Abstract
Electronic health records (EHRs) are important for the efficient management of healthcare data. However, Healthcare data travels across an open route, i.e., the Internet, making EHR security a difficult process to do. This puts healthcare data vulnerable to cyber assaults. A possible method for protecting EHRs is blockchain technology. In this work, we develop an EHR architecture based on blockchain, which ensures all stakeholder's safety and privacy. We analyze various security architectures used for EHRs and the standard encryption system is integrated with quantum computing (QC). To safeguard the conventional traditional encrypting system against quantum assaults, we provide a hybrid signature technique that combines the Elliptic Curve Digital Signature Algorithm (ECDSA) and Dilithium within the anti-quantum lattice-based blind signature. Based on the difficulty of lattice problems over finite fields, Dilithium is a lattice-based signature method that is substantially safe against selected message assaults. The developed technique creates high entropy secret keys using the lattice basis delegation mechanism. The combination of ECDSA and Dilithium provides an efficient and secure signature system that is resilient to quantum attacks. The proposed scheme ensures that only authorized users with a defined role can use the database to access the data. We evaluate the efficiency of our scheme by comparing its performance to other state-of-the-art solutions in terms of transaction throughput, resource utilization, and communication cost. Results demonstrate that the developed technique outperforms the existing techniques in terms of efficiency and security.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
Introduction
Electronic health records (EHR) are digital versions of patients' medical and treatment histories. EHR systems can completely change the medical care industry from one that predominantly uses paper to one that employs clinical data together with other types of information to support clinicians in providing superior treatment for their patients [1, 2]. An EHR is defined as "a longitudinal document of health data for patients created by one or more interactions in any healthcare service context" previous medical history, issues, prescriptions, Patient progress notes, demographics, vaccines, laboratory results, radiological reports, and vital signs are all contained in this material. Some of the most important benefits of EHRs are quick access to electronically stored records and the elimination of the horrible handwriting that has traditionally plagued the medical chart. When examining the benefits of EHRs, studies have taken a look at social, clinical, and organizational outcomes. Several clinical outcomes related to patient safety and treatment quality have been the focus of EHR investigations [3,4,5]. The appropriate administration and secure recovery of the enormous amounts of health-related information produced by standard business procedures and service providers represent a significant problem for the healthcare industry.
Another major concern for the healthcare sector is the protection of patient data. At a central location within an existing legacy Technology network that is a top target for ransomware and other cyber-attacks, many healthcare institutions keep important patient data [6, 7]. The healthcare industry is looking for possibilities provided by different technologies to tackle some of these major problems. The use of blockchain technology might greatly enhance healthcare's interoperability issues and help put Patients at the heart of the environment. Blockchain technology is a groundbreaking invention of the twenty-first century. In addition to improving security, privacy, and interoperability, it also offers regulatory and operational verification efficiencies and has a chance to make patients the focus of the ecosystem. In summary, blockchain may be utilized for remote monitoring, mobile applications, and patient ownership of their medical records, as well as for accessing and sharing patient medical records [8,9,10].
Blockchain is a system that keeps inter-entity interactions safe and "trustless" while reducing reliance on a single centralized authority and its architecture is shown in Fig. 1. Game theory and cryptography work together to facilitate consensus, immutability, and decentralization. This technology provides the building blocks for various application categories, including crypto and Decentralized Applications (DApps). The majority of blockchain's capabilities are derived from cryptographic primitives [11, 12]. The users in a blockchain platform are represented as nodes, and each node proposes and creates transactions using public key infrastructure (PKI). Both private and public keys are held by each participant in the system. The user is authenticated using a private key, and their public key serves as their public address. A transaction must be formed before the public keys of the user who started it, the person who will receive it, and the user who will send it may be used. The users utilize a private key and cryptographically sign each of them before being combined and broadcast to every other node in the blockchain network. The user was reported to have suggested a transaction after this was done [13, 14].
We look at several EHR security designs and use quantum computing (QC) to improve the existing encryption method. Quantum computing is one of the cutting-edge computer methods that is based on the amazing phenomena of quantum physics. The combination of computer science, mathematics, physics, and information theory is astounding. It alters the behavior of small physical elements like atoms, electrons, and photons to surpass traditional computers in terms of processing power, exponential speed, and energy consumption. Although QC is based on quantum mechanics, these concepts of superposition, interference, and entanglement are frequently used to explain it [15,16,17]. There has been an increase in interest in quantum computing among academics seeking to advance the capabilities of computers. Several computationally demanding aspects of healthcare are particularly well adapted to the current highly linked IoT digital health paradigm, which incorporates integrated medical equipment (such as health monitors) that could be associated with the Internet or the cloud. Not only has the healthcare IoT benefited from the tremendous growth in computational power, but quantum computers may also be able to make fundamental advancements in this field.
Research challenge
Addressing the research challenge of enhancing quantum-resistant security in healthcare blockchain networks necessitates a comprehensive approach. An important aspect is the development and application of strong signature schemes that can withstand quantum attacks. These schemes need to be able to handle the potential risks from quantum computers and easily fit into current healthcare blockchain systems. In addition, there is also the challenge of coming up with effective and adaptable strategies for managing cryptographic keys in a post-quantum world, so that they can be generated, distributed, and stored securely. Developing this task necessitates an in-depth understanding of both quantum-resistant cryptography and the complexities of healthcare data management.
Another aspect of the challenge involves addressing scalability and optimizing performance. As healthcare blockchain networks continue to expand and become more intricate, the security measures designed to withstand quantum attacks must be efficient in terms of transaction throughput and computational resources. The research challenge becomes even more complex due to the need to work with older systems and comply with regulatory requirements. Researchers need to carefully manage the incorporation of security measures that can withstand quantum attacks into current healthcare systems, guaranteeing a smooth and protected transition. The potential success of this research challenge offers the opportunity to create a robust and effective security framework that can protect Electronic Health Records from emerging quantum threats.
Case scenario
Consider a healthcare system of the future, where EHRs are at the cutting edge, ensuring effortless, secure, and confidential access to patient information. A patient named Sarah is admitted to a hospital, and her medical history, diagnostic reports, and treatment plans are securely stored in the blockchain-based EHR system. In the quantum era, the proposed hybrid signature scheme combines the ECDSA with Dilithium and lattice-based blind signatures to safeguard patients' health data. By combining EHRs with a quantum-resistant signature scheme, her sensitive information is kept secure and protected from any potential quantum threats. The system's security measures, which encompass accuracy, privacy, and protection against tampering, serve as digital safeguards to prevent any malicious efforts to compromise Sarah's health information. The experimental results demonstrate the effectiveness and dependability of the proposed scheme in real-time healthcare scenarios, as evidenced by the smooth flow of transactions. In this particular situation, the suggested signature scheme resistant to quantum attacks not only enhances the security of electronic health records but also tackles the issues of scalability, performance, and interoperability in the ever-changing healthcare environment. The system's focus on secure sharing and privacy preservation ensures that the patient's data is only accessible to authorized entities, which helps build trust in the healthcare ecosystem during various medical procedures. In addition, the resilient and efficient solution effectively addresses the challenges presented by quantum computing threats. The system's advantages become clear when healthcare providers, researchers, and regulatory bodies work together smoothly, taking advantage of the strong security measures without giving up the performance and accessibility of electronic health records.
Our contribution
Message secrecy, authenticity, integrity, and non-repudiation are all guaranteed by digital signature algorithms. There have become concerns about the security and privacy of EHRs due to their increasing digitization. Traditional cryptographic systems struggle to adequately safeguard the sensitive medical data stored in EHR. Our research presents a hybrid signature scheme that focuses on the security needs of EHR systems, offering a solution to the challenges they face. We provide a hybrid signature technique that combines ECDSA and Dilithium using a blind signature-based anti-quantum lattice technique to defend the conventional encryption system from quantum assaults. One of the most popular methods for applied cryptography is the ECDSA. The older DSA, created by David Kravitz, is standardized as ECDSA. Across finite fields, ECDSA employs elliptic curve operations as opposed to DSA, which is based on arithmetic modulo a prime. Digital signatures, safe key exchange, and secured network technologies like TLS/SSL are just a few of the areas where Elliptic Curve Cryptography (ECC) is employed a viable option to create a public key in post-quantum cryptographic standards is lattice-based cryptography [18,19,20]. Considering the difficulty of lattice issues in modular lattices, Dilithium also acts as a digital signature technique that is extremely secure from certain types of message attacks. This system's security features are quite robust, as an attacker having access to a signature oracle is unable to provide a new signature for a message that hasn't been signed previously or an alternate signature for an electronic message that already has been signed. Although traditional cryptographic methods have been successful in many areas, the complex requirements of EHR necessitate a unique approach. EHRs store confidential patient data, and the proposed hybrid signature scheme offers a customized solution to address the unique security issues posed by EHR systems. In the upcoming sections, we will discuss how our scheme can be integrated with EHR processes and its effectiveness in safeguarding the confidentiality and integrity of patient data. The following are the research's main contributions:
-
To analyze existing security architectures for securing Electronic Health Records (EHRs) and identify their strengths and weaknesses.
-
To enhance the suggested blockchain-based architecture's security by employing quantum computing approaches, such as quantum blind signatures, to protect against quantum attacks.
-
To design and implement a hybrid signature scheme that combines ECDSA and Dilithium to provide efficient and secure digital signatures for the EHR platform based on blockchain.
-
To determine the effectiveness of the suggested architecture and signature system in terms of resource consumption, transaction latency, and transaction throughput.
-
To compare the suggested approach to cutting-edge approaches according to security, efficiency, and usability.
Organization of the paper
The article's remaining sections are arranged as follows. Part II provides a summary of pertinent work. EHRs security in part III describes the use of a Quantum-Enhanced Blockchain that combines ECDSA and Dilithium with a lattice-based anti-quantum blind signature. Part IV discusses the framework's performance evaluation and implementation results. Part V concludes by discussing the findings and making some final observations.
Background and literature review
This section provides an overview of the context of our study and summarizes the existing literature.
Background
Electronic health records (EHRs)
EHRs have become the new standard for collecting patient information, replacing the traditional method of gathering data. The change is due to the fast advancements in IT and the internet. Furthermore, health information encompasses extremely confidential personal details that should be disclosed to individuals such as healthcare professionals, pharmacists, family members, insurance providers, and other medical facilities.
Blockchain technology
Blockchain is a decentralized system that records and maintains a log of transactions across multiple computers. Initially supported as the fundamental technology behind Bitcoin, it has since gained popularity for various applications beyond just cryptocurrencies [18]. Blockchain is a network of interconnected blocks that grows as more transactions are included in the blocks. This platform employs a decentralized method that enables the sharing of information and equal ownership of all data. Peer-to-peer networks control blockchains, which consist of encrypted transactions that are safeguarded by the technology. Blockchain offers numerous benefits such as ensuring the integrity of data, enhancing security, and providing anonymity. It is logical to store patients' healthcare information on it considering these advantages. The increasing advancements in technology within the medical industry have raised significant concerns regarding the security of patient medical data. Researchers from various fields have also determined that implementing blockchain technology in the medical industry would be a feasible approach.
Blockchain in electronic health records (EHR)
It has been necessary to digitize medical records much more during the past 10 years since doing so makes the data simpler to access, distribute, and utilize as the basis for improved efficiency and effectiveness in decision-making. This requirement has been influenced by healthcare workers, facilities, and supplies. Electronic health records are now the area where blockchain technology is being used in healthcare the most often [19]. It is challenging to retrieve a patient's history since EHRs (Electronic Health information) were not designed to retain lifetime information across various institutions as patients' lifestyles change and they switch between different providers. Due to the urgent need for an innovative technique for handling EHRs in a way that encourages patients to connect with their recent and previous healthcare data, several researchers have recommended employing blockchain technology.
Doctors, radiologists, healthcare professionals, chemists, and researchers commonly share exceedingly sensitive and critical patient data available in EHR for correct diagnosis and treatment. The retention, transfer, and distribution of this very private patient information around several organizations might put the patient's treatment in danger and carry significant dangers to the patient's health and ability to maintain their most current medical history. Patients who are facing chronic diseases (such as cancer and HIV) may be more susceptible to such dangers due to a protracted history of making the initial-and-post medical treatment, follow-ups, and rehabilitation processes. Today, keeping a current patient history correct is essential to guaranteeing a successful course of therapy. A blockchain-based system has been developed for monitoring, archiving, and transferring the electronic medical records of cancer patients to get around these restrictions. To manage, access, and maintain encrypted patient data, they deployed a permissioned blockchain platform. Using these suggested methods, blockchain may be utilized in medical practices to access and manage the security and confidentiality of patient data and records.
Quantum computing (QC)
The quantum computing hypothesis was initially conceived in 1982 by Richard Feynman. It has now undergone much investigation, and it is currently believed to be the demise of state-of-the-art asymmetric encryption. Quantum computing (QC) makes use of entanglement and quantum superposition as part of the physical quantum theory. QC utilizes qubits, often referred to as quantum bits, as opposed to bits, which are used in traditional computing. As a result across the qubit-based computing environment, QC handles enormous amounts of real-time parallelism of data. As a result, QC promotes the use of some fields, including electronics, information theory, cryptography, communication theory, and image processing. Superposition is a qubit characteristic that enables quantum computers to process certain sorts of calculations substantially more quickly than conventional computers. The ability of several quantum bits to be interlinked in a manner in which their current states are correlated is known as entanglement, and it is another quantum trait that can be used by quantum computers. Certain calculations can be carried out simultaneously using this characteristic, which can significantly speed up traditional computing [20].
The QC is also perfect for several computer-intensive applications, including the medical field. Medical equipment is connected to the cloud and the digital healthcare system through the internet. To solve challenging tasks, quantum computers make use of the previously mentioned characteristic. When two qubits get entangled, they can cease to be described as separate objects with distinct states, but rather as a single item with four states. Additionally, regardless of how far apart the two qubits are from one another, if any of the two qubits' states change, the entangled qubits will also change. As a result, real parallel processing power is achieved.
Relate works
Blockchain has become increasingly popular in various fields, including data storage, sharing, and confidentiality. This technology has been widely utilized in numerous studies to tackle issues within current EHR systems. Medical facilities commonly use private IT infrastructure deployments, which can have restrictions on flexibility and information sharing. Choosing the right type of blockchain (private or public) is essential when it comes to sharing medical data. Xie et al. [21] introduced a fresh blind ring sign strategy based on a lattice in the context of blockchain transaction systems that are entirely anonymous. In blockchain transactions, blind ring verification can implement total user identity privacy and anonymity. Lattice cryptography, meanwhile, can withstand attacks from quantum computing. In the beginning, the suggested signature scheme offers strong computational privacy using a high sample success rate and the small integer solving (SIS) problem using the procedures for rejecting data from a BGD. Second, the suggested signature scheme can fulfill the random oracle model's requirements for accuracy and security, involving anonymity, blindness, and unforgeability. Lastly, we build blockchain transactions according to the suggested blind ring signature algorithm, realizing the identity privacy of blockchain users in a way that is completely hidden and anti-quantum computing secure. Deng et al. [22] have studied the identity-based BS (IBBS) security criteria, created a real-world IBBS system, and demonstrated security in the standard model. Before transmitting the message to the signer, the user hides the content that requires signing. The signer uses a confidential key to create a signature for the anonymous message and then sends it back to the user. The user eliminates the signature's blinding and sends it to the verifier. The verifier ascertains whether the signer of the received signature produced it. It is crucial to protect users' privacy when conducting business online. Because of the signer's inability to see the message they signed, BS is appropriate for use in online transactions.
According to Yi et al. [23], a threshold signature technique based on the NP-hard issue of integrating quadratic functions in a finite field is safe against attacks from classical and quantum computers. Second, they add a new threshold signature technique to their list of proposed efficient blockchain consensus algorithms. They developed an entirely novel blockchain structure based on the consensus mechanism as their third step. Several application scenarios, like the Social Internet of Things (IoT), can utilize blockchain technology. With the growth of IoTs, social networks, and IoT technologies have been merged to create a unique network called SIoTs, which emphasizes social enjoyment and leverages data from personal things as its media. By using the blockchain consensus process, user privacy and SIoT security may be strengthened. Quan and Yunjia [24] have addressed this by presenting a LAS scheme, and a unique negligible Scalable Transparent Arguments of Knowledge (STARK) method based on Dilithium- CRYSTALS. The proposed LAS technique fully utilizes the STARK protocol for signature aggregation and the quick and simple Dilithium implementation to provide post-quantum secure signatures with minimal signature aspects, which are crucial for efficient transaction processing. Dilithium 2, has a manageable public key size, tiny signature size, and sufficient quantum security. Dilithium2 signatures typically have a size of 2420B, which is nearly 33 times larger than the ECDSA signature size of 72.5 bytes. They put our plan into practice and discovered that compared to utilizing ECDSA; our plan would simply triple the efficiency of Bitcoin transactions.
Johari et al. [25] introduced a significant contribution to the field by proposing the utilization of Blockchain containers across multiple ports for the storage of patient medical records. Their work introduces a Blockchain framework named "Medichain," designed from the ground up to encompass essential Blockchain functionalities for securing patient data. The Medichain framework employs a decentralized and distributed network, ensuring the effective and secure storage of patient details. Each block within the Blockchain maintains a comprehensive list of patient records, and users are empowered with the option to upload files containing record lists in JSON format. Shahid et al. [26] presented Smart Digital Signatures (SDS), a small and effective HBS scheme that is more similar to the widely used HBS system eXtended Merkle Signature Scheme (XMSS). SDS-OTS, a brand-new one-time signature (OTS) system, is included in XMSS by SDS. In addition, compared to XMSS, SDS employs a slightly distinct key compression tree. SDS, XMSS-WOTS, and XMSS-WOTS + have all been contrasted. There are 17 different values in both the private and public keys. By starting with a particular beginning value, frequently referred to as the seed, we produce each private-key value. The hashing of the information to be signed is the first step in the production of a signature. The entire amount of hexadecimal symbols the message-hash contains is 96, and we advise choosing the hash function "SHA384". Among all of the available FTS/OTS methods, the most compact OTS system is SDS-OTS.
In their study, Lee et al. [27] made significant improvements by introducing the concept of blockchain and smart contracts to create a mechanism for sharing electronic medical records, which they referred to as "medical blockchain." The main emphasis of their work is on implementing a cryptographic design to enable the sharing of medical records. The authors used simulations to show that blockchain adoption guarantees the accuracy of medical data and protects patient privacy. Furthermore, they highlight the importance of smart contracts in ensuring the authenticity of individual patient records. Mishra et al. [28] have presented the "DS-Chain" model, which is a new and innovative approach to securely storing EHR using a consortium blockchain in a multi-cloud environment. This model's main idea is to combine the operations of each EHR outsourcing into transactions on a highly efficient consortium blockchain. The main goal of the suggested approach is to protect the privacy of sensitive medical data stored in EHRs, while also ensuring that the outsourced records remain accurate and unaltered. The authors utilize a collaborative multi-cloud storage model, which offers a satisfactory level of durability and availability for the outsourced electronic health records (EHRs) within the cloud paradigm. Furthermore, the framework arranges transactions according to the corresponding EHR types on the blockchain network, ensuring the efficient removal of blocks.
Li et al. [29] developed a number theorem research unit identity-based proxy with blind signatures using a lattice that can thwart assaults from quantum computers and is independent of key infrastructure for public keys. The safety of the suggested method depends on the Ring-Small Integer Solution issue across the lattice of number theorem research units. The suggested technique complies with proxy signature and blind signature requirements. This technology is crucial to an offline electronic payment mechanism that works with fog computing architecture. We provide evidence of the effectiveness and security of hybrid identity-based proxy blind signature (IDPBS) and number theorem research unit lattice (NTRU). Qu et al. [30] have made an important improvement with their innovative distributed quantum electronic medical record system. They have also proposed a new private quantum blockchain network, highlighting the importance of security. This quantum blockchain stands out due to its unique data structure, where blocks are connected through entangled states. The timestamp is generated automatically by linking quantum blocks with controlled activities, which helps to minimize the amount of storage space needed. It is worth mentioning that the hash value of each block is recorded using only one qubit. Apart from that some other work related to the blockchain and its application are found in the literature [31,32,33,34].
A thorough examination of the literature reveals that existing cryptographic systems may not fully meet the stringent security demands of EHR. The intricate network of healthcare data, coupled with the need for patient privacy and data integrity, requires a more advanced and adaptable solution. Our research builds upon these insights to propose a hybrid signature scheme designed specifically to fortify the security of EHR data.
Problem identification
The key concerns identified via the examination of the aforementioned works are given below:
-
The Existing papers in Signature schemes require the management of public and private keys, which can be challenging in large-scale applications. If the keys are not properly managed, they may be lost, stolen, or misused, leading to security breaches.
-
Also, the size of the digital signature can be larger than the original message, which can be a problem in applications where bandwidth or storage capacity is limited. There are numerous digital signature schemes, and they are not always compatible with each other. This lack of standardization can make it difficult to implement signature schemes across different systems and applications.
-
To overcome the problem of the Existing methods, this proposed system uses a hybrid signature scheme that combines ECDSA and Dilithium with an anti-quantum blind signature to get better performance in terms of security and efficiency.
System model
Proposed methodology
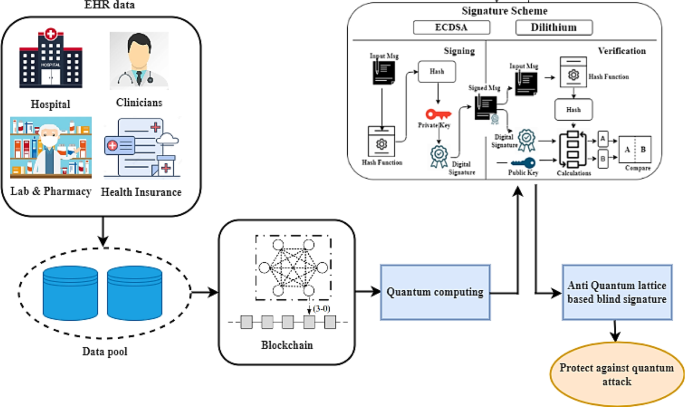
Healthcare systems are in high demand, yet it takes a lot of time and effort to obtain EHR information from one organization to another. Furthermore, there is no benchmark or ideal solution accessible to address this issue. Blockchain, on the other hand, can offer a decentralized network to address this issue, and by doing so, security in the healthcare system can also be addressed since data saved on the blockchain cannot be altered. Additionally, as quantum computers become more prevalent, the quantum assault will soon pose a serious security danger. Any quantum computers might render standard encryption useless. In light of the aforementioned problems, we suggest a secure blockchain-based solution for usage in the healthcare industry. To defend the structure against quantum attacks, we’ve also made connections between blockchain and the theoretical aspects of quantum technology [31].
The proposed protocol is structured into three distinct phases, with each subsequent phase developing upon previous ones.
Phase 1: System initialization and cryptographic setup
During the initial stage, our system goes through a thorough setup of cryptographic infrastructure. This requires setting up a strong key management system to establish a secure foundation for future cryptographic operations. Next, the ECDSA is utilized to create reliable public and private key pairs. This stage is responsible for developing the necessary cryptographic credentials that are vital for tasks such as data encryption, verification, and user authentication. Users are registered in the system and given unique cryptographic credentials that are generated using ECDSA keys. This process guarantees the recognition and safe involvement of stakeholders within the blockchain framework.
Phase 2: Secure data storage and transaction processing
Dilithium's lattice-based approach plays a crucial role in generating highly secure secret keys with maximum entropy. These keys provide a strong basis for securely storing and accessing EHRs within the blockchain. EHRs are smoothly incorporated into the blockchain, utilizing the encryption and decryption processes facilitated by the Dilithium-generated keys. This integration guarantees the privacy and security of healthcare data at every stage. The proposed model incorporates a hybrid signature scheme that combines ECDSA and Dilithium. This feature guarantees a high level of security for signing and verifying transactions within the blockchain, which significantly strengthens the overall security of the system. The system is designed to support real-time processing of transactions, ensuring the smooth and secure updating of healthcare data. This guarantees that the blockchain functions flexibly, adjusting to the changing landscape of healthcare transactions while safeguarding the privacy of all involved parties.
Phase 3: Defense against quantum threats
Dilithium's lattice-based approach plays a crucial role in generating highly secure secret keys with maximum entropy. These keys provide a strong basis for securely storing and accessing EHRs within the blockchain. EHRs are smoothly incorporated into the blockchain, utilizing the encryption and decryption processes facilitated by the Dilithium-generated keys. This integration guarantees the privacy and security of healthcare data at every stage. The proposed model incorporates a hybrid signature scheme that combines ECDSA and Dilithium. This feature guarantees a high level of security for signing and verifying transactions within the blockchain, which significantly strengthens the overall security of the system. The system is designed to support real-time processing of transactions, ensuring the smooth and secure updating of healthcare data. This guarantees that the blockchain functions flexibly, adjusting to the changing landscape of healthcare transactions while safeguarding the privacy of all involved parties.
System model design
Our proposed hybrid signature scheme plays a crucial role in strengthening the security framework of EHR. With the digitization of healthcare data on the rise, there is a growing demand for strong cryptographic solutions. Our scheme incorporates cutting-edge security measures that exceed the constraints of conventional cryptographic methods. By combining ECDSA with Dilithium and anti-quantum lattice-based blind signatures, we developed an advanced security layer. Ensuring the security of patient information is of utmost importance in EHR, protecting it from potential quantum threats and unauthorized access.
Interplay of privacy and technology
Ensuring patient privacy is of greatest significance in the healthcare field. Our hybrid signature scheme enhances the security of EHR and also plays a crucial role in safeguarding patient privacy. The lattice-based blind signatures bring a new level of privacy protection to the table, guaranteeing that confidential patient data stays secure and anonymous within the blockchain.
Blockchain as a trustless system
Our approach is based on the secure foundation of blockchain technology, which is essential for maintaining the confidentiality and reliability of electronic health records. Nevertheless, we understand the importance of scalability to make it feasible for real-world use. Our approach goes beyond the scalability limitations of traditional blockchain systems by strategically incorporating a hybrid encryption technique and an anti-quantum signature.
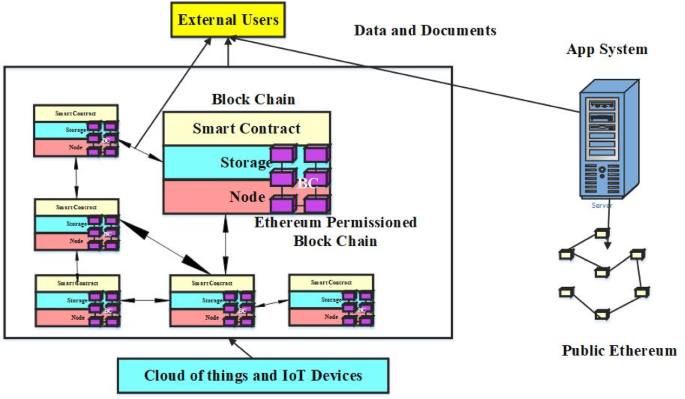
In this study, the patient, physician, lab, researcher, pharmacy, and health insurance data are all included on the blockchain. Access is defined in several smart contracts according to their duties. Blockchain medical records' patient identifiable information is gathered via the Healthcare Dataset. Blockchain-based technology is a practical option for managing individual EHRs. It is one of these cutting-edge technologies that might contribute to enhancing the confidentiality and safety of medical data. Application of QC to the conventional encryption scheme is a blockchain-based healthcare system. Figure 2 gives the block diagram of the proposed architecture.
Signature scheme
A sort of cryptographic technique known as a signature scheme protects the integrity and authenticity of messages and also non-disclosure of origin, which prevents the sender of a message from denying that they sent it. A confidential key that corresponds to the signer is used in a signature technique to calculate a digital signature over a message. Anyone can use the public key of the signer that is made accessible to all parties, to verify the signature [35]. If and only if one-way functions are present, a signature scheme is present. These solutions are undesirable in practice due to the need for the signer's secret key to vary between calls to the signature algorithm and the efficiency of these general structures. The signature method makes sure that each message's signature is distinct and that any tampering with the message will be detected by the recipient. Additionally, the signer alone receives the secret code required to establish the signature, so the recipient can be certain that the communication was delivered by them.
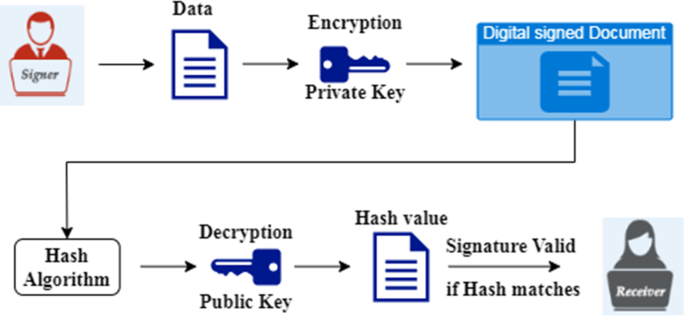
The digital signature algorithm (DSA)
Although essential for protecting information systems, data encryption is not the same as a digital signature (DS). Digital alternatives to signatures that are written (and more) are what the DS model aims to give. A DS scheme consists of three main components: a key generation algorithm that generates a public key (PK) and a secret key (SK), a data signing method that takes a message (m) and a secret key (SK) as inputs to produce a signature, and a verification method that checks if a given string is a valid signature for a message using the public key (PK). An electronic signature is a type of code that depends on both confidential information that the signer alone is conscious of and the data in the message being signed. The ability of a neutral third party to resolve a disagreement about a signer's signature fairly without demanding access to that person's private key is a requirement for valid signatures. When a signer seeks to retract a signature, it generated or whether an impostor makes a false claim, disputes may occur [36]. The basic digital signature algorithm is illustrated in Fig. 3.
Let \(q\ge \text{3 and }p\) and \(q \left|p\right.-1.\) be prime numbers. \({F}_{q}\text{ and }{F}_{p}\) Represent fields of \(q\text{ and }p\) elements respectively, as is customary. We assume that these fields are as shown by the elements \(\{0,...,q-1\}\) and \(\{0,...,p-1\}\) respectively. The residue of \(s\) after dividing by \(m\) is shown for integers \(s\) and \(m\ge 1\) by the symbol \(\left\lfloor s \right\rfloor_{m}\). Additionally, \(\mathit{log}z\) is used to represent the logarithm of binary \(z>0.\)
Let \(h:M\to {F}_{p}\) be any hash function and let \(M\) be the collection of messages that need to be signed.Component \(\alpha \in {F}_{q}^{*}\) is the signer's secret key.
Make \(g\in {F}_{p}\) an established element of \(q,\) order multiplicative multiplicity that is \({g}^{q}=1\) and \(q\ne 1\) which is publicly known. One selects a random number to sign a message with \(\mu \in M,k\in {F}_{q}^{*}\) also known as the nonce, is normally kept private. Next, one determines the next two components of \({F}_{q}\).
The message's DSA signature \(\mu \) with a nonce \(k.\) is represented by the pair \(\left(\rho \left(k\right),\sigma \left(k,\mu \right)\right)\), in reality, \(q\) typically has a bit length of 160 and the common bit size for \(p\) is between 512 and 1024.
ECDSA
The equivalent of the elliptic curve for DSA is called the ECDSA. The ANSI standard was approved in 1999, while the IEEE and NIST standards were approved in 2000. Additionally, In 1998, it was approved as an ISO standard, and discussions are now taking place to include it in additional ISO standards [37]. The discrete logarithm issue with an elliptical curve does not have a sub-exponential-time approach, unlike the regular discrete logarithmic problem and the integer factorization problem. For this reason, an elliptic curve-based technique has a significantly higher strength per key bit. The ability of ECC to withstand attacks from quantum computers is one of its key advantages. While ECC is thought to be resistant to quantum assaults, classic public-key encryption algorithms like RSA and others are thought to be vulnerable. When \(p\) is prime, the elliptic curve \(E\) over \({F}_{p}\) used by ECDSA. If \(N=\left|E\left({F}_{p}\right)\right|\) represents the total number of reasonable points over \({F}_{p}\), then it is widely known that
and that \(E\left({F}_{p}\right)\) Forming an Abelian group is the point at infinity \(\vartheta \), see Silverman,
The message \(\mu \), ECDSA signature, along with a nonce \(k\), is represented as the pair \(\left(r\left(k\right),s\left(k,\mu \right)\right)\). As in the case of DSA in practice, \(q\) is usually of bit-length around 160.
ECDSA is a simulation of DSA using an elliptic curve. But compared to DSA, it is faster and safer. There are three stages to the ECDSA: key generation, signature generation, and verification.
Key generation for ECDSA
The key pair of entity A is associated with a certain set of EC domain variables \(D= (a, q, n, b, FR, h, G)\). P is a point of rank n in the elliptic curve \(E (Fq), E\) has been assigned over \(Fq, q\) is a prime, and each individual A does the following:
Randomly select an integer d from the range \(\left[1,n-1\right]\).
Calculate \(Q=dp.\)
The private key of A's is d, public key of A's is Q.
Signature generation for ECDSA
A message \(m\) and a private key \(d\) are two domain-specific elements that affect how ECDSA signatures are generated. The outputs correspond to the signature (\(s,r\)), where sandr are integer components of the signature, and the process is as follows:
Pick an integer k at random or ostensibly at random [1, n − 1].
Calculate \(R=X1\) and \(kp=x1,y1\) mod n (where \(x1\) is thought of as a number that ranges from 0 to \(q-1\)). Go return to step 1 if R = 0.
Calculate \(k-1\,{mod}\,n.\)
Calculate \(S=k-1 \left\{h(m)+d.R\right\}\) mod n, where h is a hash function. Return to step 2 if S equals 0.
The integers (R, S) make up the message's signature.
Signature verification for ECDSA
The message m and the private key d are two domain parameters that are used in the ECDSA signature verification process.
Check to see if \(r\) and \(r\) are integers \(\in \left[1,n-1\right]\), Otherwise, the signature is not authentic..
Determine \(e=H(m)\).
Determine \(w={S}^{-1}m\,{od}\,n.\)
Determine \({u}_{1}=ew\,{mod}\,n\, \text{ and }{\text{u}}_{2}=rw \,{mod}\,n.\)
\(Y={u}_{1}G+{u}_{2}{G}_{u}=\left({x}_{2},{y}_{2}\right),ifY=O\) the signature is void, and you should cease.
Determine \(t={x}_{2} \,{mod}\,n.\)
Only if \(t=r.\) accept the signature.
Dilithium
The scheme is built upon the concept of "Fiat-Shamir with Aborts" and shares similarities with the Bai-Galbraith scheme [38]. We achieve a significant reduction in the size of the public key by compressing it by a factor slightly greater than 2. This is a notable distinction. The algorithms allow for the generation and use of hints to reconstruct the high-order bits of polynomials. The parameters. The secret keys are carefully selected to ensure that their coefficients have a maximum magnitude of η. We choose an integer β in such a way that the maximum absolute value of the dot product between s and c is less than β with a high probability (around 1 − 2 − 80) when s is selected from Sη and c is selected from B60. The parameters γ1 and γ2 determine the probability of rejection and the size of the signatures. Increasing the values of γi will result in larger signatures, but a smaller probability of rejection.
The signature scheme
Our signature algorithm is described in Algorithms 8 to 10.
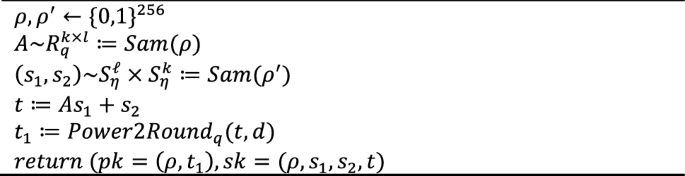
Algorithm 1 KeyGen()
To generate the key, a random 256-bit seed ρ is chosen and then expanded into a matrix \(A\in {R}_{q}^{k\times {\ell}}\) using an extendable output function called Sam. This function is specifically designed to imitate a random oracle. Sam creates the secret keys s1 and s2 by extending a random seed \({\rho }^{\prime}\) and ensures that the coefficients are uniformly random within the range of − η to η (including both extremes). The calculation of the value \(t = A{s}_{1} +{ s}_{2}\) is executed. The secret key is composed of various parameters, such as \(\rho , {s}_{1}, {s}_{2}, t\).It is worth noting that t1 is calculated as \(t = {t}_{1} \cdot {2}^{d} + {t}_{0}\), where \({t}_{0}\) is a small value.
The signing process begins by dividing the entire \(t = A{s}_{1} +{ s}_{2}\) into \({t}_{1}\, and \,{t}_{0}\), with the condition that \({t}_{1}.{2}^{d}+{t}_{0}=t\), where \(\parallel {t}_{0}{\parallel }_{\infty }\le {2}^{d-1}.\)
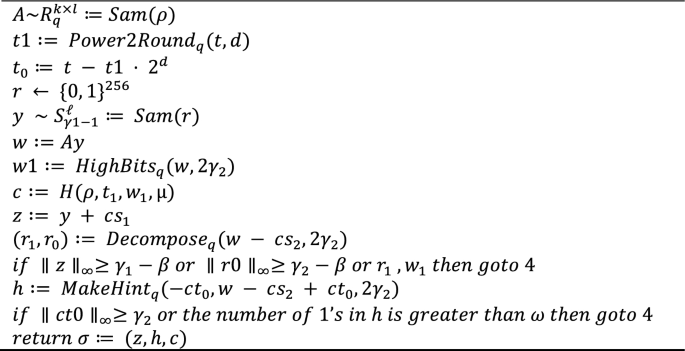
Algorithm 2 Sign\((sk = (\rho, s_1, s_2, t), \mu \epsilon M \)
In the subsequent stage of the signing algorithm, the signer will utilize the extendable output function Sam along with a random seed r to generate a sample y with coefficients in \({\text{S}}{\upgamma }_{1}-1\). After that, the signer will compute w by multiplying A with y. Next, the signer expresses w as 2γ2 times w1 plus w0. The value of w0 falls within the range of -γ2 to γ2, including both extremes. Then, the signer calculates c as \(H(\rho , {t}_{1}, {w}_{1}, \mu )\) belonging to \({B}_{60}\). Once c is acquired, the signer calculates z by adding cs to y. If any coefficient of z is greater than or equal to γ_1—β, the signing procedure will start over. If the magnitude of a coefficient of \({r}_{0}\), denoted as \({LowBits}_{q}(w - c{s}_{2}, 2{\gamma }_{2})\), is equal to or greater than \({\gamma }_{1}-\beta \), the process will restart. This portion of the protocol is crucial for maintaining security as it ensures that no information regarding the confidential keys s1 and s2 is exposed. It is crucial for the correctness of the program that r1 is equal to w1, which is verified by the final check. It is worth noting that if the maximum norm of cs2 is less than or equal to β, then if the maximum norm of r0 is less than \({\gamma }_{2} - \beta \)\(\parallel cs2{\parallel }_{\infty }\le \beta \), it immediately follows that r1 is equal to w1. Given our desire for to be ≤ β with a high level of certainty for security purposes, the likelihood of this final check being beneficial is extremely small. However, we include it to maximize the likelihood of a verifier accepting a valid signature, instead of it being only slightly close to 1.
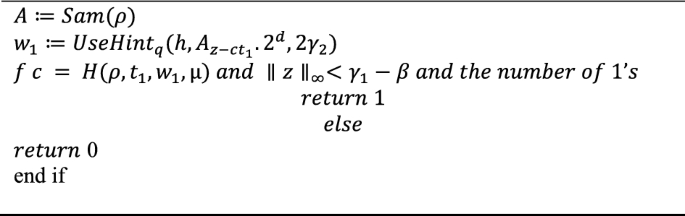
Algorithm 3. Verify \((pk = (\rho, t_1), \mu \epsilon M, \sigma = (z, h, c)) \)
Verification is performed by reconstructing w1 using the signature and the public key. Then, it checks if c is equal to \(H(\rho , {t}_{1}, {w}_{1}, \mu )\) and if all the coefficients of z1 are smaller than \({\gamma }_{1 }- \beta \). Additionally, it verifies that the number of 1's in h does not exceed ω. The quantity of ones in h is dictated by the number of ct0 values that result in a carry happening. Given the relatively small value of ct0, it is highly likely that a carry will not occur.
Anti-quantum lattice-based blind signature
A user can sign a document using an anti-quantum blind signature, a cryptographic mechanism, without disclosing any details about the person signing or the document itself [29]. As a result, it is challenging for attackers, particularly those employing quantum technology, to intercept or alter the signature. This offers an excellent degree of privacy and security. Blind signatures and lattice-based encryption work together to protect electronic medical information. The blind signature method enables a user to receive a signer's signature on a document without disclosing any details about the signer or the document. The document is first made blind using a random number that is only known to the signer and the user.
The signer then uses a lattice-based signature mechanism to sign the blinded document. Although the paper is blinded, the signer can confirm that it is a legitimate document to sign even if they are unaware of its contents. The user can utilize the same random number that was used to blind the signature after obtaining it.
Anti-quantum using a blind signature, a user can receive a signature on an electronic communication without the signer being made aware of the message's contents. This is accomplished by "blinding" the message so that the signer can sign it without understanding what it contains. When the requester wishes to keep their communication private but yet get a legitimate signature, blind signatures may be employed.
Ke generation (n, q, k, u,\(\sigma , \eta )\): Select j as the system security parameter along with a few other options (n, q, k, u,\(\sigma , \eta )\). The public key \((Y \in B_{2q}^{m*n} )\) and private key \(G \in B_{2q}^{m*n}\) are produced using the Key Gen: technique, so \(\left\| {\vec{G}} \right\| \le O(\sqrt {n\log q} ,m = O(n\log q)\). In this case, the private key is a n*m and the public key is a n*m matrix, and they provide satisfaction \(YG = ql_{n} (\bmod 2q)\) Since the public key and private key are separate, creating key pairs may be done easily.
Blind algorithm \((m,x,Y \in B_{2q}^{n*m} ) \to (e)\): The owner U should first blindfold the message before the signature phase. The signer sends a commitment \(x \leftarrow Yr\) to the user after selecting a random vector \(j = X_{{\sigma_{2} }}^{m}\) for a message µ. The message is then hidden using the blind factors and the signer's public key by the user U implementing the Blind algorithm. The blind message e of the original message \(\mu\) is then produced with probability \(\min \left( {\frac{{X_{\sigma 1}^{k} (\mu )}}{{M_{1} X_{{c,\sigma_{1} }}^{k} (\mu )}},1} \right)\). The signer receives the blind message from U at the conclusion, and the specific processes are displayed in the following Algorithm 1.

Algorithm 1. Blind algorithm
Signing algorithm \((r \leftarrow X_{{\sigma_{2} }}^{m} ,G \in B_{2q}^{m*n} \to (z)\); The signer must sign the blind communication for user U to utilize it. The signer next employs his private key \(G \in B_{2q}^{m*n}\) and the previous random vector \(r \leftarrow X_{{\sigma_{2} }}^{m}\) to perform the Signing method. This produces the signature z of the blind message \(\mu\) with probability \(\min \left( {\frac{{X_{{\sigma_{2} }}^{m} (z)}}{{M_{2} X_{{S_{{\mu ,\sigma_{2} }} }}^{m} }},1} \right)\). The user receives the signature from the signer after that. The specific procedures are illustrated in the accompanying Algorithm 2.

Algorithm 2. Signing Algorithm
Blockchain-enabled system
Blockchain is a trustworthy database that is created and updated via an autonomous, trustless methodology. The first use of blockchain technology is Bitcoin, which creates a peer-to-peer electronic currency system in a trustless setting. Blockchain software has been used in a wide range of industries recently, including banking, industry, voting, contracts, digital currency, and industry. Soon, it will be used in even more industries. Still, the most crucial aspect of these information-based technologies is always the security issue. In particular, the latest advancements in quantum computing and computers pose more risks to the cryptosystems that we employ daily. The information will be encrypted and transferred to the system server, just like in the blockchain-enabled platform. The processes that are carried out will also be documented in the blockchain ledger.
Data creation: During everyday activities, the blockchain-enabled system will generate a large amount of data, which will be transferred to the native server. Blockchain technology can create a public ledger that holds the memory address and data operation procedures. In contrast to conventional storage formats, this approach may provide data security and chronologically record data operation operations.
Data verification: Before being included in the blockchain ledger, the original data must first be validated by the whole blockchain network. The primary accounting node that acquires the right to build a new block will communicate this information to other nodes for verification within a certain time frame. After confirming the information, the general nodes sign it with their signature and send it back to the primary accountancy node. The information will be posted to the blockchain ledger and integrated into a transaction after all verification findings have been verified.
Creation of a transaction: A transaction is a data structure with inputs and outputs. The prior transaction's hash value, its output value from the previous operation's index, and the purchase owner's signature, or ScriptSig, are all contained in the inputs. The value that is the subject of the transaction and the public key of the recipient is included in the outputs, correspondingly, as Value and ScriptPubkey. For instance, to initiate a transaction with user B, user A must first locate the latter's wallet address and public key. He then inputs the expense from his wallet and initiates a transaction from one of his addresses to B's address.
Blockchain ledger generation: The transactions will be stored in the system's blocks for a certain amount of time, and each block will have a digital fingerprint attached to it to facilitate verification and block connectivity. The hash value of the previous block will be stored in the block head of the subsequent block, and one new block will link to the previous block. It will create a blockchain ledger with a chronological order at the conclusion.
Transaction completed: The blockchain network together as a whole will be informed of the newly finished block. User B then uses his matching private key to confirm the transaction. The funds will be kept for the next transaction in user B's wallet address if the signature passes verification. The requirement that the operation's total input and entire output sums match is crucial to stress. Until a transaction is recorded into a block and added to the blockchain ledger, it is not considered complete [29].
Security proof
Throughout the proof, we will assume that the adversary is given the public key \(t = A{s}_{1} + {s}_{2}\). The assumption is advantageous for the adversary, as they only receive the most significant bits of t in the actual scheme. In practice, it may be even more difficult for the opponent to decode the scheme.
Lemma 3.7.1
Forging a signature implies finding \({x}_{1}, x,x\) such that \(\parallel x1{\parallel }_{\infty }\le 2{\gamma }_{1}, \parallel {x}_{2}{\parallel }_{\infty }\le 4{\gamma }_{2}+2\), \(\parallel x3{\parallel }_{\infty }\)≤ 2 such that \(A{x}_{1}+{x}_{2} = {x}_{3}{t}_{1}\cdot {2}^{d} and (x, {x}_{2},{x}_{3})\), 0. Furthermore, vector \({u}_{2}\) has at most 2ω coefficients of absolute value greater than 2 \({\gamma }_{2}\).
Proof
The public key is defined as \(pk = (A, t)\). The adversary generates signature queries. Here, we will discuss our extractor in the scenario where the Adversary generates a successful query.
If an opponent generates a legitimate signature (z, h, c) for a message µ, it implies that they must have made inquiries
Lemma 3.7.2.
Suppose that \(q and \alpha \) are positive integers satisfying \(q > 2\alpha , q \equiv 1 (mod \alpha )\) and α even. Let \(r and z\) be vectors of elements in \({R}_{q}\) where \(\parallel z{\parallel }_{\infty } \le \alpha /2\), and let \(y, y^{\prime}\) be vectors of bits. Then the \({HighBits}_{q}, {MakeHint}_{q}\), and \({UseHint}_{q}\) algorithms satisfy the following properties:
-
(1)
\({UseHint}_{q}({MakeHint}_{q}(z, r, \alpha ), r, \alpha ) = {HighBits}_{q}(r + z, \alpha ).\)
-
(2)
Let \({v}_{1} = Use{Hint}_{q}(y, r, \alpha )\). Then \(\parallel r - {v}_{1} \cdot \alpha {\parallel }_{\infty } \le \alpha + 1\).
-
(3)
For any \(y, y^{\prime}\), if \(Use{Hint}_{q}(y, r, \alpha ) = Use{Hint}_{q}(y^{\prime}, r, \alpha ), then y = y^{\prime}.\)
Case 1: If c was queried during a signing query, then the reduction already knows another \((z^{\prime}, h^{\prime},c)\) (and the associated \({w}_{1}^{\prime}\)) for a message \(\mu ^{\prime}\) such that \(H(\rho , {t}_{1}, {w}_{1}^{\prime}, \mu ^{\prime}) = c = H(\rho , {t}_{1}, {w}_{1}, \mu ).\) This implies \(that \mu = \mu ^{\prime}\) and \({w}_{1} = {w}_{1}^{\prime}\), or else we found a second pre-image for \(c\). Since \(w1 = {w}_{1}^{\prime}\), it must be that
If \(z = z^{\prime}\), then Lemma 3.4 states that we must have \(h = h^{\prime}\), which is in contradiction with the assumption that the adversary has found a new signature. Thus it must be that \(z\ne z^{\prime}\). By Lemma 3.4, we also know that
By the triangular inequality, this implies that
This can be rewritten as
Find a value of u such that its infinity norm is less than or equal to 4γ2 + 2, given that z—z′ s not equal to zero. Since h and h' have all elements except ω equal to 0, Lemma 3.4 implies that the coefficients of \(Az - {t}_{1}c \cdot {2}^{d} - {w}_{1} \cdot 2{\gamma }_{2}\) and \(Az^{\prime} - {t}_{1}c \cdot {2}^{d} - {w}_{1} \cdot 2{\gamma }_{2}\), except for ω, are all less than γ2. Thus, the majority of the coefficients of u, except for 2ω, are smaller than 2γ2.
Case 2: Now we address the scenario where the query in Eq. (5) was performed directly on H. Using a standard forking lemma argument, it can be shown that the reduction can extract two signatures \((z, h,c) and (z^{\prime}, h^{\prime},c^{\prime})\) for c and c′, respectively.
By Lemma 3.7.2, we know that
According to the triangular inequality, this means that
This can be rewritten as
For a certain value of u, where the maximum norm of u is less than or equal to 4γ2 + 2. Just like in the previous scenario, u can have a maximum of 2ω coefficients that exceed 2γ2.
Results and discussion
Blockchain-based technology may be used by EHRs, to improve the security, usability, and confidentiality of patient data. We also assess the effectiveness of our suggested strategy in terms of communication costs, signature length, and system security.
Experimental setup
To assess the effectiveness of the suggested framework, we carried out experiments using the following configurations:
-
Processor: Intel Core i7-6498DU CPU @ 2.50 GHz 2.60 GHz
-
Memory: 8.00 GB
-
Operating System: Windows 64-bit OS (version 10)
Our proposed framework was developed using Solidity, the programming language of Ethereum. The Solidity language, provided by Ethereum, encapsulates JavaScript and Python.
Security analysis
We have utilized several simulation settings to assess the proposed scheme's performance. Block size, time delay, and the number of peers are factors considered throughout the assessment process. The hyper ledger caliper blockchain benchmark tool evaluates the performance of several blockchain.
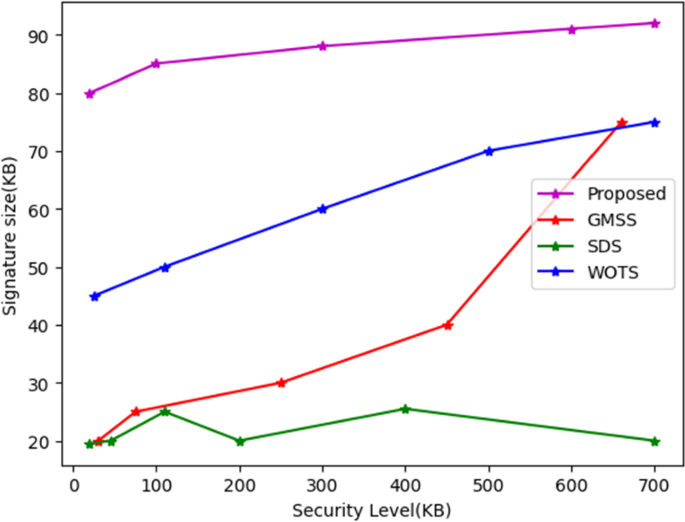
Evaluation of the security level of our signature system compared with other schemes with different signature sizes is given in Fig. 4. It illustrates how the other signature algorithm's signature size increases quickly as the security level rises. The size of the signature is only minimally increased by the proposed blind signature method. The signature size does not change as the security level increases. Additionally, the GMSS, SDS, and WOTS algorithms are not resistant to a quantum assault, but the suggested signature method is. Therefore, lattice-based encryption will be increasingly useful in the coming quantum era as quantum technology grows. This approach to lattice-based cryptography is substantially more conservative than earlier ones. Our system's security analysis makes sure that it can thwart assaults on the network that use impersonation, replay, and repudiation.
Here, we demonstrate how our system's user anonymity, message accuracy, and unforgeability are all highly assured.
Correctness
Here, we establish the validity of the signature scheme. We utilize the notation found in Algorithms 1–3.
If \(\parallel ct0{\parallel }_{\infty }<{\gamma }_{2}\), then by Lemma 3.7.2, we know that \({UseHint}_{q}(h, w - c{s}_{2} + c{t}_{0}, 2{\gamma }_{2}) = High{Bits}_{q}(w - c{s}_{2}, 2{\gamma }_{2})\).
Since w = Ay and t = As1 + s2, we have that
and \(- c{s}_{2} + c{t}_{0} = Az - c{t}_{1} \cdot {2}^{d}\). Therefore the verifier computes.
Then,
Thus, the computed value by the verifier matches that of the signer, ensuring that the verification procedure will consistently approve. This calculation confirms the accuracy of our scheme, showing its ability to handle different cryptographic challenges while preserving the integrity of the signature process.
As a result, the verification process will always be accepted since the \({w}_{1}\) that the verifier calculated and the signer are identical.
This computation verifies the accuracy of our plan and shows that it is resilient to different cryptographic difficulties without compromising the integrity of the signature procedure.
Anonymity
Theorem 1
(Anonymity) Assuming that n is the security parameter and that there are additional parameters \(m,s,\beta ,\alpha ,q\) are functions of \(n\). The odds of an opponent with polynomial time winning the anonymity game are quite small. Thus, our scheme is anonymous.
Proof
This characteristic (anonymity) is applied to both kinds of users via the use of a digital signature as a cryptographic tool or primitive. Thus, it must be shown that the ring signature being utilized is operated safely to validate the user's anonymity in the two aforementioned methods. The number of users among whom the user wishes to remain anonymous is known as the anonymity space. The anonymity space in the first kind is R, while in the second type, it is n. In this section, we typically assume that N is the anonymity space and that \({L}_{pub}\) is the list of members' public keys; using these two suppositions, we examine the digital signature and examine user pseudonymity in \(RS=\left\{m,s,\beta ,\alpha ,q\right\}.\)
Based on the demonstrated security of the utilized digital signature, the benefit to an outsider A in breaching user anonymity is computed to be \(\frac{1}{N}\), while the benefit to an insider A is determined to be \(\frac{1}{N-1}\). Consequently, the protocol ensures user anonymity by employing a secure digital signature.
The aforementioned theorem validates the anonymity of our scheme, thereby demonstrating its resilience to potential assaults and guaranteeing the preservation of user identities' confidentiality throughout the process of signature generation.
Unforgeability
Theorem 2.
Unforgeability is ensured for any efficient Probabilistic Polynomial Times (PPT) adversary G by our proposed scheme. This can be reduced to the SIS assumption.
Proof.
Assuming that the efficient attacker A has a non-negligible probability p of effectively forging the signature, we will demonstrate how the challenger C can determine a vector e, denoting a solution to the SIS problem, by utilizing the fabrication signature of efficient attacker A.
The game process is as follows:
SIS assumption:
Assuming an appropriate SIS, the technique meets target assessment bound. To put it briefly, a random SIS assignment is sent to the decrease \(Y \in B_{q}^{n \times C}\). It becomes \(x^{*}\) from the opposing party and provides the public characteristic \(W = Y + (x^{*} )^{t} \otimes g^{t} = Y\) and \(u = Yr\) for a continuously random (hidden) \(r \leftarrow \left\{ {0,1} \right\}^{C}\). Next, a function is added \(f^{*}\) from the opponent, and provides a genuinely made pledge \(W_{{f^{*} }}\)(and its inherent unpredictability); it further calculates the corresponding short multiplication matrix \(G_{{f^{*} ,x^{*} }}\) that fulfills. Lastly, if the enemy prevails, they produce a brief enough evidence \(g^{*}\) for \(y^{*} = 1 - f^{*} (x^{*} )\) which fulfills,
\(Y(\left[ {Q_{C} \left| {G_{{f^{*} ,x^{*} }} } \right.} \right]g^{*} - r) = 0\) producing a SIS solution, that will be highly likely to be nonzero because, from the adversary's perspective, r has a huge min-entropy.
(1) Setup: Given \(\le 3,m\ge 5\lambda {\text{log}}q,L=(O\sqrt{\lambda {\text{log}}q}),\vartheta =L(\omega \sqrt{{\text{log}}\lambda })\), we input security parameter \(\lambda \), and make two operations: (1) For \(1\le i\le l,C\) calls TrapGen to output \({P}_{i}\in {\mathbb{Z}}_{q}^{n\times m}\) obeying a random distribution and a set of bases \({T}_{i}\) of the lattice \({L}^{\perp }\left({P}_{i}\right)\), such that \(\left\| {\tilde{T}_{i} } \right\| \le\)\(L\). Then, \(C\) selects two hash functions: \({R}_{1}:\{\mathrm{0,1}{\}}^{*}\to {\mathbb{Z}}_{q}^{n}\), \({R}_{2}:\{\mathrm{0,1}{\}}^{*}\to {\mathbb{Z}}_{q}\). Moreover, challenger \(C\) calls AQRS.KeyExt to generate the user's public key \(L=\left\{{p}_{1},{p}_{2},\dots ,{p}_{l}\right\}\) and secret key \(s\), such that \(\parallel s\parallel \le \vartheta \sqrt{m}\). (2) \(C\) selects two matrices randomly \(B\leftarrow {\mathbb{Z}}_{q}^{n\times m},D\leftarrow {\mathbb{Z}}_{q}^{n\times m}\) then \(C\) sends \(\left({R}_{1},{R}_{2},{P}_{i},B,D\right)\) to the efficient attacker \(A\).
(2) Query: The challenger \(C\) builds lists \({L}_{1},{L}_{2},{L}_{3},{L}_{4}\) to store efficient attacker \({R}_{1}\) query, \({R}_{2}\) query, secret key \(s\) query, and signature query, respectively. Then, the efficient attacker \(A\) makes inquiries as follows and \(C\) answers these inquiries. (1) \({R}_{1}\) query: \(A\) chooses \({s}_{i}\) from \(\left\{{s}_{1},{s}_{2},\dots ,{s}_{l}\right\},i=\mathrm{1,2},\dots ,l\) to send an inquiry. After that, \(C\) checks list \({L}_{1}\), and if \(A\) has asked for this information, \(s\) will return the same result to \(A\). Otherwise, it returns \(L\) to \(A\), and add \(\left({P}_{i},{s}_{i},L,{T}_{i}\right)\) to list \({L}_{1}\). (2) \({R}_{2}\) query: \(A\) can enquire the message \(\mu \in \{\mathrm{0,1}{\}}^{*},s=\left\{{s}_{1},{s}_{2},\dots ,{s}_{l}\right\}\) and vectors \({t}_{i}\in {D}_{\vartheta }^{m+1}\). Then \(C\) checks the list \({L}_{2}\), and sets \(v={c}_{1}\), and then returns \(v\) to \(A\) and puts \((\mu ,R,T,v)\) into a list \({L}_{2}\), where \(T=\left\{{t}_{1},{t}_{2},\dots ,{t}_{l}\right\}\). It is worth mentioning that if \(A\) has asked for this information, \(C\) will return the same result to \(A\) as \({R}_{1}\) query. (3) Secret key query: First of all, \(A\) chooses the \({s}_{i}\in s\) to state secret key query. Then, \(C\) detects \(\left({P}_{i},{s}_{i},L,{T}_{i}\right)\) in List \({L}_{1}\). Through the SamplePre algorithm, \(C\) computes the secret key \(s\) satisfying \({P}_{i}\cdot s=L{\text{mod}}q\), and sends \(s\) to efficient attacker \(A\). Finally, \(A\) adds the two-tuples \(\left({s}_{i},s\right)\) in list \({L}_{3}\). (4) Signature query: To begin with, \(A\) selects the signer \({s}_{i}\), and asks \(C\) to compute a signature for message \(\mu \in \{\mathrm{0,1}{\}}^{*}\). After getting this signature query, \(C\) runs SampleDom to randomly select vector \(u\in {\mathbb{Z}}_{q}^{m+1}\), \({t}_{i}\in {\mathbb{Z}}_{q}^{m+1},i=\mathrm{1,2},\dots ,l\), such that \(\parallel u\parallel \le \vartheta \sqrt{m+1}\) and \(\left\| {t_{i} } \right\| \le\)\(\vartheta \sqrt{m+1}\). If \(u\) and \({t}_{i}\) does not meet this condition, \(C\) will restart the process. Moreover, \(C\) calculates \({R}_{1}\left({s}_{i}\right)\) as the public key of the user \({s}_{i}\), named \(L\). After that, \(C\) runs the SamplePre algorithm to get the secret key \(s\) satisfying \(\parallel s\parallel \le \vartheta \sqrt{m}\), at the same time, \(C\) also calculates \({R}_{2}(D,s)\), named \({r}_{\mu }\). Finally, \(C\) executes the SigExt Algorithm and outputs the linkable ring signature \({\vartheta }_{L}(\mu )=\left({c}_{1},{t}_{1},{t}_{2}\cdots ,{t}_{l},R,P\right)\).
(3) Forgery: Firstly, \(A\) submits a message \({\mu }^{*}\in \{\mathrm{0,1}{\}}^{*}\), the signature user identity is \({s}_{i}^{*}\in {s}^{*}\) and a forged ring signature \({\vartheta }_{{L}^{*}}(\mu )=\left({c}_{1}^{*},{t}_{1}^{*},{t}_{2}^{*}\cdots ,{t}_{l}^{*},R,P\right)\) satisfying: (1) The attacker \(A\) did not obtain the secret key of a user \({s}_{i}^{*}\); (2) The attacker \(A\) did not own the signature of \(\left({\mu }^{*},{L}^{*}\right)\); (3) The public key of any users in the ring \({L}^{*}\) is given by the challenger \(C\).
Analysis: Firstly, \(C\) queries the list \({L}_{2}\) of the efficient attacker \(A\), if \({L}_{2}\) includes \(\left({L}^{*},{\mu }^{*},{T}^{*},{v}^{*}\right)\), it will be considered as a legitimate signature. Otherwise, \(C\) gives up this game. If \({\vartheta }_{{L}^{*}}\left({\mu }^{*}\right)\) is a legitimate signature, we have the following:
Then, \(C\) obtains the secret key \({s}^{*}\) of user. Let \({t}_{i}={t}_{i}^{*},i=\mathrm{1,2},\dots ,k-1,k+1,\dots ,l\) and computes \({t}_{\pi }=\mu +{s}_{2q,\pi }\cdot {c}_{\pi }\cdot (-1{)}^{b}\), so the signature \({\vartheta }_{L}(u)=\left({c}_{1},{t}_{1},{t}_{2},\dots ,{t}_{l},R,P\right)\) is also a legal signature. Thus we have:
From the above equations, we obtain: \({T}_{P}^{*}{t}_{k}-{T}_{P}^{*}{t}_{k}^{*}=0{\text{mod}}q\) and \({R}_{B}^{*}{t}_{k}-{R}_{B}^{*}{t}_{k}^{*}=0{\text{mod}}q\).
If \({t}_{k}-{t}_{k}^{*}\ne 0\), due to \(\left\| {t_{k} } \right\| \le \vartheta \sqrt {m + 1} ,\left\| {t_{k}^{*} } \right\| \le \vartheta \sqrt {m + 1}\), we have: \(T_{P}^{*} t_{k} - T_{P}^{*} t_{k}^{*} = T_{P}^{*} \cdot\)\(\left\| {t_{k} - t_{k}^{*} } \right\| \le 2\vartheta^{2} \left( {m + 1} \right).\)
We now conclude that \({T}_{P}^{*}{t}_{k}-{T}_{P}^{*}{t}_{k}^{*}\) is a solution to the \(SIS\) assumption, and if \({t}_{k}-{t}_{k}^{*}=0,C\) will give up the game.
Assuming that the probability is \(\varepsilon \), which \(A\) can successfully forge a legitimate ring signature, and the probability of \(C\) successfully solving the SIS problem is \({\varepsilon }^{*}\). Thus, we have \({\varepsilon }^{*}=\varepsilon -\frac{1}{(2d{)}^{2}}\), equivalently, the challenger \(C\) can solve the \(SIS\) problem with probability \(\varepsilon -\frac{1}{(2d{)}^{l}}\).
The proposed scheme's unforgeability significantly validates the authenticity and integrity of records about users' interactions with other users or their access to public areas, thereby defeating tampering or falsification attempts by capable adversaries. In addition, it ensures precision in contact tracing and status updates, thereby mitigating the risk of misreporting attacks associated with epidemic tracing. For storage, we submit the records and signatures to the blockchain. The immutability and non-deletability characteristics of blockchain data after its transfer ensure that the user's signature and its associated records are impregnable. Table 1 demonstrates that our system has superior security and can withstand quantum assaults.
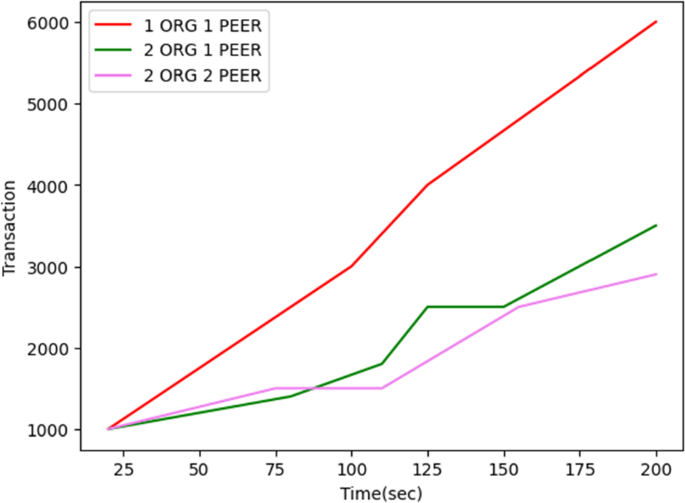
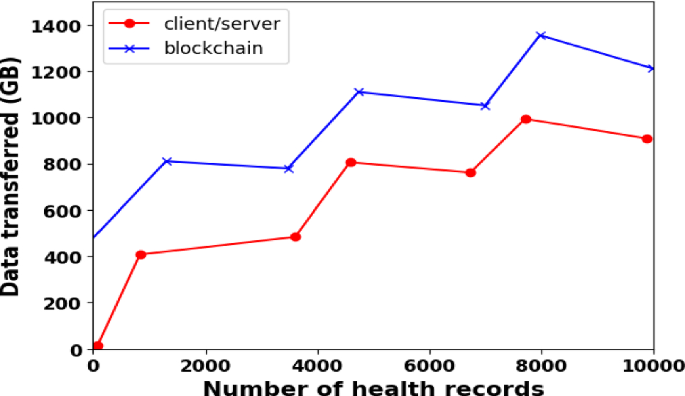
The duration of effective transactions in an average network is shown in Fig. 5. Here, 1ORG1PEER, 2ORG1PEER, and 2ORG2PEER demonstrate how different transactions work in different ways. Five rounds with 100 transactions each comprise this experiment. During this test, 1ORG1PEER only completed 2500 transactions, 2ORG1PEER completed 5000 transactions, and 2ORG2PEER completed the fewest transactions 2000 at the slowest pace, all committed at random during 180 s. With this in mind, it has been examined, and the connection between the transaction's timing, PEER, and ORG numbers has been depicted in Fig. 5. The time needed to dedicate the transactions likewise increases as PEER and ORG levels in the network rise.
Furthermore, our security analysis surpasses a simple assessment of the robustness of cryptographic mechanisms. It examines in detail how our hybrid signature scheme improves data security in the context of EHRs. The utilization of cryptographic protocols is an integral component of a multi-layered defense system, which guarantees the protection of patient data against both traditional threats and emergent quantum vulnerabilities.
Facilitating interoperability
Effective healthcare systems rely heavily on interoperability; blockchain technology has emerged as a catalyst for facilitating this vital process of data exchange. The implementation of our hybrid signature scheme, which adheres to blockchain principles, facilitates the development of interoperable electronic health records. This discourse highlights how the suggested framework functions as an intermediary, enabling secure and effective correspondence among diverse healthcare organizations, while simultaneously safeguarding the confidentiality and integrity of mutually disclosed patient data.
Resilience against quantum threats
Interoperability is crucial for efficient healthcare systems, and blockchain technology has emerged as a catalyst for easing this essential process of data interchange. Our hybrid signature technique, designed by blockchain principles, enables the creation of interoperable electronic health records. This discourse emphasizes how the proposed framework acts as a mediator, facilitating secure and efficient communication between various healthcare organizations, while also protecting the privacy and reliability of shared patient data.
Throughput
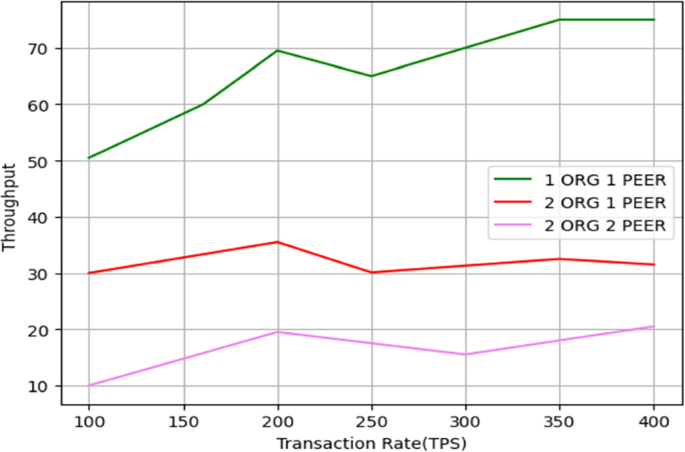
The throughput is measured in KB/sec or units of Data/Time. We evaluated the system's effectiveness when simulating the aforementioned number of users during the testing. These simulations are performed using the recommended framework, and throughput is evaluated at the end. The suggested system's throughput is depicted in Fig. 6 below. This experiment showed that as the number of transactions rose, the system's throughput significantly increased linearly.
The correlation between transaction rate and throughput is seen in Fig. 6. The 1ORG1PEER, which has a throughput of about 75 tps, provides a high throughput. The tips for 2ORG1PEER and 2ORG2PEER are reduced to 32 and 20, respectively. With this, we have looked at whether performance may benefit from higher latency.
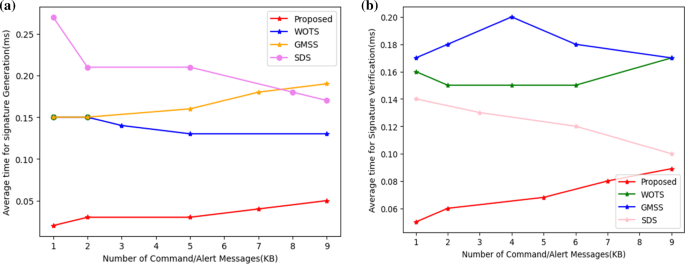
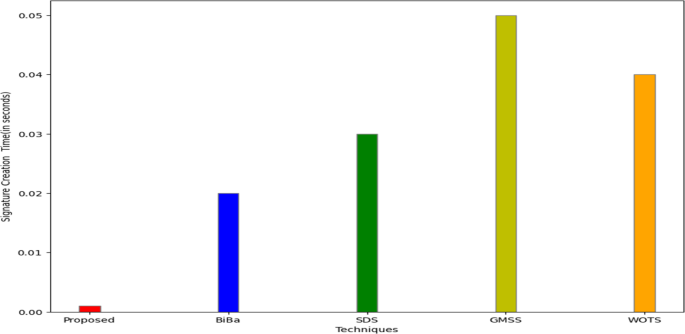
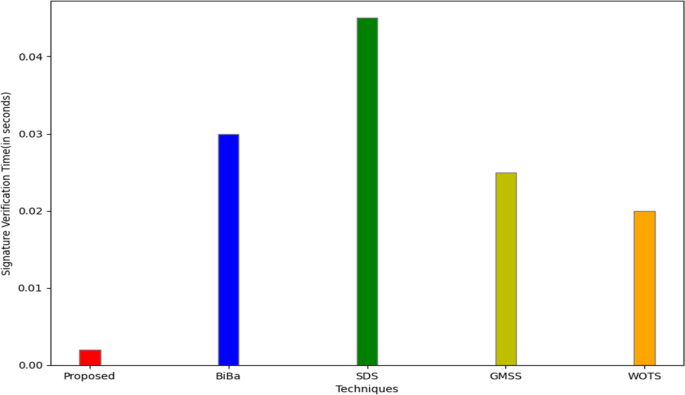
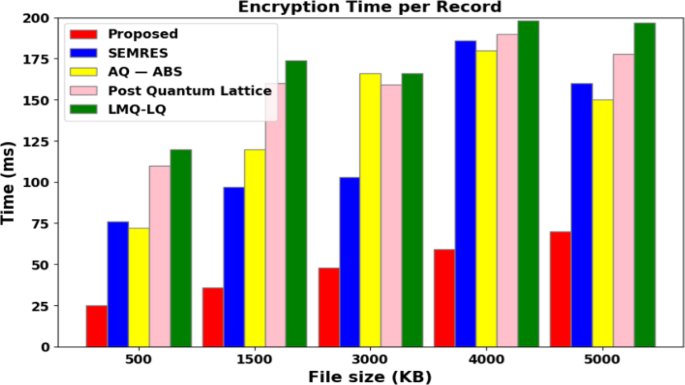
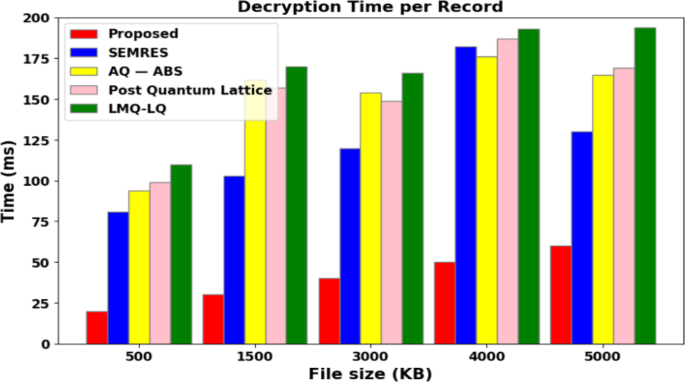
The average timings for the production and verification of signatures using conventional signature schemes, such as Smart Digital Signatures (SDS) [26], Generalized Merkle signature scheme (GMSS) [39], Winternitz One-Time Signature (WOTS) [40], and our method employing ECDSA-Dilithium with anti-quantum lattice-based blind signature, are shown in Figs. 7(a) and 7(b). These numbers unequivocally show that the suggested approach is effective and takes less time than conventional signature systems to generate and verify signatures. As a result, the suggested strategy is deployable over the actual smart grid network and is reasonably effective, efficient, and practicable.
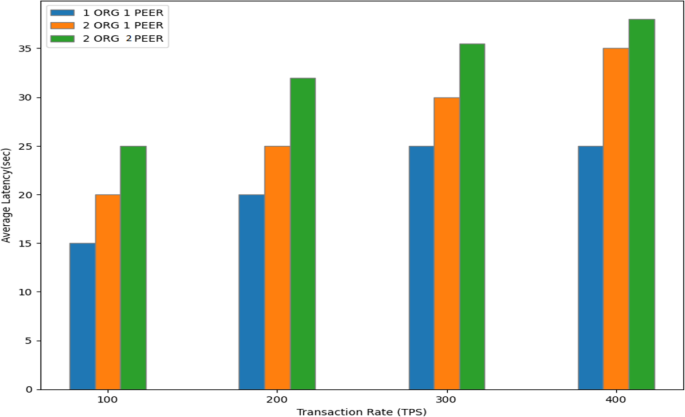
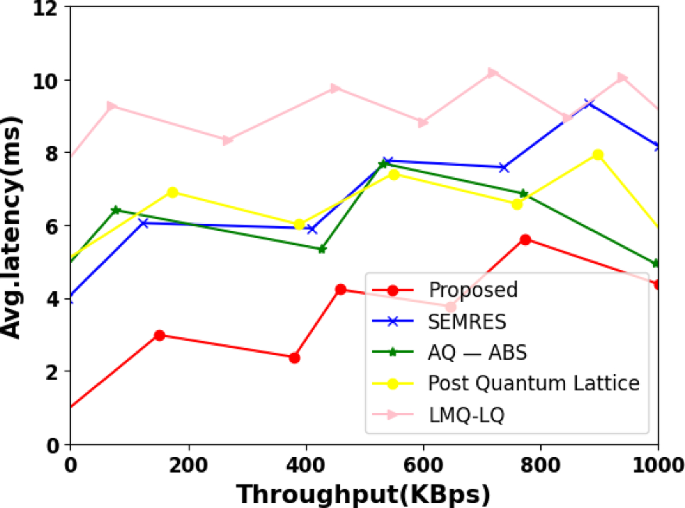
The correlation between average transaction delay and transaction rate is seen in Fig. 8. We have recorded that the 2ORG2PEER average maximum latency is 37 s, and the 2ORG1PEER average maximum latency is 35 s for a bigger network.
Latency is the interval of time between a request being made by one system component and a response being returned by another system component, as was previously mentioned. Latency is the difference between these two actions. Here, we have assessed the suggested framework's typical latency. We simulated some transactions to test the proposed framework's latency. Milliseconds are used to assess average latency.
Efficiency analysis
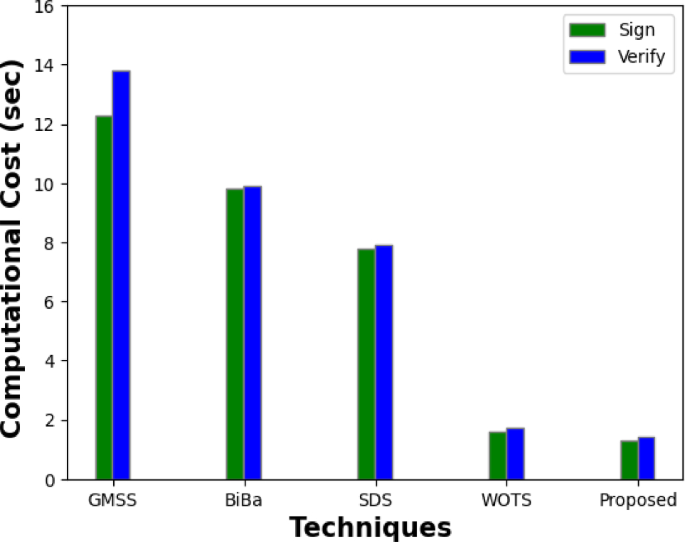
The technique broadens the lattice underneath the signature model, as seen in Fig. 9. This broadens the lattice's dimension in the signature. Although GMSS has produced signatures that are less costly and have stronger security models, there is always room for improvement. Strongly resistant to selection subring and adaptive selection message attacks, the new technique by BiBa has a lower overhead for signatures and verification than the earlier one. The cost of the WOTS plan is significantly less than that of the earlier plan. We have put out a plan to safeguard the message's unforgeability in systems and demonstrated very incomprehensible security under random models. The cost of signing and verification for our system is less than it is for the other four, as shown in Fig. 9. As a result, our plan ensures the privacy preservation system's effectiveness while also making sure it can withstand quantum assaults.
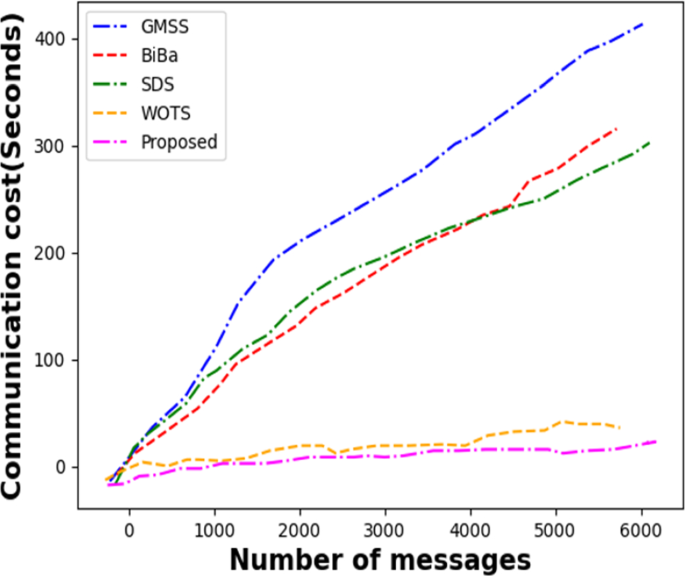
In Fig. 10, we simulate a comparison of the communication costs incurred when the system has received various numbers of messages and Specify a time interval between each user message number in the system between 0 and 6000. The GMSS proposal, which increases the dimension of the signature lattice while signing, comes at a high cost in terms of communication. BiBa's estimate of the cost of communication is somewhat greater than SDS's estimate. The SDS proposal, which addresses this issue, has less communication overhead and more steady development. As shown in Fig. 10, our suggested method for protecting system privacy when used is superior to WOTS. Our suggested technique has a reduced communication overhead with increased message volume compared to existing systems, therefore it won't cause system overload or come at a high cost.
Evaluation metrics
The suggested framework is evaluated based on its execution time, latency, and throughput metrics. Here is a brief explanation of these:
-
Execution Time is the amount of time (measured in seconds) that passes on the blockchain network between the confirmation of a transaction and its execution. Mathematically, it is \(\left(\mathit{max}(t{x}_{2})-\mathit{min}(t{x}_{1})\right.\)
-
Throughput is the maximum quantity of data that may be sent from one place to the next in a predetermined period.
-
Latency refers to the duration during which a system component is waiting for a response from another component after acting. One could say it's the distinction in time between when a transaction is initiated and when it is finished.
Compare to state of the art method
The suggested approach's execution time is comparable to that of the other signature systems. Figures 11, 12, and 13 enable comparing the proposed scheme's execution time to that of the alternative plans. Table 2 compares the traditional system and proposed in terms of security and efficiency.
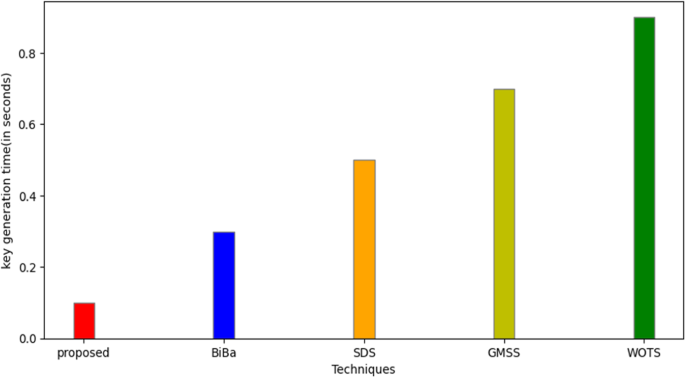
The results demonstrate that key generation, signing, and verifying signatures are three pretty effective techniques. In comparison to the current most compact BiBa, SDS, GMSS, and WOTS techniques, ECDSA and Dilithium signatures offer 80% and 75% faster key generation and signature generation speeds, respectively.
The improved effectiveness and capacity to handle larger workloads in our model are the result of a careful integration of cryptographic methods, including incorporating ECDSA, Dilithium, and the anti-quantum lattice-based blind signature. ECDSA enables the establishment of secure key pairs, the production of signatures, and the verification of data integrity, assuring the validity of transmitted information. Dilithium employs a lattice-based method to generate cryptographic keys, resulting in secret keys with high entropy and strong signatures that can withstand chosen message attacks. By including an anti-quantum lattice-based blind signature, the system is strengthened even more against any quantum risks. This hybrid signature system enhances the security of electronic health records and specifically tackles scaling concerns. The concept guarantees a more efficient and safe environment for healthcare data management by maximizing transaction throughput and reducing computing overhead. This integration exemplifies a refined strategy designed specifically to meet the unique demands of safeguarding electronic health information within the framework of blockchain technology, resulting in increased privacy and greater system performance. Figure 14 depicts a beneficial compromise between the pace at which data is processed and the time it takes for that data to be sent. With an increase in throughput, the average latency remains within an acceptable range. This demonstrates the scalability of our suggested method, highlighting its capacity to manage larger numbers of transactions without a substantial rise in processing time. When comparing our Proposed approach to other methods like SEMRES [41], AQ—ABS [42], Post Quantum Lattice [43], and LMQ-LQ [44], the graph demonstrates its superiority. Our technique achieves competitive throughput rates while maintaining decreased average latency, indicating its effectiveness in managing larger transaction loads.
Figure 15 illustrates the time required to update health records using both the traditional client/server approach and the innovative blockchain-based healthcare models. The time taken for execution is displayed for varying quantities of health records. The execution time for both client/server and blockchain models shows a direct correlation with the number of health records. As the number of records increases, the execution time also increases linearly. In contrast, the client/server model has a faster execution time when compared to blockchain. The blockchain utilizes a consensus mechanism to guarantee the validation and replication of data. The revised health record is distributed to all hospitals along with a duplicate of the ledger for verification. In addition, each peer node will distribute the block's hash to other peers in the network to collectively agree on its inclusion in the ledger. On the other hand, in the client/server approach, the hospital that stores the patient's information receives the request to update the data. Consequently, the execution time for the client/server is reduced in comparison to the blockchain method for updating health records. The client/server approach proves to be much more efficient than the blockchain platform when it comes to updating health records, with an average time reduction of 6.5 times.
Figure 16 provides a visual representation of the differences between the client/server and blockchain models when it comes to the amount of data transferred for updating health records as the number of records increases. The amount of data transferred in the blockchain platform exceeds that of the client/server network. The leader node sends health record update requests to all the peer nodes in the network, leading to a higher amount of data transfer. In addition, each peer node exchanges the block's hash with all other peers in the network, which improves data transfer. The blockchain model generally involves transferring a much larger amount of data compared to the client/server approach, with an average of 10 times more data being transferred.
Figure 17 shows a comparison of encryption time per record for different file sizes (ranging from 500 to 5000 KB). The performance of various encryption techniques, including our proposed model SEMRES, AQ—ABS, Post Quantum Lattice, and LMQ-LQ, is depicted. The time it takes to encrypt each record is a crucial factor when assessing the practicality of these techniques. The efficiency of our model is remarkable, as shown by its strong performance in the graph. The proposed technique demonstrates its ability to handle larger file sizes while maintaining a consistent encryption time, showcasing its scalability and adaptability to different data dimensions.
For our analysis of decryption time efficiency, we examined a range of file sizes from 500 to 5000 KB, as depicted in Fig. 18. The Proposed Hybrid Encryption Technique showed significant performance compared to other techniques such as SEMRES, AQ — ABS, Post Quantum Lattice, and LMQ-LQ. Our proposed model consistently demonstrated fast decryption times for healthcare records of all sizes, highlighting its effectiveness in quickly decrypting sensitive information.
Relationship between EHRs and the proposed hybrid signature scheme
1. Integration of EHRs: We have developed a hybrid signature scheme that can be easily integrated with existing EHR systems. This scheme takes advantage of decentralized and tamper-resistant blockchain technology to enhance security and reliability by integrating EHRs into the cryptographic infrastructure, a dynamic and secure environment is created for the management and sharing of sensitive medical information. Through this integration, every transaction related to patient records is securely signed using cryptography, creating an unchangeable record of data access and modifications.
2. Secure sharing: Our proposed scheme aims to enable authorized entities to securely share EHRs. The hybrid approach generates cryptographic signatures that act as digital attestations, confirming the authenticity and integrity of the shared records. Our system utilizes a decentralized and blockchain-based network to create a secure communication channel, effectively reducing the potential risks of unauthorized access, data breaches, or tampering. The secure sharing mechanism improves the collaborative nature of healthcare delivery while upholding strict data protection standards.
3. Privacy preservation: Preserving privacy is crucial when integrating EHRs with our hybrid signature scheme. The privacy-centric design is enhanced by the use of cryptographic techniques such as ECDSA and Dilithium. We have implemented a system that prioritizes the confidentiality of patient information, allowing access only to authorized entities possessing the necessary cryptographic keys. With the incorporation of anti-quantum lattice-based blind signatures, an extra level of privacy protection is introduced, enhancing the scheme's resistance against potential quantum threats.
Conclusions and future work
Patient information, such as their medical history, diagnosis, and treatments, is contained in electronic health records (EHRs). Therefore, it is crucial to guarantee that EHRs are safe and secure and are shielded from hacking or unauthorized access. The blockchain approach has the potential to transform the way we think about healthcare applications by enabling automated data gathering, third-party removal, a trustless apparatus, and data security. This study suggests an electronic health records (EHR) platform based on blockchain that guarantees privacy and security. This work suggested a hybrid signature system to defend against quantum attacks in quantum computers. ECDSA and Dilithium are two separate cryptographic signature schemes to give increased security and flexibility. The signature scheme provides a way for signers to create digital signatures that can be confirmed by anybody utilizing the public key of the signer, ensuring the validity, integrity, and non-repudiation of digital messages. Results indicate that in terms of security and effectiveness, our suggested method performs better than the ones already in use. Combining blockchain technology with other emerging technologies, like the Internet of Things (IoT), can help ensure the security of healthcare data in IoT-enabled healthcare infrastructure. Incorporating blockchain technology with artificial intelligence (AI) and deep learning (DL) can enhance the security and privacy of data in EHR systems. In future studies, we shall extend our approach to the diverse environment and handle the problems related to federated learning, cybersecurity, and health management [45,46,47].
Data availability
Not applicable.
References
Abunadi I, Kumar RL (2021) BSF-EHR: blockchain security framework for electronic health records of patients. Sensors 21(8):2865
Lee JS, Chew CJ, Liu JY, Chen YC, Tsai KY (2022) Medical blockchain: data sharing and privacy-preserving of EHR based on smart contract. J Inform Secur Appl 65:103117
Wang N, Chen J, Chen W, Shi Z, Yang H, Liu P, Li X (2022) The effectiveness of case management for cancer patients: an umbrella review. BMC Health Serv Res 22(1):1247. https://doi.org/10.1186/s12913-022-08610-1
Cai X, Geng S, Zhang J, Wu D, Cui Z, Zhang W, Chen J (2021) A sharding scheme-based many-objective optimization algorithm for enhancing security in blockchain-enabled industrial internet of things. IEEE Trans Industr Inf 17(11):7650–7658
Hu S, Chen W, Hu H, Huang W, Chen J, Hu J (2022) Coaching to develop leadership for healthcare managers: a mixed-method systematic review protocol. Syst Rev 11(1):67. https://doi.org/10.1186/s13643-022-01946-z
Mohammed MA, Lakhan A, Zebari DA, Abd Ghani MK, Marhoon HA, Abdulkareem KH, Martinek R (2024) Securing healthcare data in industrial cyber-physical systems using combining deep learning and blockchain technology. Eng Appl Artif Intell 129:107612
Mishra AR, Rani P, Alrasheedi AF, Dwivedi R (2023) Evaluating the blockchain-based healthcare supply chain using interval-valued Pythagorean fuzzy entropy-based decision support system. Eng Appl Artif Intell 126:107112
Liu Y, Fang Z, Cheung MH, Cai W, Huang J (2023) Mechanism design for blockchain storage sustainability. IEEE Commun Mag 61(8):102–107. https://doi.org/10.1109/MCOM.001.2200809
Li C, Dong M, Xin X, Li J, Chen X, Ota K (2023) Efficient privacy preserving in IoMT with blockchain and lightweight secret sharing. IEEE Internet Things J 10(24):22051–22064. https://doi.org/10.1109/JIOT.2023.3296595
Yang J, Yang K, Xiao Z, Jiang H, Xu S, Dustdar S (2023) Improving commute experience for private car users via blockchain-enabled multitask learning. IEEE Internet Things J 10(24):21656–21669. https://doi.org/10.1109/JIOT.2023.3317639
Tith D, Lee JS, Suzuki H, Wijesundara WMAB, Taira N, Obi T, Ohyama N (2020) Patient consent management by a purpose-based consent model for electronic health record based on blockchain technology. Healthc Inform Res 26(4):265–273
Fernandez-Carames TM, Fraga-Lamas P (2020) Towards post-quantum blockchain: a review on blockchain cryptography resistant to quantum computing attacks. IEEE access 8:21091–21116
Kumar GS, Premalatha K, Maheshwari GU, Kanna PR, Vijaya G, Nivaashini M (2024) Differential privacy scheme using Laplace mechanism and statistical method computation in deep neural network for privacy preservation. Eng Appl Artif Intell 128:107399
Lubis RK, Pardede AMH, Khair H (2023) Digital signature security analysis by applying the Elgamal algorithm and the idea method. J Artif Intell Eng Appl (JAIEA) 3(1):373–382
Zuo Y, Kang Z, Xu J, Chen Z (2021) BCAS: a blockchain-based ciphertext-policy attribute-based encryption scheme for cloud data security sharing. Int J Distrib Sens Netw 17(3):1550147721999616
Azzaoui AE, Sharma PK, Park JH (2022) Blockchain-based delegated quantum cloud architecture for medical big data security. J Netw Comput Appl 198:103304
Zhou Z, Wang M, Huang J, Lin S, Lv Z (2021) Blockchain in big data security for intelligent transportation with 6G. IEEE Trans Intell Transp Syst 23(7):9736–9746
Zhang Z, Ren X (2021) Data security sharing method based on CP-ABE and blockchain. J Intell Fuzzy Syst 40(2):2193–2203
Siva Kumar A, Godfrey Winster S, Ramesh R (2021) Efficient sensitivity orient blockchain encryption for improved data security in cloud. Concurr Eng 29(3):249–257
Lubis RK, Pardede AMH, Khair H (2023) Digital signature security analysis by applying the Elgamal algorithm and the idea method. J Artif Intell Eng Appl 3(1):373–382
Xie YY, Chen XB, Yang YX (2022) A new lattice-based blind ring signature for completely anonymous blockchain transaction systems. Secur Commun Netw 2022
Deng L, He X, Xia T (2021) Secure identity-based blind signature scheme for online transactions. Wirel Pers Commun 116:1525–1537
Yi H, Li Y, Wang M, Yan Z, Nie Z (2021) An efficient blockchain consensus algorithm based on post-quantum threshold signature. Big Data Res 26:100268
Quan Y (2022) Improving Bitcoin’s post-quantum transaction efficiency with a novel lattice-based aggregate signature scheme based on CRYSTALS-dilithium and a STARK protocol. IEEE Access 10:132472–132482
Johari R, Kumar V, Gupta K, Vidyarthi DP (2022) BLOSOM: BLOckchain technology for Security of Medical records. ICT Express 8(1):56–60
Shahid F, Khan A (2020) Smart digital signatures (SDS): a post-quantum digital signature scheme for distributed ledgers. Fut Gen Comput Syst 111:241–253
Lee JS, Chew CJ, Liu JY, Chen YC, Tsai KY (2022) Medical blockchain: data sharing and privacy preserving of EHR based on smart contract. J Inform Secur Appl 65:103117
Mishra R, Ramesh D, Edla DR, Qi L (2022) DS-Chain: a secure and auditable multi-cloud assisted EHR storage model on efficient deletable blockchain. J Ind Inf Integr 26:100315
Li C, Tian Y, Chen X, Li J (2021) An efficient anti-quantum lattice-based blind signature for blockchain-enabled systems. Inf Sci 546:253–264
Qu Z, Zhang Z, Zheng M (2022) A quantum blockchain-enabled framework for secure private electronic medical records in Internet of Medical Things. Inf Sci 612:942–958
Narayanan U, Paul V, Joseph S (2021) Decentralized blockchain based authentication for secure data sharing in Cloud-IoT: DeBlock-Sec. J Ambient Intell Hum Comput:1–19
Yaseen M, Mahadi B, Omar AH (2021) Blockchain technology applications, concerns and recommendations for public sector. Mesopotamian J Comput Sci 2021:1–6. https://doi.org/10.58496/MJCSC/2021/001
Abdulrahman S, Useng M (2022) Blockchain and distributed ledger technologies for IoT security: a survey paper. Mesopotamian J Comput Sci 2022:5–8. https://doi.org/10.58496/MJCSC/2022/006
Cao B, Wang X, Zhang W, Song H, Lv Z (2020) A many-objective optimization model of industrial internet of things based on private blockchain. IEEE Netw 34(5):78–83. https://doi.org/10.1109/MNET.011.1900536
Huang Y, Xu G, Song X (2022) An improved efficient identity-based quantum signature scheme. Quant Inf Process 22(1):36
Mehbodniya A, Webber JL, Neware R, Arslan F, Pamba RV, Shabaz M (2022) Modified lamport merkle digital signature blockchain framework for authentication of internet of things healthcare data. Expert Syst 39(10):e12978
Oudah MS, Maolood AT (2022). Lightweight authentication model for IoT environments based on enhanced elliptic curve digital signature and shamir secret share. Int J Intell Eng Syst15(5)
Yi H (2023) Machine learning method with applications in hardware security of post-quantum cryptography. J Grid Comput 21(2):19
Babu VJ, Jose MV (2020) Improved merkle hash tree-based one-time signature scheme for capability-enhanced security enforcing architecture for named data networking. Wireless Pers Commun 115:557–574
Oraei H, Dehkordi MH (2022) A new variant of the winternitz one time signature based on graded encoding schemes. ISeCure 14(1)
Lee YL, Lee HA, Hsu CY, Kung HH, Chiu HW (2022) SEMRES-A triple security protected blockchain based medical record exchange structure. Comput Methods Programs Biomed 215:106595
Chen X, Xu S, Qin T, Cui Y, Gao S, Kong W (2022) AQ–ABS: anti-quantum attribute-based signature for EMRs sharing with blockchain. In: 2022 IEEE Wireless Communications and Networking Conference (WCNC) (pp. 1176–1181). IEEE
Yu H, Bai L (2021) Post-quantum blind signcryption scheme from lattice. Front Inform Technol Electron Eng 22(6):891–901
Makkar GD, Semwal P, Sharma HC, Kero A, Arora M, Sharma V (2022) Smart healthcare system using post quantum technique and blockchain. NeuroQuantology 20(8):6901
Han S, Ding H, Zhao S, Ren S, Wang Z, Lin J, Zhou S (2023) Practical and robust federated learning with highly scalable regression training. IEEE Trans Neural Netw Learn Syst. https://doi.org/10.1109/TNNLS.2023.3271859
Bala IM, Mijwil M, Ali G, Sadıkoğlu E (2023) Analysing the connection between AI and industry 4.0 from a cybersecurity perspective: defending the smart revolution. Mesopotamian J Big Data 2023:61–67. https://doi.org/10.58496/MJBD/2023/009
Hu S, Chen W, Hu H, Huang W, Chen J, Hu J (2022) Coaching to develop leadership for healthcare managers: a mixed-method systematic review protocol. Syst Rev 11(1):67. https://doi.org/10.1186/s13643-022-01946-z
Acknowledgements
This study is supported via funding from Prince Sattam bin Abdulaziz University project number (PSAU/2024/R/1445)
Funding
This research received no external funding.
Author information
Authors and Affiliations
Contributions
All authors contributed equally and have read and agreed to the published version of the manuscript.
Corresponding authors
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Alsubai, S., Alqahtani, A., Garg, H. et al. A blockchain-based hybrid encryption technique with anti-quantum signature for securing electronic health records. Complex Intell. Syst. (2024). https://doi.org/10.1007/s40747-024-01477-1
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s40747-024-01477-1