Introduction
In this post and accompanying video, we review Role-Based Access Control (RBAC) roles, exploring what they are and how they play a crucial role in managing access within Microsoft Entra ID and Azure. This high-level overview aims to give you a fundamental understanding of this concept in the context of Microsoft’s cloud services.
Authentication vs. Authorization
We start with distinguishing authentication and authorization. Authentication is the process of proving an identity, whether it’s a person, group, device, or other security principles. Authentication in technology usually includes usernames, passwords, and another form of authentication with multi-factor authentication, or MFA.
On the other hand, authorization grants authenticated identities the permission to perform specific actions. Authorization provides permissions to sign into services like Exchange Online and is how administrators get rights to manage Azure resources. With Microsoft cloud services, authentication and authorization are managed by Entra ID but are two distinct activities.
Microsoft Entra RBAC Roles
Authorization within Entra ID involves RBAC roles. Entra ID, formerly known as Azure AD, serves as the identity platform for Azure and Microsoft 365 online products such as Exchange, SharePoint Online, and Intune. Each instance of Entra ID is referred to as a Tenant, representing an organization in Microsoft cloud services.
Once identities are established in Entra ID, RBAC roles are applied. There are two types of RBAC roles: Microsoft Entra roles and Azure roles. Microsoft Entra roles apply at the tenant level and control access to Entra ID resources through the Graph API. These roles can be assigned to users, groups, or other security principles, offering a range of permissions, from Global admin to Exchange administrator and license administrator.
Azure RBAC Roles
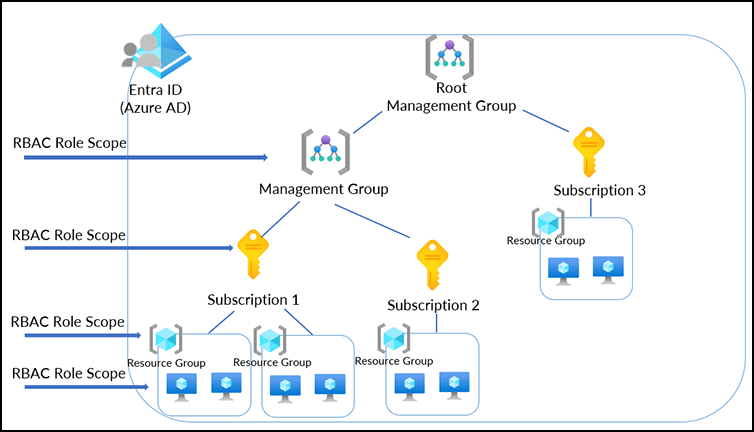
Azure RBAC roles are custom and built-in roles used to manage access to Azure resources. Azure Roles are assigned to security principles (users, groups, service principles, or managed identities) at a specific scope. This scope can range from a single VM to a management group, subscription, resource group, or individual resource. All resources inherit RBAC roles assigned at a higher scope under that scope. There is an option to deny an assignment if needed.
The granular nature of Azure RBAC allows for precise control. For instance, assigning the Virtual Machine Contributor role to a managed identity at the VM level limits its rights to that specific VM. Expanding the scope to a resource group extends those rights to all VMs within the resource group. Apply the role to the managed identity at the subscription scope and all resources in the subscription inherit the permissions. The same is true with management groups.
Common RBAC Role Mistakes and Solutions
Next, we address one of the most common RBAC role issues. In Entra ID, the Global Admin holds the highest level of access and can modify permissions. In Azure, the owner role has the most rights, including the right to manage permissions. The mistake occurs when people grant Global Admin rights to gain access to Azure subscriptions. The Global Admin role can only be scoped to the Entra ID directory, not a subscription. Granting improper permissions can lead to unnecessary access in Entra ID, posing potential security risks.
One cause of this confusion is the default settings when creating a new Azure subscription and Entra ID tenant. The default behavior is to provide the account that created the subscription with the Global Admin role in Entra ID and Subscription Owner in Azure. This can make it seem that the global admin account has rights to all resources and services in the tenant and Azure.

One item to note: Users with the Global Admin Entra ID role can grant themselves Subscription Owner rights by enabling the “access management for Azure resources” permissions in Entra ID. That setting gives the Global Admin account rights to modify permissions in the tenant’s Azure subscriptions, including giving themselves the Owner role. This is why accounts with the Global Admin role should be tightly controlled.
Conclusion
In conclusion, Microsoft Entra and Azure roles are pivotal in managing access within their respective scopes. Understanding RBAC roles is essential for effectively navigating Microsoft Entra and Azure environments. I hope this overview has clarified the fundamentals and will assist you in better managing access in your cloud environment.




