EGL202 - Lab - 1 - Compare Data With A Hash (Student)
Uploaded by
xian huiEGL202 - Lab - 1 - Compare Data With A Hash (Student)
Uploaded by
xian huiEGL202 Cyber Security Essentials
Lab 1 Compare Data with a Hash
A. Objectives
Use a hashing program to verify the integrity of data.
B. Introduction
It is important to understand when data has been corrupted or it has been tampered with. A
hashing program can be used to verify if data has changed, or if it has remained the same. A
hashing program performs a hash function on data or a file, which returns a (usually much shorter)
value.
There are many different hash functions, some very simple and some very complex. When the
same hash is performed on the same data, the value that is returned is always the same. If any
change is performed on the data, the hash value returned will be different.
Note:
You will need installation privileges and some knowledge of the process to install Windows
programs.
Task 1: Create a Text file
1) Search your computer for the Notepad program and open it.
2) Type some text in the program.
Cyber Security Essentials Page 1 Effective date: 05 Mar 2021
3) Choose File > Save.
4) Navigate to Desktop.
5) Type Hash in the File name: field, and click Save.
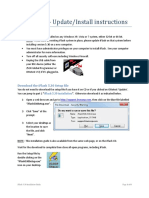
Task 2: Install HashCalc
1) Open a file explorer and locate the folder location of HashCalc in E Drive in the folder
EG2762.
2) Double click and run the setup.exe file inside.
3) Follow the installation wizard to install HashCalc.
4) Click Finish on the last screen, and close the README file if it opened. You may read
the file if you wish.
Cyber Security Essentials Page 2 Effective date: 05 Mar 2021
5) HashCalc is now installed and running.
Task 3: Calculate a hash of the Hash.txt file
1) Set the following items in HashCalc:
Data Format: File.
Data: Click the … button next to the Data field, navigate to the Desktop and
choose the Hash.txt file.
Uncheck HMAC.
Uncheck all hash types except MD5.
2) Click the Calculate button.
What is the value next to MD5?
418971d10406b135559a6edc067ca305
Cyber Security Essentials Page 3 Effective date: 05 Mar 2021
Task 4: Make a change to the Hash.txt file
1) Navigate to the Desktop and open the Hash.txt file.
2) Make a minor change to the text, such as deleting a letter, or adding a space or period.
3) Click File > Save, and close Notepad.
Task 5: Calculate a new hash of the Hash.txt file
1) Click the Calculate button in HashCalc again.
What is the value next to MD5?
________________________________________________________________________
Is the value different from the value recorded in Task 3?
yes_____________________________________________________________________
___
2) Place a check mark next to all of the hash types.
3) Click Calculate.
4) Notice that many of the hash types create a hash of a different length. Why?
_many of the hashes use a diff number of bits to produce the
hash____________________________________________________________________
___
Cyber Security Essentials Page 4 Effective date: 05 Mar 2021
You might also like
- IT0005-Laboratory-Exercise-3 - Data HashingNo ratings yetIT0005-Laboratory-Exercise-3 - Data Hashing6 pages
- LOPEZ YESSICA - 6 PARALELO A-Semana3 - Lab 21.1.6No ratings yetLOPEZ YESSICA - 6 PARALELO A-Semana3 - Lab 21.1.65 pages
- Answers to Problems for Information Security, 2nd Edition by Gurpreet DhillonNo ratings yetAnswers to Problems for Information Security, 2nd Edition by Gurpreet Dhillon7 pages
- EGL202 - Lab - 2 - Password Cracking (Student)No ratings yetEGL202 - Lab - 2 - Password Cracking (Student)12 pages
- 7.1 Data Integrity - Hashcalc: August 2009No ratings yet7.1 Data Integrity - Hashcalc: August 20095 pages
- Digital Forensics: Computer Forensics Analysis and ValidationNo ratings yetDigital Forensics: Computer Forensics Analysis and Validation11 pages
- CEH11 Lab Manual Module 20 - CryptographyNo ratings yetCEH11 Lab Manual Module 20 - Cryptography122 pages
- Introduction To Computer Forensics and HashingNo ratings yetIntroduction To Computer Forensics and Hashing35 pages
- Hashing: H (M) ". There Are Three Properties A Hash Function Should HaveNo ratings yetHashing: H (M) ". There Are Three Properties A Hash Function Should Have10 pages
- CO1508 Computer Systems & Security - Week 07 Cryptography - Hash Functions & Digital SignaturesNo ratings yetCO1508 Computer Systems & Security - Week 07 Cryptography - Hash Functions & Digital Signatures7 pages
- 2.1.8 Packet Tracer File and Data Integrity Checks Answer KeyNo ratings yet2.1.8 Packet Tracer File and Data Integrity Checks Answer Key4 pages
- Hash Function: Message Digest or Simply Hash ValuesNo ratings yetHash Function: Message Digest or Simply Hash Values20 pages
- Hacker HighSchool-Security Awareness For TeensNo ratings yetHacker HighSchool-Security Awareness For Teens192 pages
- Mastering Node.js Web Development: Go on a comprehensive journey from the fundamentals to advanced web development with Node.jsFrom EverandMastering Node.js Web Development: Go on a comprehensive journey from the fundamentals to advanced web development with Node.jsNo ratings yet
- STM32F7 Series System Arch Performance-En - dm00169764No ratings yetSTM32F7 Series System Arch Performance-En - dm0016976447 pages
- Network Layer: Logical Addressing: Dr. Kunwar Pal Dept. of CSE NIT JalandharNo ratings yetNetwork Layer: Logical Addressing: Dr. Kunwar Pal Dept. of CSE NIT Jalandhar58 pages
- Huawei FusionServer RH8100 V3 Technical PresentationNo ratings yetHuawei FusionServer RH8100 V3 Technical Presentation33 pages
- Booth's Multiplication Algorithm - Wikipedia, The Free Encyclopedia PDFNo ratings yetBooth's Multiplication Algorithm - Wikipedia, The Free Encyclopedia PDF5 pages
- IBM TS3100 TS3200 3573 L2U Manual User GuideNo ratings yetIBM TS3100 TS3200 3573 L2U Manual User Guide383 pages
- ED - 22 - 23 - Second - Midterm - A - ENG SolutionNo ratings yetED - 22 - 23 - Second - Midterm - A - ENG Solution6 pages
- Allegro® Sigrity® 16.62 - Windows Version: Installation GuideNo ratings yetAllegro® Sigrity® 16.62 - Windows Version: Installation Guide5 pages
- Configuring & Troubleshooting Windows Server 2008 Active Directory Domain ServicesNo ratings yetConfiguring & Troubleshooting Windows Server 2008 Active Directory Domain Services2 pages
- Multicore C Standard Template Library in A GeneratNo ratings yetMulticore C Standard Template Library in A Generat11 pages
- Answers to Problems for Information Security, 2nd Edition by Gurpreet DhillonAnswers to Problems for Information Security, 2nd Edition by Gurpreet Dhillon
- Digital Forensics: Computer Forensics Analysis and ValidationDigital Forensics: Computer Forensics Analysis and Validation
- Hashing: H (M) ". There Are Three Properties A Hash Function Should HaveHashing: H (M) ". There Are Three Properties A Hash Function Should Have
- CO1508 Computer Systems & Security - Week 07 Cryptography - Hash Functions & Digital SignaturesCO1508 Computer Systems & Security - Week 07 Cryptography - Hash Functions & Digital Signatures
- 2.1.8 Packet Tracer File and Data Integrity Checks Answer Key2.1.8 Packet Tracer File and Data Integrity Checks Answer Key
- Hash Function: Message Digest or Simply Hash ValuesHash Function: Message Digest or Simply Hash Values
- Mastering Node.js Web Development: Go on a comprehensive journey from the fundamentals to advanced web development with Node.jsFrom EverandMastering Node.js Web Development: Go on a comprehensive journey from the fundamentals to advanced web development with Node.js
- STM32F7 Series System Arch Performance-En - dm00169764STM32F7 Series System Arch Performance-En - dm00169764
- Network Layer: Logical Addressing: Dr. Kunwar Pal Dept. of CSE NIT JalandharNetwork Layer: Logical Addressing: Dr. Kunwar Pal Dept. of CSE NIT Jalandhar
- Huawei FusionServer RH8100 V3 Technical PresentationHuawei FusionServer RH8100 V3 Technical Presentation
- Booth's Multiplication Algorithm - Wikipedia, The Free Encyclopedia PDFBooth's Multiplication Algorithm - Wikipedia, The Free Encyclopedia PDF
- ED - 22 - 23 - Second - Midterm - A - ENG SolutionED - 22 - 23 - Second - Midterm - A - ENG Solution
- Allegro® Sigrity® 16.62 - Windows Version: Installation GuideAllegro® Sigrity® 16.62 - Windows Version: Installation Guide
- Configuring & Troubleshooting Windows Server 2008 Active Directory Domain ServicesConfiguring & Troubleshooting Windows Server 2008 Active Directory Domain Services
- Multicore C Standard Template Library in A GeneratMulticore C Standard Template Library in A Generat