18 Zone+Lab Fortigate
18 Zone+Lab Fortigate
Uploaded by
Garudmani PavanCopyright:
Available Formats
18 Zone+Lab Fortigate
18 Zone+Lab Fortigate
Uploaded by
Garudmani PavanOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Copyright:
Available Formats
18 Zone+Lab Fortigate
18 Zone+Lab Fortigate
Uploaded by
Garudmani PavanCopyright:
Available Formats
https://docs.fortinet.com/document/fortigate/7.4.
1/administration-guide/116821/zone
Open above link, and read the doc after completing below lab reading, link explanation is very
clear then below lab and you can see CLI config as well
Read lab-17, to understand easily
Zone:
o Zones are a group of one or more physical or virtual FortiGate firewall interfaces.
o To simplify the policy configuration, you can group interfaces into logical zones.
o That you can apply the security policies to control inbound and outbound traffic.
o Grouping interfaces, VLAN subinterfaces into zones simplifies creation security policies.
o Where number of network segments can use same policy settings & protection profiles.
o When add zone, select names of interfaces and VLAN subinterfaces to add to the zone.
o Each interface still has its own address and routing is still done between the interfaces.
o You can use FortiGate Firewall security policies to control the flow of intra-zone traffic.
o Admin making separate security policies make simpler by adding interfaces to a zone.
o However, you should note that an interface in a zone cannot be referenced individually.
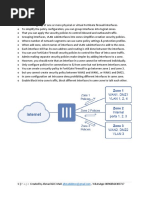
o Only configure policies for connections to & from zone but not between interfaces zone. not b/w interfaces in
o You can create a security policy in FortiGate Firewall to go between zone 1 and zone 3. the zone
o but you cannot create security policy between WAN2 and WAN1, or WAN1 and DMZ1.Refer below digaram.
o In zone configuration set intrazone deny prohibiting different interfaces in same zone.
o Enable Block intra-zone traffic, block different interfaces in same zone to talk each other.
Zone will help you to
minimize policy
1 | P a g e Created by Ahmad Ali E-Mail: ahmadalimsc@gmail.com , WhatsApp: 00966564303717
NOT SHOWING SUB
INTERFACE VLANS IN
INTERFACE MEMBERS
OPTION, BECAISE FW got 192.168.100.200 MGMT IP which is
THOSE ARE USED IN given by MGMT PC present below
POLICY
Zone Lab:
First let’s delete the previously created Firewall policies for VLAN 40 and VLAN 50.
To create a zone in Go to Network > Interfaces Click Create New > Zone.
Also you can right click
and delete policy
2 | P a g e Created by Ahmad Ali E-Mail: ahmadalimsc@gmail.com , WhatsApp: 00966564303717
Configure the Name and add the Interface Members in our case VLAN40 & VLAN50.
Enable Block intra-zone traffic, block different interfaces in same zone to talk each other.
Create a firewall policy, go to Policy & Objects > Firewall Policy, and click Create New.
3 | P a g e Created by Ahmad Ali E-Mail: ahmadalimsc@gmail.com , WhatsApp: 00966564303717
Test and Verification:
Try to access any website from SRV1 in this case facebook.com it’s working.
Now, try to access any website from SRV2 in this case twitter.com it’s working.
4 | P a g e Created by Ahmad Ali E-Mail: ahmadalimsc@gmail.com , WhatsApp: 00966564303717
Go to Dashboard> FortiView Sources to display and verify VLAN40 & VLAN50 source IP.
Go to Dashboard> FortiView Destinations to display and verify the destinations domains & IP.
Go to Dashboard> FortiView Polices to display and verify security polices has been hits & used.
5 | P a g e Created by Ahmad Ali E-Mail: ahmadalimsc@gmail.com , WhatsApp: 00966564303717
Go to Dashboard> FortiView Sessions to display and verify all VLANs visited links sessions.
Go to Log & Report> Forward Traffic to display and verify all VLANs visited links sessions.
6 | P a g e Created by Ahmad Ali E-Mail: ahmadalimsc@gmail.com , WhatsApp: 00966564303717
You might also like
- Examen para Sophos AngelDocument19 pagesExamen para Sophos AngelCarlos AynaguanoNo ratings yet
- Lab 5 Configuring Security Policy Rules and NAT RulesDocument51 pagesLab 5 Configuring Security Policy Rules and NAT RulesAnkita SinghNo ratings yet
- IBM WebSphere Application Server Interview Questions You'll Most Likely Be AskedFrom EverandIBM WebSphere Application Server Interview Questions You'll Most Likely Be AskedNo ratings yet
- FreeGate Bypass SoftwareDocument11 pagesFreeGate Bypass SoftwareSrishti Sharma Mishra100% (1)
- 01 - Create A Virtual Machine Using Azure PortalDocument11 pages01 - Create A Virtual Machine Using Azure PortalAnupam MalikNo ratings yet
- StratumFive - Thrane Thrane TT-3000SSA SSAS ConfigurationDocument1 pageStratumFive - Thrane Thrane TT-3000SSA SSAS ConfigurationRobin LalNo ratings yet
- 11 Success Drivers in NPD PDFDocument13 pages11 Success Drivers in NPD PDFAnnisa Utami PratiwiNo ratings yet
- Zone LabDocument6 pagesZone Labmanoj kumarNo ratings yet
- Lab 2 - Creating A SOHO ConfigurationDocument13 pagesLab 2 - Creating A SOHO Configurationrashmi mNo ratings yet
- Configuring A MikroTik Router From Start To FinishDocument16 pagesConfiguring A MikroTik Router From Start To FinishMirko MirkovicNo ratings yet
- Paloalto Subinterface SOPDocument13 pagesPaloalto Subinterface SOPankitNo ratings yet
- EDTECH 552 - Lab 5Document22 pagesEDTECH 552 - Lab 5Brian MatthewNo ratings yet
- Configuring DMZ On The RV34x Series RouterDocument29 pagesConfiguring DMZ On The RV34x Series RouterPhilip GovinaNo ratings yet
- Srx210 Getting Started GuideDocument4 pagesSrx210 Getting Started GuideAnonymous B6yEOYINo ratings yet
- Mini-Lab - Student GuideDocument14 pagesMini-Lab - Student GuideDiego Fernando Solis H100% (1)
- Pan Sasev1 Lab 01Document29 pagesPan Sasev1 Lab 01redesespochNo ratings yet
- Quick Start Guide : IP Address ConfigurationDocument2 pagesQuick Start Guide : IP Address ConfigurationFredy Turpo TiconaNo ratings yet
- Wireless Communication FileDocument38 pagesWireless Communication FilerishabhNo ratings yet
- 91 Iq VBBHAp SDocument10 pages91 Iq VBBHAp Skey jeyNo ratings yet
- Full Stack - Student Guide MERAKIDocument28 pagesFull Stack - Student Guide MERAKInetworking.consulting1No ratings yet
- CHLS-PANW-150-VIRTUAL - Lab GuideDocument25 pagesCHLS-PANW-150-VIRTUAL - Lab GuideMiguel GarciaNo ratings yet
- LSVPN Palo AltoDocument32 pagesLSVPN Palo AltoHarshit BhattaramNo ratings yet
- Home Network Security GuideDocument13 pagesHome Network Security GuidefabiandumitruroNo ratings yet
- Meraki SDWAN Exercise SMBDocument7 pagesMeraki SDWAN Exercise SMBNUR BALQIS BINTI IZHARNo ratings yet
- How To Split A Zone in Sub ZonesDocument2 pagesHow To Split A Zone in Sub ZonespalimariumNo ratings yet
- BridgingDocument1 pageBridgingDennisFielNo ratings yet
- Vlan in MikrotikDocument1 pageVlan in MikrotikDennis FielNo ratings yet
- SolaX Pocket WiFi SetDocument3 pagesSolaX Pocket WiFi SetRUNARUNNo ratings yet
- Procurve and Siemens PhoneDocument12 pagesProcurve and Siemens PhoneSteggosNo ratings yet
- WiFi Configuration and Security Settings of ZTE-ZXDSL-531 ADSL ModemDocument16 pagesWiFi Configuration and Security Settings of ZTE-ZXDSL-531 ADSL ModemKudeep Garg100% (1)
- Sophos XG Firewall Virtual Appliance: Getting Started GuideDocument10 pagesSophos XG Firewall Virtual Appliance: Getting Started GuideHadi AlatrashNo ratings yet
- FortiGate FGT2 12 Virtual DomainsDocument31 pagesFortiGate FGT2 12 Virtual DomainsVlad Alexandru Ionut100% (1)
- FGT2 12 Virtual DomainsDocument31 pagesFGT2 12 Virtual Domainsrobertlatino16No ratings yet
- Palo Alto and The Virtual WireDocument8 pagesPalo Alto and The Virtual WirebrilliancsysNo ratings yet
- Report - Chapter 6: FirewallDocument11 pagesReport - Chapter 6: FirewallDaniel PonsNo ratings yet
- Section 1 - Configuration-101Document30 pagesSection 1 - Configuration-101tusharf5certNo ratings yet
- Untitled 2Document13 pagesUntitled 2sheraz salimNo ratings yet
- Project Wifi JammerDocument13 pagesProject Wifi JammerVenkata Krishna Kode100% (2)
- 45-Bridge Mode LabDocument18 pages45-Bridge Mode Labsunny mauryaNo ratings yet
- Cyber Security PDFDocument88 pagesCyber Security PDFRakesh EnjalaNo ratings yet
- Lab 2 Networking DevicesDocument13 pagesLab 2 Networking DevicesramanshankarNo ratings yet
- Cable Modem Modification How-ToDocument15 pagesCable Modem Modification How-ToKalyan KantiNo ratings yet
- Cyberoam VPN ConfigDocument25 pagesCyberoam VPN ConfigajaynagarNo ratings yet
- Typical DMZ Configuration WithFTP SMTP and DNS ServersDocument5 pagesTypical DMZ Configuration WithFTP SMTP and DNS ServersDony Suryo HandoyoNo ratings yet
- Cisco Meraki SD-WAN: Walk-In Self-Paced Lab Student GuideDocument12 pagesCisco Meraki SD-WAN: Walk-In Self-Paced Lab Student GuideDmitri DicusarNo ratings yet
- Lecture 7 - VLANDocument45 pagesLecture 7 - VLANAnnatolia ErastoNo ratings yet
- Wireless LAN FlexConnectDocument11 pagesWireless LAN FlexConnectaaandradeNo ratings yet
- Getting Started-Layer 3 SubinterfacesDocument8 pagesGetting Started-Layer 3 SubinterfacesRoman BestuzhevNo ratings yet
- Meraki360 - Lab Guide: On-Site VersionDocument16 pagesMeraki360 - Lab Guide: On-Site VersionVigneshwaran NairNo ratings yet
- MTSM-4 Panel Lite InstallationDocument12 pagesMTSM-4 Panel Lite Installationleonardo333555No ratings yet
- Contact - Modem Setup - TP-Link HX510 MeshDocument2 pagesContact - Modem Setup - TP-Link HX510 Meshgeecat911No ratings yet
- Lab 1 Connect To The Management NetworkDocument18 pagesLab 1 Connect To The Management NetworkAnkita SinghNo ratings yet
- Mikrotik Setup Guest (Vlan) WifiDocument12 pagesMikrotik Setup Guest (Vlan) WifiKhodor AkoumNo ratings yet
- Firewall SettingsDocument6 pagesFirewall Settingsgestradag-1No ratings yet
- Cybersecurity Foundations Lab 3: Creating A Zero Trust EnvironmentDocument28 pagesCybersecurity Foundations Lab 3: Creating A Zero Trust EnvironmentJefry Gutiérrez CelisNo ratings yet
- CR - by HadilDocument11 pagesCR - by Hadilaymen.ghazouaniNo ratings yet
- Business Intent Overlays - SD-WAN Orchestrator DocsDocument1 pageBusiness Intent Overlays - SD-WAN Orchestrator DocsMicaiah KasekeNo ratings yet
- Mikrotik - Zone Based FirewallDocument15 pagesMikrotik - Zone Based Firewalljwtven100% (1)
- Lab 1 Creating A Zero Trust Environment PDFDocument24 pagesLab 1 Creating A Zero Trust Environment PDFJeevan Teza YadavNo ratings yet
- Lab 7: 802.1X: Wireless NetworksDocument13 pagesLab 7: 802.1X: Wireless NetworksJosel ArevaloNo ratings yet
- Mini-Lab Full-Stack Student Guide 2020Document24 pagesMini-Lab Full-Stack Student Guide 2020s0203160No ratings yet
- Hacking : A Comprehensive, Step-By-Step Guide to Techniques and Strategies to Learn Ethical Hacking with Practical Examples to Computer Hacking, Wireless Network, Cybersecurity and Penetration TestingFrom EverandHacking : A Comprehensive, Step-By-Step Guide to Techniques and Strategies to Learn Ethical Hacking with Practical Examples to Computer Hacking, Wireless Network, Cybersecurity and Penetration TestingNo ratings yet
- FCSS—Enterprise Firewall 7.4 Administrator Exam PreparationFrom EverandFCSS—Enterprise Firewall 7.4 Administrator Exam PreparationNo ratings yet
- Gerber - Pattern Making (PDS) : School of Fashion & TextilesDocument1 pageGerber - Pattern Making (PDS) : School of Fashion & TextilesAnonymous qaI31HNo ratings yet
- Qual Comm 2016Document15 pagesQual Comm 2016Manoj Kumar Gunturi100% (2)
- UDP - User Datagram ProtocolDocument7 pagesUDP - User Datagram ProtocolPeter R. Egli100% (2)
- MS Project 2013-16 Advanced WorkbookDocument86 pagesMS Project 2013-16 Advanced Workbookrvnkrish24No ratings yet
- Function Oriented Software DesignDocument4 pagesFunction Oriented Software DesignSathwik ReddyNo ratings yet
- Mct702 All UnitsDocument747 pagesMct702 All UnitsMOHITNo ratings yet
- KK Bullet Constraints-Builder PDFDocument7 pagesKK Bullet Constraints-Builder PDFrigaschNo ratings yet
- Getting Around Your A-ClassroomDocument17 pagesGetting Around Your A-ClassroomSK Tay-ac RosarioNo ratings yet
- Software DefinitionDocument45 pagesSoftware DefinitionJohnNo ratings yet
- Learning Webrtc: The Ultimate Getting Started GuideDocument59 pagesLearning Webrtc: The Ultimate Getting Started GuideweihnachtlicheNo ratings yet
- Calibration Eraser-C-EnDocument14 pagesCalibration Eraser-C-Enapi-538691317No ratings yet
- Subject Code CS-305: (Object Oriented Programming & Methodology)Document33 pagesSubject Code CS-305: (Object Oriented Programming & Methodology)poorvaNo ratings yet
- A Comprehensive Overview of Large Language Models: A B, C, D, E, F, G F, G H, J I JDocument47 pagesA Comprehensive Overview of Large Language Models: A B, C, D, E, F, G F, G H, J I Jdeepanshumishra1mgNo ratings yet
- Bio Chips: Presented byDocument19 pagesBio Chips: Presented byShruthi UpparNo ratings yet
- Mastering Markdown GitHub GuidesDocument6 pagesMastering Markdown GitHub GuidesfakkeloginNo ratings yet
- RBIS Administrator Manual v1.0Document66 pagesRBIS Administrator Manual v1.0JoyceNo ratings yet
- Google App EngineDocument14 pagesGoogle App EnginePARAGJAIN000100% (1)
- A Hybrid Modeling Approach For Predicting The Educational Use of Mobile Cloud Computing Services in Higher EducationDocument7 pagesA Hybrid Modeling Approach For Predicting The Educational Use of Mobile Cloud Computing Services in Higher Educationhuyen vuNo ratings yet
- 1 Shashank GuptaDocument2 pages1 Shashank GuptaNamit JainNo ratings yet
- Solution For HW#2: H/W Summary (20 Points) : ECE473/ECE573, Microprocessor System DesignDocument2 pagesSolution For HW#2: H/W Summary (20 Points) : ECE473/ECE573, Microprocessor System DesignVictor LoongNo ratings yet
- Syncserver - s600 User Manual PDFDocument332 pagesSyncserver - s600 User Manual PDFChuan Yau TanNo ratings yet
- Ahmad Nouman ChishtiDocument2 pagesAhmad Nouman ChishtiAyush AgarwalNo ratings yet
- Big Data CH 1Document66 pagesBig Data CH 1er.riteshtuladharNo ratings yet
- 03-20-2024 16.44.11Document28 pages03-20-2024 16.44.11wamo narcisseNo ratings yet
- Patrol Console Server and Rtserver: Getting StartedDocument324 pagesPatrol Console Server and Rtserver: Getting Started你好No ratings yet
- مقدمة في النباتاتDocument20 pagesمقدمة في النباتاتaljss.9797No ratings yet
- Lecture04 ArchitecturesDocument28 pagesLecture04 ArchitecturesSai Sukruth GoudNo ratings yet