Attempts to share information between public sector organisations over time: A case-based exploration of value conflicts
Abstract
Despite the importance of inter-organisational information sharing (IOIS) in the public sector, such endeavours often fail. Existing research has shown that the values held by collaborating organisations are one important factor affecting these kinds of initiatives. However, research has sought only to a limited extent to address how value conflicts come into play over time. Therefore, this paper aims to explore how conflicting values shape an inter-organisational information-sharing practice in the public sector over time. Using the local/global network framework, we analyse four years’ worth of information sharing in an inter-organisational advisory group in the context of Swedish nuclear waste management. We conclude that different value conflicts are emphasised to different extents at different points in time. That is, values do not uniformly affect IOIS activities, and such conflicts over time reduce the set of potential IOIS activities. We also conclude that when IOIS activities are driven by an individual organisation’s values, individual value rational activities may co-exist with a dysfunctional long-term IOIS practice.

1.Introduction
Problems with public sector inter-organisational collaboration – or pure failures such as the ones between intelligence agencies following the 9/11-incident (Maras, 2017; Yang & Maxwell, 2011) – are often attributed to inabilities to share information (Allen et al., 2014). Although a considerable amount of information exists, it is often located within the so-called silos of the various public organisations that collected it (Graham et al., 2016). Quite naturally, such a silos model (Gil-Garcia et al., 2009) makes it difficult to solve complex tasks crossing the boundaries of various public organisations. Moving towards inter-organisational information sharing (IOIS), that is, ‘sharing information between organisations’ (Karlsson et al., 2017), in the public sector means that decisions can be based on richer information (Dawes, 1996). Also, it offers important benefits such as reduced duplication in data collection, information of higher quality, improved decision-making, increased productivity, and better integration of services (Caffrey, 1998; Gil-Garcia & Helbig, 2006; Landsbergen & Wolken, 2001; Pardo & Tayi, 2007).
However, engaging with other organisations can include a great deal of complexity, such as overcoming differences in data structures, data quality, jurisdictions, and ways of working (Drake et al., 2004; Pardo & Tayi, 2007). As a result, organisations may come across numerous challenges. Research on IOIS in the public sector has been addressed during the last two decades (e.g., Drake et al., 2004; Gil-Garcia et al., 2009; Gil-Garcia et al., 2019; Luna-Reyes et al., 2007; Pardo et al., 2004; Scholl et al., 2012). Despite this knowledge development and the importance of IOIS in the public sector (Bigdeli et al., 2013a; Gil-Garcia et al., 2007), previous research has shown that such endeavours often fail (e.g., Akbulut et al., 2009; Dahlan et al., 2013; Karlsson et al., 2017; Lam, 2005; Yang, 2012; Zhang et al., 2005).
Given the rapid advancement in digital technology, it is relatively easy to attribute these failures to a lack of interoperability between different technical infrastructures, platforms, and frameworks (Scholl et al., 2012). Even though IOIS in the public sector depends, to a varying degree, on technical interoperability, previous research has shown that social and organisational challenges are equally as complex as technological ones (Atabakhsh et al., 2004; Brazelton & Gorry, 2003; Landsbergen & Wolken, 2001). Thus, the social and organisational challenges have received increased attention in recent years (Drake et al., 2004; Gil-Garcia et al., 2009; Luna-Reyes et al., 2007; Pardo et al., 2004; Sayogo et al., 2017; Scholl et al., 2012). Numerous studies have focused on identifying sets of critical factors that contribute to or hinders IOIS in the public sector (e.g., Akbulut et al., 2009; Dahlan et al., 2013; Karlsson et al., 2017; Lam, 2005; Yang, 2012; Zhang et al., 2005). Others have aggregated the relations between critical factors to identify meta-factors (e.g. Fan et al., 2014; Gharawi & Dawes, 2010; Landsbergen & Wolken, 2001; Praditya & Janssen, 2016; Yang & Maxwell, 2011). Consequently, these studies have increased knowledge of the social and organisational factors that are most likely to impact the success or failure of IOIS in the public sector.
Section 2 shows that many of these studies acknowledge conflicting values as one type of critical factor, often being identified as one of the barriers for successful IOIS. Where past inquiries seem to have put less emphasis, however, is in their consideration of how value conflicts impact the negotiation of IOIS in the public sector over time. Researchers have often studied conflicting values as a set of factors that impact IOIS in the public sector at a given time (e.g. Akbulut et al., 2009; Dahlan et al., 2013; Lam, 2005; Pardo et al., 2008; Yang & Maxwell, 2011; Zhang et al., 2005). The merits of previous research notwithstanding, most of these studies do not capture IOIS as an evolving process. The few research papers (Dawes, 1996; Karlsson et al., 2017; Scholl et al., 2012; Zhang & Dawes, 2006) investigating IOIS as an evolving process rarely had the intention to address how values come into play in such a process. On the assumption that multiple forms of rationality exist at any one time during IOIS, more needs to be known when it comes to how conflicting values change public sector IOIS during longer terms. Thus, we pose the research question: How do conflicting values shape an inter-organisational information-sharing practice in the public sector over time?
This paper aims to explore how conflicting values shape an inter-organisational information-sharing practice in the public sector over time. For this purpose, we tailor the local/global network framework proposed by Law and Callon (1994). The framework has previously been used successfully for analysing emergent negotiations of interests of different actors in an IT project (Gasson, 2006) and for better understanding the success or failure of e-government initiatives (Heeks & Stanforth, 2007). We used an inter-organisational advisory group in the context of Swedish nuclear waste management to understand the impact of conflicting values on IOIS in the public sector and illustrate the IOIS activities as a trajectory. In this context, trajectory means a process that assumes path dependencies in terms of carriers of history but, not that outcomes or states of the trajectory are strongly predicted or determined by its initial states (Araujo & Harrison, 2002). Such trajectories have been shown to be especially important in inter-organisational contexts (e.g. Araujo & Harrison, 2002; Håkansson & Waluszewski, 2002).
The remaining parts of the paper are structured as follows. The next section discusses related research on value conflicts in IOIS in the public sector. The third section addresses the theoretical framework we used in our analysis. In particular, we discuss how we have tailored it to fit our inquiry into values and the context of IOIS. In the fourth section, we discuss the research method adopted. In the fifth section, we carry out the analysis, and in the sixth section, we discuss our findings, the limitations of our study, and avenues for future research. Finally, the paper ends with a short conclusion.
2.Related research
To contextualise this study, we carried out a literature review of research on social and organisational factors and IOIS in the public sector to identify how conflicting values have been researched in international journals, at international conferences, and in book chapters between 1981 and 2020. We present the details of our analysis in Appendix A and offer an overview in this chapter. Our review shows that many studies have addressed social and organisational factors and IOIS in the public sector and that conflicting values are frequently acknowledged among the barriers to successful IOIS in the public sector.
Values could be described as prioritised principles or beliefs about end states or behaviours that transcend specific situations (Agle & Caldwell, 1999). Our review used a broader interpretation of value conflicts, comprising all kinds of expressions of conflicting rationalities. Our first observation is that value conflicts have been addressed in many of the reviewed studies – twenty-nine of forty-five studies – and that researchers have used various concepts to capture value conflicts in studies on IOIS in the public sector: cultures (e.g. Drake et al., 2004), goals (e.g. Pardo et al., 2009), interests (Dawes et al., 2012), missions (e.g. Dawes & Pardo, 2002), norms (Lee & Rao, 2007), objectives (e.g. Lam, 2005), and values (e.g. Yang & Wu, 2014).
Our second observation is that only three of the twenty-nine studies that address value conflicts have sought to address how conflicting values shape an IOIS practice in the public sector over time (Dawes et al., 2011; Dawes et al., 2012; Zhang & Dawes, 2006). Instead, most studies – twenty-six of them (e.g. Akbulut et al., 2009; Bigdeli et al., 2011; Bigdeli et al., 2013a; Dahlan et al., 2013; Dawes & Pardo, 2002; Gil-Garcia et al., 2007; Lam, 2005; Pardo et al., 2008; Yang & Maxwell, 2011; Zhang et al., 2005) – have identified and investigated value conflicts as one factor among other factors that affect the outcome of IOIS. These studies seem to have a wider focus, addressing what affects IOIS practices in the public sector.
Zhang and Dawes (2006) is one of the studies that addressed how conflicting values shape an IOIS practice in the public sector over time. They studied barriers to the success of IOIS in the public sector using a research model constructed on existing research. Emphasising that factors changed over time, they concluded that non-alignment of goals was important in causing the emergence of organisational barriers. However, this survey-based study could not reveal many details of the change process. Another study is Dawes et al. (2011), who formulated the proposition that ‘differences in beliefs, values and norms, and language will create misunderstandings, cause delay, and generate conflicts that impede collaboration and negatively influence learning in TKNs [transnational knowledge networks]’. Dawes et al. (2012) constructed, based on a case study, a dynamic model of transnational knowledge sharing where culture, goals, and interests both impact and are affected by the processes when organisations share information.
We identified seven studies (Dawes et al., 2009; Drake et al., 2004; Fedorowicz et al., 2007; Gil-Garcia et al., 2019; Luna-Reyes et al., 2007; Pardo et al., 2009; Yang, 2012; Yang & Wu, 2014) that acknowledged time as an important aspect in shaping IOIS in the public sector. However, these studies do not explicitly address time in their analysis. One example is the study by Drake et al. (2004). They analysed three subcultures of IOIS within the public sector. They argued that ‘values held by one subculture can be a barrier to information sharing with other subcultures, both within and across agencies’. Furthermore, in the back end of their paper, they claimed that ‘it is our contention that information sharing is shaped by historical experiences with information sharing’. Pardo et al. (2009) identified that the diversity of participating organisations and their goals are important determinants for IOIS in the public sector. They quoted interviews where it was argued that IOIS was a negotiation between organisations, that is, having a dynamic aspect. A final example is Yang (2012) and Yang and Wu (2014). In their search for factors that could influence IOIS in the public sector, they identified that the values related to IOIS held by organisations are important. They found that some organisations are more liberal or willing to share information, while others are more conservative. Yang (2012) concluded that negotiation among public agencies holding different values is often time-consuming.
Our third and final observation is that none of the studies mentioned above (Dawes et al., 2011, 2012; Zhang & Dawes, 2006) that address how conflicting values shape an IOIS practice has investigated whether there is any difference in how values come into play over time. Instead, value conflicts have been treated as one unified factor among other factors, although it is reasonable to assume that several value conflicts can be present simultaneously. We thus have limited detailed knowledge on how a set of values affects an IOIS practice in the public sector over time.
3.Theoretical framework
To understand the translation trajectory of IOIS in the public sector, we adapted the framework of local/global network (Law & Callon, 1994; Papadopoulos & Merali, 2008). This framework was initially developed to explain the trajectories of inter-organisational projects. It was later used as a trajectory framework to gain a better understanding of the success or failure of e-government projects by focusing on the political interactions of e-government projects (Heeks & Stanforth, 2007) and to analyse how different perspectives influenced the political trajectory of actions and interactions in the development of an IT project (Gasson, 2006). The study by Papadopoulos and Merali (2008) is an example of using the local/global network framework in organisational research. They focused on project trajectories, stakeholder networks, and the emergent dynamics in two lean implementation projects within a National Health Service trust to better understand the outcome of lean projects.
We chose the framework for two specific reasons: 1) the framework uses trajectories to uncover the dynamics of inter-organisational practices, such as how IOIS practices are shaped over time, and 2) a study on IOIS needs a framework that focuses on relations within such collaboration and shows links between the different organisations, represented by the actors that take part in the collaboration. As will be shown in the description of our research setting (see Section 4.1 for details), this framework overlaps with the characteristics of the investigated case. In the case, several public sector organisations participated in the inter-organisational advisory group on nuclear waste management. Each organisation was represented in the advisory group by one or more members to share information about experiments and findings regarding a method for storing nuclear waste. Thus, these members took part in the actual IOIS practice during several years and acted as the link between the participating organisations.
A local network is defined as ‘the development of an array of the heterogeneous set of bits and pieces that is necessary to the successful production of any working device’ (Law & Callon, 1994). In the present case, the inter-organisational advisory group represents the local network. This is ‘inside’ the IOIS practice, with a focus on the relations of actors enacting the IOIS practice. The global network has been defined by Law and Callon (1994) as ‘a set of relations between an actor and its neighbors on the one hand, and between those neighbors on the other’. The global network provides resources such as money, expertise, or political support (Heeks & Stanforth, 2007) for enabling the IOIS practice. In our case, the global network consists of the different organisations represented in the advisory group. In other words, they can be seen as residing ‘outside’ of the IOIS practice.
Information in the shape of ‘intermediaries’ (Law & Callon, 1994) is passed between the local and global networks. In the present case, intermediaries are documents, such as presentations, reports, and meeting protocols. This passing of information between organisations in the global network is carried out by the members of the advisory group as ‘a single locus that controls such transactions between the two networks’ (Heeks & Stanforth, 2007), making it an obligatory passage point (Latour, 1987) where all transactions are controlled (Law & Callon, 1994). Consequently, IOIS is dependent on the workings of the local network. It is also important to understand that there is a mutual shaping between the networks and between different actors located within the networks (Law & Callon, 1994). When an actor introduces activities in the local network based on a set of values, it can be seen as an attempt to shape the local network and its workings as values influence relations (Agle & Caldwell, 1999). Therefore, introducing activities can be seen as an attempt to mobilise members in the advisory group and control the local network. Such activities can succeed or fail to align the values promoted by other members of the advisory group and, consequently, mobilise to a lesser or larger degree the IOIS between the advisory group members as well as increase or decrease the possibilities for organisations in the global network to fulfil their roles in the larger context. Together, these activities form an IOIS trajectory.
Negotiations for IOIS can be graphically illustrated as a trajectory within a 2
Figure 1.
IOIS framework (adapted from Law & Callon, 1994).
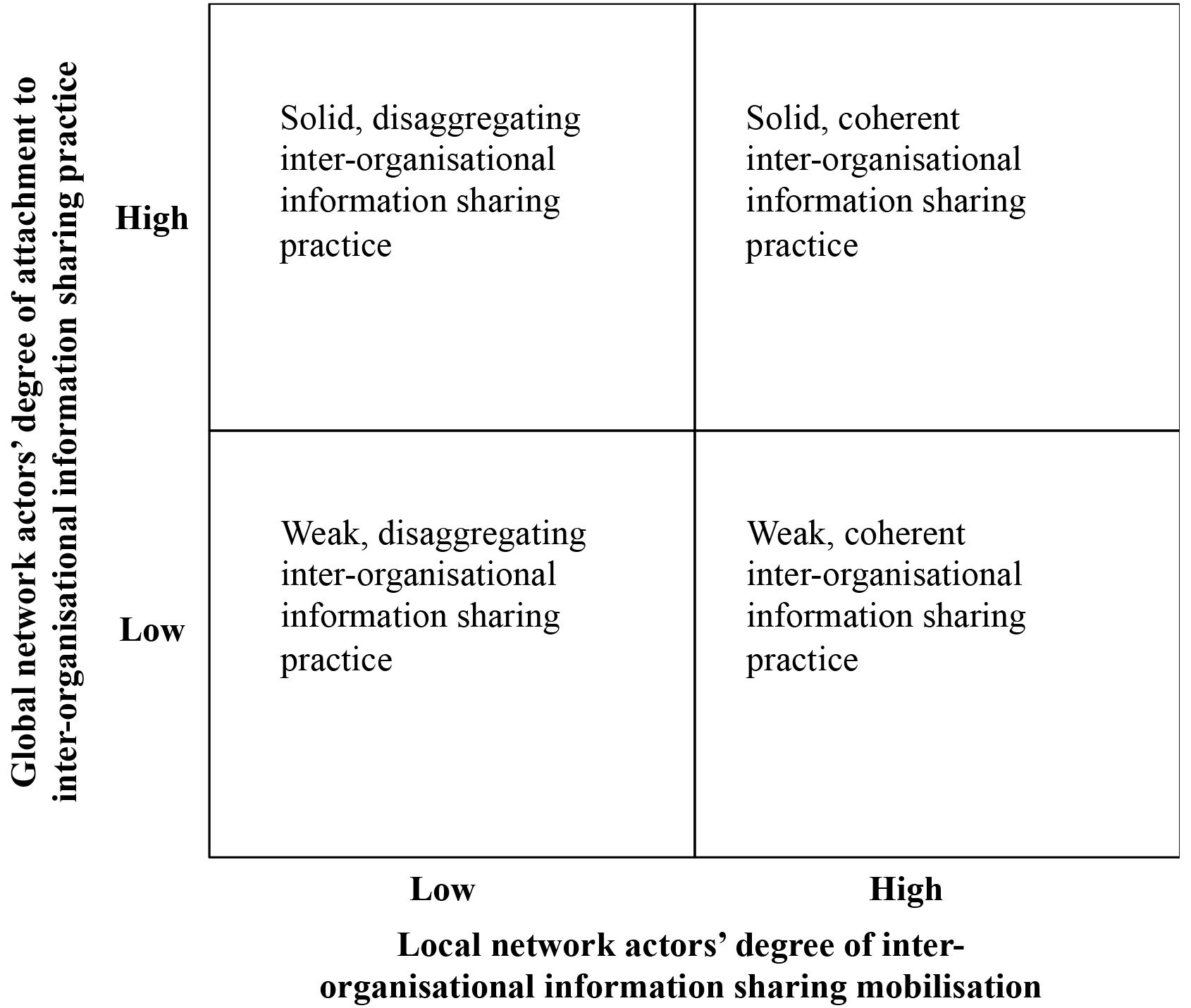
The lower-right corner illustrates a weak and coherent IOIS practice. Here the local network combines a high degree of mobilisation with a low degree of attachment. Actors in the local network are able to negotiate and compromise on their respective values so that particular characteristics of the sharing of information develop. However, the actors in the global network are weakly attached to the IOIS practice because the IOIS is not considered valuable. Finally, the lower-left corner shows a weak and disaggregating IOIS practice. Here a low degree of attachment to the IOIS practice is combined with a low degree of mobilisation to the IOIS practice. Yet again, actors in the local network emphasise activities that originate from their respective organisations’ values, stressing value conflicts. As a result, the local network actors are unsuccessful in sharing information; that is, there is a low degree of IOIS mobilisation. Simultaneously, the IOIS practice becomes weakly attached to the global network actors since it does not support the actors’ roles and the values they hold in the global network.
4.Research method
We carried out an interpretative case study (Walsham, 1995) on information sharing in an inter-organisational advisory group in the context of Swedish nuclear waste management. The particular research setting was chosen because the IOIS was to a large extent based on social interaction between collaborating organisations, emphasising the negotiations of the IOIS trajectory. In this case, the advisory group shared information between the collaborating organisations for four years. This access to longitudinal data is important in order to capture an IOIS trajectory where different values come into play over time (Heeks & Stanforth, 2007).
4.1Research setting
The Swedish nuclear power program was initiated in the late sixties, and over the years, nuclear waste disposal has become a fiercely debated issue in Sweden. The Swedish nuclear power industry established a specific organisation, Svensk Kärnbränslehantering AB (SKB), to deal with this issue. Starting in the seventies, SKB developed its KBS-3 method. In short, this method envisioned encapsulating highly radioactive nuclear waste in copper canisters with bentonite clay and depositing these in drilled, man-made holes approximately 500 metres below the surface. Even though the formal mandate to develop the solution rests with the SKB, other organisations have functioned as ‘watchdogs’ for several years. These include, for example, Miljöorganisationernas Kärnavfallsgranskning (MKG), a Swedish non-governmental organisation (NGO). In 2010, after several years of research into a suitable location for the repository, SKB chose the municipality of Östhammar in eastern Sweden as the site for the repository and SKB subsequently applied for a permit to construct the repository.
At the same time, SKB decided to create an advisory group in response to a study on nuclear waste management carried out by the KTH Royal Institute of Technology (KTH). The study indicated that copper might corrode when exposed to water with certain chemical and physical characteristics. Such characteristics resembled those found at Sweden’s proposed final repository. Corrosion could thus severely jeopardise the safety of the KBS-3 method. The purpose of the advisory group was to ‘give external organisations, including public agencies, environmental organisations, and KTH insights in the planning, execution, and results from the new experiments on copper corrosion in oxygen free environment’ (Protocol advisory group, March 24, 2010). It meant that the advisory group included several types of organisations, including municipalities, counties, regional actors, research institutions, government-owned companies, and NGOs. Thus, they could all be considered as representing different types of organisations in the public sector (Perry & Rainey, 1988).
4.2Data collection
The data were obtained from two sources: (i) documents and (ii) interviews. These two data sources present an opportunity to triangulate data and different perspectives on the IOIS practice (Patton, 1990). The documents were an important source to understand what information has been shared and the reasons behind the sharing (or not). They worked as intermediaries between the local and global networks. We collected eighteen documents in the form of meeting protocols held by the advisory group between 2010 and 2014, which were maintained by SKB and reviewed by advisory group members. The meeting protocols included both summaries of advisory group meetings as well as rich verbatims from the discussions. The length of the meeting protocols ranged between 7 and 14 pages. Furthermore, the meeting protocols included forty-seven appendices (e.g., presentations) from the advisory group’s meetings. The meeting protocols enabled detailed modelling of how work was conducted in the advisory group and allowed the tracing of additional intermediaries in the form of reports passed between the networks after the advisory group meetings. In total, collecting the documents created an understanding of how specific information was perceived at specific times. The collected documents served as input for the interviews and to validate statements made by the interviewees.
In total, six semi-structured interviews with members of the advisory group were carried out (see Appendix B for the interview protocol). The selection of respondents was based on our analysis of the meeting protocols. Of all the local network participants, SKB, MKG, and KTH were identified as key organisations, that is, organisations that took an active part in the studied IOIS practice and particularly in the activities that altered the IOIS practice over time. Therefore, one representative from each of these organisations figured as a key informant in the interviews. Drawing on the idea of purposeful sampling (Patton, 1990), we sought pertinent data that elaborated on the activities that altered the IOIS practice and the rationale behind these activities. Interviews were also carried out with the advisory group’s chairperson (an independent consultant), and with the representatives from the Östhammar and Oskarshamn municipalities. These latter interviews were complementary and contributed to a contextual understanding. The interviews were conducted by phone, recorded on tape, and subsequently transcribed before analysis. All interviews lasted approximately one hour and were carried out in 2014 after the advisory group had been dissolved.
4.3Analysis
By viewing the IOIS practice as emergent, negotiated, and dynamic, it takes on the characteristics of a process. This process was analysed in terms of key information-sharing activities that substantially altered the advisory group’s IOIS. The analysis was carried out in six steps, where the first three steps draw upon business process modelling (Aguilar-Savén, 2004) and in particular modelling of action diagrams (Ågerfalk & Goldkuhl, 2001). In action diagrams, it is possible to model different activities (actions) of a process, the actors involved in the activities, and the flow of information between the activities.
1. We listed activities in the IOIS practice and the information that was used in those activities or resulted from those activities. We used intermediaries in the form of shared documents together with interviews as input for this analysis. The shared documents, such as meeting protocols, contained descriptions of IOIS activities and/or activities that affected IOIS. To identify IOIS activities, we analysed the interviews with a focus on the respondents’ descriptions of how information was shared or not shared.
2. We reconstructed the IOIS practice by placing the identified activities in chronological order and identified activities that altered the IOIS practice. We analysed the interviews for respondents’ description of how these activities affected future IOIS and the respondents’ views on why changes appeared.
3. We identified the actors who were involved in each activity, as well as the actor driving each activity. This was done using the documents and interviews as input.
4. Similar to Heeks and Stanforth (2007), we analysed how each activity introduced movements in the framework (Fig. 1). In our case, movements meant a) it increased or decreased the advisory board members’ mobilisation of IOIS (horizontal movement) and b) it increased or decreased the participating organisations’ attachment to the IOIS practice (vertical movement). For example, if an activity meant that additional information was enrolled in the advisory group, it increased the mobilisation. Furthermore, if by sharing the information one or more organisations found additional support for their role(s) in the global network, without other organisations losing support for carrying out their role(s), we identified an increased attachment to the IOIS practice.
5. We identified the values that the different actors used when introducing these activities to the IOIS practice. Similar to Hedström et al. (2011), we used end states or behaviours as a starting point for capturing values. Particular attention was paid to identified activities or words related to these activities, that: a) showed approval or disapproval, b) were intended to achieve a certain goal or result, and c) showed a consistent tendency regarding the choices made.
6. We analysed the extent to which the advisory group members driving a particular activity emphasised or de-emphasised values of the organisations to which they belonged. Hence, this step focused on the change in emphasis on conflicting values causing the horizontal and vertical movements.
5.Analysing the trajectory
Table 1 shows a compilation of the values at play in each of the nine key IOIS activities. The leftmost column shows the identifier of the IOIS activity (A-I). The three subsequent columns contain the values that were at play: one column per analysed organisation. Figure 2 illustrates the IOIS practice as a trajectory, using the same IOIS activities. The plus and minus signs on the arrows illustrate an increased and decreased emphasis on conflicting values, respectively.
Table 1
Values that guided organisations in different activities of the IOIS practice
| Values at play | |||
|---|---|---|---|
| IOIS activity | SKB | MKG | KTH |
| A: Inviting group members | – Transparency– Suspicion | – Suspicion | – |
| B: Requesting total transparency | – Transparency– Confidentiality | – Transparency | – Scientific rigour– Scientific validity |
| C: Requesting access to SKB’s research reports | – Confidentiality | – Transparency | – |
| D: Reporting research results | – Confidentiality– Legitimation | – Suspicion | – Availability– Suspicion |
| E: Dissemination of the work to the general public | – Control– Legitimation– Empowerment | – Transparency | – |
| F: Revising the publication policy | – Confidentiality | – Transparency– Availability | – Transparency– Availability |
| G: MKG is opting out | – Confidentiality | – Transparency | – |
| H: Reviewing research reports | – Control | – | – Integrity of data– Scientific validity |
| I: KTH is opting out | – Control | – | – Scientific rigour– Scientific validity |
Note: ‘–’ no value could be identified for this actor during this activity.
5.1A: Inviting group members
The advisory group was established in early 2010 by SKB as a response to a study by researchers of KTH. They indicated that copper corrosion might occur in water with certain characteristics despite the absence of free oxygen. Even though SKB was ‘doubtful about copper reacting with water under the formation of hydrogen gas’ (Protocol advisory group, March 24, 2010), they decided to establish an advisory group. Thus, this act of establishment expressed suspicion as a value, in the sense that it is important to question the intention of others. They invited several actors, and among the organisations accepting the invitation were KTH and MKG (Protocol advisory group, March 24, 2010). In an interview, one MKG representative stated that they ‘saw this as interesting, and, therefore, MKG decided to participate in the advisory group although we somehow suspected that this was PR [a public relations exercise], that it was a big promotional project from the SKB’s perspective’. This indicates a value of suspicion originating from MKG concerning SKB’s decision to establish the advisory group. The suspicion would have been that SKB ultimately wanted to prove that the KBS-3 method was not flawed.
Figure 2.
The trajectory of the IOIS practice.
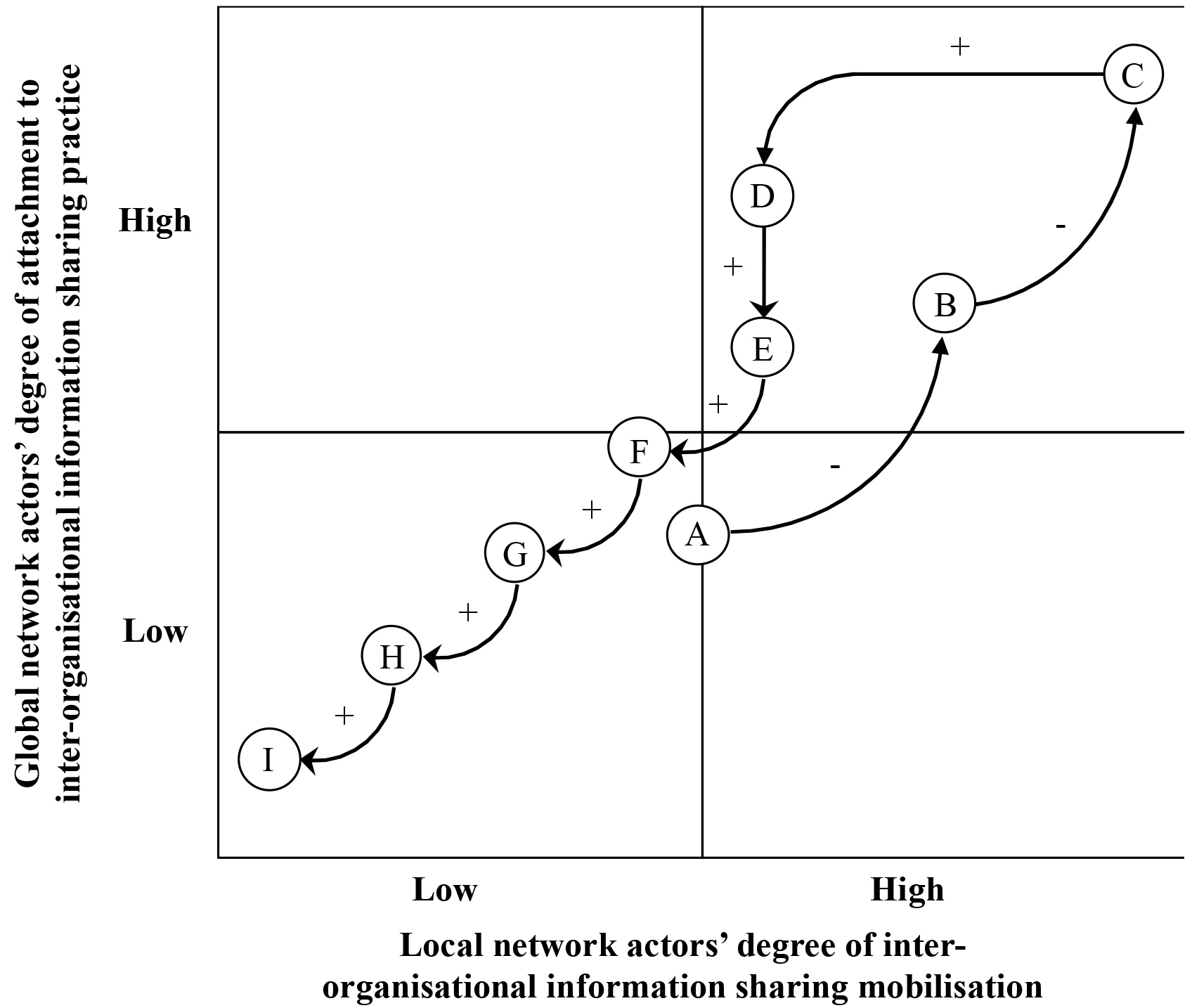
Originally, SKB identified two research projects that should be reported to the advisory group. The first project, by Uppsala University (UU), aimed at repeating the experiments of KTH. The second project, by SP Technical Research Institute of Sweden (SP), analysed the long-term corrosion characteristics of copper. SKB expressed the view that IOIS in the advisory group should be guided by the value of transparency; that is, it is important to be open. One SKB representative said, ‘We also concluded that, for an advisory group of this kind, full transparency about the ongoing experiments would be essential’. With this ambition of transparency, SKB suggested future IOIS activities to the advisory group, where future project activities to UU and SP researchers were to be presented and discussed before effectuation. In this way, the advisory group was supposed to function as an obligatory passage point for the two projects, where research about copper corrosion carried out in the global network would always be discussed in advance within the local network. This also meant that any results and interpretations from this research were to be presented to the advisory group.
At point A in Fig. 2, the local network actors entertained a suspicion value of the other global network actors’ motives. The global network actors were considered weakly attached to the IOIS practice, a practice that so far was without any proof of either coherency or disaggregation with regards to IOIS mobilisation.
5.2B: Requesting total transparency
At point B in Fig. 2, the MKG representative and the KTH researchers demanded that the SKB representatives should share all relevant information about SKB’s research on copper corrosion. SKB established the advisory group to discuss ‘corrosion of copper in an oxygen-free environment’ (Protocol advisory group, March 24, 2010), and additional research on copper corrosion was not supposed to be reviewed by the advisory group. Subsequently, SKB did not view the advisory group as a legitimate arena for IOIS about all research projects on copper corrosion. Thus, a value of confidentiality emerges; that is, it is important not to disclose information to unauthorised actors.
By contrast, MKG regarded this demarcation of the IOIS as too narrow and emphasised the value of transparency. When interviewed, an MKG representative said, ‘Already in the acceptance letter we addressed the issue that SKB has conducted a lot of other copper corrosion research […] and we would therefore like to have a complete openness about the whole thing, so to speak’. The MKG representative repeatedly insisted that information about all SKB’s research projects on copper corrosion should be shared in the advisory group. For example, during the first advisory group meeting, an MKG representative requested access to an additional project: ‘I suggest that the LOT experiments are made available in the same way as the current project’ (Protocol advisory group, May 19, 2010). The same protocol showed that the SKB representatives were open to this ‘as a possibility’, based on SKB’s respective value of transparency. Later, SKB decided that information about two experiments from the Äspö laboratory were to be made available to the advisory group.
Similarly, the KTH researchers supported the MKG representative’s request for more information about additional research projects on copper corrosion: ‘All experiments are important! It is important for openness […] It would be valuable if the advisory group had access to how additional experiments were arranged’ (Protocol advisory group, May 19, 2010). KTH understood its role as that of a scientific reviewer and advisor to the projects that the advisory group was informed about. According to one KTH representative, ‘We realised that we were the only ones who could comment on them [the results] scientifically’. As a scientific reviewer and advisor, the researchers from KTH were motivated by their attachment to the values of scientific rigour (i.e., it is important to undertake studies in a way that enhances confidence in the veracity of their findings) and scientific validity (i.e., it is important how well a scientific piece of research measures what it sets out to measure or how well it reflects the reality it claims to represent).
At point B in Fig. 2, confidentiality is competing with transparency, scientific rigour, and scientific validity during the negotiation. The trajectory moved upwards and to the right. The SKB representatives decreased their emphasis on SKB’s value of confidentiality, which resulted in the increased mobilisation of information sharing for the local network actors. Also, it meant that the global network actors increased the attachment to the local network; the activity increased the possibility for MKG and KTH to act as watchdog and reviewer, respectively.
5.3C: Requesting access to SKB’s research reports
The MKG representative regularly requested access to research results of SKB projects. When the advisory group was established, SKB published research reports and work-in-progress reports. The latter were ‘compilations that we had created for our own use. We could share these with someone who needed them for further work relating to our [research] questions’ (Interview SKB representative). Hence, these reports were shared upon request. The MKG representative’s requests were driven by the value of transparency. According to the protocols of the advisory group, the MKG representative was very keen on accessing additional SKB research on copper corrosion. Such an interest was confirmed by one KTH researcher. ‘We did not try to push them [SKB] so hard, but NN [at MKG] tried to do it as a matter of principle’. According to the MKG representative: ‘I started to say that here you have a reference, can we get this report and then they started to send us the reports, including a yearly report which was an IPR report [work-in-progress report] plus four quarterly reports of the work conducted at that time. In these you could see other reports, which I started to gather one by one. And this became a system that made the IPR reports publicly available’. Consequently, SKB came along and enrolled requested reports in the work carried out by the advisory group.
At point C in Fig. 2, confidentiality is competing with transparency, and the trajectory moves upwards and to the right. SKB’s representative de-emphasising confidentiality and deciding to enrol their IPRs in the advisory group increased information sharing mobilisation in the advisory group. Yet again, this additional information made it easier for MKG and KTH to act according to their roles, increasing the global network actors’ attachment to the IOIS practice.
5.4D: Reporting research results
The actors in the global network reported their ongoing research to the advisory group. For example, researchers from UU (e.g., Protocol advisory group, March 23, 2011; November 6, 2012; June 14, 2013) and SP (e.g., Protocol advisory group, August 27, 2010; March 23, 2011; February 1, 2012) gave presentations about the results of ongoing research. Furthermore, these results and their impact on the future project activities were discussed. This shows how the advisory group was considered an obligatory passage point. According to one SKB representative, these actors were in control of those presentations and the type of information they made available: ‘When Uppsala presented their results, they did it without any comments from SKB. They participated and presented their results in their own name’.
However, the actual access to this information was a contested issue, which appears to be related to some extent to the needs of the advisory group members when reviewing and suggesting directions for future work. KTH researchers claimed that information was made available in such a way that it was black-boxed. One KTH representative said, ‘We were not given access to anything in advance, instead, there was a quick presentation of a lot of results, and that became a problem in itself. These were quite complex presentations […], and we did not even get the presentations afterwards […]. Also, the minutes were released several months after the meeting, and this caused conflicts’. Hence, as shown in Table 1, a tension developed between the values of confidentiality and availability (i.e., it is important to make information available and usable on demand).
Also, both the researchers from KTH and the MKG representative expressed the suspicion that not all of the experiments done by SKB on copper corrosion were presented to the advisory group. One KTH researcher stated, ‘I think Uppsala did more experiments, but we were not informed about them. That was somehow the methodology of SKB. They signed a contract with the researchers from Uppsala, where it was stated that SKB owned all the results. SKB had the right to modify their texts. It even is stated as such in their contract. […] It was a very bad agreement. MKG got hold of the contract’. This statement about the research contract with UU shows that the researchers from KTH and the MKG representative were suspicious of the reporting by SKB.
SKB presented a different point of view regarding whether the ongoing research had been made available, albeit with some exceptions. One SKB representative said, ‘Information was made available in the protocols. I believe there was one occasion when the persons doing the presentation did not want to distribute the material. In that case, we decided at the meeting not to send out the notes either. I believe it was in an early stage when the researchers from Uppsala presented their results, results that they felt unsure of’. Also, one SKB representative expressed that SKB had the burden of proof. They needed to show why it was not possible to draw conclusions from some experiments. SKB argued that their actions were motivated by their attachment to the value of legitimation; that is, it is important to assert with logic and justification.
At point D in Fig. 2, the values of availability and suspicion are competing with confidentiality and legitimation. As a result, the trajectory moves to the left and downwards. Different views on how research on copper corrosion was made accessible for review in the advisory group hampered the advisory group members’ possibility to give feedback. This made it more difficult for MKG and KTH to act according to their roles, decreasing their attachment to the IOIS practice.
5.5E: Dissemination of the work to the general public
In an interview, one SKB representative said, ‘The day we [SKB] send the protocols [of the advisory group] to the Swedish Agency for Radiation Safety, then they become automatically public documents [according to the Swedish principle of access to official records]’. This procedure was important from the point of view of SKB in terms of their aim to ‘achieve quality in reporting’ and to ensure ‘that all members of the advisory group would get the chance to give feedback on the content before it was made public’. This view can be associated with the values of legitimation and empowerment (i.e., it is important to enable participants to represent their interests).
However, directly after each advisory group meeting, and before SKB had published the meeting protocol of the advisory group, MKG decided to publish on their website their interpretation of the work of the advisory group. In addition, MKG provided further information such as about IPR reports. MKG’s actions were anchored in their value of transparency. In an interview with an MKG representative, it was stated: ‘We have built the trustworthiness of our organisation on transparency and believe it is important’.
SKB considered at this point that none of the organisations had broken any confidentiality commitments. However, one SKB representative argued simultaneously that ‘They [MKG’s statements] could in some cases differ quite substantially from what the official meeting minutes said,’ and ‘we [SKB] wanted to retain the right to inform people about what happened, regardless of the fact that other parties could inform people as they saw fit. The responsibility for the dissemination of information was, so to speak, ours’ (Interview SKB representative). As Table 1 shows, the SKB based their view on the value of control; that is, it is important to be able to influence or direct the course of events.
At point E in Fig. 2, the transparency value is competing with control, empowerment, and legitimation. The trajectory moved downwards. MKG’s increased emphasis on the transparency value was the guiding principle for sharing the IPR reports. This dissemination of the work from the advisory group to the general public did not change the local network’s IOIS mobilisation. However, it made it more difficult for SKB to fulfil their role in the global network.
5.6F: Revising the publication policy
In an interview with a representative from SKB, the following statement was made: ‘This advisory group had a great impact on SKB’s publication policy’. SKB noticed the advisory group’s recurrent pattern of requesting and using research reports and work-in-progress reports for purposes other than those intended by SKB. As one SKB representative said, ‘It became very clear, quickly, that this was not a good way to build trust’. SKB stressed the confidentiality value by sharpening its publication policy. ‘We concluded quite early on, based on the ongoing work in the advisory group, that we should not have public reports. If we have material, which we of course have, this is to be viewed as intermediate results and never classified as a report or a finished product; instead it is a document. The whole company [SKB] bought in on this, eventually. It took some time’ (Interview SKB representative). This statement shows that SKB’s information sharing procedure did not only change with regard to the local network; it also impacted the global network, making all of SKB’s external information sharing activities more restricted.
SKB’s decision was a blow to MKG’s possibilities for disseminating information to the general public. The dissemination of the advisory group’s work to the general public continued after SKB had changed their publication policy; however, the information that could be published was now more restricted. In an interview, the MKG representative noted: ‘Now the IPR reports do not exist anymore, I do not know what happened, if they changed to a new report system […]. This is a culture that should not be there, I think, when such important issues are at stake’. This change was also noted by the researchers from KTH, who claimed that they were now ‘regarded in the same way as the general public, instead of having some kind of exclusive position as a member of the advisory group’ (interview KTH representative). Consequently, this was a setback for both MKG and KTH, who both viewed availability and transparency as important values that were worth protecting.
At point F in Fig. 2, the confidentiality value is competing with transparency and availability. This moved the trajectory to the left and downwards. SKB’s new publication policy reduced the IOIS mobilisation of the local network. This meant that MKG could not be as transparent towards the general public as they wanted, and KTH got access to less research data, decreasing their attachment to the IOIS practice.
5.7G: MKG is opting out
In October 2012, MKG officially gave notice that they were leaving the advisory group. ‘We did not leave because of any conflict or something like that, not at all, but out of principle [perceived lack of transparency]’ (Interview MKG representative). MKG consistently wanted the protocols to include everything about the experiments on copper corrosion. At the same time, SKB, because of its increasing attachment to the value of confidentiality, was more careful about which data should be disclosed.
At point G in Fig. 2, confidentiality is competing with transparency. This moved the trajectory downwards and to the left. The MKG representative leaving the advisory group meant de-attaching MKG from the IOIS practice. Also, and from the perspective of SKB and KTH, this decreased the mobilisation of IOIS in the advisory group, as less feedback would be shared in the local network.
5.8H: Reviewing research reports
The review of preliminary research reports continued for a while, even after MKG had left the advisory group. However, difficulties arose when the researchers from KTH claimed that one SKB representative had instructed them, when reviewing a report, to disregard later research findings that would influence the report. According to the researchers from KTH, these new findings would uncover a potential bias that may have affected the data in the report. According to them, the process did not conform to established scientific practice, thus conflicting with their values of data integrity (i.e., it is important that information is accurate and complete) and scientific validity. They contended that SKB wanted to force the researchers from UU to publish a flawed report: ‘We said that now we know there are erroneous conclusions building on erroneous results – that is, equipment that is no good – then you cannot expect us to review it. It is not possible. You have to openly admit that, “well, we had such problems with the equipment so we cannot say anything about copper corrosion”. Then NN from the SKB came in and said, “No, we cannot go on like this, you can go home and review the report even though we know that there are problems here. We will deal with them in the next report.” That was too much for us. […]. We thought it would be more or less unethical to review it’ (Interview KTH representative). Thus, this tension originates from different views on values. As shown in Table 1, the SKB representative’s instructions were motivated by their attachment to the control value.
At point H in Fig. 2, the control value is competing with integrity of data and scientific validity. This shifted the trajectory left and downwards. When the SKB representative decided to enforce the value of control, the representative restricted the research data to review and the KTH researchers’ feedback to the advisory group. It decreased KTH’s attachment to the IOIS practice; acting as a reviewer became more difficult.
5.9I: KTH is opting out
In 2013, the researchers from KTH declined further participation in the advisory group, claiming that they had been instructed by SKB to violate the integrity of research data by disregarding research findings that would influence the review of a research report. They interpreted the series of events as a process that started to deviate from established procedures of scientific operation, such as the ones routinely adhered to by researchers from KTH.
At point I in Fig. 2, the researchers from KTH stressed the values of scientific validity and scientific rigour. This emphasised the conflict with SKB’s control value and shifted the trajectory downwards and to the left. When the KTH researchers left the advisory group, they de-attached themselves from the IOIS practice. Also, it meant a further decrease of the IOIS mobilisation of the local network actors.
After the KTH researchers left the advisory group, the advisory group continued their work until the group was finally dissolved in early 2014 (Protocol advisory group, February 25, 2014). One SKB representative argued: ‘When KTH left, we no longer had a scientific counterpart in the group, and it became just SKB informing municipalities and counties […]. We can do that anytime and for that, we do not need an advisory group’.
6.Discussion
6.1Implications for research
From the analysis of the particular case presented here, it appears that IOIS in the public sector is a process of complex interactions, where the interactions change over time. Having said that, we do not claim that this specific finding is new. Instead, this aspect of our results corroborates earlier findings (Drake et al., 2004; Gil-Garcia et al., 2007; Karlsson et al., 2017; Scholl et al., 2012; Zhang & Dawes, 2006). Thus, we confirm that there appears to exist a feedback loop (Drake et al., 2004), or learning process (Dawes, 1996), by which IOIS is shaped by previous experiences of IOIS activates. More importantly, the present analysis highlights the importance of studying IOIS in the public sector as a phenomenon consisting of more than just isolated activities.
To date, research has concluded that conflicting values affect IOIS in the public sector (e.g. Dawes & Pardo, 2002; Drake et al., 2004; Luna-Reyes et al., 2007; Pardo et al., 2009; Yang, 2012; Yang & Wu, 2014; Zhang & Dawes, 2006) – something that we confirm. However, as we have shown, many of the existing studies have taken a static view and factorial approach on values conflicts (e.g. Akbulut et al., 2009; Bigdeli et al., 2011, 2013a; Dahlan et al., 2013; Dawes & Pardo, 2002; Gil-Garcia et al., 2007; Lam, 2005; Pardo et al., 2008; Yang & Maxwell, 2011; Zhang et al., 2005). It means that these studies have focused on what affects IOIS. We contribute by uncovering how values come into play over time in an IOIS practice in the public sector. In particular, our findings show that different values come into play in relation and as a reaction to different activities (Table 1). Thus, we contribute by showing that values are not one unified category of factors when taking time into consideration. This also adds to our understanding on how factors, such as no agreements on goals (Gil-Garcia et al., 2007; Zhang et al., 2005) and accommodating the diversity of participating organisations and their goals (Gil-García & Sayogo, 2016; Sayogo & Gil-García, 2014; Sayogo et al., 2016) affect IOIS. Goals are end states driven by values and should, therefore, not be viewed as a coherent factor. Instead, goals will most likely affect the outcome of IOIS in the public sector differently at different times.
While a few studies have treated IOIS in the public sector as a dynamic phenomenon, including the factors of conflicting rationalities, they did not go into details regarding the dynamics (Drake et al., 2004; Luna-Reyes et al., 2007; Yang, 2012; Yang & Wu, 2014; Zhang & Dawes, 2006). We contribute to these studies by showing that the outcome of value conflicts depends on how the driver of an activity decides to emphasise a set of values in a specific situation. Although many of the identified values are present throughout the lifespan of the case studied here, they gained importance at different times. Thus, value conflicts are emphasised differently at different times. This finding implies that the shaping of an IOIS practice in the public sector is not solely a function of conflicts of values that needs to be identified, it is, even more, a function of the extent and the exact time in the ongoing collaboration at which these divergent values are challenged. This leads us to our first theoretical proposition:
P1. If value conflicts in a public sector IOIS practice exist over time, they will be emphasised to different extents at different times.
By focusing on the dynamics of these conflicts, we have provided a deeper understanding of the topic of conflicting values in the course of IOIS in the public sector. Our analysis shows that the organisations started with a rather broad view on the set of possible IOIS activities. In the course of the collaboration, the gathering of novel experiences on IOIS in the advisory group is ongoing, and the local network actors begin to stress different values; thus, the set of potential IOIS activities is reduced. Thus, we add depth to the understanding of how the non-alignment of rationales cause organisational barriers to emerge (Zhang & Dawes, 2006). We also add a dynamic aspect to Pardo et al.’s (2008) proposition that the ‘willingness to accommodate diversity of participating organisations and their goals affects governance structures in cross-boundary information sharing initiatives’. Our case showed that, over time, the organisations became less willing to compromise their respective positions. Also, each of these activities is rational, given the values that drive them, although some of these activities are not beneficial for the IOIS practice. For example, MKG’s decision to publish the IPR reports is driven by the value of transparency, although in the long run, it meant that SKB changed their information policy, and these reports ceased to exist. This type of long-term development is not possible to uncover without taking a process view on IOIS. This leads us to our second and third theoretical propositions:
P2. If conflicting values are stressed in a public sector IOIS practice over time, the set of potential IOIS activities is reduced.
P3. If value conflicts in a public sector IOIS practice exist and IOIS activities are driven by an individual organisation’s values, individual value rational activities may co-exist with a dysfunctional long-term IOIS practice.
The present case study also confirmed earlier findings from Drake et al. (2004) that information is not neutral in an IOIS practice. The values that the key organisations in the advisory group hold, which are shown in Table 1, could be thought of as resembling sub-cultures and the co-existing rationalities as identified by Drake et al. (2004). Interpreting our results using these scholars’ nomenclature, the researchers from KTH adhered to values found in the scientific sub-culture; MKG emphasised values typical for a political subculture, and SKB emphasised values usually associated with the sub-culture of bureaucracy. However, we show that different values of a culture are emphasised at different times. We also confirmed earlier findings about how organisations in the public sector may have a greater or lesser liberal attitude towards IOIS (Yang, 2012; Yang & Wu, 2014). By applying a dynamic perspective, we illustrated that positions are not fixed but can change over time. Indeed, SKB moved from a more liberal to a more conservative position by emphasising confidentiality and control values. Hence, our analysis corroborates the notion that the cultural trait of cooperativeness within an organisation can lead to difficulties ‘in holding the principle of confidentiality in such an information sharing environment’ (Chang & Lin, 2007).
6.2Implications for practice
Our results can inform managers that an IOIS practice in the public sector is complex and consists of many interactions. The trajectory described presently, shows that sometimes these activities are reactions originating from previous activities. Hence, it is important for practitioners to consider carefully how they use shared information, the characteristics of the new activities they introduce into the collaboration, and why these activities are introduced. Otherwise, there is a risk of retaliatory behaviour. As discussed above, isolated activities might be rational from the point of view of the individual local network actor and from the set of values they adhere to. However, such activities can be dysfunctional for the IOIS practice because they might decrease the organisations’ attachment to the IOIS practice.
The risk described above highlights the importance of acknowledging that collaborating organisations can start IOIS while being driven by widely divergent values. Therefore, organisations in the public sector that enter into IOIS cannot take for granted that shared information is used according to their respective values; indeed, this was the case when MKG publicly shared the IPR reports from SKB. On the one hand, this shows that it is essential to have explicit understandings of the IOIS and that it could be worth considering a legally binding agreement as the basis for the efficient operation of IOIS. The present case study also showed that IOIS in the public sector is shaped over time. Therefore, it is important for organisations to plan ahead when entering IOIS and consider legally binding agreements robust enough to withstand changing circumstances. Of course, such agreements do not necessarily cover all eventualities. Still, negotiating legally binding agreements could increase the likelihood of addressing potential scenarios that can surface potential value conflicts. On the other hand, we do not claim that every instance of an IOIS warrants that degree of legality, or that advising organisations about non-disclosure agreements is new. It is part of modern contract law (e.g. Grossman, 2009).
Our analysis showed that it is important to consider not only that information is shared between organisations but also how it is shared. It means that organisations in the public sector that are about to enter into IOIS need to analyse the different roles or functions that they can have in a collaboration. Thus, organisations also need to know in advance the different tasks they are expected to contribute to. Information needs to be made available in such a way that the organisations can fulfil these tasks. In the present case, the difference of the values driving the expectations of the collaborating organisations was simply too large. For example, researchers from KTH expressed the view that information about research was made available in such a way that it was difficult for them to act as a scientific reviewer. Thus, managers of collaborating public sector organisations need to negotiate a framework that includes the principles of the IOIS practice and its procedures.
It is also important to design IOIS practices to include mechanisms for renegotiation of the framework under which information is shared. For example, in the present case, SKB neither entered the advisory group with the intention to share the IPR reports nor did they know the results of their decision to share them. Including a renegotiation mechanism in the IOIS practice would make it possible to identify dysfunctional activities and deal with the emphasised values conflicts. If such mechanisms exist, issues can be escalated to the organisations in the global network. That is, issues do not need to be dealt with by the actors working in the IOIS practice.
As has been shown, values are the fundamental driving force for activities. It is important that IOIS policies are in line with the values of their respective organisations. Otherwise, there is a risk that both managers and employees act in a way that is non-compliant with the policy. It also means that it is important in public sector organisations to communicate the organisation’s values and in which situations certain values are specifically important to stress because it will never be possible to develop IOIS policies that cover every aspect of an IOIS practice.
6.3Limitations and future research
An obvious limitation of this study is that it is based on one case study from a specific policy domain, nuclear waste management. Thus, it is reasonable to assume that actors anchor their activities in strongly held values in this domain because of what is at stake and the dramatic implications that decisions in this area could have. Nonetheless, our study has uncovered some novel findings on how value conflicts shape an IOIS practice in the public sector. More studies will reveal whether the present findings and, in particular, our theoretical propositions, have validity beyond this particular case. Therefore, one interesting avenue of future research is a thorough validation of the propositions using both qualitative and quantitative studies. In the present case, the collaborating organisations, from the onset, had widely different views of the mutual problems they had come together to solve. Thus, the case offered unique possibilities for the investigation of values in such a context of emerging conflicts. However, research on such settings is limited, making it difficult to compare and contrast similar cases. It means that a second interesting avenue of future research is whether certain types of value conflicts are associated with certain stages of an IOIS practice, something that would require comparison across cases. A third avenue for future research would be to explore whether and how the idea of a value-oriented trajectory has value in other IOIS domains where the stakes and the types of actors are different.
7.Conclusions
In this study, we aimed to explore how conflicting values shape an inter-organisational information sharing (IOIS) practice in the public sector over time, and we, therefore, posed the research question: How do conflicting values shape an inter-organisational information sharing practice in the public sector over time? Based on our case study, the answer is in three parts. First, we found that how organisations choose to emphasise different values changes during the IOIS practice, and it has profound effects on the degree of shared information and the participating organisations’ abilities to fulfil their individual roles. This change is not uniform, and we add to existing theory on IOIS in the public sector by our first theoretical proposition: If value conflicts in a public sector IOIS practice exist over time, they will be emphasised to different extents at different times. Thus, to understand how value conflicts impact the shaping of IOIS practices, there is a need to understand when and to what extent conflicting values are stressed. Second, we found that over time the collaborating organisation became less willing to compromise their respective positions with regard to IOIS. This led us to our second proposition: If conflicting values are stressed in a public sector IOIS practice over time, the set of potential IOIS activities is reduced. Third, we found that when an organisation realises that its information is not shared and/or used according to the organisation’s values, it will most likely change its activities to attempt a change of the existing IOIS practice – even if such a change could mean compromising the IOIS practice. Here, we add to existing theory on IOIS in the public sector by our third theoretical proposition: If value conflicts in a public sector IOIS practice exist and IOIS activities are driven by an individual organisation’s values, individual value rational activities may co-exist with a dysfunctional long-term IOIS practice.
Acknowledgments
This research has been funded by the Swedish Civil Contingencies Agency.
Supplementary data
The supplementary files are available to download from http://dx.doi.org/10.3233/IP-200234.
References
[1] | Agle, B.R., & Caldwell, C.B. ((1999) ). Understanding research on values in business: a level of analysis framework. Business & Society, 38: (3), 326-387. |
[2] | Aguilar-Savén, R.S. ((2004) ). Business process modelling: review and framework. International Journal of Production Economics, 90: (2), 129-149. |
[3] | Akbulut, A.Y., Kelle, P., Pawlowski, S.D., Schneider, H., & Looney, C.A. ((2009) ). To share or not to share? Examining the factors influencing local agency electronic information sharing. International Journal of Business Information Systems, 4: (2), 143-172. |
[4] | Allen, D.K., Karanasios, S., & Norman, A. ((2014) ). Information sharing and interoperability: the case of major incident management. European Journal of Information Systems, 23: (4), 418-432. |
[5] | Araujo, L., & Harrison, D. ((2002) ). Path dependence, agency and technological evolution. Technology Analysis & Strategic Management, 14: (1), 5-20. |
[6] | Atabakhsh, H., Larson, C., Petersen, T., Violette, C., & Chen, H. ((2004) ). Information sharing and collaboration policies within government agencies. In Chen, H., Moore, R., Zeng, D.D., & Leavitt, v., (Eds.), Lecture notes in computer science: Intelligence and Security Informatics, Second Symposium on Intelligence and Security Informatics, ISI 2004, Berlin: Springer, Vol. 3073, pp. 467-475. |
[7] | Bellamy, C., Raab, C., Warren, A., & Heeney, C. ((2008) ). Information-sharing and confidentiality in social policy: regulating multi-agency working. Public Administration, 86: (3), 737-759. |
[8] | Bigdeli, A.Z., Kamal, M.M., & de Cesare, S. (2011, 9–11 June, 2011). Inter-Organisational Electronic Information Sharing in Local G2G Settings: A Socio-Technical Issue. Paper presented at the 19th European Conference on Information Systems (ECIS 2011), Helsinki, Finland. |
[9] | Bigdeli, A.Z., Kamal, M.M., & de Cesare, S. ((2013) a). Electronic information sharing in local government authorities: factors influencing the decision-making process. International Journal of Information Management, 33: (5), 816-830. |
[10] | Bigdeli, A.Z., Kamal, M.M., & de Cesare, S. ((2013) b). Information sharing through inter-organisational systems in local government. 7: (2), 148-176. Retrieved from http://www.emeraldinsight.com/journals.htm?issn=1750-6166&volume=7&issue=2&articleid=17088400&show=abstract. |
[11] | Brazelton, J., & Gorry, A.G. ((2003) ). Creating a knowledge-sharing community: if you build it, will they come? Communication of the ACM, 46: (2), 23-25. |
[12] | Caffrey, L. ((1998) ). Information Sharing Between & Within Governments. London: Commonwealth Secretariat. |
[13] | Chang, S.E., & Lin, C.-S. ((2007) ). Exploring organizational culture for information security management. Industrial Management & Data Systems, 107: (3), 438-458. |
[14] | Dahlan, A.R.A., Dahan, H.M., & Saman, Y.M. ((2013) ). The Government Information Sharing (GIS) in Natural Disaster Management and Risk Reduction. Paper presented at the 5th International Conference on Information and Communication Technology for the Muslim World (ICT4M) Rabat. |
[15] | Dawes, S.S. ((1996) ). Interagency information sharing: expected benefits, manageable risks. Journal of Policy Analysis and Management, 15: (3), 377-394. |
[16] | Dawes, S.S., Cresswell, A.M., & Pardo, T.A. ((2009) ). From “need to know” to “need to share”: tangled problems, information boundaries, and the building of public sector knowledge networks. Public Administration Review, 69: (3), 392-402. |
[17] | Dawes, S.S., Gharawi, M.A., & Burke, B. ((2011) ). Knowledge and Information Sharing in Transnational Knowledge Networks: A Contextual Perspective. Paper presented at the The 44th Hawaii International Conference on System Sciences (HICSS 2011), Kauai, HI, USA. doi: 10.1109/HICSS.2011.268. |
[18] | Dawes, S.S., Gharawi, M.A., & Burke, B. ((2012) ). Transnational public sector knowledge networks: Knowledge and information sharing in a multi-dimensional context. 29: (1). Retrieved from |
[19] | Dawes, S.S., & Pardo, T.A. ((2002) ). Building collaborative digital government systems – Systemic constraints and effective practices. In McIver, W.J., Jr & Elmagarmid, A.K., (Eds.), Advances in Digital Government – Technology, Human Factors, and Policy, Boston: Kluwer Academic Publishers, pp. 259-273. |
[20] | Drake, D.B., Steckler, N.A., & Koch, M.J. ((2004) ). Information sharing in and across government agencies: the role and influence of scientist, politician, and bureaucrat subcultures. Social Science Computer Review, 22: (1), 67-84. |
[21] | Eom, S.-J., & Kim, J.H. ((2017) ). Information Sharing Success in Korean Metropolitan Governments: Combining Multi-level Factors with Fuzzy-set Analysis. In Hinnant, C.C., & Ojo, A., (Eds.), dg.o ’17: Proceedings of the 18th Annual International Conference on Digital Government Research, New York, NY, United States: Association for Computing Machinery, pp. 279-288. |
[22] | Fan, J., & Zhang, P. ((2009) ). A field study of G2G information sharing in Chinese context based on the layered behavioral model. Paper Presented at the The 42nd Hawaii International Conference on System Sciences (HICSS 2009), Waikoloa, HI; United States. |
[23] | Fan, J., Zhang, P., & Yen, D.C. ((2014) ). G2G information sharing among government agencies. Information & Management, 51: (1), 120-128. |
[24] | Fedorowicz, J., Gogam, J.L., & Williams, C.B. ((2007) ). A collaborative network for first responders: lessons from the CapWIN case. Government Information Quarterly, 24: (4), 785-807. |
[25] | Gasson, S. ((2006) ). A genealogical study of boundary-spanning IS design. European Journal of Information Systems, 15: (1), 26-41. |
[26] | Gharawi, M., & Dawes, S.S. ((2010) ). Conceptualizing Knowledge and Information Sharing in Transnational Knowledge Networks. Paper Presented at the the 4th International Conference on Theory and Practice of Electronic Governance (ICEGOV 2010), Beijing, China. |
[27] | Gil-Garcia, J.R., Chengalur-Smith, I., & Duchessi, P. ((2007) ). Collaborative e-Government: impediments and benefits of information-sharing projects in the public sector. European Journal of Information Systems, 16: (2), 121-133. |
[28] | Gil-Garcia, J.R., Chun, S.A., & Janssen, M. ((2009) ). Government information sharing and integration: combining the social and the technical. Information Polity, 14: (1/2), 1-10. |
[29] | Gil-Garcia, J.R., Guler, A., Pardo, T.A., & Burke, G.B. ((2019) ). Characterizing the importance of clarity of roles and responsibilities in government inter-organizational collaboration and information sharing initiatives. Government Information Quarterly, 36: (4), Article number 101393. Retrieved from http://offcampus.lib.washington.edu/login?url=http://search.ebscohost.com/login.aspx?direct=true&db=lxh&AN=139768105&site=ehost-live&scope=cite. |
[30] | Gil-García, J.R., Guler, A., Pardo, T.A., & Burke, G.B. ((2010) ). Trust in Government Cross-Boundary Information Sharing Initiatives: Identifying the Determinants. Paper Presented at the The 43rd Hawaii International Conference on System Sciences (HICSS 2010), Honolulu, HI, USA. |
[31] | Gil-Garcia, J.R., & Helbig, N. ((2006) ). Exploring e-government benefits and success factors. In Anttiroiko, A.-V., & Malkia, M., (Eds.), Encyclopedia of Digital Government, Hershey, PA: Idea Group Inc, pp. 803-811. |
[32] | Gil-García, J.R., & Sayogo, D.S. ((2016) ). Government inter-organizational information sharing initiatives: understanding the main determinants of success. Government Information Quarterly, 33: (3), 572-582. Retrieved from |
[33] | Gil-García, J.R., Schneider, C.A., Pardo, T.A., & Cresswell, A.M. (2005, 3–6 January, 2005). Interorganizational information integration in the criminal justice enterprise: Preliminary lessons from state and county initiatives. Paper Presented at the 38th Annual Hawaii International Conference on System Sciences (HICSS 2005), Big Island, Hawaii. |
[34] | Graham, F.S., Gooden, S.T., & Martin, K.J. ((2016) ). Navigating the transparency – privacy paradox in public sector data sharing. American Review of Public Administration, 46: (5), 569-591. |
[35] | Grossman, M. ((2009) ). Technology Law: What Every Business (and Business-minded Person) Needs to Know. Lanham, MD, USA: Scarecrow Press. |
[36] | Hedström, K., Kolkowska, E., Karlsson, F., & Allen, J.P. ((2011) ). Value conflicts for information security management. Journal of Strategic Information Systems, 20: (4), 373-384. |
[37] | Heeks, R., & Stanforth, C. ((2007) ). Understanding e-Government project trajectories from an actor-network perspective. European Journal of Information Systems, 16: (2), 165-177. |
[38] | Håkansson, H., & Waluszewski, A. ((2002) ). Path dependence: restricting or facilitating technical development? Journal of Business Research, 55: (7), 561-570. |
[39] | Karlsson, F., Frostenson, M., Prenkert, F., Kolkowska, E., & Helin, S. ((2017) ). Inter-organisational information sharing in the public sector: a longitudinal case study on the reshaping of success factors. Government Information Quarterly, 34: (4), 567-577. |
[40] | Lam, W. ((2005) ). Barriers to e-government integration. Journal of Enterprise Information Management, 18: (5), 511-530. |
[41] | Landsbergen, D.J., & Wolken, G.J. ((2001) ). Realizing the promise: government information systems and the fourth generation of information technology. Public Administration Review, 61: (2), 206-220. |
[42] | Latour, B. ((1987) ). Science in action: how to follow scientists and engineers through society. Cambridge, MA: Harvard University Press. |
[43] | Law, J., & Callon, M. ((1994) ). The life and death of an aircraft: a network analysis of technical change. In Bijker, W.E., & Law, J., (Eds.), Shaping technology/building society. Studies in sociotechnical change. Cambridge, Mass: MIT Press. |
[44] | Lee, J., & Rao, H.R. ((2007) ). Exploring the causes and effects of inter-agency information sharing systems adoption in the anti/counter-terrorism and disaster management domains. Paper Presented at the The 8th Annual International Digital Government Research Conference ( DG.O 2007). |
[45] | Lips, A.M.B., O’Neill, R.R., & Eppel, E.A. ((2011) ). Cross-agency collaboration in New Zealand: an empirical study of information sharing practices, enablers and barriers in managing for shared social outcomes. International Journal of Public Administration, 34: (4), 255-266. |
[46] | Luna-Reyes, L.F., Gil-Garcia, J.R., & Cruz, C.B. ((2007) ). Collaborative digital government in Mexico: some lessons from federal web-based interorganizational information integration initiatives. Government Information Quarterly, 24: (4), 808-826. |
[47] | Maras, M.-H. ((2017) ). Overcoming the intelligence-sharing paradox: Improving information sharing through change in organizational culture. Comparative Strategy, 36: (3), 187-197. |
[48] | Navarrete, C., Gil-García, J.R., Mellouli, S., Pardo, T.A., & Scholl, H.J. ((2010) ). Multinational E-Government Collaboration, Information Sharing, and Interoperability: An Integrative Model. Paper Presented at the The 43rd Hawaii International Conference on System Sciences (HICSS 2010), Honolulu, HI, USA |
[49] | Papadopoulos, T., & Merali, Y. ((2008) ). Stakeholder network dynamics and emergent trajectories of lean implementation projects: a study in the UK national health service. Public Money and Management, 28: (1), 41-48. |
[50] | Pardo, T.A., Burke, B., Gil-García, R., & Guler, A. ((2009) ). Clarity of Roles and Responsibilities in Government Cross-Boundary Information Sharing Initiatives: Identifying the Determinants. Paper Presented at the 5th International Conference on e-Government, Boston, USA. |
[51] | Pardo, T.A., Cresswell, A.M., Dawes, S.S., & Burke, G.B. (2004, 5–8 January, 2004). Modeling the social & technical processes of interorganizational information integration. Paper Presented at the 37th Hawaii International Conference on System Sciences (HICSS 2004), Hawaii. |
[52] | Pardo, T.A., Gil-García, J.R., & Burke, G.B. (2008, 7–10 Janaury, 2008). Governance Structures in Cross-Boundary Information Sharing: Lessons from State and Local Criminal Justice Initiatives. Paper Presented at the 41st Hawaii International Conference on System Sciences (HICSS 2008), Waikoloa, Big Island, Hawaii. |
[53] | Pardo, T.A., Sayogo, D.S., & Canestraro, D.S. ((2011) ). Computing and Information Technology Challenges for 21st Century Financial Market Regulators. In M, J., J, S.H., A, W.M., & Y, T., (Eds.), Electronic Government. EGOV 2011, Berlin, Heidelberg: Springer, Vol. Lecture Notes in Computer Science, Vol. 6846, pp. 198-209. |
[54] | Pardo, T.A., & Tayi, G.K. ((2007) ). Interorganizational information integration: a key enabler for digital government. Government Information Quarterly, 24: (4), 691-715. |
[55] | Patton, M.Q. ((1990) ). Qualitative evaluation and research methods (2nd ed. ed.). Newbury Park, CA: Sage. |
[56] | Perry, J.L., & Rainey, H.G. ((1988) ). The public-private distinction in organization theory: a critique and research strategy. Academy of Management Executive, 13: (2), 182-201. |
[57] | Praditya, D., & Janssen, M. ((2016) ). Factors influencing the creation of information sharing arrangements between private and public organizations. In Dečman, M., & Jukić, T., (Eds.), Proceedings of the European Conference on e-Government, ECEG, Academic Conferences and Publishing International Limited Reading, pp. 154-161. |
[58] | Sayogo, D.S., & Gil-Garcia, J.R. (2015, 5–8 January, 2015). Analyzing the Influence of Governance Structure Determinants on the Success of Inter-Organizational Information Sharing Initiatives. Paper Presented at the 2015 48th Hawaii International Conference on System Sciences, Kauai, Hawaii. |
[59] | Sayogo, D.S., & Gil-García, J.R. (2014, June 18–21, 2014). Understanding the Determinants of Success in Inter-Organizational Information Sharing Initiatives: Results from a National Survey. Paper Presented at the 15th Annual International Conference on Digital Government Research, Aguascalientes City, Mexico. |
[60] | Sayogo, D.S., Gil-García, J.R., & Cronemberger, F. ((2016) ). Determinants of Clarity of Roles and Responsibilities in Interagency Information Integration and Sharing (IIS). In Scholl, H.J., Glassey, O., Janssen, M., Klievink, B., Lindgren, I., Parycek, P., Tambouris, E., Wimmer, M.A., Janowski, T., & Sá Soares, D., (Eds.), Electronic Government – 15 IFIP WG 8.5 International Conference, EGOV 2016, Berlin, Heidelberg: Springer, Vol. Lecture Notes in Computer Science, Vol. 9820, pp. 126-134. |
[61] | Sayogo, D.S., Gil-García, J.R., Cronemberger, F.A., & Widagdo, B. ((2017) ). The Mediating Role of Trust for Inter-Organizational Information Sharing (IIS) Success in the Public Sector. In Hinnant, C.C., & Ojo, A., (Eds.), dg.o ’17: Proceedings of the 18th Annual International Conference on Digital Government Research, New York, NY, United States: Association for Computing Machinery, pp. 426-435. |
[62] | Scholl, H.J., Kubicek, H., Cimander, R., & Klischewski, R. ((2012) ). Process integration, information sharing, and system interoperation in government: a comparative case analysis. Government Information Quarterly, 29: (3), 313-323. |
[63] | Schooley, B.L., & Horan, T.A. ((2007) ). Towards end-to-end government performance management: case study of interorganizational information integration in emergency medical services (EMS). Government Information Quarterly, 24: (4), 755-784. |
[64] | Urciuoli, L., Hintsa, J., & Ahokas, J. ((2013) ). Drivers and barriers affecting usage of e-Customs – a global survey with customs administrations using multivariate analysis techniques. Government Information Quarterly, 30: (4), 473-485. |
[65] | Van Cauter, L., Snoeck, M., & Crompvoets, J. ((2015) ). Removing the Blinkers: What a Process View Learns About G2G Information Systems in Flanders. In Tambouris, E., Janssen, M., Scholl, H.J., Wimmer, M.A., Tarabanis, K., Gascó, M., Klievink, B., Lindgren, I., & Parycek, P., (Eds.), Electronic Government – 14th IFIP WG 8.5 International Conference, EGOV 2015, Heidelberg: Springer, Vol. Lecture Notes in Computer Science, Vol. 9248, pp. 209-221. |
[66] | Walsham, G. ((1995) ). Interpretive case studies in IS research: nature and method. European Journal of Information Systems, 4: , 74-81. |
[67] | Wastell, D., Kawalek, P., Langmead-Jones, P., & Ormerod, R. ((2004) ). Information systems and partnership in multi-agency networks: an action research project in crime reduction. Information and Organization, 14: (3), 189-210. Retrieved from http://www.sciencedirect.com/science/article/B6W7M-4C47BCF-1/2/c102b806623cc457938e12c5eaff3062. |
[68] | Webster, J., & Watson, R.T. ((2002) ). Analyzing the past to prepare for the future: writing a literature review. MIS Quarterly, 26: (2), 13-22. |
[69] | Yang, T.-M. ((2012) ). The Complexity of Cross-Boundary Information Sharing: An Organizational Perspective on Taiwan E-Government. Paper Presented at the The 6th International Conference on Theory and Practice of Electronic Governance (ICEGOV’12), Albany, New York. |
[70] | Yang, T.-M., Lo, J., & Shiang, J. ((2015) ). To open or not to open? Determinants of open government data. Journal of Information Science, 41: (5), 596-612. Retrieved from |
[71] | Yang, T.-M., & Maxwell, T.A. ((2011) ). Information-sharing in public organizations: a literature review of interpersonal, intra-organizational and inter-organizational success factors. Government Information Quarterly, 28: (2), 164-175. |
[72] | Yang, T.-M., & Wu, Y.-J. ((2014) ). Exploring the determinants of crossboundary information sharing in the public sector: an e-Government case study in Taiwan. Journal of Information Science, 40: (5), 649-668. |
[73] | Zhang, J., Cresswell, A., & Thompson, F. ((2002) ). Participants expectations and the success of knowledge networking in the public sector. Paper Presented at the Americas Conference on Information Systems 2002. |
[74] | Zhang, J., & Dawes, S.S. ((2006) ). Expectations and perceptions of benefits, barriers, and success in public sector knowledge networks. Public Performance & Management Review, 29: (4), 433-466. |
[75] | Zhang, J., Dawes, S.S., & Sarkis, J. ((2005) ). Exploring stakeholders’ expectations of the benefits and barriers of e-government knowledge sharing. Journal of Enterprise Information Management, 18: (5), 548-567. |
[76] | Zhang, J., Faerman, S.R., & Cresswell, A.M. (2006, 4–7 Jan. 2006). The Effect of Organizational/Technological Factors and the Nature of Knowledge on Knowledge Sharing. Paper Presented at the The 39th Hawaii International Conference on System Sciences (HICSS 2006), Kauia, HI, USA, USA. |
[77] | Zheng, L., Jiang, Y., Yang, T.-M., & Pardo, T.A. (2008, December 1–4, 2008). Sharing information for product quality and food safety in China: Barriers and enablers. Paper Presented at the The 2nd International Conference on Theory and Practice of Electronic Governance, ICEGOV 2008, Cairo, Egypt. |
[78] | Ågerfalk, P.J., & Goldkuhl, G. ((2001) ). Business action and information modelling: the task of the new millennium. In Rossi, M., & Siau, K., (Eds.), Information Modeling in the New Millennium, Hershey, PA: Idea Group Publishing, pp. 110-136. |




