Role-based access control (RBAC) in 2024


We adhere to clear ethical standards and follow an objective methodology. The brands with links to their websites fund our research.
Network security statistics show that ~65% of surveyed companies have 1,000+ high-value files available to each employee.
Organizations can leverage role-based access control (RBAC) by assigning permissions to users based on their role within an organization to
- enhance granular control and network visibility
- and limit network access to protect their data.
See a step-by-step guide explaining how RBAC works, and how organizations can use it to protect their network security against the most common cyber attack vectors.
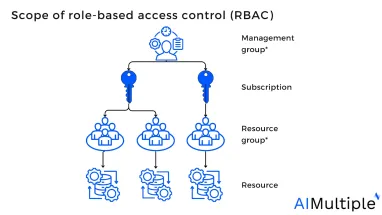
What is Role-based access control (RBAC)?
Role-based access control (RBAC) is controlling network accessibility depending on the authority of each user within an organization. For example, security teams can use open source RBAC tools to define access controls based on user roles and permissions.
Figure: Role relationship

Source: Ferraiolo, D.F.; Kuhn, D.R.1
Read more: RBAC use cases, RBAC examples.
4 types of role-based access control
1. Core: The core model defines the key components of any role-based access control system. Core RBAC follows three rules:
1.1 A user can only work at a job if they have been allocated a role entailed with that job function.
1.2 An administration has to assign a certain role(s) to a particular user.
1.3 A user can only have access to a certain job if their role is related to that job.
2. Hierarchical: Hierarchical role-based access control establishes linkages between roles (e.g., senior, mid-level, junior) by using a hierarchy inside the role framework. Authorized users with senior positions in hierarchical RBAC can allow all of their juniors’ permissions along with their requirements.
3. Constrained: Constrained RBAC enhances the core model’s assignment of roles by enabling administrators to separate roles that are classified as static and dynamic.
- Static: A single user under Static Separation of Duty (SSD) cannot hold mutually exclusive roles. This eliminates discretionary access control, for example, one person cannot concurrently request and approve an expenditure.
- Dynamic: A user under the Dynamic Separation of Duty (DSD) model can have opposite roles. However, the user may not perform both tasks in the same session.
4. Symmetric: Administrators can undertake both permission-role and user-role assessments using symmetric RBAC control.
RBAC permissions

When assigning user permissions, organizations can determine the type of permission assigned for each user by customizing what each position should accomplish when using role-based access control.
Access
- Which users have access to a certain object, such as a file, program, or database?
- Which users need to be notified of the accessibility of specific resources?
- What restrictions should be imposed on visibility?
Customization
- Which users can make adjustments to particular items?
- What authorizations are necessary to make adjustments?
Sharing
- Who may download a file?
- Which users can share a file?
Example: The following table shows the authorization levels for three roles: senior writer, writer, and reader.
Table: Role-based access control table designed for article-writing software
| Role | Senior writer | Writer | Reader | |
|---|---|---|---|---|
| Edit | ✅ | ✅ | ✖ | |
| Delete | ✅ | ✖ | ✖ | |
| Read | ✅ | ✅ | ✅ |
RBAC implementation
Demonstration of RBAC script in ASP.NET Core
In this example, RBAC controls entail granting authorization to specify which roles. Initially, security teams may define a user login & ID to assess permissions. Thus, they can create an application registration script to define roles:
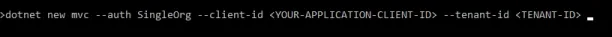
- The code uses the .NET command to develop a new web application. The script helps the web application decide if the user can log into the application. More specifically:
- “–client-id” notices if the user is from an application login,
- and “–tenant-id” notices if the user is from a non-application login.
Adding role-based authorization in ASP.NET
When a user is formed, it may be assigned to several roles. Bert, for example, may have both the Administrator and User roles, whereas Emma might only have the User role.
Multiple roles (HRManager, Finance) can be assigned in a comma-separated list. For example, users with the –HRManager or –Finance roles can have access to the –SalaryController role.
Figure: Adding roles to employees in ASP.NET Core

Source: Microsoft2
Additionally, multiple access restrictions can be assigned to one user. For example, one user can be granted for both the –PowerUser and –ControlPanelUser roles:
Figure: Adding action-level roles to employees in ASP.NET Core

Source: Microsoft3
Benefits of RBAC
Enhanced operational efficiency: Companies can use RBAC to reduce the need for documentation and password changes when hiring freshers or changing the responsibilities of current employees.
Decreased risk of data breaches: Employing RBAC involves formulating security risk assessment and limiting access to private data, and lowering the risk of data breaches or leaking.
Improved data protection: RBAC follows the rule of least privilege, a fundamental concept of zero-trust architecture, which states that a user is only provided the user privileges necessary to do their job. By regulating access in this way, companies may eliminate unwanted dangers and the possibility of data breaches.
More control over regulatory compliance: Using pre-determined role structures improves visibility, supervision, and auditing. Administrators can discover and remedy errors in user permissions, enabling improved regulatory data compliance (HIPAA, GDPR, SOX, SOC 2, and ISO 27001).
Streamlines workflows: With RBAC Employees will no longer be required to contact administrators for access to information and systems, and IT can become free of the burden of managing one-time authorization for each user.
For example, RBAC can provision tasks such as onboarding and offboarding. Administrators may leverage fine-grained access control such as granular access controls by customizing permissions for current employees who change responsibilities within the business.
Increased network visibility: RBAC provides a scope of network activities (an overview of who has access to what they need to execute their tasks) so that administrators and managers will have improved insights and visibility into the organization.
For guidance on choosing the right tool or service for your project, check out our data-driven lists of software-defined perimeter (SDP) software and zero trust networking software.
Further reading
- Top 10 Microsegmentation Tools
- Top 10 Insider Threat Management Software
- Microsegmentation: What is it? Benefits & Challenges
- Zero Trust Network Access (ZTNA): Definition & Benefits
- 10 Cybersecurity Best Practices for Corporations
External links
External Links
- 1. “Role-Based Access Control” (PDF). October 1992. Retrieved December 27, 2023.
- 2. “Role-based authorization in ASP.NET Core“. Microsoft. July 14, 2023. Retrieved December 27, 2023.
- 3. “Role-based authorization in ASP.NET Core“. Microsoft. July 14, 2023. Retrieved December 27, 2023.

Cem's work has been cited by leading global publications including Business Insider, Forbes, Washington Post, global firms like Deloitte, HPE and NGOs like World Economic Forum and supranational organizations like European Commission. You can see more reputable companies and resources that referenced AIMultiple.
Throughout his career, Cem served as a tech consultant, tech buyer and tech entrepreneur. He advised enterprises on their technology decisions at McKinsey & Company and Altman Solon for more than a decade. He also published a McKinsey report on digitalization.
He led technology strategy and procurement of a telco while reporting to the CEO. He has also led commercial growth of deep tech company Hypatos that reached a 7 digit annual recurring revenue and a 9 digit valuation from 0 within 2 years. Cem's work in Hypatos was covered by leading technology publications like TechCrunch and Business Insider.
Cem regularly speaks at international technology conferences. He graduated from Bogazici University as a computer engineer and holds an MBA from Columbia Business School.
Comments
Your email address will not be published. All fields are required.