Abstract
This paper describes the design and verification of a copy elimination and memory deallocation scheme for a compiler that translates the verification-friendly programming language Whiley into efficient C code. We use a combination of static analysis and runtime flags to replace array copies with reference assignments when possible. Formal proofs have been carried out, both manually and with the automatic theorem prover Boogie, to show that the generated code satisfies a crucial invariant, which is needed to show the absence of invalid memory access errors and memory leaks. Our benchmark results show that the compiler effectively reduces the time complexity of LZ77 decompression from \(O(n^2)\) to the theoretically lowest possible level \(O(n\log n)\) while avoiding all memory leaks.

Similar content being viewed by others
Data availability statements
1. The datasets generated during and/or analysed during the current study are available in the [Github] repository, [https://github.com/samminweng/WhileyOpenCL]. 2. The datasets generated during and/or analysed during the current study are available from the corresponding author on reasonable request. 3. All data generated or analysed during this study are included in this published article [and its supplementary information files].
References
Aho AV, Sethi R, Ullman JD (1986) Compilers: principles, techniques, and tools, chap 8. Addison-Wesley Longman Publishing Co. Inc, Boston, pp 529–531
Blandy J (2015) Why rust? Trustworthy, concurrent systems programming. O’Reilly, Sebastopol
Gopinath K, Hennessy JL (1989) Copy elimination in functional languages. In: Proceedings of the 16th ACM SIGPLAN-SIGACT symposium on principles of programming languages. ACM, New York, NY, USA, POPL ’89, pp 303–314, https://doi.org/10.1145/75277.75304
Goyal D, Paige R (1998) A new solution to the hidden copy problem. In: Levi G (ed) Static analysis. Springer, Berlin, pp 327–348
Graham SL, Kessler PB, McKusick MK (2004) Gprof: A call graph execution profiler. SIGPLAN Not 39(4):49–57. https://doi.org/10.1145/989393.989401
Hoare T (2003) The verifying compiler: a grand challenge for computing research. In: Böszörményi L, Schojer P (eds) Modular programming languages. Springer, Berlin, pp 25–35
Hudak P, Bloss A (1985) The aggregate update problem in functional programming systems. In: Proceedings of the 12th ACM SIGACT-SIGPLAN symposium on principles of programming languages. ACM, New York, NY, USA, POPL ’85, pp 300–314, https://doi.org/10.1145/318593.318660
Huth M, Ryan M (2004) Logic in computer science: modelling and reasoning about systems. Cambridge University Press, New York
ISO, IEC 9899:2011 (2011) Information technology-programming languages-C. Standard, International Organization for Standardization, Geneva, Switzerland
Lameed N, Hendren L (2011) Staged static techniques to efficiently implement array copy semantics in a MATLAB JIT compiler. In: Knoop J (ed) Compiler construction. Springer, Berlin, pp 22–41
Leino R (2008) This is Boogie 2. Microsoft Research. https://www.microsoft.com/en-us/research/publication/this-is-boogie-2-2/
Nethercote N, Seward J (2007) Valgrind: a framework for heavyweight dynamic binary instrumentation. In: ACM Sigplan notices. ACM, vol 42, pp 89–100
Odersky M (1991) How to make destructive updates less destructive. In: Proceedings of the 18th ACM SIGPLAN-SIGACT symposium on principles of programming languages. ACM, New York, NY, USA, POPL ’91, pp 25–36, https://doi.org/10.1145/99583.99590
Pearce D (2021) A lightweight formalism for reference lifetimes and borrowing in Rust. ACM Trans Program Lang Syst. https://doi.org/10.1145/3443420
Pearce DJ, Groves L (2015) Designing a verifying compiler: lessons learned from developing Whiley. Sci Comput Program 113:191–220. https://doi.org/10.1016/j.scico.2015.09.006
Protzenko J, Zinzindohoué JK, Rastogi A, Ramananandro T, Wang P, Zanella-Béguelin S, Delignat-Lavaud A, Hriţcu C, Bhargavan K, Fournet C, Swamy N (2017) Verified low-level programming embedded in F*. Proc ACM Program Lang 1(ICFP):17:1–17:29. https://doi.org/10.1145/3110261
Sastry AVS, Clinger W, Ariola Z (1993) Order-of-evaluation analysis for destructive updates in strict functional languages with flat aggregates. In: Proceedings of the conference on functional programming languages and computer architecture. ACM, New York, NY, USA, FPCA ’93, pp 266–275, https://doi.org/10.1145/165180.165222
Seidl H, Wilhelm R, Hack S (2012) Compiler design: analysis and transformation. Springer, Berlin
Shahriyar R, Blackburn SM, Frampton D (2012) Down for the count? Getting reference counting back in the ring. ACM SIGPLAN Not 47(11):73–83. https://doi.org/10.1145/2426642.2259008
Shahriyar R, Blackburn SM, Yang X, McKinley KS (2013) Taking off the gloves with reference counting immix. In: Conference on object-oriented programming systems, languages, and applications, OOPSLA, pp 93–110, https://doi.org/10.1145/2509136.2509527
Shankar N (2001) Static analysis for safe destructive updates in a functional language. In: Selected papers from the 11th international workshop on logic based program synthesis and transformation. Springer, London, UK, LOPSTR ’01, pp 1–24
Swamy N, Hriţcu C, Keller C, Rastogi A, Delignat-Lavaud A, Forest S, Bhargavan K, Fournet C, Strub PY, Kohlweiss M, Zinzindohoue JK, Zanella-Béguelin S (2016) Dependent types and multi-monadic effects in F*. ACM SIGPLAN Not 51(1):256–270. https://doi.org/10.1145/2914770.2837655
Wand M, Clinger WD (2001) Set constraints for destructive array update optimization. J Funct Program 11(3):319–346. https://doi.org/10.1017/S0956796801003938
Weng MH (2019) Efficient compilation of a verification-friendly programming language. PhD thesis, University of Waikato, Hamilton, New Zealand
Weng MH, Utting M, Pfahringer B (2016) Bound analysis for Whiley programs. Electron Notes Theor Comput Sci 320:53–67. https://doi.org/10.1016/j.entcs.2016.01.005
Weng MH, Pfahringer B, Utting M (2017) Static techniques for reducing memory usage in the C implementation of Whiley programs. In: ACSW’17, ACM
Ziv J, Lempel A (1977) A universal algorithm for sequential data compression. IEEE Trans Inf Theory 23(3):337–343. https://doi.org/10.1109/TIT.1977.1055714
Acknowledgements
We would like to thank Dr. David J. Pearce and the Whiley team for their support, and Oracle Labs, Australia for travel funding. This work also greatly benefits from the useful feedback of the members of the Sydney Area Programming Languages INterest Group (SAPLING).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
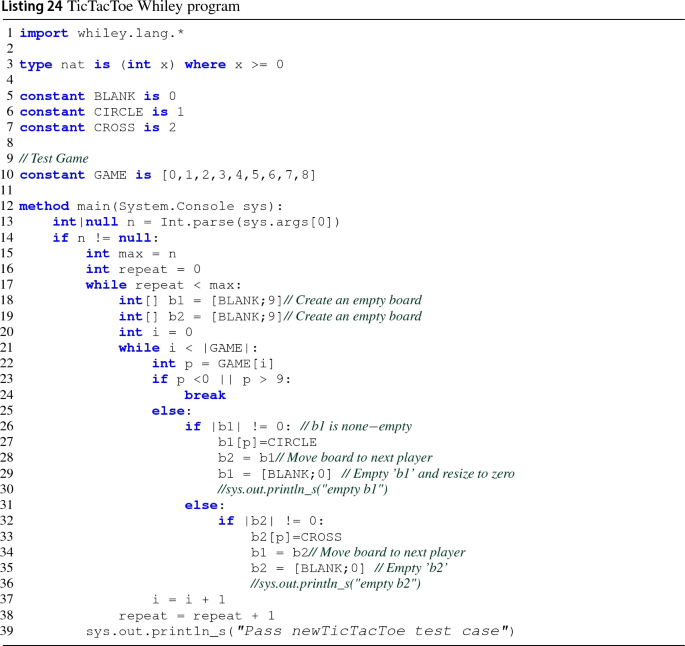
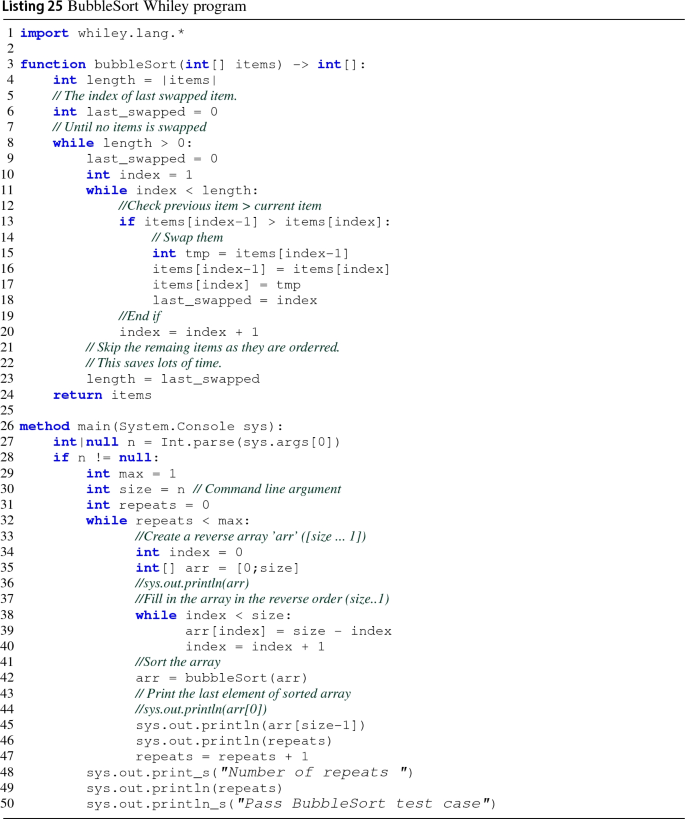
Source programs
Source programs
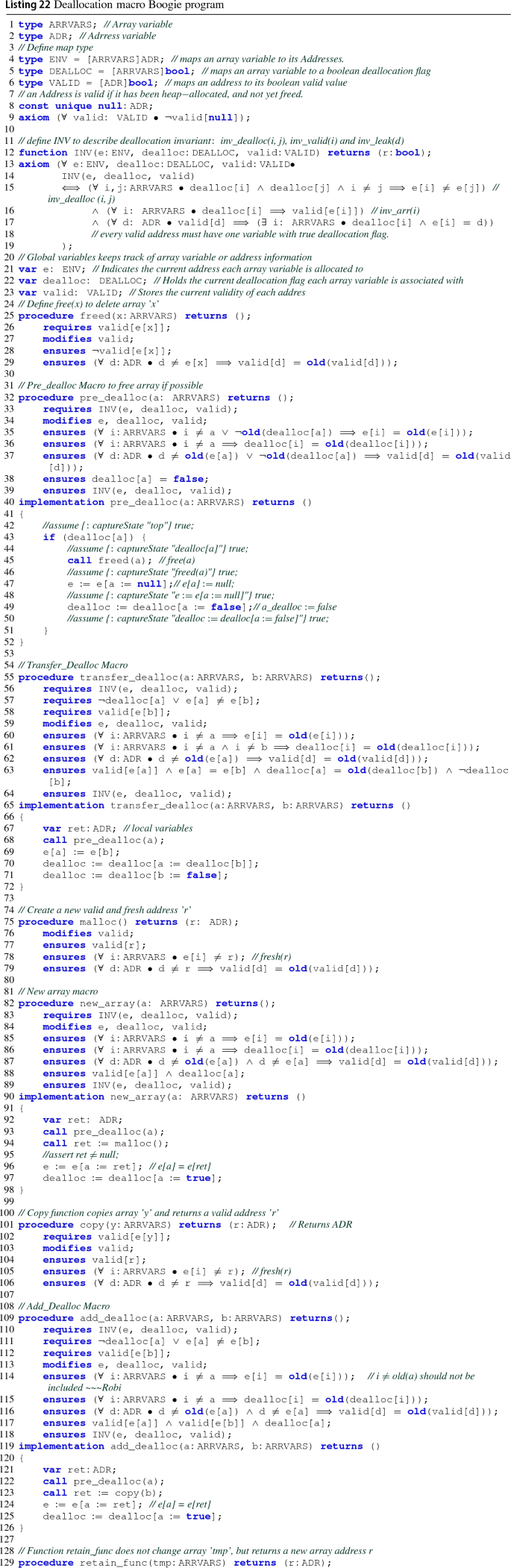
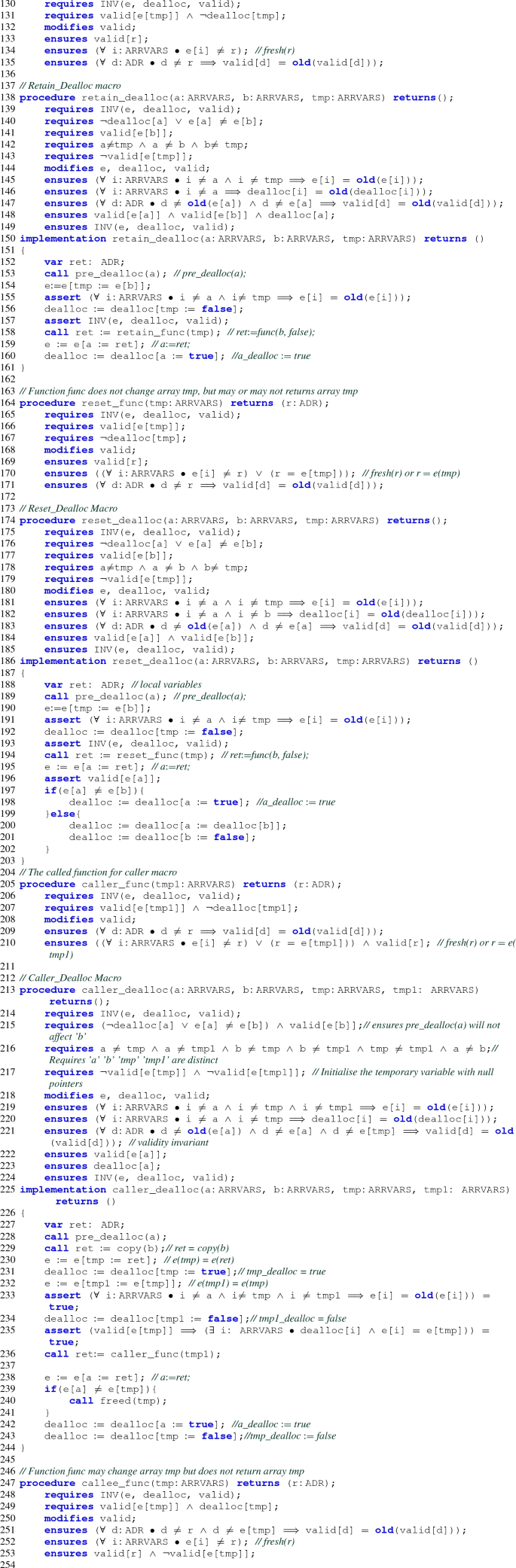
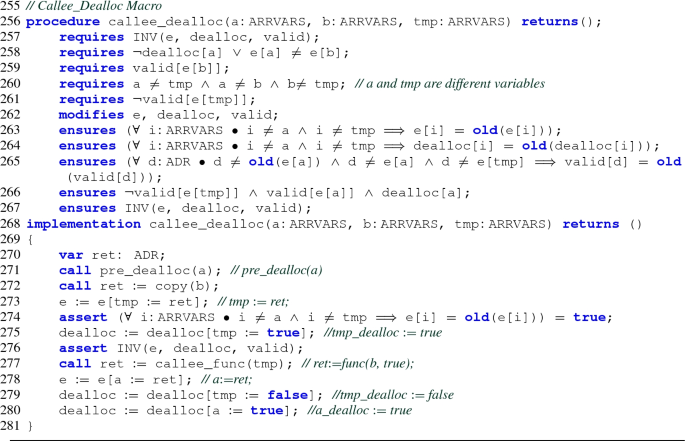
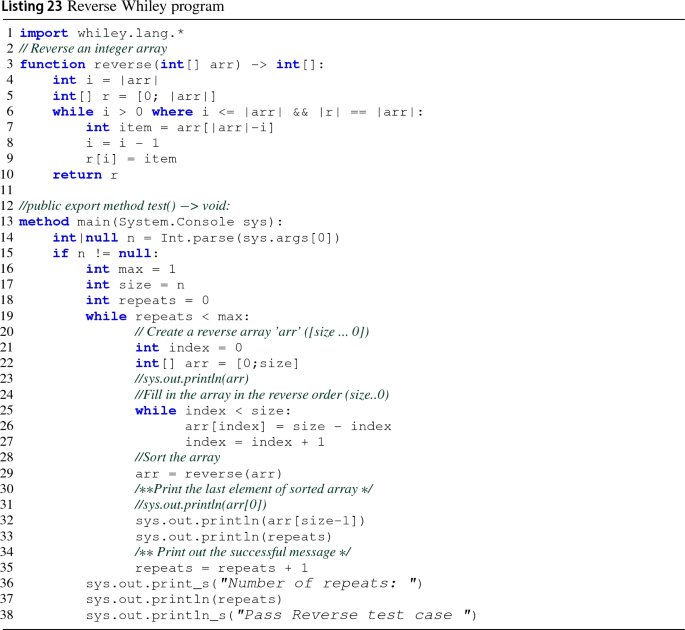
Rights and permissions
About this article
Cite this article
Weng, MH., Malik, R. & Utting, M. Automatic proofs of memory deallocation for a Whiley-to-C Compiler. Form Methods Syst Des 57, 429–472 (2021). https://doi.org/10.1007/s10703-021-00378-0
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10703-021-00378-0


