked image. They are also subjected to rotation by a certain angle degree and to scaling attack with a certain scaling factor. In Table 8, the test image is rotated to 5 degrees clockwise, is cropped with 20%, and is scaled with 75%.
Afterward, the extracted watermarks are shown for W1 and W2 with their NC values (Table 8). Other attack parameters are tested in these experiments and compared to existing schemes. In Tables 10 and 11, the average NCs and SSIMs of W1 and W2 are always greater than 0.9 for the considered attacks. In Table 12 the BERs are estimated nearly the same with little difference for various parameters of attacks scenario. It is noteworthy, moreover, that the selected regions for embedding spread the watermark all over the image which demonstrates strong robustness when this kind of attack takes place.
-
Sharpening and HE attacks
Image sharpening represents any enhancement method that highlights fine details in an image. Our scheme is tested against Sharpening attack with a (3 × 3) mask. Also, Histogram equalization, which is a popular contrast management method frequently used for medical image enhancement, is subjected to watermarked images for tests. The results of the extracted watermarks and their NCs are depicted in Tables 9 and 11. In these tables, the average NC values are greater than 0.9, nearer to 1, and superior to the contrasting schemes. These results show that our method resists sharpening and HE attacks).
-
Sobel and blurring attack
In the last experiment, Our technique is tested against Sobel and blurring attacks. As seen in Tables 9 and 11 the average NC values are close to the ideal values. In Table 10, we prove the effectiveness of the proposed scheme which results in better SSIM values compared to [5]. The BER values are less than 25% when subjected to these attacks as shown in Table 12. These results substantiate that the proposed technique is resistant to Sobel and blurring attacks.
As a result, there is no error-free scheme against attacks in medical image watermarking. Our approach is robust to many image attacks including JPEG compression until 50%, 3 × 3, and 5 × 5 filtering, the addition of 0.01 and 0.0002 of Gaussian noise, the addition of S&P (0.01, 0.005, and 0.001), Speckle, Poisson, rotation 5° and 10°, cropping 20%, scaling (75%, 90%, 150%, and 200%), Sharpening, HE, Sobel, and blurring. According to the comparison of the obtained results with [5, 7, 21, 24, 39], we can say that our extracted watermarks have higher average NCs, SSIMs, and lower average BER values. Therefore, it can be concluded that selected embedding regions increased the security of the watermark that makes it highly robust against many kinds of attacks.
5.5 False positive test
False positive detection (FPD) is a result of watermark extraction from unwatermarked medical image, which is a watermarked medical image that was not originally embedded. In such a case, the FPD happens and therefore one could say that the watermarking system lacks security. In this subsection, the proposed extraction process is evaluated on the same database presented in the second subsection. Some tested samples of unwatermarked images and both watermarks W1 and W2 are used for these experiments. Table 13 shows the visual outcome of the extracted watermarks with their NC values. The obtained NC values are greater than 0.01. In general, we accept that the FPD occurs if the NCs are larger than 0.6 [44]. With this in mind, the obtained result for FPD of the proposed extraction process is zero, which is equivalent to one precision level value according to Eq. (33). However, our scheme overcomes the false positive problem and is adequately secured.
5.6 Execution time assessement
The execution time of both embedding and extraction methods of our medical image watermarking technique is assessed. It can be seen in Table 14 that our watermarking process is effective in terms of speed.
6 Conclusion
In this work, we propose a novel, robust, imperceptible, and secure medical image watermarking method. Indeed, since the personal data of patient’s have a sensitive character, they impose more integrity and confidentiality when accessed by an unauthorized person, also they should demonstrate strong robustness against several image processing attacks. With this in mind, the HT and the sliding window technique are used to extract the most textured regions in the medical image with a view to choose the appropriate areas for embedding the watermark without affecting the medical diagnosis content. Further, encryption before embedding using Arnold Transform is done to ensure inaccessibility of watermark to the unauthorized user and therefore enhancing the security of our scheme. By testing 160 medical images, the imperceptibility of our approach is acceptable and the watermark can be totally retrieved in attack-free cases. Otherwise, the robustness of our scheme outperforms the existing recent schemes which make it robust enough to various attacks. Compared with the existing robust watermarking, it has been seen that our scheme meets the common watermarking properties, including invisibility, capacity, robustness, and security. Overall, our method is an ideal candidate to serve as a secure and strong authentication system and information hiding for e-healthcare applications.
7 Future scope
In the future, we intend to develop suitable techniques for restoring the altered image and identify the tampered locations. Further, subjecting the watermarked image into additional watermarking attacks and working with color medical images can be included for an effective medical image watermarking approach.
References
Abdulfetah AA, Sun X, Yang H, Mohammad N (2010) Robust adaptive image watermarking using visual models in DWT and DCT domain. Inf Technol J 9:460–466. https://doi.org/10.3923/itj.2010.460.466
Al-Haj AM (2010) Advanced techniques in multimedia watermarking: image, video and audio applications: image, video and audio applications. IGI Global
Al-Juaid NA, Gutub AA, Khan EA (2018) Enhancing PC data security via combining RSA cryptography and video based steganography. J Inf Secur Cybercrimes Res. https://doi.org/10.26735/16587790.2018.006
Atta-ur-Rahman SK, Aldhafferi N et al (2018) Reversible and fragile watermarking for medical images. Comput Math Methods Med 2018:1–7. https://doi.org/10.1155/2018/3461382
Bamal R, Kasana SS (2019) Dual hybrid medical watermarking using walsh-slantlet transform. Multimed Tools Appl 78:17899–17927. https://doi.org/10.1007/s11042-018-6820-9
Barba-J L, Vargas-Quintero L, Calderon JA, Torres Moreno C (2020) An image fusion method based on the Hermite transform applied to nuclear medicine and x-ray tomographic modalities. J Phys Conf Ser 1547:012017. https://doi.org/10.1088/1742-6596/1547/1/012017
Bastani A, Ahouz F (2020) High capacity and secure watermarking for medical images using Tchebichef Moments. RADIOENGINEERING 29:636–643. https://doi.org/10.13164/re.2020.0636
Berghel H, O’Gorman L (1996) Protecting ownership rights through digital watermarking. Computer 29:101–103. https://doi.org/10.1109/2.511977
Bhatti UA, Yu Z, Yuan L et al (2022) A Robust Remote Sensing Image Watermarking Algorithm Based on Region-Specific SURF. In: Ullah A, Anwar S, Rocha Á, Gill S (eds) Proceedings of international conference on information technology and applications. Springer Nature Singapore, Singapore, pp 75–85
Bhatti UA, Yu Z, Yuan L et al (2020) Geometric algebra applications in geospatial artificial intelligence and remote sensing image processing. IEEE Access 8:155783–155796. https://doi.org/10.1109/ACCESS.2020.3018544
Bhatti UA, Yu Z, Li J et al (2020) Hybrid watermarking algorithm using Clifford Algebra with Arnold Scrambling and Chaotic Encryption. IEEE Access 8:76386–76398. https://doi.org/10.1109/ACCESS.2020.2988298
Bhatti UA, Yuan L, Yu Z et al (2021) Predictive data modeling using sp-kNN for risk factor evaluation in urban demographical healthcare data. J Med Imaging Health Inform 11:7–14. https://doi.org/10.1166/jmihi.2021.3313
Chauhan DS, Singh AK, Adarsh A et al (2019) Combining Mexican hat wavelet and spread spectrum for adaptive watermarking and its statistical detection using medical images. Multimed Tools Appl 78:12647–12661. https://doi.org/10.1007/s11042-017-5348-8
Cox IJ (2008) Digital watermarking and steganography, 2nd ed. Morgan Kaufmann Publishers, Amsterdam, Boston
Cox IJ, Miller ML, Bloom JA (2000) Watermarking applications and their properties. In: Proceedings of the the international conference on information technology: coding and computing (ITCC’00). IEEE Computer Society, Washington, DC, USA, pp 6-
Department GMCRLCS, Young RA (1985) The Gaussian Derivative Theory of spatial vision: analysis of cortical cell receptive field line-weighting profiles. General Motors Research Laboratories
Eden M, Unser M, Leonardi R (1986) Polynomial representation of pictures. Signal Process 10:385–393. https://doi.org/10.1016/0165-1684(86)90046-0
Ernawan F, Ariatmanto D (2023) A recent survey on image watermarking using scaling factor techniques for copyright protection. Multimed Tools Appl. https://doi.org/10.1007/s11042-023-14447-5
Fang Y, Liu J, Li J et al (2022) Robust zero-watermarking algorithm for medical images based on SIFT and Bandelet-DCT. Multimed Tools Appl 81:16863–16879. https://doi.org/10.1007/s11042-022-12592-x
Gomez-Coronel SL, Moya-Albor E, Brieva J, Ponce H (2020) A perceptive watermarking approach applied to COVID-19 imaging data. In: Brieva J, Lepore N, Romero Castro E, Linguraru MG (eds) 16th international symposium on medical information processing and analysis. SPIE, Lima, Peru, pp 34
Hosny KM, Darwish MM, Li K, Salah A (2018) Parallel multi-core CPU and GPU for fast and robust medical image watermarking. IEEE Access 6:77212–77225. https://doi.org/10.1109/ACCESS.2018.2879919
Hu R, Xiang S (2021) Lossless robust image watermarking by using polar harmonic transform. Signal Process 179:107833. https://doi.org/10.1016/j.sigpro.2020.107833
Katzenbeisser S, Petitcolas FA (2000) Information hiding techniques for steganography and digital watermarking, 1st ed. Artech House, Inc., USA
Khare P, Srivastava VK (2021) A secured and robust medical image watermarking approach for protecting integrity of medical images. Trans Emerging Tel Tech 32. https://doi.org/10.1002/ett.3918
Martens J-B (2003) Image Technology Design. Springer US, Boston, MA
Martens J-B (2006) The Hermite transform: a survey. EURASIP J Adv Signal Process 2006. https://doi.org/10.1155/ASP/2006/26145
Martens J-B (1990) The Hermite transform-applications. IEEE Trans Acoust Speech Signal Process 38:1607–1618. https://doi.org/10.1109/29.60076
Mousavi SM, Naghsh A, Abu-Bakar SAR (2014) Watermarking techniques used in medical images: a survey. J Digit Imaging 27:714–729. https://doi.org/10.1007/s10278-014-9700-5
Patil N, Udupi VR (2019) Development of Reversible Video Watermarking Algorithm based on Hybrid DWT-SVD. 8:5
Rai A, Singh HV (2017) SVM based robust watermarking for enhanced medical image security. Multimed Tools Appl 76:18605–18618. https://doi.org/10.1007/s11042-016-4215-3
Ramly S, Aljunid SA, Shaker Hussain H (2011) SVM-SS Watermarking model for medical images. In: Ariwa E, El-Qawasmeh E (eds) Digital enterprise and information systems. Springer Berlin Heidelberg, Berlin, Heidelberg, pp 372–386
Rani N (2012) Digital Watermarking. Global J Comp Sci Technol 12(F13):1–4
Rivero-Moreno CJ, Bres S (2004) Texture feature extraction and indexing by Hermite filters. In: Proceedings of the 17th international conference on pattern recognition, 2004. ICPR 2004. IEEE, Cambridge, UK, Vol 1, pp 684–687
Sabbane F, Tairi H (2019) Medical image watermarking technique based on polynomial decomposition. Multimed Tools Appl 78:34129–34155. https://doi.org/10.1007/s11042-019-08134-7
Sabbane F, Aherrahrou N, Tairi H (2019) A new region based watermarking scheme for medical images. In: Proceedings of the new challenges in data sciences: acts of the second conference of the Moroccan Classification Society - SMC ’19. ACM Press, Kenitra, Morocco, pp 1–6
Sharma S, Zou JJ, Fang G (2023) A dual watermarking scheme for identity protection. Multimed Tools Appl 82:2207–2236. https://doi.org/10.1007/s11042-022-13207-1
Shehab A, Elhoseny M, Muhammad K et al (2018) Secure and robust fragile watermarking scheme for medical images. IEEE Access 6:10269–10278. https://doi.org/10.1109/ACCESS.2018.2799240
Singh A, Kumar B, Singh G, Mohan A (2017) Medical Image Watermarking: techniques and Applications. Springer Science+Business Media, New York, NY
Singh MK, Kumar S, Ali M, Saini D (2021) Application of a novel image moment computation in X-ray and MRI image watermarking. IET Image Proc 15:666–682. https://doi.org/10.1049/ipr2.12052
Singh KU, Kumar A, Singh T, Ram M (2022) Image-based decision making for reliable and proper diagnosing in NIFTI format using watermarking. Multimed Tools Appl 81:39577–39603. https://doi.org/10.1007/s11042-022-12192-9
Soltani Panah A, Van Schyndel R, Sellis T, Bertino E (2016) On the properties of non-media digital watermarking: a review of state of the art techniques. IEEE Access 4:2670–2704. https://doi.org/10.1109/ACCESS.2016.2570812
Tao H, Chongmin L, Mohamad Zain J, Abdalla AN (2014) Robust image watermarking theories and techniques: a review. J Appl Res Technol 12:122–138. https://doi.org/10.1016/S1665-6423(14)71612-8
Thakur S, Singh AK, Ghrera SP, Mohan A (2020) Chaotic based secure watermarking approach for medical images. Multimed Tools Appl 79:4263–4276. https://doi.org/10.1007/s11042-018-6691-0
Thanki R, Borra S, Dwivedi V, Borisagar K (2017) An efficient medical image watermarking scheme based on FDCuT–DCT. Eng Sci Technol Int J 20:1366–1379. https://doi.org/10.1016/j.jestch.2017.06.001
van Dijk AM, Martens J-B (1996) Feature-based image compression with steered Hermite transforms. In: Proceedings of 3rd IEEE international conference on image processing. IEEE, Lausanne, Switzerland, pp 205–208
Wang Z, Bovik AC, Sheikh HR, Simoncelli EP (2004) Image quality assessment: from error visibility to structural similarity. IEEE Trans on Image Process 13:600–612. https://doi.org/10.1109/TIP.2003.819861
Wu L, Zhang J, Deng W, He D (2009) Arnold Transformation Algorithm and Anti-Arnold Transformation Algorithm. In: 2009 first international conference on information science and engineering. IEEE, Nanjing, China, pp 1164–1167
Xia Z, Wang X, Wang M et al (2019) Geometrically invariant color medical image null-watermarking based on precise quaternion polar harmonic fourier moments. IEEE Access 7:122544–122560. https://doi.org/10.1109/ACCESS.2019.2935174
Xiao B, Luo J, Bi X et al (2020) Fractional discrete Tchebyshev moments and their applications in image encryption and watermarking. Inf Sci 516:545–559. https://doi.org/10.1016/j.ins.2019.12.044
Xie H, Zhang Y, Zhang H, Li Z (2023) Novel medical image cryptogram technology based on segmentation and DNA encoding. Multimed Tools Appl. https://doi.org/10.1007/s11042-023-14546-3
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Ethical approval
This article does not contain any studies with human participants or animals performed by any of the authors.
Additional information
Publisher's note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Sabbane, F., Tairi, H. Watermarking approach based on Hermite transform and a sliding window algorithm. Multimed Tools Appl 82, 47635–47667 (2023). https://doi.org/10.1007/s11042-023-15324-x
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-023-15324-x