Attack Anatomy
Anatomy of a Spear Phishing Attack
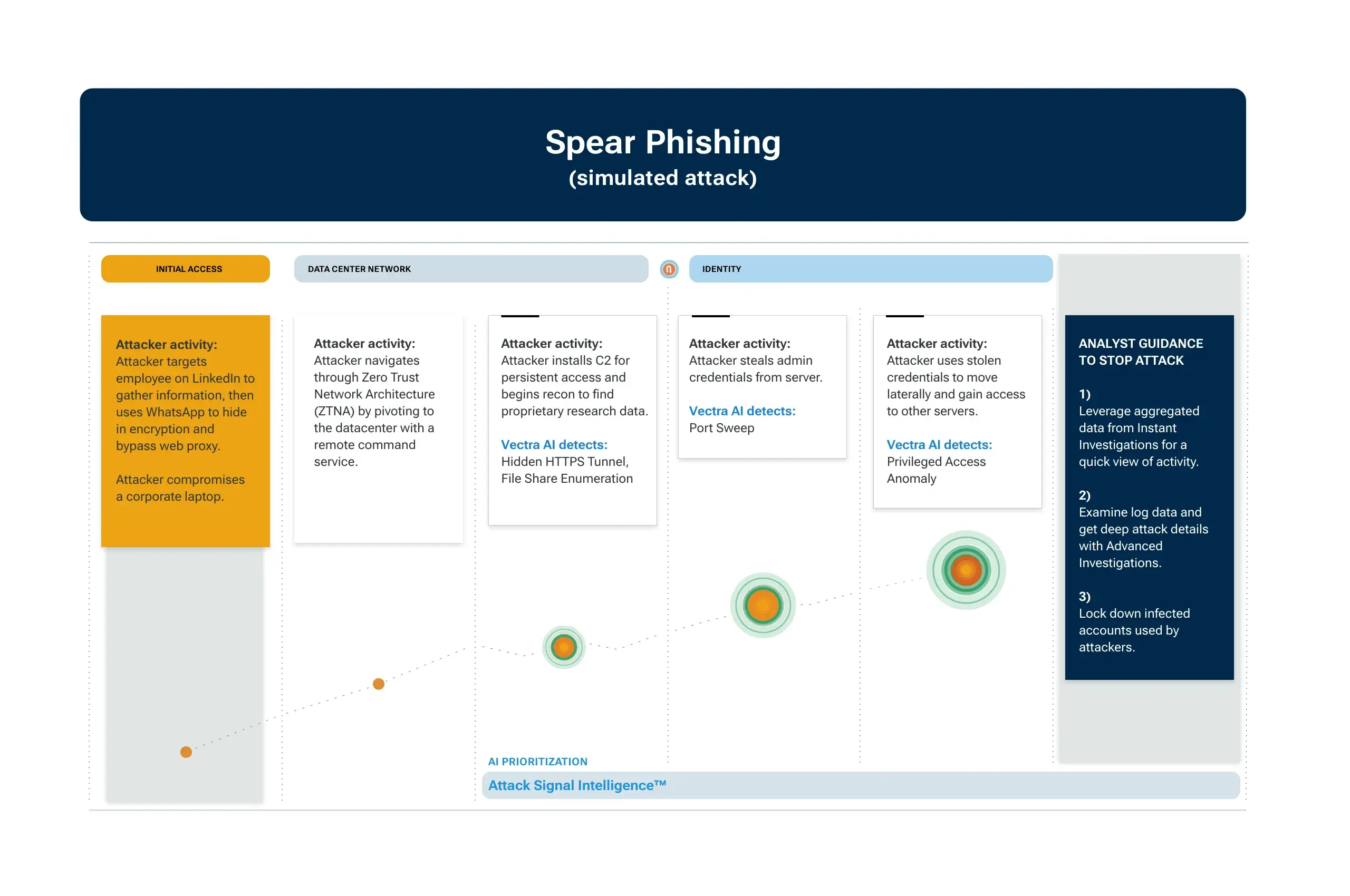
In this simulated Lazarus Group attack, defenders were put on the spot after attackers used spear phishing to compromise a corporate laptop and set up persistent access. With AI-driven Attack Signal Intelligence to automatically correlate detections across each attack surface, defenders knew exactly where to focus efforts.
What is spear phishing?
Spear phishing is a highly targeted — and highly effective — type of phishing attack. Unlike generic phishing campaigns sent to large numbers of people, spear phishing targets specific individuals or organizations. It involves extensive research to craft highly personalized emails, phone calls, or social media messages, which often appear to come from a trusted source such as a colleague, supervisor, or known business partner. The attacker carefully researches their target to help make the message look legitimate and urge the victim to take action. Even highly skilled employees fall for spear phishing emails, making these targeted attacks a top priority for defenders.
Why attackers use spear phishing
Spear phishing is frequently used by ransomware groups and APTs such as Akira, Black Basta, and APT29. Attackers use it to:
- Increase the likelihood of success
- Gain data center access
- Steal sensitive information
- Infect devices with malware
The process of a spear phishing attack
Spear phishing attacks follow a highly structured process:
- Research: Spear phishers gather detailed information about the target, often through social media, public databases, or previous breaches.
- Creating the bait: The attacker then crafts a convincing message that appears to be from a trusted source, complete with personal information, recent events, mutual acquaintances, and other individualized details.
- Delivery: The message is delivered along with a malicious link or attachment, such as malware or a fake website designed to steal login credentials.
- Exploitation: Once the employee takes the bait, the attacker gains access to move laterally within your organization’s network and escalate the attack.
How to counter spear phishing attacks
Prevention tools often fail to stop this type of attack, making them a threat even with secure web gateway, firewalls, and IPS. For this reason, it’s critical to have proper detections in place so you can see and respond to attacks immediately. Vectra AI detects common spear phishing tactics including:
- Hidden TTPS Tunnel
- File Share Enumeration
- Suspicious and Outbound Port Sweep
- Entra ID Privilege Operation Anomaly
- M365 Internal Spear Phishing
For example, in one simulated attack that started with an attack targeting an employee on LinkedIn, the attacker:
- Encrypted WhatsApp to bypass web
- Compromised the employee’s corporate laptop
- Moved to the data center via remote command
In this instance, Vectra AI quickly revealed where hidden tunnels are set up and which identities were impacted — allowing defenders to respond instantly.
See how Vectra AI exposed an active spear phishing attack
We simulated a Lazarus Group attack to find out exactly what happens when a state-sponsored cybercrime group targets an employee on LinkedIn, pivots past zero trust network access (ZTNA), and swipes admin credentials. V how defendpped the attack from progressing.