Abstract
In this paper, we investigate the performance analysis of the IEEE 802.11 DCF protocol at the data link layer. We analyze the impact of network coding in saturated and non-saturated traffic conditions. The cross-layer analytical framework is presented in analyzing the performance of the encode-and-forward (EF) relaying wireless networks. This situation is employed at the physical layer under the conditions of non-saturated traffic and finite-length queue at the data link layer. First, a model of a two-hop EF relaying wireless channel is proposed as an equivalent extend multi-dimensional Markovian state transition model in queuing analysis. Then, the performance in terms of queuing delay, throughput and packet loss rate are derived. We provide closed-form expressions for the delay and throughput of two-hop unbalanced bidirectional traffic cases both with and without network coding. We consider the buffers on nodes are unsaturated. The analytical results are mainly derived by solving queuing systems for the buffer behavior at the relay node. To overcome the hidden node problem in multi hop wireless networks, we develop a useful mathematical model. Both models have been evaluated through simulations and simulation results show good agreement with the analytical results.












Similar content being viewed by others
References
Ishmael, J., Bury, S., Pezaros, D., & Race, N. (2008). Deploying rural community wireless mesh networks. IEEE Internet Computing, 12(4), 22–29.
Soldani, D., & Dixit, S. (2008). Wireless relays for broadband access [radio communications series]. IEEE Communications Magazine, 46(3), 58–66.
Eugster, P., Guerraoui, R., Kermarrec, A., & Massoulié, L. (2004). Epidemic information dissemination in distributed systems. Computer, 37(5), 60–67.
Ieee std 802.11-2007, part 11. wireless lan medium access control (mac) and physical layer (phy) specifications. IEEE Std. 2007 2007; :Part 11. doi:10.1109/IEEESTD.2007.92296.
Bianchi, G. (2000). Performance analysis of the ieee 802.11 distributed coordination function. IEEE Journal on Selected Areas in Communications, 18(3), 535–547.
Robinson, J. W., & Randhawa, T. S. (2004). Saturation throughput analysis of ieee 802.11 e enhanced distributed coordination function. IEEE Journal on Selected Areas in Communications, 22(5), 917–928.
Duffy, K., Malone, D., & Leith, D. (2005). Modeling the 802.11 distributed coordination function in non-saturated conditions. IEEE Communications Letters, 9(8), 715–717.
Ni, Q., Li, T., Turletti, T., & Xiao, Y. (2005). Saturation throughput analysis of error-prone 802.11 wireless networks. Wireless Communications and Mobile Computing, 5(8), 945–956.
Fragouli, C., & Widmer, J. (2008). Efficient broadcasting using network coding. IEEE/ACM Transactions on Networking, 16(2), 450–463.
Wu, H., Peng, Y., Long, K., Cheng, S., & Ma, J. (2002) Performance of reliable transport protocol over ieee 802.11 wireless lan: analysis and enhancement. In INFOCOM 2002. Twenty-first annual joint conference of the IEEE computer and communications societies. proceedings. IEEE, vol. 2. IEEE, 2002, pp. 599–607.
Chatzimisios, P., Boucouvalas, A., & Vitsas, V. (2003). Ieee 802.11 packet delay-a finite retry limit analy- sis. In Global telecommunications conference, 2003. GLOBECOM’03. IEEE, vol. 2. IEEE, pp. 950–954.
Babich, F., & Comisso, M. (2009). Throughput and delay analysis of 802.11-based wireless networks using smart and directional antennas. IEEE Transactions on Communications, 57(5), 1413–1423.
Zhang, L., Yantai, S., Oliver, Y., & Guanghong, W. (2006). Study of medium access delay in ieee 802.11 wireless networks. IEICE transactions on Communications, 89(4), 1284–1293.
Xiao, Y. (2005). Performance analysis of priority schemes for ieee 802.11 and ieee 802.11 e wireless lans. IEEE Transactions on Wireless Communications, 4(4), 1506–1515.
Gupta, V., Gong, M., Dharmaraja, S., & Williamson, C. (2010). Analytical modeling of bidirectional multi-channel ieee 802.11 mac protocols. International Journal of Communication Systems, 24(5), 647–665.
Kao, H., Wu, P., & Lee, C. (2011). Analysis and enhancement of multi-channel mac protocol for ad hoc networks. International Journal of Communication Systems, 24(3), 310–324.
Rui, X., Hou, J., & Zhou, L. (2012). Decode-and-forward with full-duplex relaying. International Journal of Communication Systems, 25(2), 270–275.
Liu, W., Jin, H., Wang, X., & Guizani, M. (2011). A novel ieee 802.11-based mac protocol supporting cooperative communications. International Journal of Communication Systems, 24(11), 1480–1495.
Ke, C., Wei, C., Lin, K., & Ding, J. (2011). A smart exponential-threshold-linear backoff mechanism for ieee 802.11 wlans. International Journal of Communication Systems, 24(8), 1033–1048.
Engelstad, P., Osterbo, O. (2006). Analysis of the total delay of ieee 802.11 e edca and 802.11 dcf. In Communications, 2006. ICC’06. IEEE International Conference on, vol. 2. IEEE, pp. 552–559.
Malone, D., Duffy, K., & Leith, D. (2007). Modeling the 802.11 distributed coordination function in nonsaturated heterogeneous condition, IEEE/ACM Transactions on Networking, 15(1), 159–172.
Zhai, H., Kwon, Y., & Fang, Y. (2004). Performance analysis of ieee 802.11 mac protocols in wireless lans. Wireless Communications and Mobile Computing, 4(8), 917–931.
Tickoo, O., & Sikdar, B. (2008). Modeling queueing and channel access delay in unsaturated ieee 802.11 random access mac based wireless networks. IEEE/ACM Transactions on Networking (TON), 16(4), 878–891.
Felemban, E., & Ekici, E. (2011). Single hop ieee 802.11 dcf analysis revisited: Accurate modeling of channel access delay and throughput for saturated and unsaturated traffic cases. IEEE Transactions on Wireless Communications, 10(10), 3256–3266.
Foh, C., Zukerman, M., & Tantra, J. (2007). A markovian framework for performance evaluation of ieee 802.11. IEEE Transactions on Wireless Communications, 6(4), 1265–1276.
Liu, J., Goeckel, D., & Towsley, D. (2007). Bounds on the gain of network coding and broadcasting in wireless networks. In INFOCOM, 2007. 26th IEEE international conference on computer communications, IEEE. IEEE 2007, pp. 724–732.
Chaporkar, P., & Proutiere, A. (2007) Adaptive network coding and scheduling for maximizing throughput in wireless networks. In Proceedings of the 13th annual ACM international conference on Mobile computing and networking, ACM, 2007, pp. 135–146.
Chen, W., Letaief, K., & Cao, Z. (2007). Opportunistic network coding for wireless networks. In Communications 2007. ICC’07. IEEE international conference on, IEEE, 2007, pp. 4634–4639.
Asterjadhi, A., Fasolo, E., Rossi, M., Widmer, J., & Zorzi, M. (2010). Toward network coding-based protocols for data broadcasting in wireless ad hoc networks. IEEE Transactions on Wireless Communications, 9(2), 662–673.
Fasolo, E., Rossi, M., Widmer, J., & Zorzi, M. (2007). On mac scheduling and packet combination strategies for practical random network coding. In Communications, 2007. ICC’07. IEEE international conference on, IEEE, 2007, pp. 3582–3589.
Sagduyu, Y., & Ephremides, A. (2008). Cross-layer optimization of mac and network coding in wireless queueing tandem networks. IEEE Transactions on Information Theory, 54(2), 554–571.
Le, J., Lui, J., & Chiu, D. (2008). How many packets can we encode? An analysis of practical wireless network coding. In INFOCOM 2008. The 27th conference on computer communications. IEEE, IEEE, pp. 371–375.
Argyriou, A. (2009). Wireless network coding with improved opportunistic listening. IEEE Transactions on Wireless Communications, 8(4), 2014–2023.
Hsu, Y., Abedini, N., Ramasamy, S., Gautam, N., Sprintson, A., Shakkottai, S., et al. (2011). Opportunities for network coding: To wait or not to wait. Information Theory Proceedings (ISIT), 2011 IEEE International Symposium on, IEEE, pp. 791–795.
Cloud, J., Zeger, L., & Médard, M. (2012). Mac centered cooperation synergistic design of network coding, multi-packet reception, and improved fairness to increase network throughput. IEEE Journal on Selected Areas in Communications, 30(2), 341–349.
Hasegawa, J., Yomo, H., Kondo, Y., Davis, P., Suzuki, R., Obana, S., et al. (2009). Bidirectional packet aggregation and coding for voip transmission in wireless multi-hop networks. In Communications, 2009. ICC’09. IEEE international conference on, IEEE, pp. 1–6.
Fouli, K., Casse, J., Sergeev, I., Médard, M., & Maier, M. (2012). Broadcasting xors: On the application of network coding in access point-to-multipoint networks. Multiple Access Communications. Springer, 25–36.
Hsu, Y. P., & Sprintson, A. (2012). Opportunistic network coding: Competitive analysis. In International Symposium on Network Coding (NetCod), 2012, IEEE, pp. 191–196.
Antonopoulos, A., Verikoukis, C., Skianis, C., & Akan, O. B. (2012). Energy efficient network coding-based mac for cooperative arq wireless networks. Ad Hoc Networks.
Katti, S., Rahul, H., Hu, W., Katabi, D., Médard, M., & Crowcroft, J. (2008). Xors in the air: practical wireless network coding. IEEE/ACM Transactions on Networking (TON), 16(3), 497–510.
Hirantha Sithira Abeysekera, B., Matsuda, T., & Takine, T. (2008). Dynamic contention window control mechanism to achieve fairness between uplink and downlink flows in ieee 802.11 wireless lans. IEEE Transactions on Wireless Communications, 7(9), 3517–3525.
Chatzimisios, P., Boucouvalas, A., & Vitsas, V. (2004). Effectiveness of rts/cts handshake in ieee 802.11 a wireless lans. Electronics Letters, 40(14):915–916.
Author information
Authors and Affiliations
Corresponding author
Appendices
Appendix 1: Proof of Lemma 1
Proof
The sum of steady-state probabilities \(Q(0), Q(1*)\) and \(Q(2*)\) and the ratio of the steady-state probabilities \(Q(1*)\) to \(Q(2*)\) are proportional:
where \(Q(v*) = \sum _{\fancyscript{V}_1^n\in \{1,2\}^n} Q(v\fancyscript{V}_1^n)\)
By solving the equations in Eq. 44,
The arrival rate \(\lambda _R\) in relay node \(\mathbf{R}\) and the departure rate \(\mu _R\) from relay node \(\mathbf{R}\) are balanced in steady-state. They are expressed as:
We can calculate the relation between \(Q(1\fancyscript{V}_1^n)\) and \(Q(2\fancyscript{V}_1^n)\) as Eq. and applying the detailed balance equations in ascending order of queue state length gives these results:
By applying these equations, the following Lemma is obtained.\(\square \)
Appendix 2: Proof of Lemma 2
Proof
From Eq. 7, the steady-state probability \(P_v(0)\) can be expressed as:
From Eq. 7, the steady-state probabilities \(P(n)\) after some algebra can be expanded as:
\(\square \)
Appendix 3: Proof of Lemma 3
Proof
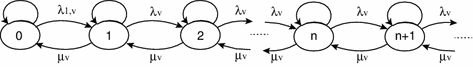
It is assumed that the steady-state probability \(P(0,0)\) is positive, i.e. both virtual queues are non-saturated. Figure 13 illustrates the Markov chain with respect to the number of packets in virtual queue \(v\) at relay node \(\mathbf{R}\). The state transition probability from states 0 to 1 is equal to:
The detailed balance equations are obtained as follows:
Summing all the steady-state probabilities \(P_v(n)\) , the normalized condition and some algebra enable us to obtain Lemma 3 as follows: \(\sum _{n=0}^\infty P_v(n) = 1 \Rightarrow \frac{P_v(0)(1-\tau _R)+\rho _v\tau _RP(0,0)}{(1-\rho _v)(1-\tau _R)} = 1\).\(\square \)
Appendix 4: Proof of Lemma 4
Proof
Based on Fig. 5, we can express the detailed balance equation as follows:
for any \((n_1,n_2)\ne (0,0)\). The above detailed balance equations provide:
for any \((n_1,n_2)\ne (0,0)\).
Summing all the steady-state probabilities \(P(n_1,n_2)\), which are functions of \(P(0,0)\), and the normalized condition enable us to obtain
and then an approximate expression of \(P(0,0)\) is derived as
Appendix 5: Proof of Proposition 1
Proof
First, we note the following relations:
The stationary probability to be in state \(\pi _I\) can be evaluated as follows:
Employing the normalization condition, after some mathematical manipulations, and remembering the relation \(\sum _{i=0}^m\pi _{i,0} = \pi _{0,0}\frac{1-P_{eq}^{m+1}}{1-P_{eq}}\), it is possible to obtain:
The normalization condition yields the following equation for computation of \(\pi _{0,0}\):
Equation 60 is then used to compute \(\tau \) , the probability that a station starts a transmission in a randomly chosen time slot. In fact, taking into account that a packet transmission occurs when the back-off counter reaches zero, we have:
\(\square \)
Appendix 6: Proof of Proposition 2
Proof
According to Fig. 7, there are three durations that the considered node spends at a particular back-off state, \(D_I\), \(D_S\) and \(D_C\). In the idle state, the considered node waits one time slot before decrementing the back-off counter. When the considered node enters the successful state we can compute the duration in this state as follows:
where \(D_I=1\). Similarly, when the node enters a back-off state and finds the channel busy with a collision, this duration can be expressed as:
Let us consider the two cases in detail to calculate the average slot duration for each case:
-
Entering from a previous back-off state: The average slot duration in this case can be expressed using \(P_d\) as
$$\begin{aligned} D_1 = \frac{1}{P_{d}}(p_{ei}D_I+p_{es}D_S+ p_{ec}D_C). \end{aligned}$$(64) -
Entering from a transmission state: In this case we can compute the average slot duration as follows
$$\begin{aligned} D_2 = \frac{\overline{CW}-1}{q\overline{CW}}(p_{ei}D_I+p_{es}D_S+ p_{ec}D_C). \end{aligned}$$(65)
Then we can compute the average slot duration as \(\fancyscript{D} = (1-\tau )D_1 + \tau D_2\). \(\square \)
Rights and permissions
About this article
Cite this article
Mirrezaei, S.M., Faez, K. & Ghasemi, A. Performance Analysis of Network Coding Based Two-Way Relay Wireless Networks Deploying IEEE 802.11. Wireless Pers Commun 76, 41–76 (2014). https://doi.org/10.1007/s11277-013-1485-1
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-013-1485-1