Full Report On Cell Phone Based Door Opening System Using Microcontroller
Uploaded by
Kavya AjithFull Report On Cell Phone Based Door Opening System Using Microcontroller
Uploaded by
Kavya AjithApril 2014
Cell phone based DTMF controlled garage door opening system
CHAPTER 1
INTRODUCTION
In this age of digital technology, every device and its operation has become
digital. Now with digital based door lock systems, it is easier to control the door
movement of garage door or house. The new automated door lock system does not need a
key to lock or unlock the door.
This digital door entry system is in fact controlled by cell phone which is actually
performing the role of remote over here. The keyless door remote is an electronic circuit
based device. This remote transmits DTMF signals via air to another device of the system
installed in the garage door. This system can be operated from any corner of the world.
The working of this locking system is very simple. You just have to carry the cell phone
with yourself and you can control the locks from anywhere without any problem. It works
on the entry number. The owner has to press that entry number on the cell phone for
controlling the locking system. The entry number is unique in nature and so is the remote
device of an automatic keyless system.
You can install a keyless entry system in your house as well as in your vehicle.
Now, a days theft cases are increasing everywhere and the key based locking system is
no longer a safe option. It is quite easy for thieves and robbers to open the traditional key
based doors either with duplicate keys or some other way. Therefore for safety of your
house and vehicle, this system can be installed. With this system, you will never be in
tension of leaving your house and vehicle out of your supervision. Not only this, it also
help us to move out of some really odd situations like you locked the door and left and in
your absence other members came back and then they have to wait outside if they were
not having key with themselves.
Mobile phones today became very popular an essential entity for one and all and
so, for any mobile based application there is great reception. Wireless controlled systems
utilize RF circuits which had limitations like limited range, limited frequency ranges and
controls. But a mobile phone controlled systems can hold up these limitations.
Dept. of Electronics and Communication
METS School of Engineering, Mala
April 2014
Cell phone based DTMF controlled garage door opening system
1.1 MOTIVATION
Keyless entry has been a luxury whose availability is confined primarily to
vehicles. The cell phone security system takes this idea of key less entry and transforms it
in to a convenient, versatile security system that utilizes cell phone technology and the
land line telephone network. By taking the advantage of caller identification and dualtone multi frequency signalling, the security system has the ability to introduce two levels
of security. The first level will be decoding the calling partys identification information
while the second level would consist of the user attempting a pass word entry over the
phone. By combining the mobility of this telecommunication medium with
microcontrollers, the system achieves a secure, convenient and automated form of
security for a place of residence.
1.2 OBJECTIVE
The main objective of this system is to unlock a door by a mobile phone using a
unique code entered through the keypad of the phone. The other objective include,
correctly decode the DTMF signals from the users mobile.
1.3 ORGANIZATION
The first chapter is introduction, and it includes motivation and objectives of our
project. Second chapter is existing systems and it describes the prototype of our system
where we got the idea from. Third chapter deals with proposed systems which includes
block diagram, circuit diagram, working and theory. Evaluation tool is the fourth chapter,
which helped us in the simulation of project.
Fifth chapter is PCB design and fabrication. It is one of the most important
chapter, which contains PCB designing, manufacturing, PCB layout, and component
layout. Next chapter is deals with project estimation which give an idea about total cost
incurred in our project. Advantages and applications are explained in chapter 7.the
following chapter deals with results and discussion about the result obtained. The final
chapter is conclusion. In this we conclude our project, and explain the modifications that
can be applied to the system in future.
Dept. of Electronics and Communication
METS School of Engineering, Mala
April 2014
Cell phone based DTMF controlled garage door opening system
CHAPTER 2
EXISTING SYSTEM
The previous lock methods have proven to be a bit unsatisfactory in one way or
the other. Though, some have advantages outweighing the disadvantages while others
have much more disadvantages. Due to the fact that live and property may be at stake, it
is important to always have a reliable lock system, putting into consideration the high rate
of crime and insecurity. Most door lock systems also require carrying external lock
devices which complete the system; this may include keys, cards, remote controls, etc. On
losing any of these devices, one may need to change the lock system in order to apply
precaution(s) in case they have fallen into wrong hands.
As interest in wireless communication continues to grow, the remote controlled
systems are increasingly being integrated into everyday life. Even though modern
technology has allowed for the automation of many aspects of domestic lifestyles, from
automatic motion sensing lights, automatic control of home appliances to automatic
garage door openers, all these system use RF technology for wireless control. . However,
the use of RF contributes to enhancing the already mysterious nature of communication
strategies, which had limitations like limited range.
Also, due to the rapid growth in computer, GSM control system and technology
advancement in general, it may be seen worthwhile to move with the recent trends either
privately-in our homes or in our establishments.
Dept. of Electronics and Communication
METS School of Engineering, Mala
April 2014
Cell phone based DTMF controlled garage door opening system
CHAPTER 3
PROPOSED SYSTEM
The main objective of this system is to unlock a door by a mobile phone using a
unique code entered through the keypad of the phone. Opening and closing of doors
involves human to be physically involved in to the task. In this cell phone controlled,
password protected door locking system, the opening and closing of a door is achieved by
using a mobile phone.
This article summarizes the use of DTMF signalling technology to send and
receive the control commands from user in order to open or close the door. Password
protection is given to the system with help of microcontroller and corresponding
algorithm that authenticate the user by checking the password provided by the user. So, if
and only if the user press correct password then only user get authenticate and gets the
access to open or close the door.
3.1BLOCK DIAGRAM
Dept. of Electronics and Communication
METS School of Engineering, Mala
Fig.3.1 Block Diagram
April 2014
Cell phone based DTMF controlled garage door opening system
Power Supply
The power supply provides the necessary voltage to the entire circuit. The power
supply section consists of mainly a step down transformer, a bridge rectifier and a fixed
voltage regulator. A step down transformer and a bridge rectifier is used to convert the
230V/50Hz AC to DC. Two regulators ICs 7805 and 7806 are also used here to give
constant supply of 5V and 6V to all sub systems.
DTMF Decoder
DTMF decoder, decode the DTMF (Dual tone multi frequency) signals from
mobile phone into the equivalent binary form. For example, if 2 is pressed on the
keypad, the output of the decoder will be 0010. Here we use DTMF receiver IC, Motorola
MT8870, which is an 18-pin IC.
Microcontroller
It is the heart of our system. Microcontroller is pre programmed to take decision
corresponds to input. Password protection is given to the system with the help of a
microcontroller and corresponding algorithm that authenticate the user by checking the
password provided by the user. The microcontroller here we used is Atmega 8. It is a 28
pin DIP High-performance, Low-power AtmelAVR 8-bit Microcontroller and has
8Kbytes of In-System Self-programmable Flash program memory.
Motor and Driver Circuit
This section consist of a DC motor, relay, NPN transistor BC 548 and a resistor of
10k. The motor used over here is a 5V DC motor. Motor drivers acts as current amplifiers
since they take a low control signal and provide a high current signal. This higher current
is used to drive the motor. Relay is an electrically operated switch used to cut off the
load. The relay used here is SPDT switch that is single pole double throw. Here a
common terminal connects to either of two others.
LCD Module
A 16x2 LCD module is used here to display instructions to the user. It consists of
16 rows and 2 columns of 5x7 or 5x8 LCD dot matrices. It is available in a 16pin package
Dept. of Electronics and Communication
METS School of Engineering, Mala
April 2014
Cell phone based DTMF controlled garage door opening system
with back light, contrast adjustment function and each dot matrix has 5x7 or 5x8
dot resolution.
Matrix Keypad
A 4x4 matrix key pad is used as a substitute for entering the password in case, the
user forgot to take his mobile phone in his hand.
3.2 CIRCUIT DIAGRAM
Fig.3.2 Circuit Diagram
3.3 WORKING AND THEORY
This project use of DTMF signalling technology to send and receive the control
commands from user in order to open or close the door. Password protection is given to
the system with help of microcontroller and corresponding algorithm that authenticate the
user by checking the password provided by the user. So, if and only if the user press
correct password then only user get authenticate and gets the access to open or close the
Door. The user in order to open the door should make a voice call to the phone which is
stacked with the controller unit acting as receiver mobile. This receiver mobile is kept in
auto answer mode. So after a ring it will automatically accept the call. Now if user presses
Dept. of Electronics and Communication
METS School of Engineering, Mala
April 2014
Cell phone based DTMF controlled garage door opening system
any button on keypad of phone, the tone corresponds to that button is sent to other end.
This tone is fed to DTMF Decoder, where the DTMF frequency is converted in to the
equivalent digital form. For example, if 2 is pressed on the keypad, the output of the
decoder will be 0010. This digital information is given to the microcontroller. The
Microcontroller is pre-programmed to take decision corresponds to input button pressed.
A 16x2 LCD display is interfaced with the control unit to display instructions to user.
Depending upon the user password, controller will decide to open/close the door if the
user get authenticate, by using relay drive circuit and motor.
Fig. 3.2 illustrates the actual circuit that has been used to obtain the working
model of cell phone controlled, password protected door locking system. It consists of
Microcontroller, motor driver circuit, DTMF Decoder, LCD display,4x4 matrix keypad
and a power supply section. The microcontroller here we used is Atmega 8.Initially
microcontroller accepts binary input from DTMF decoder MT8870 to OPEN/CLOSE the
door respectively. Digital information coming from DTMF decoder is fed to the
microcontroller. The input from the receiver mobile is given to the pin no. 2 of DTMF
decoder ( MT8870) Via a resistor capacitor circuitry through a audio jack pin of receiver
mobile.
DTMF
When you press a button in the telephone keypad, a connection is made that
generates a resultant signal of two tones at the same time. These two tones are taken from
a row frequency and a column frequency. The resultant frequency signal is called "Dual
Tone Multiple Frequency". These tones are identical and unique. A DTMF signal is the
algebraic sum of two different audio frequencies, and can be expressed as follows:
f(t) = A0sin(2**fa*t) + B0sin(2**fb*t) + ...........(1)
Where fa and fb are two different audio frequencies with A and B. DTMF signal
fa belongs to the low frequency group and fb belongs to the high frequency group. Each
of the low and high frequency groups comprise four frequencies from the various keys
present on the telephone keypad; two different frequencies, one from the high frequency
group and another from the low frequency group are used to produce a DTMF signal to
represent the pressed key. The amplitudes of the two sine waves should be such that
(0.7 < (A/B) < 0.9)V .(2)
Dept. of Electronics and Communication
METS School of Engineering, Mala
April 2014
Cell phone based DTMF controlled garage door opening system
The frequencies are chosen such that they are not the harmonics of each other. The
frequencies associated with various keys on the keypad are shown in table.
Table 3. 1 Telephone Keypad with Frequency
1209 Hz
1336 Hz
1477 Hz
1633 Hz
697 Hz
770 Hz
852 Hz
941 Hz
When you send these DTMF signals to the telephone exchange through cables, the
servers in the telephone exchange identifies these signals and makes the connection to the
person you are calling. When you press the digit 5 in the keypad it generates a resultant
tone signal which is made up of frequencies 770Hz and 1336Hz. Pressing digit 8 will
produce the tone taken from tones 852Hz and 1336Hz. In both the cases, the column
frequency 1336 Hz is the same. These signals are digital signals which are symmetrical
with the sinusoidal wave. Due to its accuracy and uniqueness, these DTMF signals are
used in controlling systems using telephones. By using some DTMF generating IC s
(UM91214, UM91214, etc.) we can generate DTMF tones without depending on the
telephone set.
IC MT 8870
The MT-8870 is a full DTMF Receiver that integrates both band split filter and
decoder functions into a single 18-pin DIP. Its filter section uses switched capacitor
technology for both the high and low group filters and for dial tone rejection. Its decoder
uses digital counting techniques to detect and decode all 16 DTMF tone pairs into a 4-bit
code. Provision of an on-chip differential input amplifier, clock generator, and latched tri-
Dept. of Electronics and Communication
METS School of Engineering, Mala
April 2014
Cell phone based DTMF controlled garage door opening system
state interface bus. Minimal external components required include a low-cost 3.579545
MHz crystal, a timing resistor, and a timing capacitor. MT-8870 operating functions
include a band split filter that separates the high and low tones of the received pair, and a
digital decoder that verifies both the frequency and duration of the received tones before
passing the resulting 4-bit code to the output bus. The low and high group tones are
separated by applying the dual-tone signal to the inputs of two 6th order switched
capacitor band pass filters with bandwidths that correspond to the bands enclosing the
low and high group tones.
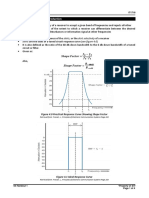
Fig. 3.3 IC 8870 Block Diagram
The filter also incorporates notches at 350 and 440 Hz, providing excellent dial
tone rejection. Each filter output is followed by a single-order switched capacitor section-
Dept. of Electronics and Communication
METS School of Engineering, Mala
April 2014
Cell phone based DTMF controlled garage door opening system
that smoothest the signals prior to limiting. Signal limiting is performed by high gain
comparators provided with hysteresis to prevent detection of unwanted low-level signals
and noise.
The MT-8870 decoder uses a digital counting technique to determine the
frequencies of the limited tones and to verify that they correspond to standard DTMF
frequencies. When the detector recognizes the simultaneous presence of two valid tones
(known as signal condition), it raises the Early Steering flag (EST). Any subsequent loss
of signal condition will cause EST to fall. Before a decoded tone pair is registered, the
receiver checks for valid signal duration (referred to as character- recognition-condition).
This check is performed by an external RC time constant driven by Est. A short delay to
allow the output latch to settle, the delayed steering output flag (STD) goes high,
signalling that a received tone pair has been registered. The contents of the output latch
are made available on the 4-bit output bus by raising the three state control input (OE) to
logic high. Inhibit mode is enabled by a logic high input to pin 5 (INH). It inhibits the
detection of 1633 Hz. The output code 13 will remain the same as the previous detected
code. On the M- 8870 models, this pin is tied to ground (logic low).
The input arrangement of the MT-8870 provides a differential input operational
amplifier as well as a bias source (VREF) to bias the inputs at mid-rail. Provision is made
for connection of a feedback resistor to the op-amp output (GS) for gain adjustment.
The internal clock circuit is completed with the addition of a standard 3.579545 MHz
crystal.
ATMEGA8L MICROCONTROLLER
It is a High-performance, Low-power Atmel AVR 8-bit Microcontroller. AVR is
a modified
Harvard
architecture 8-bit RISC single
chip microcontroller which
was
developed by Atmel in 1996. The AVR was one of the first microcontroller families to use
on-chip flash memory for program storage, as opposed to one-time programmable
ROM, EPROM, or EEPROM used by other microcontrollers at the time. Flash EEPROM,
and SRAM are all integrated onto a single chip, removing the need for external memory
in most applications.
Dept. of Electronics and Communication
10
METS School of Engineering, Mala
April 2014
Cell phone based DTMF controlled garage door opening system
Some devices have a parallel external bus option to allow adding additional data
memory or memory-mapped devices. Almost all devices (except the smallest Tiny AVR
chips) have serial interfaces, which can be used to connect larger serial EEPROMs or
flash chips.
FEATURES
High-performance, Low-power Atmel AVR 8-bit Microcontroller
Advanced RISC Architecture
130 Powerful Instructions Most Single-clock Cycle Execution
32 8 General Purpose Working Registers
Fully Static Operation
Up to 16MIPS Throughput at 16MHz
On-chip 2-cycle Multiplier
High Endurance Non-volatile Memory segments
8Kbytes of In-System Self-programmable Flash program memory
512Bytes EEPROM
1Kbyte Internal SRAM
Peripheral Features
Two 8-bit Timer/Counters with Separate Prescaler, one Compare Mode
One 16-bit Timer/Counter with Separate Prescaler, Compare Mode, and Capture
Mode
Real Time Counter with Separate Oscillator
Three PWM Channels
8-channel ADC in TQFP and QFN/MLF package
Byte-oriented Two-wire Serial Interface
Programmable Serial USART
Master/Slave SPI Serial Interface
Programmable Watchdog Timer with Separate On-chip Oscillator
On-chip Analog Comparator
ATmega 8 can be mapped with Arduino Development Software. The pin mapping for the
ATmega is given below.
ATMEGA 8L
Dept. of Electronics and Communication
11
METS School of Engineering, Mala
April 2014
Cell phone based DTMF controlled garage door opening system
Fig.3.4 Pin Details of Atmega8L
Dept. of Electronics and Communication
12
METS School of Engineering, Mala
April 2014
Cell phone based DTMF controlled garage door opening system
CHAPTER 4
EVALUATION TOOLS
4.1 PROTEUS
Proteus 8 is a single application with many service modules offering different
functionality (schematic capture, PCB layout, etc.). The wrapper that enables all of the
various tools to communicate with each other consists of three main parts.
Application Framework
Proteus 8 consists of a single application (PDS.EXE). This is the framework or
container which hosts all of the functionality of Proteus. ISIS, ARES, 3DV all open as
tabbed windows within this framework and therefore all have access to the common
database.
Common Database
The common database contains information about parts used in the project. A part
can contain both a schematic component and a PCB footprint as well both user and
system properties. Shared access to this database by all application modules makes
possible a huge number of new features, many of which will evolve over the course of the
Version 8 lifecycle.
Live Netlist
Together with the common database the maintenance of a live netlist allows all
open modules to automatically reflect changes. The most obvious example of this is
wiring in ISIS producing ratsnest connections in ARES but it goes much further than that.
The new Bill of Materials module contains a live viewer and the 3D Viewer and Design
Explorer are also linked into the live netlist. The strength of its architecture has allowed
us to integrate first conventional graph based simulation and with Proteus VSM
interactive circuit simulation into the design environment.
Dept. of Electronics and Communication
13
METS School of Engineering, Mala
April 2014
Cell phone based DTMF controlled garage door opening system
You can now draw a complete-circuit for a micro-controller based system and
then test it interactively, all from within the same piece of software. Meanwhile, ISIS
retains a host of features aimed at the PCB designer, so that the same design can be
exported for production with ARES or other PCB layout software
Features
Runs on Windows XP onwards.
Automatic wire routing and dot placement/removal.
Powerful tools for selecting objects and assigning their properties.
Total support for buses including component pins, inter-sheet terminals, module
ports and wires.
Live netlisting to the ARES Layout module and additional netlist outputs to suit
other PCB layout tools.
Design Global Annotation allowing multiple instances of a sub-circuit to have
different component references.
Automatic Annotation - the ability to number the components automatically.
ISIS & ARES
Users intending to design PCB's using the ARES Layout module will find some of
the following PCB layout specific features of interest:
The ability to assign and configure net classes directly from the place wire label
command on a schematic connection. This allow you to specify trace width and
via styles and feeds into the design rule manager in ARES where you can further
configure board constraints.
Sheet Global Net Properties which allow you to efficiently define a net class for
all the nets on a given sheet (e.g. a power supply needing POWER width tracks).
Physical terminals which provide the means to have the pins on a connector
scattered all over a design.
A visual packaging tool which shows the PCB footprint and its pin numbers
alongside the list of pin names for the schematic part ISIS & Simulation.
Dept. of Electronics and Communication
14
METS School of Engineering, Mala
April 2014
Cell phone based DTMF controlled garage door opening system
ISIS & SIMULATION
ISIS provides the development environment for PROTEUS VSM. This product
combines mixed mode circuit simulation, micro-processor models and interactive
component models to allow the simulation of complete micro-controller based designs.
ISIS provides the means to enter the design in the first place, the architecture for
real time interactive simulation and a system for managing the source and object code
associated with each project. In addition, a number of graph objects can be placed on the
schematic to enable conventional time, frequency and swept variable simulation to be
performed.
4.2 ARDUINO UNO
Arduino is an open-source electronics prototyping platform based on flexible,
easy-to-use hardware and software. It's intended for artists, designers, hobbyists and
anyone interested in creating interactive objects or environments. Arduino can sense the
environment by receiving input from a variety of sensors and can affect its surroundings
by controlling lights, motors, and other actuators. The microcontroller on the board is
programmed using the Arduino programming language(based on Wiring) and the
Arduino development environment(based on Processing).
Arduino projects can be stand-alone or they can communicate with software
running on a computer (e.g. Flash, Processing, MaxMSP).The boards can be built by
hand or purchased preassembled; the software can be downloaded for free rather than
requiring a physical press of the reset button before an upload, the Arduino Uno is
designed in a way that allows it to be reset by software running on a connected computer.
One of the hardware flow control lines (DTR) of the ATmega8U2/16U2 is connected to
the reset line of the ATmega328 via a 100 nano farad capacitor. When this line is
asserted(taken low), the reset line drops long enough to reset the chip. The Arduino
software uses this capability to allow you to upload code by simply pressing the upload
button in the Arduino environment. This means that the boot loader can have a shorter
time out, as the lowering of DTR can be well-coordinated with the start of the upload.
Dept. of Electronics and Communication
15
METS School of Engineering, Mala
April 2014
Cell phone based DTMF controlled garage door opening system
CHAPTER 5
PCB DESIGNING AND FABRICATION
5.1 PCB DESIGNING
A printed circuit board, or PCB, is used to mechanically support and electrically
connect electronic components using conductive pathways, tracks or signal traces etched
from copper sheets laminated onto a non-conductive substrate. When the board has only
copper tracks and features, and no circuit elements such as capacitors, resistors or active
devices have been manufactured into the actual substrate of the board, it is more correctly
referred to as printed wiring board (PWB) or etched wiring board. Use of the term PWB
or printed wiring board although more accurate and distinct from what would be known
as a true printed circuit board, has generally fallen by the wayside for many people as the
distinction between circuit and wiring has become blurred. Today printed wiring (circuit)
boards are used in virtually all but the simplest commercially produced electronic
devices, and allow fully automated assembly processes that were not possible or practical
in earlier era tag type circuit assembly processes.
A PCB populated with electronic components is called a printed circuit assembly
(PCA), printed circuit board assembly or PCB Assembly (PCBA). In informal use the
term "PCB" is used both for bare and assembled boards, the context clarifying the
meaning. The various tools for implementing and designing the PCB is given below:
ELECTRONIC DESIGN AUTOMATION (EDA) TOOLS
With the advent of powerful computing system and interactive software, several
stages in the design and development of an electronic circuit has undergone automation.
These software and hardware tools, which enable automation, are called EDA tools. This
tools helps us in such a way that we can draw the circuit; list the functioning of the circuit
in the best inputs in assimilation software .After successful simulation of the circuit, the
Dept. of Electronics and Communication
16
METS School of Engineering, Mala
April 2014
Cell phone based DTMF controlled garage door opening system
placing and routing software does the PCB artwork. In this project the design automation
tool used is Dip Trace. Dip Trace is a complete PCB Design system. It includes four
programs:
PCB Layout - PCB design with easy to use manual routing tools and auto router.
Schematic - creates schematic and exports netlist to PCB.
Pattern Editor - allows to make package footprints (patterns).
Component Editor - allows to draw parts and attach patterns to them.
For creating the PCB artwork the design process is of the following steps:
Drawing the circuit schematic
This is done in Dip Trace schematic capture. It includes many libraries with
thousands of component symbols .We can select the required symbol from the library and
place it on the schematic page. After placing the component symbol, the interconnection
is completed using bus tool .After drawing the schematic, the following operations are
performed.
Convert schematic into PCB
Then select the menu option 'Switch to Board' to convert the schematic to PCB.
Layout can be updated from Schematic in a few clicks at anytime
Routing
Routing is the interconnection of components using upper tracks of required
width. Before starting routing the following things are done:
Enabling /disabling required layers:
The number of layers used and enabling the artwork depends upon the complexity of the
circuit and fabrication technology available. If the board is single sided enable only
bottom or solder side layer, so that the track will come only on one side of the PCB. If the
circuit is more complex enable the required number of inner layer considering the
fabrication technique and cost.
Dept. of Electronics and Communication
17
METS School of Engineering, Mala
April 2014
Cell phone based DTMF controlled garage door opening system
Manual routing / Auto routing
Dip Trace PCB software includes 2 automatic routers which is able to route complex
multi-layer boards as well as simple single-layer layouts. Intelligent manual routing tools
allow you to create and edit traces by 90, 45 degree or without any limitations. Through,
blind or buried vias can be used in automatic and manual routingIn this, the PCB design
has to manually connect each track. This is time consuming, but is required in some
cases. In this also the software checks for errors and reports.
5.2 MANUFACTURING
PROCESSING THE FILM:
The layout is printed in a butter paper using a laser printer. The layout is
transferred to the copper clad sheet using the screen print procedure. First a
negative screen of layout is prepared with the help of a professional screen printer.
Then the copper clad sheet is kept under this screen. The printed board is kept
under shade for a few hours till the ink becomes dry.
The etching medium is prepared with an-hydrous ferric chloride and water. The
printed circuit board is kept in this solution till the exposed copper dissolves in the
solution fully. After that the board is taken out and rinsed in flowing water under a
tap. The ink is removed with the help of NC thinner (available in the paint shops).
The board is coated with solder in order to prevent oxidation. Another screen,
which contains component side layout, is prepared and the same is printed on the
component side of the board. A paper epoxy laminate is used as the board.
STANDARD REQUIREMENTS:
The minimum conductor width of the finished PCB shall not be less than 0.05mm
for signal and 0.4mm for power line. The standard ratio is taken as 1:1, 5:2 for signal
power respectively.
Dept. of Electronics and Communication
18
METS School of Engineering, Mala
April 2014
Cell phone based DTMF controlled garage door opening system
CLEANING:
Surface of copper clad may contain oxides, greases, oil or solid. They should be
removed by the following procedure:
Wipe with cotton wool soaked with tricolour ethylene.
Dip in 10% HCL solution at room temperature.
Scrap with powder.
Rinse with chlorine free water.
Observe the wetting of water on the surface. If the wetting is uniform without any
island, the surface is clean.
ARTWORK TRANSFER:
Artwork transfer can be done in many ways and procedure used in the work is named
fabrication process. Usually used methods are:
Silk screen printing.
Photographic method.
Direct method.
In direct method artwork is transferred to clad sheet in the ratio 1:1 using paint or
permanent ink.
ETCHING:
The vast majority of printed circuit boards are made by bonding a layer of copper
over the entire substrate ,sometimes on both sides,(creating a blank PCB) then
removing unwanted copper traces. A few PCBs are made by adding traces to the bare
substrate (or a substrate with a very thin layer of copper) usually by a complex process of
multiple electroplating steps.
Dept. of Electronics and Communication
19
METS School of Engineering, Mala
April 2014
Cell phone based DTMF controlled garage door opening system
DRILLING:
The holes for mounting components are drilled using a high speed drilling
machine. The size of the holes to be drilled will be specified during the layout designing
depending upon the component lead diameter. For drilling we use 1mm drill bit.
VARNISH COATING:
If the board is unprotected, copper oxides are formed over the conductor and it
affects sold arability and neatness of the board. For this, insulation coating such as
varnish can be used.
SOLDERING:
After the above process the components are soldered on the board. Soldering
angles varies from 5 to 29 degrees.
Dept. of Electronics and Communication
20
METS School of Engineering, Mala
April 2014
Cell phone based DTMF controlled garage door opening system
5.3 PCB LAYOUT
Fig.5.1
Dept. of Electronics and Communication
PCB layout
21
METS School of Engineering, Mala
April 2014
Cell phone based DTMF controlled garage door opening system
5.4 COMPONENT LAYOUT
Fig.5.2 Component layout
Dept. of Electronics and Communication
22
METS School of Engineering, Mala
April 2014
Cell phone based DTMF controlled garage door opening system
CHAPTER 6
PROJECT ESTIMATION
Table 6.1 Project Estimation
COMPONENT UNIT
PRICE
NO. OF
PIECES
COST
Resistors
.50
10
5.00
Potentiometer
1.00
Capacitors
1.50
03.00
Diodes
04.00
LED
02.00
Transformer
90
90.00
Transistor
04.00
Relay
20
40.00
Atmega 8
110
110.00
Mt8870
35
35.00
Crystal Oscillator
16.00
DC Motor
150
150.00
LCD Module
130
130.00
Matrix Keypad
144
144.00
PCB
30
30.00
Total
Dept. of Electronics and Communication
Rs:764.00
23
METS School of Engineering, Mala
April 2014
Cell phone based DTMF controlled garage door opening system
CHAPTER 7
ADVANTAGES AND APPLICATIONS
7.1 ADVANTAGES
It provides keyless entry to the premises and is a versatile security system that
utilizes cell phone technology. Overcoming the limited range of infrared and radio
remote controls. This system takes advantage of the widespread acceptance of cell phones
in automation. Our system doesnt have the problems of range limits and we can access
the door from anywhere in the world.
7.2 APPLICATIONS
Just by pressing the key pad of mobile phone we can open or close the garage
doors automatically with a unique pass word from anywhere in the world. It include areas
like home security providing this keyless entry to door.
Dept. of Electronics and Communication
24
METS School of Engineering, Mala
April 2014
Cell phone based DTMF controlled garage door opening system
CHAPTER 8
RESULTS AND DISCUSSION
8.1 RESULTS
We were able to construct a Cell phone based DTMF controlled garage
door opening system that could demonstrate our aim. Whenever the user entered his pass
word using mobile phone, unique frequencies are generated corresponding to the pass
word which are decoded by DTMF decoder IC at the receiving end. If this decoded
values matches with the password stored in the microcontroller, then controller initiates a
mechanism to open or close the door. Also the user could see the information and result
through the LCD module.
Fig.8.1 DTMF Signal for Digit 1
Fig.8.2 Breadboard Implementation
Dept. of Electronics and Communication
25
METS School of Engineering, Mala
April 2014
Cell phone based DTMF controlled garage door opening system
8.2 DISCUSSION
The DTMF signals generated were clean and virtually free of noise. We verified
this using an oscilloscope to capture the signal generated and checking for noise spikes.
Also, the DTMF decoder circuit verified that the signals were genuine DTMF signals
since they were able to be decoded. The figure above shows the DTMF signal
corresponds to digit 1. Since this signal is a mixture of 697 Hz & 1209 Hz, we added
these two frequencies and verified the obtained signal. A problem incurred with this
system is some mobile phones which working as receiver didnt correctly decode all
DTMF signals. The filters in their audio section filter out some of the DTMF frequencies.
But mobile phones having Android application work very well with our system.
Dept. of Electronics and Communication
26
METS School of Engineering, Mala
April 2014
Cell phone based DTMF controlled garage door opening system
CHAPTER 9
CONCLUSION
The design and implementation of microcontroller based security door system
using mobile phone has been proven to be a reasonable advancement in door security
system technology and access control. From this experimentation we conclude that it is
feasible to implement the Cell Phone Controlled, Password Protected Door Locking
System which is in turn illustrate the use of DTMF technology for control of remote
applications.
The security system will hopefully fulfil its other primary goal which is to
influence a change within the market - a change towards a more convenient, responsive,
automated security system such as the cell phone security system. It is possible to provide
high security protection to home, banks and the places where the confidentiality, privacy
and security is to be preserved.
Dept. of Electronics and Communication
27
METS School of Engineering, Mala
April 2014
Cell phone based DTMF controlled garage door opening system
REFERENCES
[1] Ashish Jadhav, Mahesh Kumbhar and Meenakshi Pawar, Cell phone Controlled
ground Combat Vehicle, International Journal of Computer and communication
engineering Vol. 1, No. 2, ISSN: 2010-3743, pp 114-116, July 2012.
[2]
International Journal Of Electronics And Communication Engineering &
Technology (IJECET), ISSN 0976 6464(Print), ISSN 0976 6472(Online) Volume
3, Issue 2, pp pp 263-270, July-September 2012.
[3] DTMF Explained, www.genave.com/dtmf [2008, March 31].
[4] Free datasheet download site, www.alldatasheet.com [2008, June 29].
[5] Vladimir, G. (2005), "Electrical Relays: Principles and Applications", CRC Press
(Taylor & Francis group), London. Available: http://en.wikipedia.org/wiki/relays
[2008, April 10].
[6] www.arduinouno.com
[7] www.engineersgarage.com
[8] www.edgefxkits.com
Dept. of Electronics and Communication
28
METS School of Engineering, Mala
April 2014
Cell phone based DTMF controlled garage door opening system
APPENDIX
Dept. of Electronics and Communication
29
METS School of Engineering, Mala
You might also like
- Embedded IoT Assignment Answers TemplateNo ratings yetEmbedded IoT Assignment Answers Template5 pages
- Transmission Line Multiple Fault Detection and Indication To Electricity Board100% (1)Transmission Line Multiple Fault Detection and Indication To Electricity Board74 pages
- Rfid Based Vehicle Monitoring and Toll Collection System0% (1)Rfid Based Vehicle Monitoring and Toll Collection System38 pages
- Bharat Heavy Elelctricals Limited: Operation & Maintenance Manual of Bhelscan Flame Scanner System (Bn10)100% (1)Bharat Heavy Elelctricals Limited: Operation & Maintenance Manual of Bhelscan Flame Scanner System (Bn10)25 pages
- Industrial Automation Using Mobile CommunicationNo ratings yetIndustrial Automation Using Mobile Communication19 pages
- A Project Report On Cell Phone Detector-1No ratings yetA Project Report On Cell Phone Detector-14 pages
- Bluetooth Enabled Digital Door Lock Using Arduino-4100% (1)Bluetooth Enabled Digital Door Lock Using Arduino-430 pages
- Micro Controller Based Digital Visitor CounterNo ratings yetMicro Controller Based Digital Visitor Counter36 pages
- Wireless Charging of Mobile Phones Using Microwaves100% (1)Wireless Charging of Mobile Phones Using Microwaves15 pages
- Home Automation System Using Embedded SystemNo ratings yetHome Automation System Using Embedded System8 pages
- Construction of Automatic Door Bell System With The Object Detection100% (1)Construction of Automatic Door Bell System With The Object Detection3 pages
- Mini Project INTERCOM LM386 by Abid Parwez100% (4)Mini Project INTERCOM LM386 by Abid Parwez26 pages
- 03.PIR and GSM Based House Security SystemNo ratings yet03.PIR and GSM Based House Security System4 pages
- Microcontroller Based Automatic Missile Detection and Destroy SystemNo ratings yetMicrocontroller Based Automatic Missile Detection and Destroy System31 pages
- Aim: Study The Features, Specification and Working of Cellular Mobile0% (1)Aim: Study The Features, Specification and Working of Cellular Mobile5 pages
- Project Report On Gimbal Controller Using STM32No ratings yetProject Report On Gimbal Controller Using STM3225 pages
- Project Report On Obstacel Detector Using 7404100% (2)Project Report On Obstacel Detector Using 740443 pages
- AUTOMATIC CAR SPEED +RF Control ArudinoNo ratings yetAUTOMATIC CAR SPEED +RF Control Arudino19 pages
- Literature Review For GSM Based Home Security SystemNo ratings yetLiterature Review For GSM Based Home Security System6 pages
- Security System Using RFID: A Project ReportNo ratings yetSecurity System Using RFID: A Project Report30 pages
- Final Mini Project Documentation (VBNB)No ratings yetFinal Mini Project Documentation (VBNB)33 pages
- AVR Microcontrollers - Guide To Learning The Microcontroller Embedded System100% (2)AVR Microcontrollers - Guide To Learning The Microcontroller Embedded System13 pages
- Voice Based Notice Board Using Android ApplicationNo ratings yetVoice Based Notice Board Using Android Application17 pages
- Live Human Being Detection Wireless Remote Controlled Robot90% (10)Live Human Being Detection Wireless Remote Controlled Robot59 pages
- DOOR LOCK Through Telephone Using DTMF COMPLETEDNo ratings yetDOOR LOCK Through Telephone Using DTMF COMPLETED39 pages
- 2013 Microcontroller Based Reprogrammable Digital Door Lock Security Systemby Using Keypadand GSMor CDMATechnologyNo ratings yet2013 Microcontroller Based Reprogrammable Digital Door Lock Security Systemby Using Keypadand GSMor CDMATechnology6 pages
- Cell Phone Based DTMF Controlled Garage Door Opening System75% (8)Cell Phone Based DTMF Controlled Garage Door Opening System42 pages
- DTMF Based Door Locking System: Microsys SolutionNo ratings yetDTMF Based Door Locking System: Microsys Solution5 pages
- RGPV Syllabus 4th Sem Biomedical EngineeringNo ratings yetRGPV Syllabus 4th Sem Biomedical Engineering6 pages
- Aion 3pdt Refractor Bypass DocumentationNo ratings yetAion 3pdt Refractor Bypass Documentation1 page
- Bandstop Filters and The Bainter Topology: by Bonnie C. BakerNo ratings yetBandstop Filters and The Bainter Topology: by Bonnie C. Baker5 pages
- Cost Optimized Product Selection Guide PDFNo ratings yetCost Optimized Product Selection Guide PDF22 pages
- Basic Principles of Signal Reproduction: Skirts Are The Sides of A Tuned Circuit Response Curve (See Figure 4.0)No ratings yetBasic Principles of Signal Reproduction: Skirts Are The Sides of A Tuned Circuit Response Curve (See Figure 4.0)4 pages
- Design of Ultra Low Power 1 Bit Full Adder Cell Using Advance GDI 6T Logic StyleNo ratings yetDesign of Ultra Low Power 1 Bit Full Adder Cell Using Advance GDI 6T Logic Style5 pages
- ISMA-B-MIX18 Instalation Instruction V4.0No ratings yetISMA-B-MIX18 Instalation Instruction V4.02 pages
- Check List of Physics Important Questions 2m 3m 5mNo ratings yetCheck List of Physics Important Questions 2m 3m 5m16 pages
- A Study On Insulation Coordination of A Wind Turbine Generator System and A Distribution Line100% (1)A Study On Insulation Coordination of A Wind Turbine Generator System and A Distribution Line6 pages
- Lim Zheng Jie - Thesis - Single Photon Detection at Telecom WavelengthNo ratings yetLim Zheng Jie - Thesis - Single Photon Detection at Telecom Wavelength72 pages
- Transmission Line Multiple Fault Detection and Indication To Electricity BoardTransmission Line Multiple Fault Detection and Indication To Electricity Board
- Rfid Based Vehicle Monitoring and Toll Collection SystemRfid Based Vehicle Monitoring and Toll Collection System
- Bharat Heavy Elelctricals Limited: Operation & Maintenance Manual of Bhelscan Flame Scanner System (Bn10)Bharat Heavy Elelctricals Limited: Operation & Maintenance Manual of Bhelscan Flame Scanner System (Bn10)
- Bluetooth Enabled Digital Door Lock Using Arduino-4Bluetooth Enabled Digital Door Lock Using Arduino-4
- Wireless Charging of Mobile Phones Using MicrowavesWireless Charging of Mobile Phones Using Microwaves
- Construction of Automatic Door Bell System With The Object DetectionConstruction of Automatic Door Bell System With The Object Detection
- Microcontroller Based Automatic Missile Detection and Destroy SystemMicrocontroller Based Automatic Missile Detection and Destroy System
- Aim: Study The Features, Specification and Working of Cellular MobileAim: Study The Features, Specification and Working of Cellular Mobile
- Literature Review For GSM Based Home Security SystemLiterature Review For GSM Based Home Security System
- AVR Microcontrollers - Guide To Learning The Microcontroller Embedded SystemAVR Microcontrollers - Guide To Learning The Microcontroller Embedded System
- Voice Based Notice Board Using Android ApplicationVoice Based Notice Board Using Android Application
- Live Human Being Detection Wireless Remote Controlled RobotLive Human Being Detection Wireless Remote Controlled Robot
- 2013 Microcontroller Based Reprogrammable Digital Door Lock Security Systemby Using Keypadand GSMor CDMATechnology2013 Microcontroller Based Reprogrammable Digital Door Lock Security Systemby Using Keypadand GSMor CDMATechnology
- Cell Phone Based DTMF Controlled Garage Door Opening SystemCell Phone Based DTMF Controlled Garage Door Opening System
- Bandstop Filters and The Bainter Topology: by Bonnie C. BakerBandstop Filters and The Bainter Topology: by Bonnie C. Baker
- Basic Principles of Signal Reproduction: Skirts Are The Sides of A Tuned Circuit Response Curve (See Figure 4.0)Basic Principles of Signal Reproduction: Skirts Are The Sides of A Tuned Circuit Response Curve (See Figure 4.0)
- Design of Ultra Low Power 1 Bit Full Adder Cell Using Advance GDI 6T Logic StyleDesign of Ultra Low Power 1 Bit Full Adder Cell Using Advance GDI 6T Logic Style
- Check List of Physics Important Questions 2m 3m 5mCheck List of Physics Important Questions 2m 3m 5m
- A Study On Insulation Coordination of A Wind Turbine Generator System and A Distribution LineA Study On Insulation Coordination of A Wind Turbine Generator System and A Distribution Line
- Lim Zheng Jie - Thesis - Single Photon Detection at Telecom WavelengthLim Zheng Jie - Thesis - Single Photon Detection at Telecom Wavelength