
Newly discovered side-channel attack side steps current defense mechanisms
By Ryan Noone
Data compression has long been a technique employed to enhance web performance and the user experience. The process reduces the size of files and resources, such as images, video, and text, before they are transmitted over the internet, significantly reducing the amount of data being transferred and offering faster load times. However, over the years, data compression has become a well-known source of side-channel attacks, capable of leaking users’ personal information to potential adversaries.
In most previously known side-channel attacks, data leaks occur because of software-visible uses of compression. But in a recent study, co-authored by Carnegie Mellon Software and Societal Systems Assistant Professor Riccardo Paccagnella, he and fellow researchers have uncovered a new type of side-channel attack, dubbed GPU.zip which exploits software-transparent uses of compression. With this unique approach, GPU.zip side steps current side-channel attack defense mechanisms.
“If a user visits a malicious website, GPU.zip enables adversaries to extract pixels from iframes within the site,” said Paccagnella. “Once the attack is finished, the adversary is left with what’s essentially a screenshot of the content rendered within the target iframe.”
In their paper, ‘GPU.zip: On the Side-Channel Implications of Hardware-Based Graphical Data Compression,” the researchers share a proof-of-concept for a realistic attack by “stealing” a username from Wikipedia. The figure below shows the results of their attack on an Intel i7-8700 and an AMD Ryzen 7 4800U. Although their attack was unoptimized, it was completed in just 30 minutes on the AMD Ryzen with 97 percent accuracy. The Intel i7 attack was significantly slower, taking 215 minutes, but saw an accuracy rate of 98.3 percent.
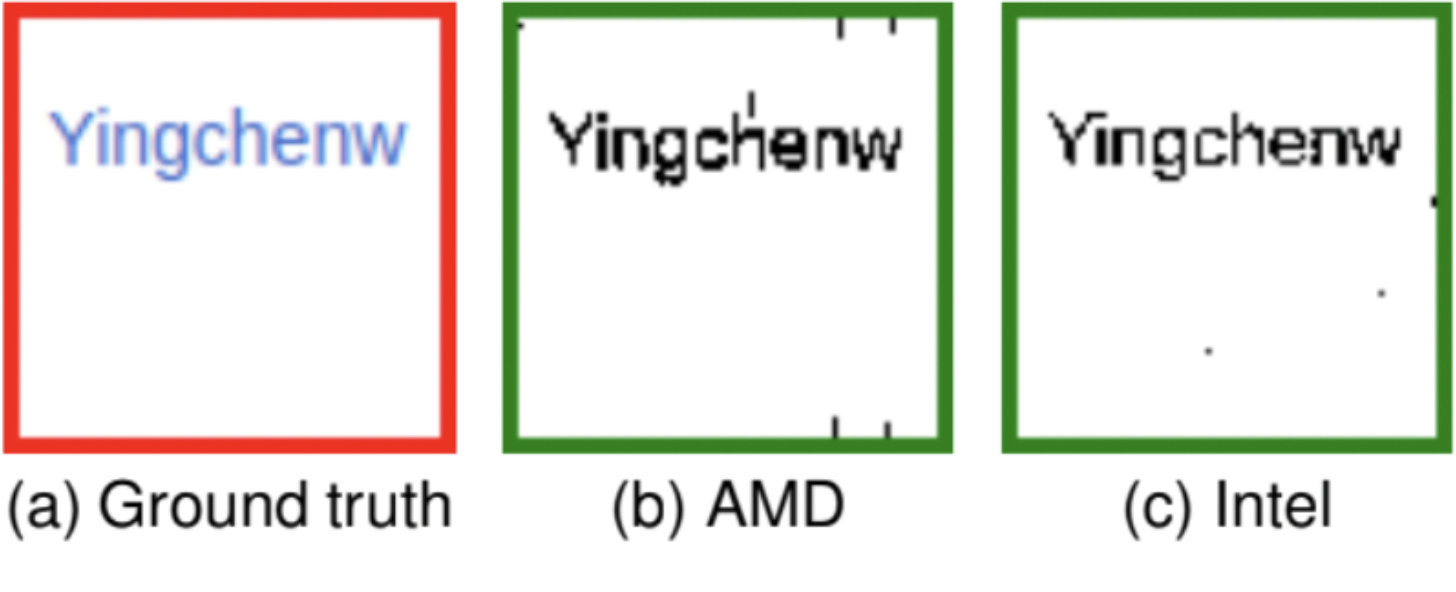
Results of researchers proof of concept attack using GPU.zip. Figure A shows the ground truth, or the way the information was displayed on Wikipedia. Figures B and C show the results of the pixel-stealing attack on an AMD Ryzen 7 and Intel i7.