Cycubix CCSP Mindmap Aug2019
Cycubix CCSP Mindmap Aug2019
Uploaded by
gavas2000Copyright:
Available Formats
Cycubix CCSP Mindmap Aug2019
Cycubix CCSP Mindmap Aug2019
Uploaded by
gavas2000Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Copyright:
Available Formats
Cycubix CCSP Mindmap Aug2019
Cycubix CCSP Mindmap Aug2019
Uploaded by
gavas2000Copyright:
Available Formats
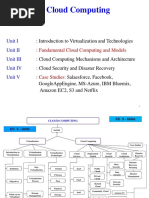
A.
1 Cloud Computing Definitions
A.2 Cloud Computing Roles
A. Understand Cloud Computing Concepts
A.3 Key Computing Characteristics
A.4 Building Block Technologies
B.1 Cloud Computing Activities
B.2 Cloud Service Capabilities
B.3 Cloud Service Categories
B. Describe Cloud Reference Architecture
B.4 Cloud Deployment Models
B.5 Cloud Shared Considerations
B.6 Impact of Related Technologies
C.1 Cryptography and Key Management
1 - Cloud Concepts, Architecture and Design (17%) C.2 Access Control
C.3 Data and Media Sanitisation
C. Understand Security Concepts Relevant to Cloud Computing
C.4 Network Security
C.5 Virtualisation Security
C.6 Common Threats
D.1 Cloud Secure Data Lifecycle
D.2 Cloud based Disaster Recovery (DR) and Business
Continuity (BC) planning
D. Understand Design Principles of Secure Cloud Computing D.3 Cost/Benefit Analysis
D.4 Functional Security Requirements
D5. Security Considerations for Different Cloud Categories
E.1 Verification Against Criteria
E. Evaluate Cloud Service Providers
E.2 System/Subsystem Product Certifications
A.1 Cloud Data Life Cycle Phases
A. Describe Cloud Data Concepts
A.2 Data Dispersion
B.1 Storage Types
B. Design and Implement Cloud Data Storage Architectures
B.2 Threats to Storage Types
C.1 Encryption and Key Management
C.2 Hashing
C.3 Masking
C. Design and Apply Data Security Technologies and Strategies C.4 Tokenisation
C.5 Data Loss Prevention (DLP)
C.6 Data Obfuscation
C7. Data De-identification
D.1 Structured Data
D. Implement Data Discovery
2 - Cloud Data Security (19%) D.2 Unstructured Data
E.1 Mapping
E. Implement Data Classification E.2 Labeling
E.3 Sensitive data
F.1 Objectives
F. Design and Implement Information Rights Management (IRM)
F.2 Appropriate Tools
G.1 Data Retention Policies
G.2 Data Deletion Procedures and Mechanisms
G. Plan and Implement Data Retention, Deletion and Archiving
Policies
G.3 Data Archiving Procedures and Mechanisms
G.4 Legal Hold
H.1 Definition of Event Sources and Requirement of Identity
Attribution
H. Design and Implement Auditability, Traceability and
Accountability of Data Events H.2 Logging, Storage and Analysis of Data Events
H.3 Chain of Custody and Non-repudiation
A.1 Physical Environment
A.2 Network and Communications
A.3 Compute
A. Comprehend Cloud Infrastructure Components
A.4 Virtualisation
A.5 Storage
A.6 Management Plan
B.1 Logical Design
B. Design a Secure Data Center B.2 Physical Design
B.3 Environmental Design
C.1 Risk Assessment and Analysis
C.2 Cloud Vulnerabilities, Threats and
Attacks
C. Analyze Risks Associated with Cloud Infrastructure
3 - Cloud Platform and Infrastructure Security (17%) C.3 Virtualization Risks
C.4 Counter-measure Strategies
D.1 Physical and Environmental Protection
D.2 System and Communication Protection
D. Design and Plan Security Controls D.3 Virtualization Systems Protection
D.4 Identification, Authentication and Authorization
in Cloud Infrastructure
D.5 Audit Mechanismsn
E.1 Risks Related to the Cloud Environment
E.2 Business Requirements
E. Plan Disaster Recovery (DR) and Business Continuity (BC) E.3 Business Continuity/Disaster Recovery
Strategy
E.4 Creation, Implementation and Testing
of Plan
A1. Cloud Development Basics
A. Advocate Training and Awareness for Application Security A2. Common Pitfalls
A3. Common Cloud Vulnerabilities
B1. Business Requirements
B. Describe the Secure Software Development Life Cycle
(SDLC) Process
B2. Phases and Methodologies
C1. Avoid Common Vulnerabilities During
Development
C2. Cloud-specific Risks
C. Apply the Secure Software Development Life Cycle (SDLC) C3. Quality Assurance
C4. Threat Modeling
C5. Software Configuration Management and
Versioning
D1. Functional Testing
D. Apply Cloud Software Assurance and Validation
D2. Security Testing Methodologies
4. Cloud Application Security (17%)
E1. Approved Application Programming Interfaces (API)
E2. Supply-chain Management
E. Use Verified Secure Software
E3. Third Party Software Management
E4.Validated Open Source Software
F1. Supplemental Security components
F2. Cryptography
F. Comprehend the Specifics of Cloud Application Architecture
F3. Sandboxing
F4. Application Virtualization and Orchestration
CCSP Domains
August 2019 G1. Federated Identity
G2. Identity Providers
G. Design Appropriate Identity and Access Management (IAM) G3. Single Sign-On (SSO)
Solutions
G4. Multi-factor Authentication
G5. Cloud Access Security Broker (CASB)
A1. Hardware Specific Security Configuration Requirements
A2. Installation and Configuration of Virtualization Management
Tools
A. Implement and Build Physical and Logical Infrastructure for
Cloud Environment A3.Virtual Hardware Specific Security Configuration
Requirements
A4. Installation of Guest Operating System (OS) Virtualization
Toolsets
B1. Configure Access Control for Local and Remote
Access
B2. Secure Network Configuration
B3. Operating System (OS) Hardening Through the
B. Operate Physical and Logical Infrastructure for Cloud Application of Baselines
Environment
B4. Availability of Stand-Alone Hosts
B5. Availability of Clustered Hosts
B6. Availability of Guest Operating System (OS)
C1. Access Controls for Remote Access
C2. Operating System (OS) Baseline Compliance
Monitoring and Remediation
C3. Patch Management
C4. Performance and Capacity Monitoring
C. Manage Physical and Logical Infrastructure for Cloud
Environment
C5. Hardware Monitoring
C6. Configuration of Host and Guest Operating
System (OS) Backup and Restore Functions
C7. Network Security Controls
C8. Management Plan
D1. Change Management
D2. Continuity Management
5. Cloud Security Operations (17%)
D3. Information Security Management
D4. Continual Service Improvement Management
D5. Incident Management
D6. Problem Management
D. Implement Operational Controls and Standards
D7. Release Management
D8. Deployment Management
D9. Configuration Management
D10. Service level Management
D11. Availability Management
D12. Capacity Management
E1. Forensic Data Collection Methodologies
E. Support Digital Forensics E2. Evidence Management
E3. Collect, Acquire and Preserve Digital Evidence
F1.Vendors
F2. Customers
F. Manage Communication with Relevant Parties F3. Partners
F4. Regulators
F5. Other Stakeholders
G1. Security Operations Center (SOC)
G2. Monitoring of Security Controls
G. Manage Security Operations
G3. Log Capture and Analysis
G4. Incident Management
A1. Conflicting International Legislation
A2. Evaluation of Legal Risks Specific to Cloud
Computing
A. Articulate Legal Requirements and Unique Risks within the
Cloud Environment A3. Legal Framework and Guidelines
A4. eDiscovery
A5. Forensics Requirements
B1. Difference Between Contractual and Regulated Private Data
B2. Country-Specific Legislation Related to Private Data
B. Understand Privacy Issues
B3. Jurisdictional Differences in Data Privacy
B4. Standard Privacy Requirements
C1. Internal and External Audit Controls
C2. Impact of Audit Requirements
C3. Identify Assurance Challenges of Virtualization
and Cloud
C4. Types of Audit Reports
C5. Restrictions of Audit Scope Statements
C6. Gap Analysis
C. Understand Audit Process, Methodologies, and Required C7. Audit Planning
Adaptations for a Cloud Environment
C8. Internal Information Security Management System (ISMS)
6. Legal, Risk and Compliance (13%)
C9. Internal Information Security Controls System
C10. Policies
C11. Identification and Involvement of Relevant
Stakeholders
C12. Specialized Compliance Requirements for
Highly-Regulated Industries
C13. Impact of Distributed Information Technology
(IT) Model
D1. Assess Providers Risk Management Programs
D2. Difference Between Data Owner/Controller vs.
Data Custodian/Processor
D3. Regulatory Transparency Requirements
D. Understand Implications of Cloud to Enterprise Risk
Management D4. Risk Treatment
D5. Different Risk Frameworks
D6. Metrics for Risk Management
D7. Assessment of Risk Environment
E1. Business Requirements
E2.Vendor Management
E. Understand Outsourcing and Cloud Contract Design
E3. Contract Management
E4. Supply-chain Management
You might also like
- 390 - Certified Cloud Security Professional CCSP - 1572385660 PDF100% (1)390 - Certified Cloud Security Professional CCSP - 1572385660 PDF231 pages
- Exam C1000-100 IBM Cloud Solution Architect v4 Sample TestNo ratings yetExam C1000-100 IBM Cloud Solution Architect v4 Sample Test4 pages
- Certified Cloud Security Professional (CCSP) : Study Guide100% (1)Certified Cloud Security Professional (CCSP) : Study Guide182 pages
- Case Study Walmart's Everyday Hiring StrategyNo ratings yetCase Study Walmart's Everyday Hiring Strategy4 pages
- Cloud Computing MCQ Unit I IntroductionNo ratings yetCloud Computing MCQ Unit I Introduction52 pages
- Azure_Fundamentals_(AZ-900)_2023_D1_ProjectsNo ratings yetAzure_Fundamentals_(AZ-900)_2023_D1_Projects14 pages
- A Summary On Issues and Challenges in Private Clouds: Sadish Kumar MANOHARANNo ratings yetA Summary On Issues and Challenges in Private Clouds: Sadish Kumar MANOHARAN8 pages
- T-27 - 2 Cloud Computing Concepts and Benefits - Konten MateriNo ratings yetT-27 - 2 Cloud Computing Concepts and Benefits - Konten Materi39 pages
- Cloud Security Using Blowfish and Key Management Encryption AlgorithmNo ratings yetCloud Security Using Blowfish and Key Management Encryption Algorithm4 pages
- A Review of Multiple Layer Security of Cloud Server: AbstractNo ratings yetA Review of Multiple Layer Security of Cloud Server: Abstract4 pages
- Cloud Computing MCQ (Multi Choice Questions) - JavatpointNo ratings yetCloud Computing MCQ (Multi Choice Questions) - Javatpoint60 pages
- Unit-II - FUNDAMENTAL CLOUD COMPUTING AND MODELS100% (1)Unit-II - FUNDAMENTAL CLOUD COMPUTING AND MODELS68 pages
- Cloud Computing Security:: Amazon Web ServiceNo ratings yetCloud Computing Security:: Amazon Web Service5 pages
- Recent Trends On Security Issues in Multi-Cloud Computing: A SurveyNo ratings yetRecent Trends On Security Issues in Multi-Cloud Computing: A Survey5 pages
- CEC315 - Introduction To Cloud Computing - Module 1No ratings yetCEC315 - Introduction To Cloud Computing - Module 128 pages
- Booklet of Handouts - Cloud Computing V4No ratings yetBooklet of Handouts - Cloud Computing V4196 pages
- 1100+ TOP Cloud Computing Objective Questions-Answers MCQsNo ratings yet1100+ TOP Cloud Computing Objective Questions-Answers MCQs359 pages
- Cloud-Computing-Sandeep-Bhowmik-Edisi-1-2017No ratings yetCloud-Computing-Sandeep-Bhowmik-Edisi-1-201715 pages
- Part C: Course Specific: 40 (As Prescribed by AKTU) 4 Jyotirmay - Patel@srms - Ac.inNo ratings yetPart C: Course Specific: 40 (As Prescribed by AKTU) 4 Jyotirmay - Patel@srms - Ac.in17 pages
- Cloud Computing MCQ (Multi Choice Questions) - JavatpointNo ratings yetCloud Computing MCQ (Multi Choice Questions) - Javatpoint66 pages
- The Cloud: Information Technology For The WorkplaceNo ratings yetThe Cloud: Information Technology For The Workplace33 pages
- Cloud Computing An Introduction 9789386286918 9781683920922 2017934712 1561571571 1683920929 - CompressNo ratings yetCloud Computing An Introduction 9789386286918 9781683920922 2017934712 1561571571 1683920929 - Compress223 pages
- Various Security Threats and Their Solutions in Cloud ComputingNo ratings yetVarious Security Threats and Their Solutions in Cloud Computing7 pages
- A Two Level-Security Model For Cloud Computing Based On The Biometric Features and Multi-Level EncryptionNo ratings yetA Two Level-Security Model For Cloud Computing Based On The Biometric Features and Multi-Level Encryption13 pages
- CCIE™ and CCDE™ Written Exam Evolving Technologies Study GuideNo ratings yetCCIE™ and CCDE™ Written Exam Evolving Technologies Study Guide39 pages
- Standard Chartered Q2 Quarterly Outlook 2024 1712522269No ratings yetStandard Chartered Q2 Quarterly Outlook 2024 171252226935 pages
- A Quantitative Approach To Problem Solving 1No ratings yetA Quantitative Approach To Problem Solving 180 pages
- General Electric After Jack Welch: Succession and Success?: Pier A. Abetti0% (1)General Electric After Jack Welch: Succession and Success?: Pier A. Abetti14 pages
- Importance of Business Policy From The Viewpoint of Career ChoiceNo ratings yetImportance of Business Policy From The Viewpoint of Career Choice5 pages
- Strategic and Operational Plan (2020-2022)No ratings yetStrategic and Operational Plan (2020-2022)11 pages
- Cultural Changes: Recent Launch System ProposalsNo ratings yetCultural Changes: Recent Launch System Proposals76 pages
- Prajeesh Raghavan: Personal Details Nationality: Date of Birth: Marital StatusNo ratings yetPrajeesh Raghavan: Personal Details Nationality: Date of Birth: Marital Status4 pages
- SGS - Group01 - Le Ho Nhat Ha - S4030854 MP ASM3No ratings yetSGS - Group01 - Le Ho Nhat Ha - S4030854 MP ASM319 pages
- Guiding Documents For Zonal & Sub-Zonal & Port Offices 17.06.2011 PDFNo ratings yetGuiding Documents For Zonal & Sub-Zonal & Port Offices 17.06.2011 PDF483 pages
- MICVV Write-Up: Name-Parth Shah Roll Number - 201832075 Interview - 13No ratings yetMICVV Write-Up: Name-Parth Shah Roll Number - 201832075 Interview - 131 page
- CHAPTER #1: Entrepreneurship and The Entrepreneur: Entrepreneurial ManagementNo ratings yetCHAPTER #1: Entrepreneurship and The Entrepreneur: Entrepreneurial Management4 pages
- MOU - Digify PRO Online 2024 NIGERIA SignedNo ratings yetMOU - Digify PRO Online 2024 NIGERIA Signed5 pages
- 2024 11 4 10 38 55 Statement - 1712812135936No ratings yet2024 11 4 10 38 55 Statement - 17128121359365 pages
- Spare Parts Catalogue Castel 2020 en CompressedNo ratings yetSpare Parts Catalogue Castel 2020 en Compressed90 pages