Trusted by Industry Leaders
The Problem
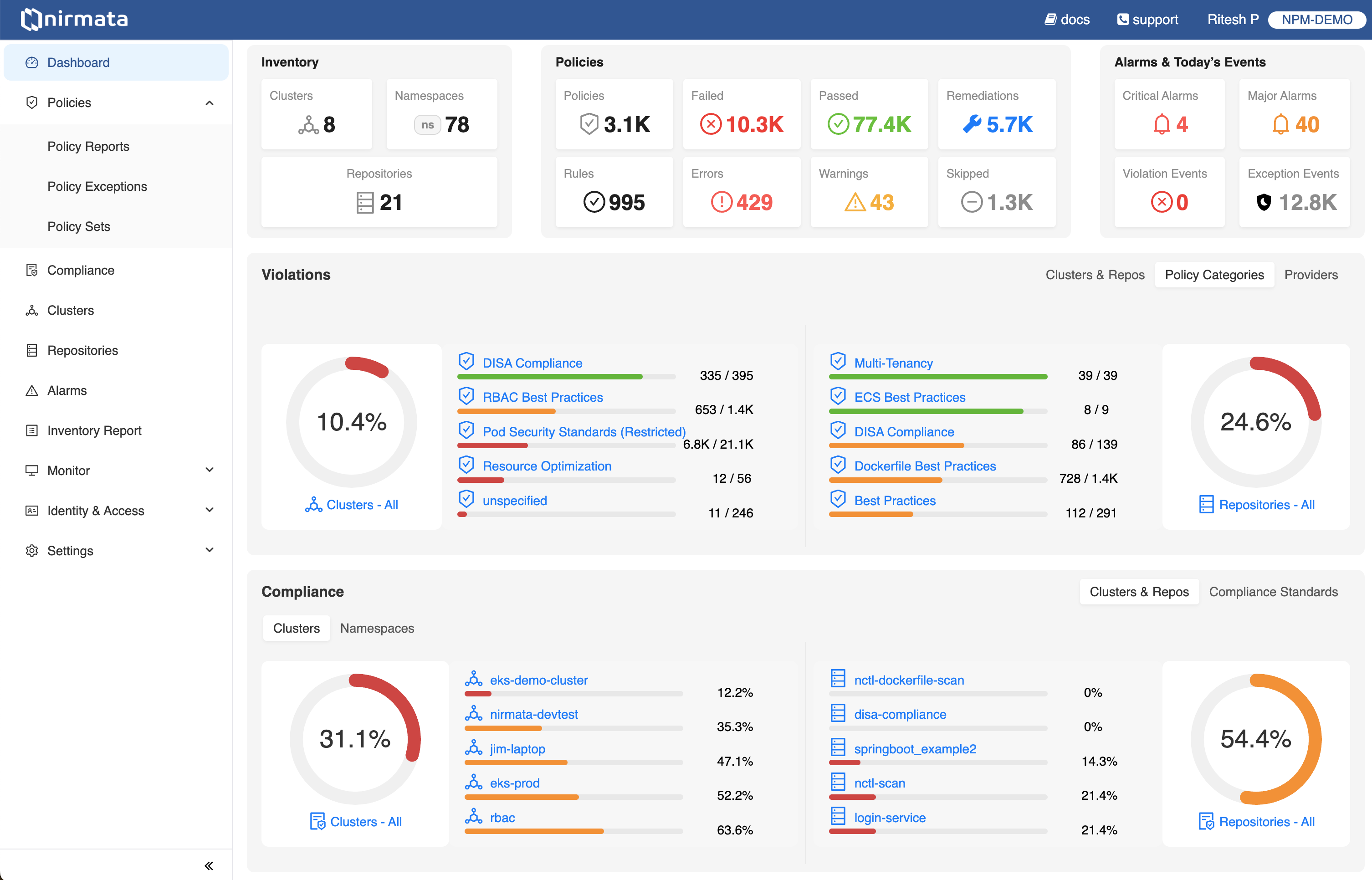
Security is Overwhelmed by Complexity
Let’s face it, securing cloud-native environments has become too complex. Runtime tools can’t prevent costly misconfigurations. Security teams are not cloud-native domain experts and “shift-left” simply burdens busy developers — leaving most Kubernetes clusters and workloads insecure and exposing a large attack surface. There has to be a better way.
180%
increase in security issues
93%
reported a security incident
Misconfigurations
are the leading cause
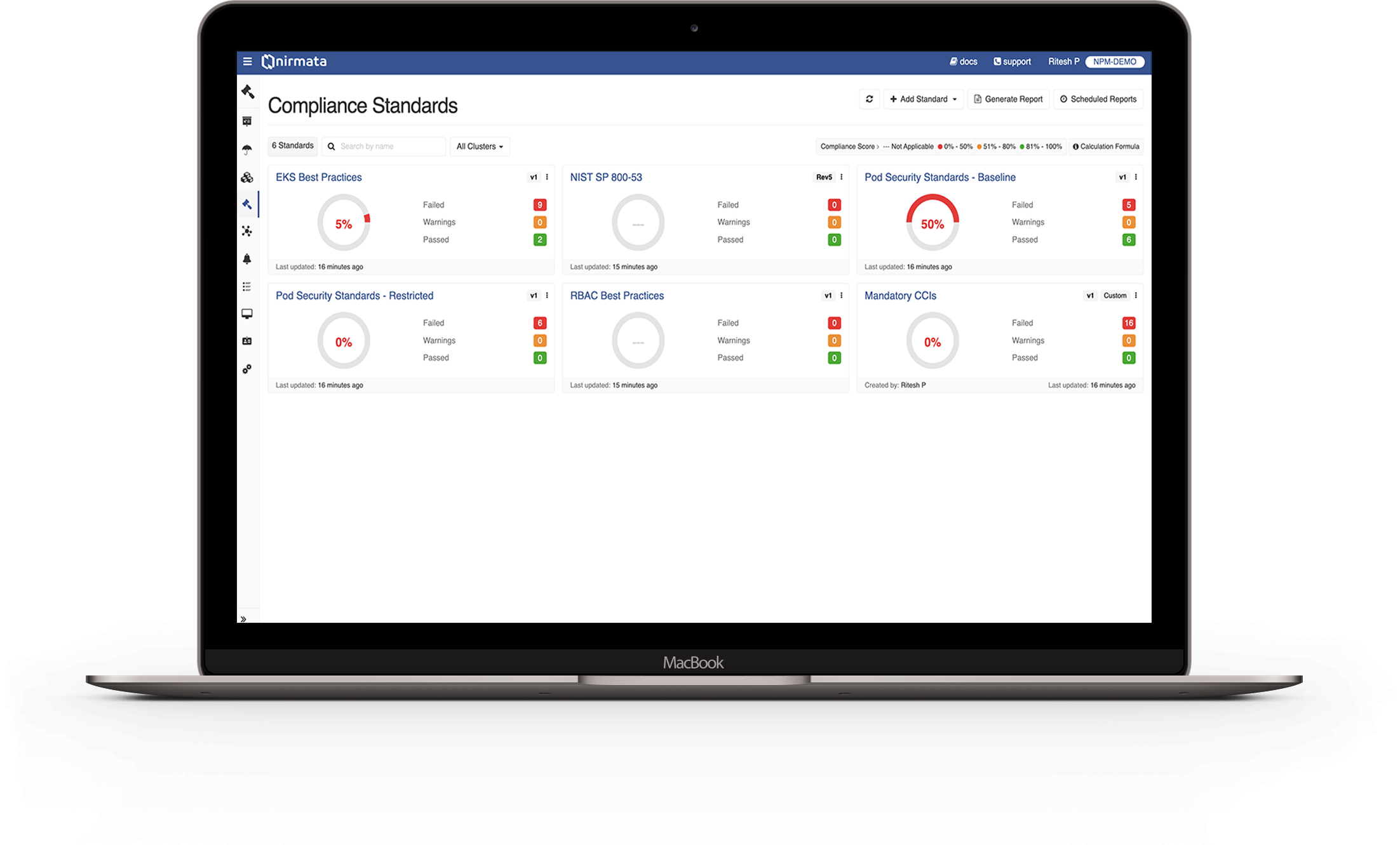
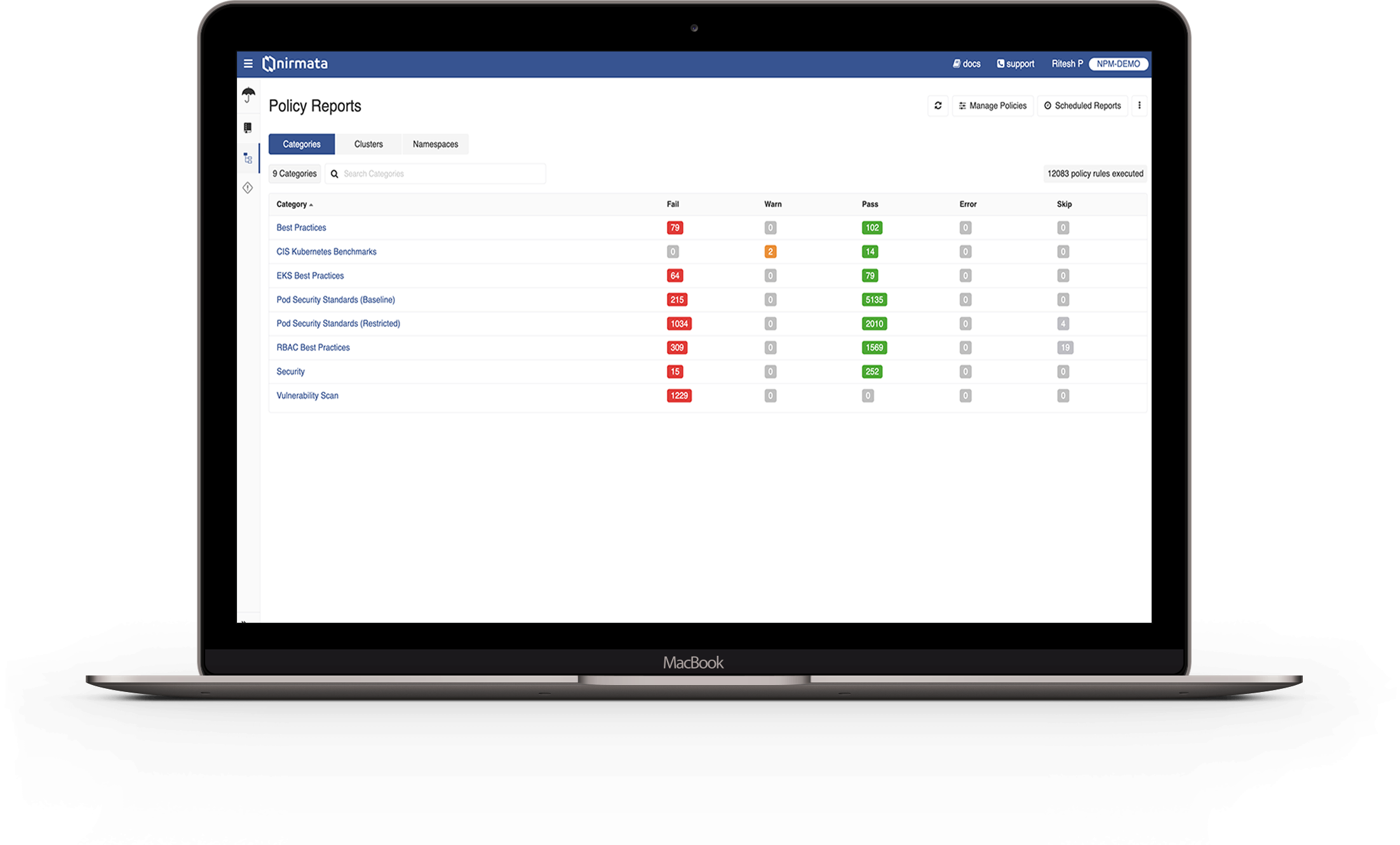
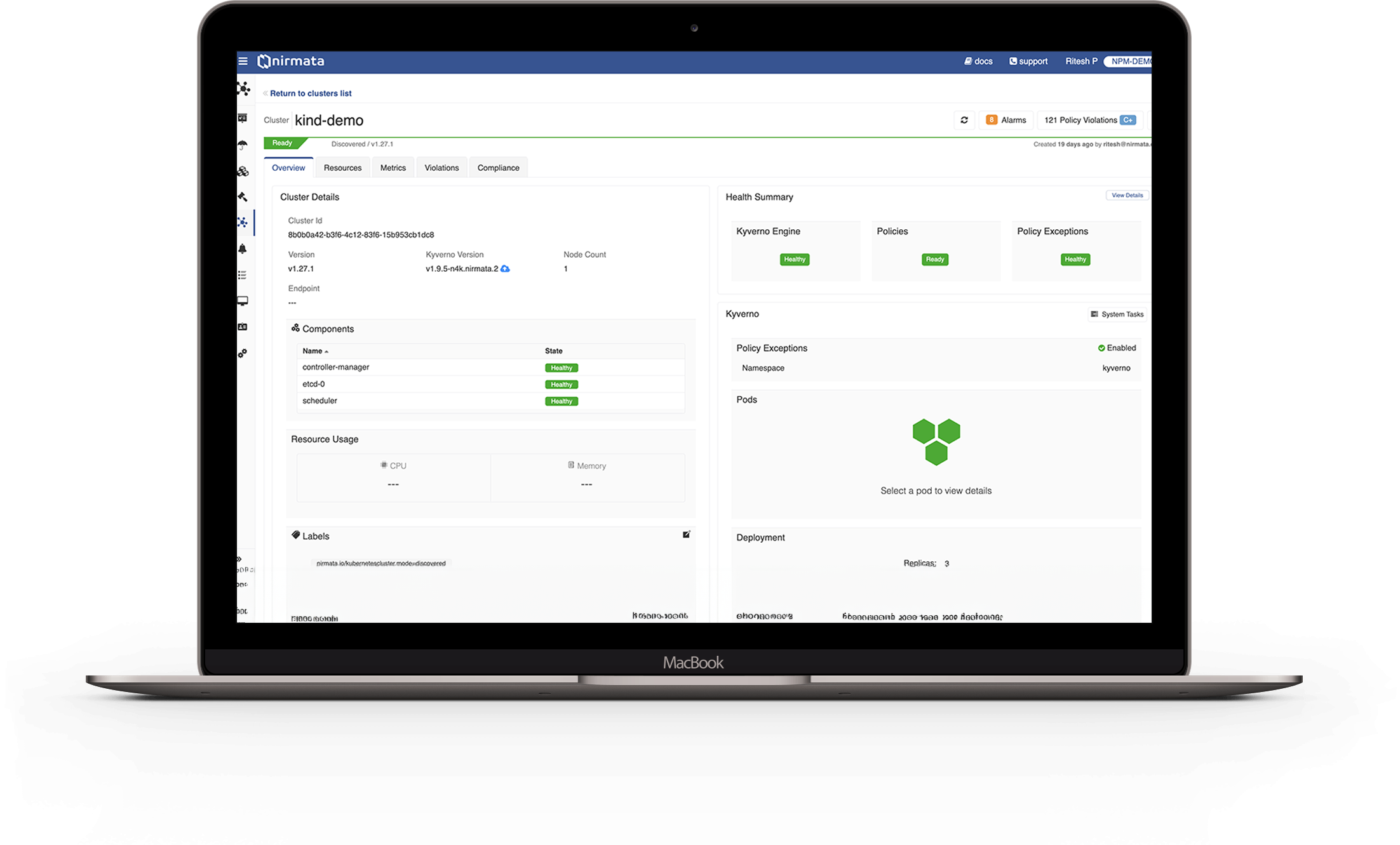
The Solution
Automate Security with Policy As Code
Nirmata enables platform engineering teams to proactively address Kubernetes security concerns, using policy as code integrated with native tools. With Nirmata, the platform team enables policies to effectively govern security, operations, costs, and best practices across Kubernetes clusters, CI/CD pipelines, and cloud services. Nirmata prevents costly misconfigurations and generates secure defaults in real time to automate security and compliance for cloud-native environments.
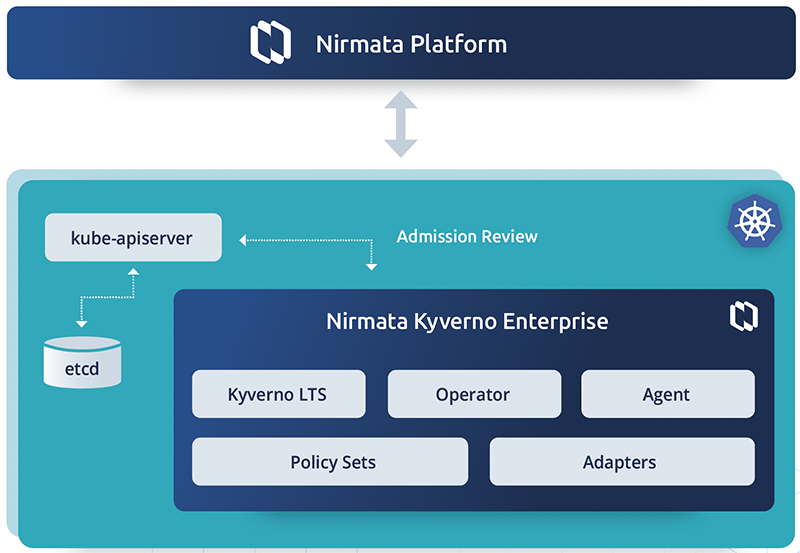
Shift Down Security
Empowers developers, facilitates proactive risk mitigation, and establishes a competitive advantage through swift and secure innovation by shifting down security,
What is Shift Down Security?
- Platform-Enforced Security: Incorporating robust security controls and configuration checks into developer platforms to ensure secure deployments.
- Integrated DevSecOps Tooling: Embedding security tools into CI/CD pipelines for automated scans and policy enforcement.
- Compliance Through Automation: Streamlining adherence to industry regulations and establishing an auditable security posture.
Works with Your Favorite DevOps Tools
Kyverno by the Numbers
3.2B+
Image Pulls
5.5K+
GitHub Stars
300+
Contributors
3,000+
Slack Members