Network Simulation Using OPNET
Uploaded by
Tema HassanNetwork Simulation Using OPNET
Uploaded by
Tema HassanNetwork simulation Using
OPNET
In the network research area, it is very costly
to deploy a complete test bed containing
multiple networked computers, routers and
data links to validate and verify a certain
network protocol or a specific network
algorithm.
The
network
simulators
in
these
circumstances save a lot of money and time
in accomplishing this task.
Network simulators are also particularly
useful in allowing the network designers to
test new networking protocols or to change
the existing protocols in a controlled and
reproducible manner.
Computer assisted simulation can model
hypothetical and real-life objects or activities
on a computer so that it can be studied to see
how the system function.
Different variables can be used to predict the
behavior of the system. Computer simulation can be
used to assist the modeling and analysis in many
natural systems.
since network technologies is keeping developing
very fast and so many different organizations
participate in the whole process and they have
different technologies or products running on
different software on the Internet. That is why the
network simulations always require open platforms
which should be scalable enough to include different
efforts and different packages in the simulations of
the whole network.
Generally a network simulator will comprise
of a wide range of networking technologies
and protocols and help users to build
complex networks from basic building blocks
like clusters of nodes and links. With their
help, one can design different network
topologies using various types of nodes such
as end-hosts, hubs, network bridges,
routers, etc.
Network simulation and
simulator
Generally speaking, network simulators try to model
the real world networks.
The principal idea is that if a system can be modeled,
then features of the model can be changed and the
corresponding results can be analyzed.
As the process of model modification is relatively
cheap than the complete real implementation, a
wide variety of scenarios can be analyzed at low cost
(relative to making changes to a real network).
However, network simulators are not perfect. They
can not perfectly model all the details of the
networks. However, if well modeled, they will be
close enough so as to give the researcher a
meaningful insight into the network under test, and
how changes will affect its operation.
Simulation and emulation
In the research area of computer and communications
networks, simulation is a useful technique since the
behavior of a network can be modeled by calculating
the interaction between the different network
components (they can be end-host or network entities
such as routers, physical links or packets) using
mathematical formulas.
They can also be modeled by actually or virtually
capturing and playing back experimental observations
from a real production networks. After we get the
observation data from simulation experiments, the
behavior of the network and protocols supported can
then be observed and analyzed in a series of offline
test experiments.
All kinds of environmental attributes can also be
modified in a controlled manner to assess how the
network can behave under different parameters
Simulation and emulation
Another characteristic of network simulation that worth
noticing is that the simulation program can be used
together with different applications and services in order to
observe end-to-end or other point-to-point performance in
the networks.
Network emulation, however, means that network under
planning is simulated in order to assess its performance or
to predict the impact of possible changes, or optimizations.
The major difference lying between them is that a network
emulator means that end-systems such as computers can
be attached to the emulator and will act exactly as they
are attached to a real network.
The major point is that the network emulator's job is to
emulate the network which connects end-hosts, but not the
end-hosts themselves.
Type of network
simulators
Different types of network simulators can be categorized
and explained based on some criteria such as if they are
commercial or free, or if they are simple ones or complex
ones.
Commercial and open source simulators. Some of the
network simulators are commercial which means that they
would not provide the source code of its software or the
affiliated packages to the general users for free. All the
user s have to pay to get the license to use their software
or pay to order specific packages for their own specific
usage requirements. One typical example is the OPNET
[OPNET].
Commercial simulator has its advantage and disadvantage.
The advantage is that it generally has complete and up-todate documentations and they can be consistently
maintained by some specialized staff in that company.
However, the open source network simulator is
disadvantageous in this aspect, and generally there are not
Type of network
simulators
the open source network simulator has the advantage that
everything is very open and everyone or organization can
contribute to it
OPNET
OPNET ' s software environment is called (Modeler), which
is specialized for network research and development. It can
be flexibly used to study communication networks,
devices, protocols, and applications.
Because of the fact of being a commercial software
provider, OPNET offers relatively much powerful visual or
graphical support for the users.
The graphical editor interface can be used to build network
topology and
entities from the application layer to the physical layer.
Object-oriented programming technique is used to create
the mapping from the graphical design to the
implementation of the real systems.
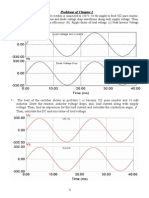
An example of the graphical GUI of OPNET can be seen in
figure 1. We can see all the topology configuration and
simulation results can be presented very intuitively and
visually. The parameters can also be adjusted and the
experiments can be repeated easily through easy
OPNET
OPNET
OPNET is based on a mechanism called discrete event
system which means that the system behavior can
simulate by modeling the events in the system in the order
of the scenarios the user has set up.
Hierarchical structure is used to organize the networks. As
other
network
simulators,
OPNET
also
provides
programming tools for users to define the packet format of
the protocol. The programming tools are also required to
accomplish the tasks of defining the state transition
machine, defining network model and the process module.
As of all, OPNET is a popular simulator used in industry for
network research and development. The GUI interface and
the programming tools are also useful to help the user to
build the system they want.
OPNET Main features
1.
2.
3.
4.
5.
6.
7.
8.
9.
OPNET inherently has three main functions: modeling,
simulating, and analysis. For modeling, it provides intuitive
graphical environment to create all kinds of models of
protocols.
For analysis, the simulation results and data can be
analyzed and displayed very easily. User friendly graphs,
charts, statistics, and even animation can be generated b y
OPNET for users ' convenience.
Fast discrete event simulation engine
Lot of component library with source code
Object-oriented modeling
Hierarchical modeling environment
32-bit and 64-bit graphical user interface
Discrete Event, Hybrid, and Analytical simulation
32-bit and 64-bit parallel simulation kernel
Integrated, GUI-based debugging and analysis
Open interface for integrating external component libraries
The 7 Layers of the OSI Model
TheOpenSystemInterconnection (OSI) model definesa
networking framework to implement protocols in seven
layers. Control is passed from one layer to the next,
starting at the application layer in one station, and
proceeding to the bottom layer, over the channel to the
next station and back up the hierarchy.
The OSI model takes the task of internetworking and
divides that up into what is referred to as avertical
stackthat consists of the following layers.
1. Physical (Layer 1)
This layer conveys the bit stream - electrical impulse, light or
radio signalthrough thenetworkat the electrical and
mechanical level. It provides thehardwaremeans of sending
and receiving data on a carrier, including defining cables,
cards and physical aspects.Fast Ethernet,RS232, andATM
areprotocolswith physical layer components.
Layer 1 Physical examples include Ethernet, FDDI
The 7 Layers of the OSI Model
2. Data Link (Layer 2)
At this layer, data packets areencodedand decoded into bits.
It
furnishestransmission protocolknowledge
and
management and handles errors in the physical layer, flow
control and frame synchronization. The data link layer is
divided into two sub layers: The Media Access Control (MAC)
layer and theLogical Link Control(LLC) layer. The MAC sub
layer controls how a computer on the network gains access to
the data and permission to transmit it. The LLC layer controls
framesynchronization, flow control and error checking.
Layer 2 Data Link examples include PPP, FDDI, ATM, IEEE
802.5/ 802.2, IEEE 802.3/802.2
The 7 Layers of the OSI Model
3. Network (Layer 3)
This
layer
providesswitchingandroutingtechnologies,
creating logical paths, known asvirtual circuits, for
transmitting data fromnodeto node. Routing and forwarding
are functions of this layer, as well asaddressing,
internetworking,
error
handling,congestioncontrol
and
packet sequencing.
4.Transport (Layer 4)
This layer provides transparent transfer of data between end
systems, orhosts, and is responsible for end-to-end error
recovery andflow control. It ensures complete data transfer.
5. Session (Layer 5)
This layer establishes, manages and terminates connections
betweenapplications. The session layer sets up, coordinates,
and terminates conversations, exchanges, and dialogues
between the applications at each end. It deals with session
and connection coordination.
The 7 Layers of the OSI Model
6. Presentation (Layer 6)
This layer provides independence from differences in data
representation
(e.g.,encryption)
by
translating
from
application to network format, and vice versa. The
presentation layer works to transform data into the form that
the application layer can accept. This layer formats and
encrypts data to be sent across anetwork, providing freedom
from compatibility problems. It is sometimes called the syntax
layer.
Layer 6 Presentation examples include encryption, ASCII, GIF,
PICT, JPEG, MPEG, MIDI.
7. Application (Layer 7)
This layer supportsapplicationand end-user processes.
Communication partners are identified, quality of service is
identified, user authentication and privacy are considered,
and any constraints on datasyntaxare identified. Everything
at this layer is application-specific. This layer provides
application services forfile transfers,e-mail, and other
networksoftwareservices.TelnetandFTPare applications
You might also like
- School of Engineering Wireless Communication Lab 1: Wireless LAN (WLAN)No ratings yetSchool of Engineering Wireless Communication Lab 1: Wireless LAN (WLAN)7 pages
- Packet Tracer - Investigate The TCP/IP and OSI Models in ActionNo ratings yetPacket Tracer - Investigate The TCP/IP and OSI Models in Action5 pages
- EX - NO:1 Write A Code Simulating ARP /RARP Protocols: Aim: Algorithm: Server100% (1)EX - NO:1 Write A Code Simulating ARP /RARP Protocols: Aim: Algorithm: Server25 pages
- OPNET Modeler - Introduction LTE SimulationNo ratings yetOPNET Modeler - Introduction LTE Simulation16 pages
- Integrated Services & Differentiated Services100% (1)Integrated Services & Differentiated Services47 pages
- OMNeT++ Installation Guide - Omnetpp3.3-WinxpNo ratings yetOMNeT++ Installation Guide - Omnetpp3.3-Winxp4 pages
- TCP Connection Status: Figure 1. TCP State Transition DiagramNo ratings yetTCP Connection Status: Figure 1. TCP State Transition Diagram5 pages
- Energy-Efficient User Scheduling and Power Allocation For NOMA Wireless NetworksNo ratings yetEnergy-Efficient User Scheduling and Power Allocation For NOMA Wireless Networks36 pages
- 06 HUAWEI CBS5.5 Software Structure-CBP&CBPAdapter ISSUE1.00No ratings yet06 HUAWEI CBS5.5 Software Structure-CBP&CBPAdapter ISSUE1.0071 pages
- Module 3 STP and RSTP: Lab 3-1 Configuring STP Learning ObjectivesNo ratings yetModule 3 STP and RSTP: Lab 3-1 Configuring STP Learning Objectives28 pages
- PJSIP - Open Source SIP, Media, and NAT Traversal LibraryNo ratings yetPJSIP - Open Source SIP, Media, and NAT Traversal Library2 pages
- Make 5G Backhaul Feasible Everywhere PDFNo ratings yetMake 5G Backhaul Feasible Everywhere PDF14 pages
- Chapter 12 Wireless Sensor Networks: From Reference Book: Adhoc Wireless Networks By: B.S. ManojNo ratings yetChapter 12 Wireless Sensor Networks: From Reference Book: Adhoc Wireless Networks By: B.S. Manoj42 pages
- Design and Implementation of Network Monitoring SystemNo ratings yetDesign and Implementation of Network Monitoring System5 pages
- BGP: Border Gateway Protocol: An Interdomain Routing ProtocolNo ratings yetBGP: Border Gateway Protocol: An Interdomain Routing Protocol14 pages
- Network Programming in Java Internet Protocols (IP, UDP, TCP), B01DY9BNOA, Apr. 6, 2016, by Alan MOUHLINo ratings yetNetwork Programming in Java Internet Protocols (IP, UDP, TCP), B01DY9BNOA, Apr. 6, 2016, by Alan MOUHLI19 pages
- Network Design: Planning A Network With Different Users, Hosts, and ServicesNo ratings yetNetwork Design: Planning A Network With Different Users, Hosts, and Services8 pages
- Jarkom 2 (Vlan) Lan Design: Tasmi, S.Si,. M.Kom, MTCNA, MTCRENo ratings yetJarkom 2 (Vlan) Lan Design: Tasmi, S.Si,. M.Kom, MTCNA, MTCRE26 pages
- OS Lecture3 - Inter Process CommunicationNo ratings yetOS Lecture3 - Inter Process Communication43 pages
- Cracking Wifi Passwords Using Aircrack-Ng Using A Target-Specific Custom Wordlist Generated by UsNo ratings yetCracking Wifi Passwords Using Aircrack-Ng Using A Target-Specific Custom Wordlist Generated by Us9 pages
- Python Project Captcha Making Using Python Gui100% (1)Python Project Captcha Making Using Python Gui18 pages
- Connectivity Prediction in Mobile Ad Hoc Networks for Real-Time ControlFrom EverandConnectivity Prediction in Mobile Ad Hoc Networks for Real-Time Control5/5 (1)
- Emerging Technologies in Information and Communications TechnologyFrom EverandEmerging Technologies in Information and Communications TechnologyNo ratings yet
- EX - NO: 7 Study of Network Simulator (NS) and Simulation of Congestion Control Algorithms Using NS AIMNo ratings yetEX - NO: 7 Study of Network Simulator (NS) and Simulation of Congestion Control Algorithms Using NS AIM9 pages
- Top 10 List of Network Simulation Tools - Downloadable Link InsideNo ratings yetTop 10 List of Network Simulation Tools - Downloadable Link Inside20 pages
- Experiment - 1: AIM: Installation of Network Simulator (NS2) On Ubuntu 14.04No ratings yetExperiment - 1: AIM: Installation of Network Simulator (NS2) On Ubuntu 14.0433 pages
- Key Features and Optimum Performance of Network Simulators: A Brief StudyNo ratings yetKey Features and Optimum Performance of Network Simulators: A Brief Study7 pages
- Mobile Ad Hoc Network Simulation Using NS2: ANUSHA REDDY (T150228560)100% (1)Mobile Ad Hoc Network Simulation Using NS2: ANUSHA REDDY (T150228560)30 pages
- Assignment 3: Muhammad Farrukh 180990 Muhammad Mubashir Saleem 181074 Haseeb Tariq 181118No ratings yetAssignment 3: Muhammad Farrukh 180990 Muhammad Mubashir Saleem 181074 Haseeb Tariq 1811183 pages
- Qualitative Comparison of Network Simulation ToolsNo ratings yetQualitative Comparison of Network Simulation Tools62 pages
- LABSHEET-9 Introduction To Network Simulator (OPNET)No ratings yetLABSHEET-9 Introduction To Network Simulator (OPNET)18 pages
- Stop and Wait Protocol: Ex. No.1 (A) Date: AimNo ratings yetStop and Wait Protocol: Ex. No.1 (A) Date: Aim53 pages
- School of Engineering Wireless Communication Lab 1: Wireless LAN (WLAN)School of Engineering Wireless Communication Lab 1: Wireless LAN (WLAN)
- Packet Tracer - Investigate The TCP/IP and OSI Models in ActionPacket Tracer - Investigate The TCP/IP and OSI Models in Action
- EX - NO:1 Write A Code Simulating ARP /RARP Protocols: Aim: Algorithm: ServerEX - NO:1 Write A Code Simulating ARP /RARP Protocols: Aim: Algorithm: Server
- TCP Connection Status: Figure 1. TCP State Transition DiagramTCP Connection Status: Figure 1. TCP State Transition Diagram
- Energy-Efficient User Scheduling and Power Allocation For NOMA Wireless NetworksEnergy-Efficient User Scheduling and Power Allocation For NOMA Wireless Networks
- 06 HUAWEI CBS5.5 Software Structure-CBP&CBPAdapter ISSUE1.0006 HUAWEI CBS5.5 Software Structure-CBP&CBPAdapter ISSUE1.00
- Module 3 STP and RSTP: Lab 3-1 Configuring STP Learning ObjectivesModule 3 STP and RSTP: Lab 3-1 Configuring STP Learning Objectives
- PJSIP - Open Source SIP, Media, and NAT Traversal LibraryPJSIP - Open Source SIP, Media, and NAT Traversal Library
- Chapter 12 Wireless Sensor Networks: From Reference Book: Adhoc Wireless Networks By: B.S. ManojChapter 12 Wireless Sensor Networks: From Reference Book: Adhoc Wireless Networks By: B.S. Manoj
- Design and Implementation of Network Monitoring SystemDesign and Implementation of Network Monitoring System
- BGP: Border Gateway Protocol: An Interdomain Routing ProtocolBGP: Border Gateway Protocol: An Interdomain Routing Protocol
- Network Programming in Java Internet Protocols (IP, UDP, TCP), B01DY9BNOA, Apr. 6, 2016, by Alan MOUHLINetwork Programming in Java Internet Protocols (IP, UDP, TCP), B01DY9BNOA, Apr. 6, 2016, by Alan MOUHLI
- Network Design: Planning A Network With Different Users, Hosts, and ServicesNetwork Design: Planning A Network With Different Users, Hosts, and Services
- Jarkom 2 (Vlan) Lan Design: Tasmi, S.Si,. M.Kom, MTCNA, MTCREJarkom 2 (Vlan) Lan Design: Tasmi, S.Si,. M.Kom, MTCNA, MTCRE
- Cracking Wifi Passwords Using Aircrack-Ng Using A Target-Specific Custom Wordlist Generated by UsCracking Wifi Passwords Using Aircrack-Ng Using A Target-Specific Custom Wordlist Generated by Us
- The IMS: IP Multimedia Concepts and ServicesFrom EverandThe IMS: IP Multimedia Concepts and Services
- Connectivity Prediction in Mobile Ad Hoc Networks for Real-Time ControlFrom EverandConnectivity Prediction in Mobile Ad Hoc Networks for Real-Time Control
- New Telecom Networks: Enterprises and SecurityFrom EverandNew Telecom Networks: Enterprises and Security
- Emerging Technologies in Information and Communications TechnologyFrom EverandEmerging Technologies in Information and Communications Technology
- EX - NO: 7 Study of Network Simulator (NS) and Simulation of Congestion Control Algorithms Using NS AIMEX - NO: 7 Study of Network Simulator (NS) and Simulation of Congestion Control Algorithms Using NS AIM
- Top 10 List of Network Simulation Tools - Downloadable Link InsideTop 10 List of Network Simulation Tools - Downloadable Link Inside
- Experiment - 1: AIM: Installation of Network Simulator (NS2) On Ubuntu 14.04Experiment - 1: AIM: Installation of Network Simulator (NS2) On Ubuntu 14.04
- Key Features and Optimum Performance of Network Simulators: A Brief StudyKey Features and Optimum Performance of Network Simulators: A Brief Study
- Mobile Ad Hoc Network Simulation Using NS2: ANUSHA REDDY (T150228560)Mobile Ad Hoc Network Simulation Using NS2: ANUSHA REDDY (T150228560)
- Assignment 3: Muhammad Farrukh 180990 Muhammad Mubashir Saleem 181074 Haseeb Tariq 181118Assignment 3: Muhammad Farrukh 180990 Muhammad Mubashir Saleem 181074 Haseeb Tariq 181118
- Qualitative Comparison of Network Simulation ToolsQualitative Comparison of Network Simulation Tools
- LABSHEET-9 Introduction To Network Simulator (OPNET)LABSHEET-9 Introduction To Network Simulator (OPNET)