Configure user security in an environment
Microsoft Dataverse uses a role-based security model to control access to a database and its resources in an environment. Use security roles to configure access to all resources in an environment or to specific apps and data in the environment. A combination of access levels and permissions in a security role determines which apps and data users can view and how they can interact with those apps and data.
An environment can have no or one Dataverse database. You assign security roles differently for environments that have no Dataverse database and environments that have a Dataverse database.
Learn more about environments in Power Platform.
Predefined security roles
Environments include predefined security roles that reflect common user tasks. The predefined security roles follow the security best practice of "minimum required access": provide the least access to the minimum business data that a user needs to use an app. These security roles can be assigned to a user, owner team, and group team. The predefined security roles that are available in an environment depend on the environment type and the apps you have installed in it.
Another set of security roles is assigned to application users. Those security roles are installed by our services and can't be updated.
Environments without a Dataverse database
Environment Maker and Environment Admin are the only predefined roles for environments that have no Dataverse database. These roles are described in the following table.
| Security role | Description |
|---|---|
| Environment Admin | The Environment Admin role can perform all administrative actions on an environment, including:
|
| Environment Maker | Can create new resources associated with an environment, including apps, connections, custom APIs, and flows using Microsoft Power Automate. However, this role doesn't have privileges to access data in an environment. Environment makers can also distribute the apps they build in an environment to other users in your organization. They can share the app with individual users, security groups, or all users in the organization. |
Environments with a Dataverse database
If the environment has a Dataverse database, a user must be assigned the System Administrator role instead of the Environment Admin role to have full admin privileges.
Users who make apps that connect to the database and need to create or update entities and security roles must have the System Customizer role in addition to the Environment Maker role. The Environment Maker role doesn't have privileges on the environment's data.
The following table describes the predefined security roles in an environment that has a Dataverse database. You can't edit these roles.
| Security role | Description |
|---|---|
| App Opener | Has minimum privileges for common tasks. This role is primarily used as a template to create a custom security role for model-driven apps. It doesn't have any privileges to the core business tables, such as Account, Contact, and Activity. However, it has Organization-level read access to system tables, such as Process, to support reading system-supplied workflows. Note that this security role is used when a new, custom security role is created. |
| Basic User | For out-of-the-box entities only, can run an app in the environment and perform common tasks on the records they own. It has privileges to the core business tables, such as Account, Contact, and Activity. Note: The Common Data Service User security role was renamed Basic User. Only the name was changed; user privileges and role assignment are the same. If you have a solution with the Common Data Service User security role, you should update the solution before you import it again. Otherwise, you might inadvertently change the security role name back to User when you import the solution. |
| Delegate | Allows code to impersonate, or run as, another user. Typically used with another security role to allow access to records. |
| Dynamics 365 Administrator | Dynamics 365 administrator is a Microsoft Power Platform service admin role. This role can do admin functions on Microsoft Power Platform because they have the system administrator role. |
| Environment Maker | Can create new resources associated with an environment, including apps, connections, custom APIs, and flows using Microsoft Power Automate. However, this role doesn't have any privileges to access data in an environment. Environment makers can also distribute the apps they build in an environment to other users in your organization. They can share the app with individual users, security groups, or all users in the organization. |
| Global Administrator | Global administrator is a Microsoft 365 administrator role. A person who purchases the Microsoft business subscription is a global administrator and has unlimited control over products in the subscription and access to most data. |
| Global Reader | The Global Reader role isn't supported yet in the Power Platform admin center. |
| Office Collaborator | Has Read permission to tables in which a record was shared with the organization. Doesn't have access to any other core and custom table records. This role is assigned to the Office Collaborators owner team and not to an individual user. |
| Power Platform administrator | Power Platform administrator is a Microsoft Power Platform service administrator role. This role can perform admin functions on Microsoft Power Platform because they have the system administrator role. |
| Service Deleted | Has full Delete permission to all entities, including custom entities. This role is primarily used by the service and requires deleting records in all entities. This role can't be assigned to a user or team. |
| Service Reader | Has full Read permission to all entities, including custom entities. This role is primarily used by the service and requires reading all entities. This role can't be assigned to a user or team. |
| Service Writer | Has full Create, Read, and Write permission to all entities, including custom entities. This role is primarily used by the service and requires creating and updating records. This role can't be assigned to a user or team. |
| Support User | Has full Read permission to customization and business management settings, which allow support staff to troubleshoot environment configuration issues. This role doesn't have access to core records. This role can't be assigned to a user or team. |
| System Administrator | Has full permission to customize or administer the environment, including creating, modifying, and assigning security roles. Can view all data in the environment. |
| System Customizer | Has full permission to customize the environment. Can view all custom table data in the environment. However, users with this role can only view records that they create in Account, Contact, Activity tables. |
| Website App Owner | A user who owns the website application registration in the Azure portal. |
| Website Owner | The user who created the Power Pages website. This role is managed and can't be changed. |
In addition to the predefined security roles described for Dataverse, other security roles might be available in your environment depending on the Power Platform components—Power Apps, Power Automate, Power Virtual Agents—you have. The following table provides links to more information.
| Power Platform component | Information |
|---|---|
| Power Apps | Predefined security roles for environments with a Dataverse database |
| Power Automate | Security and privacy |
| Power Pages | Roles required for website administration |
| Power Virtual Agents | Assign environment security roles |
Dataverse for Teams environments
Learn more about predefined security roles in Dataverse for Teams environments.
App-specific security roles
If you deploy Dynamics 365 apps in your environment, other security roles are added. The following table provides links to more information.
| Dynamics 365 app | Security role docs |
|---|---|
| Dynamics 365 Sales | Predefined security roles for Sales |
| Dynamics 365 Marketing | Security roles added by Dynamics 365 Marketing |
| Dynamics 365 Field Service | Dynamics 365 Field Service roles + definitions |
| Dynamics 365 Customer Service | Roles in Omnichannel for Customer Service |
| Dynamics 365 Customer Insights | Customer Insights roles |
| App profile manager | Roles and privileges associated with app profile manager |
| Dynamics 365 Finance | Security roles in the public sector |
| Finance and operations apps | Security roles in Microsoft Power Platform |
Summary of resources available to predefined security roles
The following table describes which resources each security role can author.
| Resource | Environment Maker | Environment Admin | System Customizer | System Admin |
|---|---|---|---|---|
| Canvas app | X | X | X | X |
| Cloud flow | X (non–solution-aware) | X | X | X |
| Connector | X (non–solution-aware) | X | X | X |
| Connection* | X | X | X | X |
| Data gateway | - | X | - | X |
| Dataflow | X | X | X | X |
| Dataverse tables | - | - | X | X |
| Model-driven app | X | - | X | X |
| Solution framework | X | - | X | X |
| Desktop flow** | - | - | X | X |
| AI Builder | - | - | X | X |
*Connections are used in canvas apps and Power Automate.
**Dataverse for Teams users don't get access to desktop flows by default. You need to upgrade your environment to full Dataverse capabilities and acquire desktop flow license plans to use desktop flows.
Assign security roles to users in an environment that has no Dataverse database
For environments with no Dataverse database, a user who has the Environment Admin role in the environment can assign security roles to individual users or groups from Microsoft Entra ID.
Sign in to the Power Platform admin center.
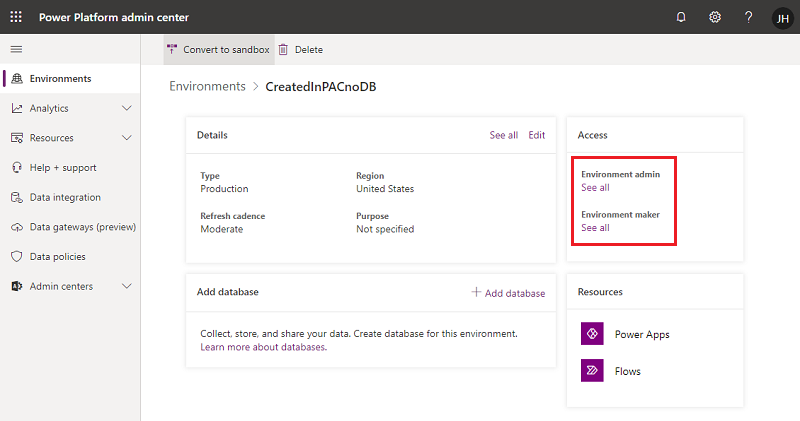
Select Environments > [select an environment].
In the Access tile, select See all for Environment admin or Environment maker to add or remove people for either role.
Select Add people, and then specify the name or email address of one or more users or groups from Microsoft Entra ID.
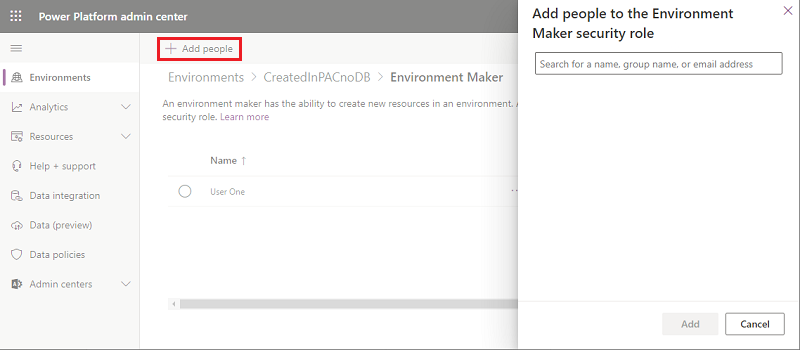
Select Add.
Assign security roles to users in an environment that has a Dataverse database
Security roles can be assigned to individual users, owner teams, and Microsoft Entra group teams. Before you assign a role to a user, verify the user's account has been added to and is enabled in the environment.
In general, a security role can only be assigned to users whose accounts are enabled in the environment. To assign a security role to a user account that's disabled in the environment, turn on allowRoleAssignmentOnDisabledUsers in OrgDBOrgSettings.
Sign in to the Power Platform admin center.
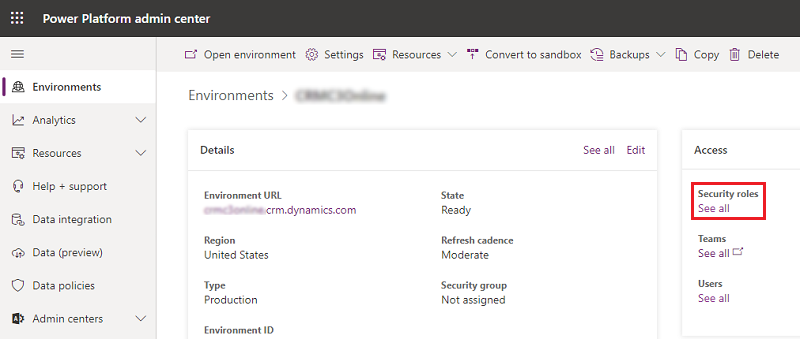
Select Environments > [select an environment].
In the Access tile, select See all under Security roles.
Make sure the correct business unit is selected in the list, and then select a role from the list of roles in the environment.
Select Add people, and then specify the name or email address of one or more users or groups from Microsoft Entra ID.
Select Add.
Create, edit, or copy a security role using the new, modern UI
You can easily create, edit, or copy a security role and customize it to meet your needs.
Go to the Power Platform admin center, select Environments in the navigation pane, and then select an environment.
Select Settings.
Expand Users + Permissions.
Select Security roles.
Complete the appropriate task:
Create a security role
Select New role from the command bar.
In the Role Name field, enter a name for the new role.
In the Business unit field, select the business unit the role belongs to.
Select whether team members should inherit the role.
If this setting is enabled and the role is assigned to a team, all team members inherit all the privileges associated with the role.
Select Save.
Edit a security role
Either select the role name or select the row and then select Edit. Then define the privileges and properties of the security role.
Some predefined security roles can't be edited. If you try to edit these roles, the Save and Save + Close buttons aren't available.
Copy a security role
Select the security role and then select Copy. Give the role a new name. Edit the security role as needed.
Only the privileges are copied, not any assigned members and teams.
Audit security roles
Audit security roles to better understand changes made to security in your Power Platform environment.
Create or configure a custom security role
If your app uses a custom entity, its privileges must be explicitly granted in a security role before your app can be used. You can either add these privileges in an existing security role or create a custom security role.
Every security role must include a minimum set of privileges. Learn more about security roles and privileges.
Tip
The environment might maintain records that can be used by multiple apps. You might need multiple security roles that grant different privileges. For example:
- Some users (call them Editors) might only need to read, update, and attach other records, so their security role will have read, write, and append privileges.
- Other users might need all the privileges that Editors have plus the ability to create, append to, delete, and share. The security role for these users will have create, read, write, append, delete, assign, append to, and share privileges.
Create a custom security role with minimum privileges to run an app
Sign in to the Power Platform admin center, select Environments in the navigation pane, and then select an environment.
Select Settings > Users + permissions > Security roles.
Select the App Opener role, and then select Copy.
Enter the name of the custom role, and then select Copy.
In the list of security roles, select the new role, and then select More actions (…) > Edit.
In the role editor, select the Custom Entities tab.
Find your custom table in the list, and select the Read, Write, and Append privileges.
Select Save and Close.
Create a custom security role from scratch
Sign in to the Power Platform admin center, select Environments in the navigation pane, and then select an environment.
Select Settings > Users + permissions > Security roles.
Select New role.
Enter the name of the new role on the Details tab.
On the other tabs, find your entity and then select actions and the scope for performing them.
Select a tab, and search for your entity. For example, select the Custom Entities tab to set permissions on a custom entity.
Select the privileges Read, Write, Append.
Select Save and Close.
Minimum privileges to run an app
When you create a custom security role, the role must have a set of minimum privileges for a user to run an app. Learn more about required minimum privileges.
See also
Grant users access
Control user access to environments: security groups and licenses
How access to a record is determined
Feedback
Coming soon: Throughout 2024 we will be phasing out GitHub Issues as the feedback mechanism for content and replacing it with a new feedback system. For more information see: https://aka.ms/ContentUserFeedback.
Submit and view feedback for