Abstract
Publicly Verifiable Secret Sharing (PVSS) allows a dealer to publish encrypted shares of a secret so that parties holding the corresponding decryption keys may later reconstruct it. Both dealing and reconstruction are non-interactive and any verifier can check their validity. PVSS finds applications in randomness beacons, distributed key generation (DKG) and in YOSO MPC (Gentry et al. CRYPTO’21), when endowed with suitable publicly verifiable re-sharing as in YOLO YOSO (Cascudo et al. ASIACRYPT’22).
We introduce a PVSS scheme over class groups that achieves similar efficiency to state-of-the art schemes that only allow for reconstructing a function of the secret, while our scheme allows the reconstruction of the original secret. Our construction generalizes the DDH-based scheme of YOLO YOSO to operate over class groups, which poses technical challenges in adapting the necessary NIZKs in face of the unknown group order and the fact that efficient NIZKs of knowledge are not as simple to construct in this setting.
Building on our PVSS scheme’s ability to recover the original secret, we propose two DKG protocols for discrete logarithm key pairs: a biasable 1-round protocol, which improves on the concrete communication/computational complexities of previous works; and a 2-round unbiasable protocol, which improves on the round complexity of previous works. We also add publicly verifiable resharing towards anonymous committees to our PVSS, so that it can be used to efficiently transfer state among committees in the YOSO setting. Together with a recent construction of MPC in the YOSO model based on class groups (Braun et al. CRYPTO’23), this results in the most efficient full realization (i.e. without assuming receiver anonymous channels) of YOSO MPC based on the CDN framework with transparent setup.
Ignacio Cascudo was partially supported by the Spanish Government under the project SecuRing (ref. PID2019-110873RJ-I00) and the PRODIGY Project (TED2021-132464B-I00), both funded by MCIN/AEI/10.13039/501100011033/. PRODIGY is also funded by the European Union NextGenerationEU/PRTR. He was also partially supported by the European Union under GA 101096435 (CONFIDENTIAL-6G). Views and opinions expressed are however those of the author(s) only and do not necessarily reflect those of the European Union or the European Commission. Neither the European Union nor the European Commission can be held responsible for them.
Bernardo David was supported by the Independent Research Fund Denmark (IRFD) grant number 0165-00079B.
You have full access to this open access chapter, Download conference paper PDF
1 Introduction
Publicly Verifiable Secret Sharing [38] (PVSS) allows for a dealer to publish encrypted secret shares in such a way that any verifier can check their validity. Moreover, after the parties holding the corresponding decryption keys reconstruct the secret, any verifier can also check the secret’s validity with respect to the encrypted shares (typically by checking the consistency between the encrypted and plaintext shares used for reconstruction). Many PVSS schemes are known [4, 8, 9, 24, 27, 31, 36, 37], but the state-of-the-art constructions [11] based on number theoretic assumptions only allow for reconstructing \(g^s\), where \(g \in \mathbb {G}\) is the generator of a cyclic group \(\mathbb {G}\) and \(s \in \mathbb {Z}_p\) is the secret. This limitation can be circumvented [12] by sharing a random secret \(s'\) with the PVSS and publishing a one-time pad of the actual secret s with a key derived (e.g. via a random oracle) from the reconstructable secret \(g^{s'}\). However, this solution limits the efficiency of a number of PVSS applications. In particular, the secret sharing scheme derived in this way is no longer linear.
Distributed Key Generation (DKG). Besides randomness beacons (e.g. [8, 9]), one of the main applications of PVSS schemes is in constructing Distributed Key Generation (DKG) protocols. Such protocols [23, 25, 29, 30, 33, 34] allow for parties to obtain Shamir shares \(\textsf{sk}_i\) of a secret key \(\textsf{sk}\in \mathbb {Z}_p\) and the corresponding public key \(g^\textsf{sk}\) while revealing nothing else. The recent unbiasable DKG protocol of [12] builds on the PVSS scheme of [9] to achieve higher efficiency than previous protocols in terms of round/computational complexities (and in many cases [23, 25, 29] also better communication complexity). However, even though it requires only 2 rounds in case there is no cheating, it still falls short of round optimality [33] in case a malicious party triggers a dispute phase that requires 2 extra rounds. This issue stems from the fact that, in order to allow the parties to retrieve \(s_i\), the DKG of [12] must publish a separate encryption of shares \(s_i\) apart from the original PVSS [9] encrypted shares, since those can only be reconstructed to \(g^{s_i}\). In case the PVSS encrypted shares are not consistent with the extra encryption, the dispute phase must be triggered to avoid bias.
The YOSO Model. The recent introduction of the You Only Speak Once (YOSO) model for multiparty computation (MPC) protocols [26] and related models [1, 18, 20] has sparked a renewed interest in PVSS schemes with added properties. In the YOSO model, each round of the protocol is executed by a fresh randomly selected committee of parties who remain anonymous until they send their first message, after which they no longer participate in the execution. This is interesting as it improves scalability because small committees are sufficient to execute each round, as well as resulting in protocols resistant to adaptive corruptions, given that the adversary does not know who to corrupt. However, due to the ephemeral nature of these committees, each of them must transfer their secret state to the next, which is hard given their anonymity. In the YOSO model, it is assumed that all parties have access to ideal receiver anonymous communication channels (RACC), which allow for sending messages to an anonymous party to be randomnly chosen at a later point. Hence, protocols in the YOSO model assume RACCs as setup but aim at minimizing their use. In particular, it was observed in [26] that the Cramer-Damgård-Nielsen (CDN) [19] approach to MPC via threshold encryption is particularly well suited to this setting, as secret key shares are the only secret state maintained by parties. Only very recently, Braun et al. proposed a YOSO MPC protocol [6] following the CDN approach without assuming pre-distribution of secret key shares as trusted setup. This protocol assumes access to ideal RACCs in order to realize a threshold encryption scheme over class groups with a matching DKG and a protocol for re-sharing the secret key at every round.
PVSS in the YOSO Model. A number of tools [3, 7, 28] have been proposed to implement RACCs but only recently an efficient publicly verifiable (re-)sharing scheme compatible with such techniques was proposed in YOLO YOSO [11]. The YOLO YOSO scheme allows for parties to share secrets by publishing publicly verifiable encrypted shares and then re-share those secrets into a fresh set of shares for the next anonymous committee without assuming access to an ideal RACC, thus providing a way to realize the communication infrastructure of the YOSO model using only a random oracle and a Public Key Infrastructure (PKI) as setup (i.e. a transparent setup). However, besides suffering from the issue that only \(g^s\) can be reconstructed from encrypted shares of s, YOLO YOSO is based on DDH and not directly compatible with class groups. Hence, if YOLO YOSO was used to realize the RACC setup required in the protocol of [6] one would need to rely on freakishly large groups where DDH is hard and be prepared to rely both on DDH and on hardness assumptions over class groups.
1.1 Our Contributions
We introduce an efficient PVSS scheme based on class groups that allows for reconstructing the original secret, enabling applications to DKG and YOSO MPC. Our main results are summarized as follows:
- PVSS over class groups::
-
We construct a PVSS scheme over class groups [16] that allows for reconstructing the original secret achieving similar efficiencyFootnote 1 as previous works [9, 11] that only allowed for recovering functions of the secret. Moreover, our scheme achieves a stronger security guarantee. In addition to this, privacy is based solely on the DDH-f assumption [17], known to be implied by both DDH and hard subgroup membership on class groups.
- Efficient NIZKs of encrypted share validity::
-
Our design differs from the schemes of [9, 11], overcoming the hurdles of avoiding extracting witnesses and adapting the SCRAPE [8] share validity test to the class group setting.
- DKG protocols for Discrete Logarithm key pairs::
-
We show how our PVSS can be used to construct a 1-round biasable DKG protocol that outperforms the state-of-the-art [29]. We also construct a 2-round unbiasable protocol which is round-optimal [33], improving on the state-of-the-art [12].
- Full realization of Efficient YOSO MPC with transparent setup::
-
Our PVSS can be endowed with publicly verifiable re-sharing towards anonymous committees, lifted from YOLO YOSO [11] via our new NIZKs of share validity. Using this efficient realization of the RACC setup needed by the communication-efficient protocol of [6] yields the most efficient full realization (i.e. without assuming ideal RACCs) of YOSO MPC with transparent setup based solely on class groups.
When constructing our PVSS scheme, we face the main technical hurdle of constructing an efficient NIZK of share validity over class groups. Similarly to [9, 11], we start from Shamir’s secret sharing, encrypt the shares (using encryption over class groups) and want to apply the SCRAPE [8] test to verify share validity. However, we cannot apply the SCRAPE test directly, since the security analysis of this technique crucially relies on the group order, which is unknown for class groups. Moreover, current techniques [6, 13, 14] for zero knowledge proof systems over class groups do not allow for efficient proofs of knowledge for complex relations such as that of share validity via the SCRAPE test. In order to overcome both of these difficulties we make the following main technical contributions: 1. a new analysis of the SCRAPE test for encrypted shares over groups of unknown order (i.e. class groups); 2. a new efficient NIZK proof of share validity (but not of knowledge) based on the SCRAPE test for Shamir shares encrypted over class groups; 3. a new proof strategy for our PVSS scheme based on a NIZK that does not allow for extracting adversarial shares.
We construct our 2-round unbiasable DKG protocol as a direct application of our new PVSS protocol. First, all parties publish encrypted shares of random secrets along with proofs of share validity, which are checked so that invalid share vectors and their creators are ignored. Next, honest parties decrypt the shares they received and combine them to generate their share of the secret key and a partial public key, which is published along with a correctness proof so that all parties may compute the final public key. While a similar approach was taken in Mt. Random [12], that DKG requires two extra rounds in case of cheating. The ALBATROSS [9] PVSS used in [12] only allows parties to share \(g^{s_i}\), not the original share \(s_i\), requiring an extra ciphertext containing \(s_i\) to be published. When the share in the separate ciphertext differs from the PVSS encrypted share, a dispute phase consisting of 2 extra rounds is executed. We eliminate the dispute phase and achieve a round-optimal [33] protocol by relying on the fact that we can recover the original \(s_i\) in our new PVSS scheme’s encrypted shares.
Our 1-round DKG protocol publishes the information needed for computing public key shares and the final public key along with the encrypted shared of our PVSS scheme. Doing so avoids the need for the second round where this information is revealed but allows for an adversary to bias the public key by observing the shares published by the honest parties before publishing its own shares. While this bias is unavoidable in 1-round DKG protocols [33], it does not pose a problem when DKG is used in many applications (see e.g. [30]). Our approach cannot be implemented by a simple modification of our 2-round protocol, since it is necessary to prove consistency between encrypted shares used to derive the secret key and public shares used to derive the public key. In order to do so, we design an efficient NIZK proving this relation for our PVSS scheme. Our 1-round protocol requires computing less group operations and communicating less group elements than the work of Kate et al. [32], which in turn is shown to be more efficient than the Groth [29] DKG. Hence, our 1-round DKG improves on the concrete efficiency of [29, 32].
Another application of our new PVSS scheme is in efficiently realizing publicly verifiable (re-)sharing towards anonymous committees selected at random, which is crucial in the YOSO model. We adapt our techniques for proving encrypted share validity over class groups to obtain an efficient NIZK of encrypted re-sharing data validity. We remark that efficiently and non-interactively proving re-sharing validity is the main hurdle when constructing secret sharing schemes for the YOSO model, where all parties must do re-sharing at every round. This extended PVSS with re-sharing can be combined with the shuffle-based encryption to the future scheme from YOLO YOSO [11], which only requires a publicly verifiable mixnet, known to be realizable with proofs of shuffle correctness [2] for linearly homomorphic encryption schemes (e.g. based on class groups [16]). The resulting publicly verifiable secret (re-)sharing scheme towards anonymous committees implements the communication infrastructure needed for the efficient YOSO MPC protocol proposed in [6], which follows the CDN [19] approach to reduce the size of secret state transferred among anonymous committees to a minimum and is based on class groups to achieve transparent setup. However, our solution does not require assuming ideal receiver anonymous communication channels (RACC) as in [6], while improving on the efficiency of the proof of resharing, which in [6] requires executing two instances of an inefficient PVSS-like protocol. Hence, combining our results with the protocol of [6] yields the most efficient full realization of YOSO MPC with transparent setup.
1.2 Related Works
Cryptography Over Class Groups: The Castagnos-Laguillaumie (CL) framework for encryption based on class groups was introduced in [16] and later refined in [6, 13,14,15, 17, 39]. This framework creates a finite group of unknown order where the discrete logarithm is assumed hard to compute, together with a cyclic subgroup where the discrete logarithm is actually easy. This allows for constructing additively homomorphic ElGamal-style encryption, where it is possible to encode plaintexts into the group where the discrete logarithm is easy, compute linear operations on multiple ciphertexts and obtain the result m instead of \(g^m\).
Publicly Verifiable Secret Sharing: Many PVSS schemes based on different techniques for proving share validity are known [4, 24, 31, 36,37,38]. SCRAPE [8] was the first scheme to achieve O(n) complexity for share validity verification, allowing for executions with tens of thousands of parties. ALBATROSS [9] built on the SCRAPE techniques to construct a compact NIZK for share validity and also achieved sharing of large batches of secrets. This NIZK was generalized and further improved in YOLO YOSO [11], where support for re-sharing and anonymous committees was also efficiently achieved for the first time. Recently, Mt. Random [12] extended ALBATROSS, showing how to slowly release sub-batches of secrets. While these previous works build on number theoretical assumptions, an efficient PVSS scheme from lattice-based assumptions is constructed in [27].
Distributed Key Generation: Most DKG protocols use secret sharing in a similar way as ours, the key difference being how parties prove the correctness of their shares and public information. The classic DKG by Pedersen [34], employs Feldman’s VSS, resulting in a protocol with 1 round in case of no disputes, and 2 extra rounds if there are disputes. Fouque and Stern [23] proposed a one-round DKG based on the Paillier cryptosystem that still allows the adversary to bias public keys. Groth [29] proposed a 1-round protocol based on pairings. Recently, Katz [33] showed that all 1-round protocols are biasable and proposed round-optimal protocols. Gennaro et al. [25] were the first to observe that Pedersen’s DKG is biased and made it unbiasable by introducing a new round of interaction and a new round of dispute resolution. Gurkan et al. [30] introduces a pairing-based DKG based on the notion of aggregation via gossip. Cascudo et al. [12] introduce the Mt. Random DKG, which follows a similar approach as our constructions but is based on the ALBATROSS [9] PVSS, requiring 2 extra conflict resolution rounds to avoid bias. Recently, Kate et al. introduced a DKG based on class groups improving on the performance of Groth [29].
YOSO MPC: The original YOSO MPC model and the first constructions were introduced in [26], while similar models with less stringent restrictions on interaction and matching protocols were introduced in Fluid MPC [18] and in SCALES [1]. A similar model without anonymity but stricter interaction restrictions and matching protocols were introduced in [20]. Further protocols for the Fluid MPC and YOSO MPC models were proposed in [6, 35], respectively. Suitable receiver anonymous communication channels for original YOSO model (where parties remain anonymous until they act) were first constructed in [3, 28], respectively suffering from a low corruption threshold (less than 1/4 of parties) and from high complexity. Towards solving this issue, the notion of Encryption to the Future (EtF) was introduced in [7] and efficient DDH-based EtF schemes with matching PVSS (and re-sharing) were introduced in [11].
Independent Work: Several 2-round (i.e. round optimal) unbiasable DKG protocols based on generic secret sharing, encryption and NIZK schemes are proposed in [33]. However, the core technical issue of obtaining efficient concrete instantiations is not addressed. In [32], the authors propose 1-round (biasable) and 2-round (unbisable) DKG protocols based on “leaky” non-interactive VSS (NI-VSS) protocol. This NI-VSS achieves a weaker security notion than our PVSS as it leaks information about the secret, which is shown to be sufficient for their DKG constructions but is clearly insufficient for general use (e.g. our YOSO MPC application). Moreover, the NIZK of share validity of [32] is based on a NIZK of exponent knowledge and requires more communication/computation than our NIZKs, which circumvent the need for extracting witnesses.
2 Preliminaries
For \(m,n\in \mathbb {Z}\), we denote \([m,n]:=\{m,m+1,\dots ,n\}\). Moreover, we write \([n]=[1,n]=\{1,\dots ,n\}\). For a finite set S, we denote by \(x\leftarrow _{\$}S\) the selection of a uniformly random element in S. If we are sampling from a non-necessarily uniform distribution \(\mathcal {D}\), then we write \(x\leftarrow \mathcal {D}\). In this paper q will always denote a prime number and then \(\mathbb {Z}_q:=\mathbb {Z}/q\mathbb {Z}\) is the field of integers modulo q. \(\mathbb {Z}_q[X]_{\le t}\) denotes the set of polynomials in \(\mathbb {Z}_q[X]\) of degree at most t. Let \(S\subseteq \mathbb {N}\) a finite set and \(A=\{\alpha _i: i\in S\}\) be a set of pairwise distinct points contained in a field \(\mathbb {F}\). For \(i\in S\), we define the Lagrange interpolation polynomial \(\textrm{Lag}_{i,S,A}(X):=\prod _{j\in S\setminus \{i\}} \frac{X-\alpha _j}{\alpha _i-\alpha _j}\). Recall that \(L(X)=\sum _{i\in S} y_i\cdot \textrm{Lag}_{i,S,A}(X)\) is the unique polynomial in \(\mathbb {F}[X]\) of degree at most \(|S|-1\) with \(L(\alpha _i)=y_i\) for all \(i\in S\).
Relations are written as \(\mathcal {R}=\{(x;w): R(x,w)=1\}\) where x is the statement, w is the witness and R is some predicate. We write \(\texttt {NIZK}(\mathcal {R})\) (respectively \(\texttt {NIZKPoK}(\mathcal {R})\)) to denote a generic non-interactive zero knowledge proof (respectively proof of knowledge) for relation \(\mathcal {R}\), without instantiating it at that point.
2.1 Publicly Verifiable Secret Sharing(PVSS)
We first present our definitions of a publicly verifiable secret sharing scheme and security properties, where we mainly adopt the definitions from [11]. After that, we recall the SCRAPE test [8] which has been of great utility in several works on publicly verifiable secret sharing and applications [8, 9, 11, 30].
Model. A PVSS scheme consists of the following algorithms.
-
Setup
-
\(\textsf{Setup}(1^\lambda ,\textsf{ip})\rightarrow \textsf{pp}\) outputs public parameters \(\textsf{pp}\). The initial parameters \(\textsf{ip}\) contain information about number of parties, privacy and reconstruction thresholds and spaces of secrets and shares. The public parameters include a description of spaces of private and public keys \(\textsf{SK}\) and \(\textsf{PK}\) and the relation \(\mathcal {R}_{\textsf{Key}}\subseteq \textsf{PK}\times \textsf{SK}\) describing valid key pairs.
-
\(\textsf{KeyGen}(\textsf{pp},id)\rightarrow (\textsf{sk},\textsf{pk},\textsf{Pf}_{\textsf{pk}})\), where \((\textsf{pk};\textsf{sk})\in \mathcal {R}_{\textsf{Key}}\) and \(\textsf{Pf}_{\textsf{pk}}\) is a proof meant to assert that \(\textsf{pk}\) is a valid public key.
-
\(\textsf{VerifyKey}(\textsf{pp}, id, \textsf{pk}, \textsf{Pf}_{\textsf{pk}})\rightarrow 0/1\) (as a verdict on whether \(\textsf{pk}\) is valid).
-
-
Distribution
-
\(\textsf{Dist}(\textsf{pp},(\textsf{pk}_i)_{i\in [n]}, \textbf{s})\rightarrow ((C_i)_{i\in [n]},\textsf{Pf}_{\textsf{Sh}})\) where \(\textbf{s}\in \mathcal {S}\) is a secret, outputs “encrypted shares” \(C_i\) and a proof \(\textsf{Pf}_{\textsf{Sh}}\) of sharing correctness.
-
-
Distribution Verification
-
\(\textsf{VerifySharing}(\textsf{pp}, (\textsf{pk}_i, C_i)_{i \in [n]},\textsf{Pf}_{\textsf{Sh}})\rightarrow 0/1\) (as a verdict on whether the sharing is valid).
-
-
Reconstruction
-
\(\textsf{DecShare}(\textsf{pp}, \textsf{pk}_i, \textsf{sk}_i, C_i)\rightarrow (A_i,\textsf{Pf}_{\textsf{Dec}_{i}})\), outputs a decrypted share \(A_i\) and a proof \(\textsf{Pf}_{\textsf{Dec}_{i}}\) of correct decryption.
-
\(\textsf{Rec}(\textsf{pp}, \{A_i: i\in \mathcal {T}\})\) for some \(\mathcal {T}\subseteq [n]\) outputs an element of the secret space \(\textbf{s}'\in \mathcal {S}\) or an error symbol \(\bot \).
-
-
Reconstruction Verification
-
\(\textsf{VerifyDec}(\textsf{pp}, \textsf{pk}_i, C_i, A_i, \textsf{Pf}_{\textsf{Dec}_{i}})\rightarrow 0/1\) (as a verdict on whether \(A_i\) is a valid decryption of \(C_i\)).
-
Security Properties. The formal security definitions for a PVSS scheme are presented in the full version [10], but we sum them up here. Correctness with r-reconstruction means that, if every party acts honestly, any subset of r parties can jointly reconstruct the secret correctly. Verifiability means that parties cannot cheat in key generation, share distribution (including encrypting inconsistent shares) and share decryption without being caught with high probability. Privacy is captured via the notion of t-indistinguishability, which means that no set of t corrupted parties can distinguish between sharings of two secrets, given their secret keys and public information. While some previous PVSS such as [8, 9] can only achieve IND1-privacy, where the two secrets are chosen randomly by a challenger, in this paper we use the stronger IND2 property that ensures indistinguishability holds even if the adversary has chosen the two secrets.
The SCRAPE Test. We recall the SCRAPE test from [8]. Given fixed evaluation points \(\alpha _1,\dots ,\alpha _n\) in a finite field \(\mathbb {F}\), the SCRAPE test allows to check whether a vector \(\textbf{y}=(y_1,...,y_n)\in \mathbb {F}^n\) is of the form \((p(\alpha _1),\dots ,p(\alpha _n))\) for some \(p(X)\in \mathbb {F}[X]_{\le d}\), by computing the inner product of \(\textbf{y}\) with a vector sampled uniformly at random from a certain set.Footnote 2 This is summed up in Theorem 1.
Theorem 1 (SCRAPE test, [8])
[SCRAPE test, [8]] Let \(\mathbb {F}\) be a finite field, \(\alpha _1,\dots ,\alpha _n\) pairwise distinct elements of \(\mathbb {F}\), \(y_1,\dots ,y_n\) arbitrary elements of \(\mathbb {F}\), \(0\le d\le n-2\) an integer. Let \(v_i=\prod _{j\in [n]\setminus \{i\}}(\alpha _i-\alpha _j)^{-1}\). Let \(m^*(X):=m_0+m_1X+\dots +m_{n-d-2}X^{n-d-2}\leftarrow _{\$}\mathbb {F}[X]_{\le n-d-2}\) and
-
1.
If there exists a polynomial \(p\in \mathbb {F}[X]\) of degree \(\le d\) such that \(y_i=p(\alpha _i)\) for all \(i\in [n]\), then \(\Pr [T=0]=1\).
-
2.
Otherwise, \(\Pr [T=0]= 1/|\mathbb {F}|\).
where the probability is over the uniform choice of \(m^*(X)\).
For completion, we provide a proof of this theorem in the full version [10].
2.2 Background on Class Groups
The CL Framework [16]. We first provide some background on the CL framework for encryption based on class groups. First, there is a probabilistic algorithm \(\textsf{CLGen}\) which is given security parameter \(\lambda \), and some prime \(q>2^{\lambda }\), and outputs \(\textsf{pp}_{\textsf{CL}}=(q,\bar{s},\hat{G},F,f,g_q,\rho )\leftarrow \textsf{CLGen}(1^{\lambda },q;\rho )\). Here \(\rho \in \{0,1\}^{\lambda }\) is the randomness used by \(\textsf{CLGen}\) and it is included in the output to signify that it can be publicly known. We will omit it from the argument of \(\textsf{CLGen}\) when it is not important. The (non-necessarily cyclic) group \(\hat{G}\) has odd cardinality \(q\cdot \hat{s}\) where \(\gcd (q,\hat{s})=1\), and where \(\hat{s}\) is unknown but we know an upper bound \(\bar{s}\), i.e. \(\hat{s}\le \bar{s}\). For technical reasons, we also assume without loss of generality \(\gcd (q,\bar{s})=1\).
Having \(F=\langle f\rangle \) denote the subgroup of cardinality q, \(\hat{G}\) is a direct product \(\hat{G}=\hat{G}^q\times F\), where \(\hat{G}^q\) is the group of containing the q-th powers of elements in \(\hat{G}\), and is of order \(\hat{s}\). \(\hat{G}\) is not necessarily cyclic, but there is a cyclic subgroup \(G\subseteq \hat{G}\) of order \(q\cdot s\) (again s is unknown) that factors as \(G=G^q\times F\) where \(G^q=\langle g_q\rangle \) again contains the q-th powers of elements in G. Note then that \(G=\langle g\rangle \) with \(g=f\cdot g_q\). Given some element in \(\hat{G}\) it is not known how to determine if it is in G efficiently.
A key feature of this framework is that for subgroup \(F\le G\) there is an efficient deterministic discrete logarithm algorithm \(\textsf{CLSolve}\) that given \(f'\in F\) computes the unique \(x\leftarrow \textsf{CLSolve}(\textsf{pp}_{CL}, f')\), with \(x\in [0,q-1]\) such that \(f^x=f'\).
We will need distributions \(\mathcal {D}, \mathcal {D}_q\), over the integers such that \(\{g^x: x\leftarrow \mathcal {D}\}\) and \(\{g_q^x: x\leftarrow \mathcal {D}_q\}\) are statistically close to the uniform distributions in G and \(G^q\), respectively. \(\mathcal {D}, \mathcal {D}_q\) can be instantiated by either uniform or discrete Gaussian distributions [15, 16, 39]: in particular, choosing \(\mathcal {D}\) (resp. \(\mathcal {D}_q\)) to be the uniform distribution in \([q\bar{s}2^{\kappa -2}]\) (resp. \([\bar{s}2^{\kappa -2}]\)) leads to distributions whose statistical distances to the uniform distributions in the respective groups are at most \(2^{-\kappa }\). Note also that the distribution \(\{g_q^{x'}\cdot f^a: x'\leftarrow \mathcal {D}_q, a\leftarrow _{\$}\mathbb {Z}_q \}\) is almost uniform in G, as a consequence of the factorization \(G=G^q\times F\).
Based on this framework, Castagnos and Laguillaumie construct a linearly homomorphic encryption scheme for messages in \(\mathbb {Z}_q\) in [16]. Later, variations of this encryption scheme were presented in [17]. In particular, the share distribution in our PVSS is closely related to one of the schemes presented in [17]: concretely the scheme where \(\textsf{sk}\leftarrow \mathcal {D}_q\), \(\textsf{pk}=g_q^\textsf{sk}\) and the encryption of \(m\in \mathbb {Z}_q\) under \(\textsf{pk}\) and randomness \(r\leftarrow \mathcal {D}_q\) is the pair \((c_1,c_2)=(g_q^r,\ \textsf{pk}^r f^m)\in G^q\times G\). The message can then be decrypted as \(m=\textsf{CLSolve}(c_2\cdot c_1^{-\textsf{sk}})\). The scheme was proved IND-CPA secure under the hard subset membership (\(\texttt {HSM}\)) assumption, described below. We describe first the assumptions we will need directly for our proofs.
First there is the \(\texttt {DDH}\text{- }\!\texttt {f}\) assumption from [17]
Definition 1
(\(\texttt {DDH}\text{- }\!\texttt {f}\) assumption, [17]). For a PPT \(\mathcal {A}\), let \(\textsf{Adv}_{\mathcal {A}}^{\texttt {DDH}\text{- }\!\texttt {f}}(\lambda )\) be
\(\texttt {DDH}\text{- }\!\texttt {f}\) is hard for \(\textsf{CLGen}\) if for all PPT \(\mathcal {A}\), \(Adv_{\mathcal {A}}^{\texttt {DDH}\text{- }\!\texttt {f}}(\lambda )\) is negligible in \(\lambda \).
Second, the more recent rough order assumption from [6].
Definition 2
(Rough Order assumption, [6]). For a natural number \(C\in \mathbb {N}\) and security parameter \(\lambda \), consider \(\mathcal {D}_C^{\texttt {rough}}\) the uniform distribution in the set \(\{\rho \in \{0,1\}^{\lambda }: \textsf{pp}_{CL}\leftarrow \textsf{CLGen}(1^\lambda ,q;\rho ) \wedge \forall \text { prime } p<C,\ p\not \mid \textrm{ord}(\hat{G}) \}\). Let
\(\texttt {RO}_C\) is hard for \(\textsf{CLGen}\) if for all PPT \(\mathcal {A}\), the \(\textsf{Adv}_{\mathcal {A}}^{\texttt {RO}_C}(\lambda )\) is negligible in \(\lambda \).
We refer to [6] for the discussion of why this assumption is plausible. Moreover, we remark, as was also done in [6], that the assumption involves an inefficient challenger (as we do not know how to sample from \(\mathcal {D}_C^{\texttt {rough}}\) efficiently). However, also as [6] does, we will only use the assumption inside a security proof, namely that of Theorem 7,Footnote 3 to argue that if an adversary successfully attacks a protocol, it would be able to determine that that given class group has a low order element, contradicting the assumption.
Other Hardness Assumptions on Class Groups. The standard Decisional Diffie-Hellman (DDH) assumption on G states that distinguishing tuples \((g^x,g^y,g^{xy})\) from tuples \((g^x,g^y,g^z)\) where x, y, z are sampled independently from \(\mathcal {D}\) is hard. More precisely:
Definition 3
(\(\texttt {DDH}\)-assumption on G). For a PPT \(\mathcal {A}\), let \(\textsf{Adv}_{\mathcal {A}}^{\texttt {DDH}}(\lambda )\) be
We say that the \(\texttt {DDH}\) problem is hard for \(\textsf{CLGen}\) if for all PPT \(\mathcal {A}\), \(Adv_{\mathcal {A}}^{\texttt {DDH}}(\lambda )\) is negligible in \(\lambda \).
The \(\texttt {HSM}\) assumption states that it is hard to distinguish elements sampled from G from elements sampled from \(G^q\) (using \(\mathcal {D}\) and \(\mathcal {D}_q\) respectively).
Definition 4
(Hard Subgroup Membership (\(\texttt {HSM}\)) assumption, [17]). For a PPT \(\mathcal {A}\), let \(\textsf{Adv}_{\mathcal {A}}^{\texttt {HSM}}(\lambda )\) be
We say that the \(\texttt {HSM}\) problem is hard for \(\textsf{CLGen}\) if for all PPT \(\mathcal {A}\), \(Adv_{\mathcal {A}}^{\texttt {HSM}}(\lambda )\) is negligible in \(\lambda \).
2.3 Zero Knowledge Proofs for Class Groups
In this section, we recall some proofs for statements involving discrete logarithms in class groups from recent works. In this paper we will need both proofs of knowledge of discrete logarithm and proofs of discrete logarithm equality. However, in the second case we will not need the proofs to be proofs of knowledge.
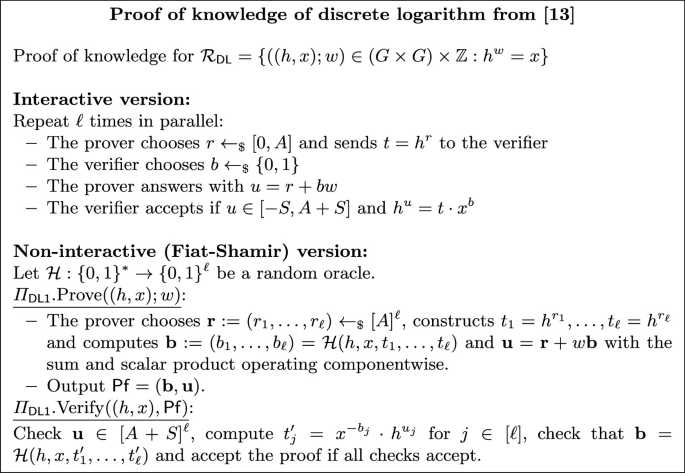
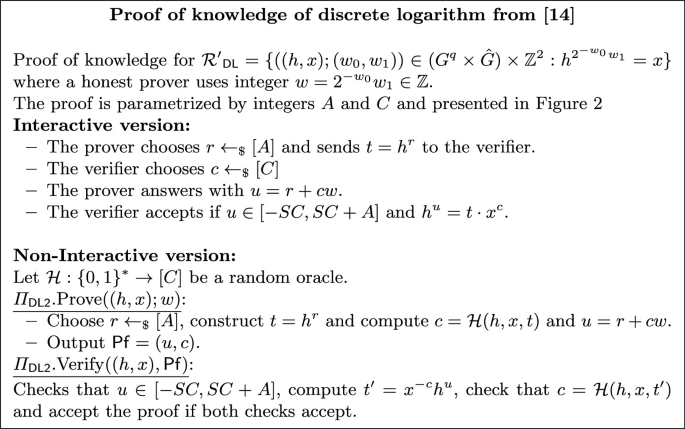
Proofs of Knowledge of Discrete Logarithm. We consider two proofs of knowledge of discrete logarithm, introduced respectively in [13, 14].Footnote 4. Let \(\mathcal {R}_{\textsf{DL}}=\{((h,x);w)\in (G\times G)\times \mathbb {Z}:h^w=x\}\). For these and all the proofs below to be statistically honest-verifier zero knowledge, we will require the witness w to be in an interval \([-S,S]\) for some public bound S (the proofs require to set parameters which depend on S). We remark that the soundness does not guarantee that the witness is in that interval. There is a tradeoff between both proofs in terms of complexity and security assumptions: the first proof is less efficient but does not require any assumption; the second one is more efficient but is based on the hardness assumptions (i.e. it is an argument of knowledge) \(\texttt {LO}_C\) and \(\texttt {SR}\); perhaps more importantly, it requires h to be uniformly random, and in particular not decided by the adversary. We give a brief description of these proof systems and refer the readers to [13, 14] for more details. The proof (Fig. 1) is parameterized by natural numbers A and \(\ell \). We will refer to its non-interactive version via Fiat-Shamir with the name \(\varPi _{\textsf{DL1}}\).
Proof of knowledge of discrete logarithm from [13]
Theorem 2
(Adapted from [13]). The interactive proof in Fig. 1 is a Proof of Knowledge for \(\mathcal {R}_{\textsf{DL}}\) with knowledge soundness \(2^{-\ell }\), and it is statistically zero-knowledge as long as \(w\in [-S,S]\), \(\ell \) is polynomial and \(\ell S/A\) is negligible. By the Fiat-Shamir heuristic, the non-interactive version has the same properties in the random oracle model.
Theorem 3
(Adapted from [14]). Under the \(\texttt {LO}_C\) and \(\texttt {SR}\) assumption, and assuming h is uniformly random in a large enough subset in \(G^q\), the protocol in Fig. 2 is a computationally sound proof of knowledge for \(\mathcal {R'}_{\textsf{DL}}\) with knowledge soundness error 4/C, complete if \(w\in [-S,S]\), and statistically special honest-verifier zero knowledge as long as \(w\in [-S,S]\) and SC/A is negligible. By the Fiat-Shamir heuristic, the non-interactive version has the same properties in the random oracle model.
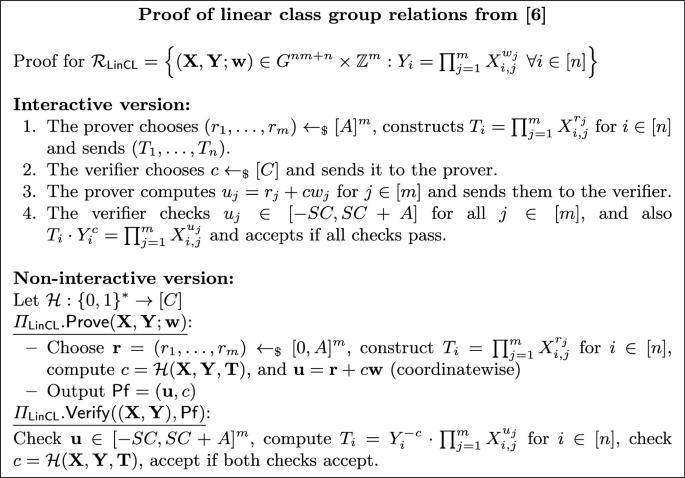
Sound Proofs of Discrete Logarithm Equality and Linear Relations. The proofs of knowledge above are either somewhat inefficient, in the first case, or require that the basis is not controlled by the adversary, in the second. In several cases we will need proofs of discrete logarithm equality where we can settle for proofs with soundness, instead of proofs of knowledge. We can instantiate these from the proofs for linear relations in a class group introduced in [6]. In this case, soundness requires the rough-order assumption also introduced in [6].
Consider the following relation \(\mathcal {R}_{\textsf{LinCL}}\) given byFootnote 5
For \(m=1\), this is in fact the discrete logarithm equality relation
A \(\varSigma \)-protocol for \(\mathcal {R}_{\textsf{LinCL}}\), parametrized by \(A,C\in \mathbb {N}\), is given in Fig. 3. We denote \(\textbf{X}=(X_{i,j})_{i\in [n], j\in [m]}, \textbf{Y}=(Y_i)_{i\in [n]}, \textbf{w}=(w_j)_{j\in [m]}\).
Proof of knowledge of discrete logarithm from [14]
Lemma 1
([6]). The interactive proof in Fig. 3 is complete, computationally sound with soundness error \(1/C+\textsf{negl}\) under the \(\texttt {RO}_C\) assumption and statistically special honest-verifier zero knowledge if SC/A is negligible. By the Fiat-Shamir heuristic, the non-interactive version has the same properties in the random oracle model.
Remark 1
By the result of [22], the non-interactive version of the proof in Fig. 3 obtained via the Fiat-Shamir transform in the random oracle model is simulation sound.
3 PVSS over Class Groups
3.1 The PVSS Scheme
Our PVSS is similar to the DHPVSS scheme in YOLO YOSO [11], which we recall in the full version [10] for comparison. In particular we replace the El Gamal encryption used there by the Castagnos-Laguillaumie-Tucker encryption from [17]. The benefit we obtain over DHPVSS is that in our scheme parties can reconstruct the share “field” secret \(s\in \mathbb {Z}_q\), where in DHPVSS they can only reconstruct \(g^s\) (with g being a generator of the DDH-hard group \(\mathbb {G}\)). This is fine for applications of PVSS such as distributed randomness beacons [8] and can also be turned into a PVSS for \(\mathbb {Z}_q\) by defining the secret to be \(s'=H(g^s)+a\), for some efficiently computable \(H:\mathbb {G}\rightarrow \mathbb {Z}_q\) and an element a published by the dealer. But then the PVSS is no longer linear, which makes it harder to be used for MPC-related applications and DKG.
In exchange, there arise some technical challenges with respect to [11]. First, several steps of the construction need ZK proofs, and ZK proofs of knowledge are somewhat inefficient or only applicable under certain conditions (see remarks above and Sect. 2.3). Fortunately, we show that we only really need proofs of knowledge in the key generation algorithm. This means that using less efficient PoKs (\(\varPi _{\textsf{DL1}}\) in Sect. 2.3) may not be so problematic as key generation can be carried out long before the PVSS takes place; but also one can use the more efficient proof \(\varPi _{\textsf{DL2}}\) from [14] (Section 2.3) by randomizing the generator \(g_q\). The second issue will be the construction of an efficient (constant in the number of parties n) proof of correct sharing, but we defer this discussion to Sect. 3.2.
We present our scheme for a general case where the space of secrets is \(\mathbb {Z}_q^k\). For applications in this paper we only need \(k=1\), but the general case is not much harder to present an in addition PVSS with larger secrets have been considered for some applications e.g. in [9].
Proof of linear class group relations from [6]
PVSS Scheme qCLPVSS. Let \(\lambda \) be the security parameter and \(q>2^\lambda \) prime. Let k (size of the secret), t (privacy threshold) and n (number of parties) be natural numbers, with \(k,t,n=\textsf{poly}\!\!\left( \lambda \right) \) (and hence we can assume \(n+k\le q\)) and \(k+t\le n\). Our scheme \(\textsf{qCLPVSS}\) consists of the tuple of algorithms \((\textsf{Setup},\textsf{KeyGen},\textsf{VerifyKey},\textsf{Dist},\textsf{VerifySharing},\textsf{DecShare},\textsf{Rec},\textsf{VerifyDec})\) below:
-
\(\textsf{qCLPVSS}.\textsf{Setup}(1^\lambda ,q,k,t,n)\):
-
1.
Specify a set of pairwise distinct points \(\{\beta _1,\dots ,\beta _k,\alpha _1,\dots ,\alpha _n\}\subset \mathbb {Z}_q\).
Let \(\textsf{pp}_{\textsf{Sh}}=(q, k, t, n,(\beta _j)_{j\in [k]}, (\alpha _i)_{i\in [n]})\)
-
2.
Run \(\textsf{pp}_{\textsf{CL}}:=(q,\bar{s},f,g_q,\hat{G},F,\rho )\leftarrow \textsf{CLGen}(1^{\lambda },q)\).
-
3.
The output is then \(\textsf{pp}=(\textsf{pp}_{\textsf{Sh}}, \textsf{pp}_{\textsf{CL}})\).
-
1.
-
\(\textsf{qCLPVSS}.\textsf{KeyGen}(\textsf{pp},i)\):
-
1.
Sample \(\textsf{sk}_i\leftarrow \mathcal {D}_q\) and compute \(\textsf{pk}_i=g_q^{\textsf{sk}_i}\).
-
2.
Create proof \(\textsf{Pf}_{{\textsf{pk}}_{i}}=\texttt {NIZKPoK}_{\textsf{DL}}.\textsf{Prove}(\{(g_q,\textsf{pk}_i);\textsf{sk}_i: \textsf{pk}_i=g_q^{\textsf{sk}_i}\})\)
-
3.
Output\((\textsf{sk}_i, \textsf{pk}_i,\textsf{Pf}_{{\textsf{pk}}_{i}})\).
-
1.
-
\(\textsf{qCLPVSS}.\textsf{VerifyKey}(\textsf{pp},i,\textsf{pk}_i,\textsf{Pf}_{{\textsf{pk}}_{i}})\):
Run \(\texttt {NIZKPoK}_{\textsf{DL}}.\textsf{Verify}\) on \(\textsf{Pf}_{{\textsf{pk}}_{i}}\) with respect to statement \((g_q,\textsf{pk}_i)\) and output its result.
-
\(\textsf{qCLPVSS}.\textsf{Dist}(\textsf{pp},(\textsf{pk}_i)_{i\in [n]},\textbf{s})\), where \(\textbf{s}=(s_1,\dots ,s_k)\in \mathbb {Z}_q^k\):
-
1.
Create a Shamir sharing of \(\textbf{s}\): sample a polynomial \(p(X)\in \mathbb {Z}_q[X]_{\le t+k-1}\) with \(p(\beta _j)=s_j\) for \(j\in [k]\) and set \(\sigma _i=p(\alpha _i)\) for \(i\in [n]\).
-
2.
Sample \(r\leftarrow \mathcal {D}_q\) and compute \(R=g_q^r\).
-
3.
Create \(B_i=\textsf{pk}_i^r\cdot f^{\sigma _i}\).
-
4.
Create the sharing proof (not necessarily of knowledge)
$$\textsf{Pf}_{\textsf{Sh}}=\texttt {NIZK}_{\textsf{Sh}}.\textsf{Prove}(\{(f,g_q,(\textsf{pk}_i)_{i=1}^n,R, (B_i)_{i=1}^n); (p(X),r):$$$$\deg p(X)\le t+k-1,\ R=g_q^r,\ B_i=\textsf{pk}_i^r \cdot f^{p(\alpha _i)}\ \forall i\in [n]\})$$We show how to instantiate \(\texttt {NIZK}_{\textsf{Sh}}\) in Sect. 3.2.
-
5.
Output \((R, B_1,\dots ,B_n, \textsf{Pf}_{\textsf{Sh}})\). To make it syntactically consistent with our definition in Sect. 2.1, we define \(C_i:=(R,B_i)\) for all \(i\in [n]\), and notice that \((R, B_1,\dots ,B_n, \textsf{Pf}_{\textsf{Sh}})\) contains the same information as \((C_1,\dots ,C_n,\textsf{Pf}_{\textsf{Sh}})\).
-
1.
-
\(\textsf{qCLPVSS}.\textsf{VerifySharing}(\textsf{pp},(\textsf{pk}_i)_{i\in [n]}, (C_1,\dots ,C_n, \textsf{Pf}_{\textsf{Sh}}))\), where \(C_i=(R,B_i)\):
Run \(\texttt {NIZK}_{\textsf{Sh}}.\textsf{Verify}\) on \(\textsf{Pf}_{\textsf{Sh}}\) with respect to statement \((f,g_q,(\textsf{pk}_i)_{i=1}^n,R, (B_i)_{i=1}^n)\) and output its result.
-
\(\textsf{qCLPVSS}.\textsf{DecShare}(\textsf{pp},\textsf{pk}_i,\textsf{sk}_i,C_i)\), where \(C_i=(R,B_i)\):
-
1.
Compute \(f_i=B_i\cdot R^{-\textsf{sk}_i}\), \(A_i=\textsf{CLSolve}(f_i)\) and \(M_i=f_i^{-1}\cdot B_i\).
-
2.
Compute \(\textsf{Pf}_{\textsf{Dec}_{i}}=\texttt {NIZK}_{\textsf{DLEQ}}.\textsf{Prove}(\{(g_q,R,\textsf{pk}_i,M_i);\textsf{sk}_i:g_q^{\textsf{sk}_i}=\textsf{pk}_i, R^{\textsf{sk}_i}=M_i\})\). Again this does not need to be a proof of knowledge.
-
3.
Output \((A_i, \textsf{Pf}_{\textsf{Dec}_{i}})\).
-
1.
-
\(\textsf{qCLPVSS}.\textsf{Rec}(\textsf{pp}, \{A_i: i\in \mathcal {T}\})\):
-
1.
If \(|\mathcal {T}|<t+k\), output \(\bot \).
-
2.
Otherwise select \(\mathcal {T}'\subseteq \mathcal {T}\), with \(|\mathcal {T}'|=t+k\) (e.g. the first \(t+k\) indices in \(\mathcal {T}\)).
-
3.
For each \(j\in [k]\), define \(s'_j=\sum _{i\in \mathcal {T}'}A_i\cdot {L_i(\beta _j)}\) where \(L_i(X)=\textrm{Lag}_{i,\mathcal {T}',}\)\({\{\alpha _i:i\in \mathcal {T}'\}}\).Footnote 6
-
4.
Output \(\textbf{s}'=(s'_1,\dots ,s'_k)\) .
-
1.
-
\(\textsf{qCLPVSS}.\textsf{VerifyDec}(\textsf{pp}, C_i, A_i, \textsf{Pf}_{{\textsf{Dec}}_{i}})\) where \(C_i=(R,B_i)\):
Compute \(M_i=f^{-A_i}\cdot B_i\) and run \(\texttt {NIZK}_{\textsf{DLEQ}}.\textsf{Verify}\) on \(\textsf{Pf}_{{\textsf{Dec}}_{i}}\) with respect to statement \((g_q,R,\textsf{pk}_i,M_i)\), and output the result of the verification.
We now show that the PVSS above guarantees the security properties from Sect. 2.1. In particular there is \(t+k\)-reconstruction and t-IND2-privacy.
Theorem 4
\(\textsf{qCLPVSS}\) is a correct PVSS with \(t+k\)-reconstruction
Proof
The proof is quite immediate, we give a detailed proof in the full version [10].
Theorem 5
-
If \(\texttt {NIZKPoK}_{DL}\) is a proof of knowledge with knowledge error negligible in \(\lambda \) then \(\textsf{qCLPVSS}\) has verifiability of key generation.
-
If \(\texttt {NIZK}_{\textsf{Sh}}\) is a proof with soundness error negligible in \(\lambda \) then \(\textsf{qCLPVSS}\) has verifiability of sharing distribution.
-
If \(\texttt {NIZK}_{\textsf{DLEQ}}\) with soundness error negligible in \(\lambda \) then \(\textsf{qCLPVSS}\) has verifiability of share decryption.
Proof
Trivial as the statements proved by the NIZK proofs exactly guarantee correct key generation, sharing distribution and share decryption, respectively.
In order to prove t-IND2-secrecy, we need to introduce a modified hardness assumption, and show it is implied by \(\texttt {DDH}\text{- }\!\texttt {f}\). The new assumption, \(\texttt {DDH}\text{- }\!\texttt {qf}\) is very similar to \(\texttt {DDH}\text{- }\!\texttt {f}\) but the generator of G is replaced by the generator of \(G^q\).
Definition 5
(\(\texttt {DDH}\text{- }\!\texttt {qf}\) hardness assumption). For a PPT \(\mathcal {A}\) let
\(\texttt {DDH}\text{- }\!\texttt {qf}\) is hard for \(\textsf{CLGen}\) if \(\forall \) PPT \(\mathcal {A}\), \(Adv_{\mathcal {A}}^{\texttt {DDH}\text{- }\!\texttt {qf}}(\lambda )\) is negligible in \(\lambda \).
Lemma 2
If \(\texttt {DDH}\text{- }\!\texttt {f}\) is hard for \(\textsf{CLGen}\), then \(\texttt {DDH}\text{- }\!\texttt {qf}\) is hard for \(\textsf{CLGen}\).
Proof
We show the proof in the full version [10].
Theorem 6
\(\textsf{qCLPVSS}\) is t-IND2-secret under \(\texttt {DDH}\text{- }\!\texttt {f}\), assuming \(\texttt {NIZK}_{\textsf{Sh}}\), \(\texttt {NIZK}_{\textsf{DLEQ}}\) are zero-knowledge proofs and \(\texttt {NIZKPoK}_{\textsf{DL}}\) is a zero-knowledge proof of knowledge.
Proof
The proof is presented in the full version [10].
3.2 Instantiating the Proofs
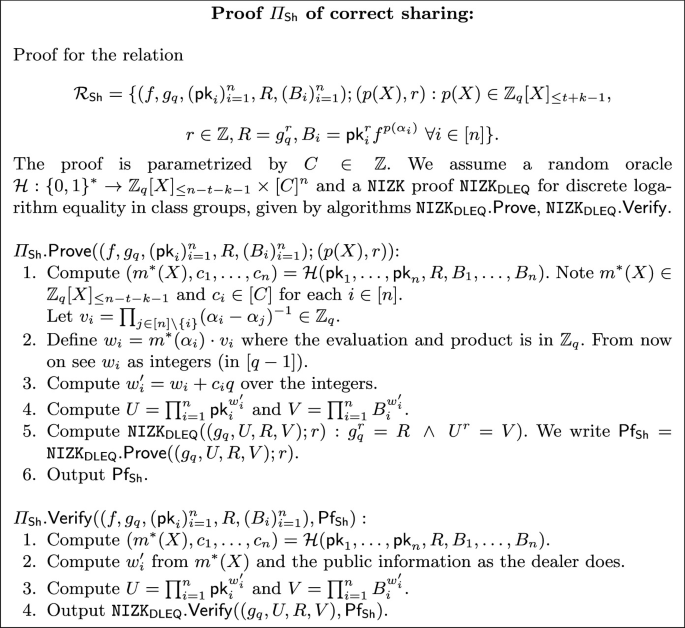
Sharing Proof. We discuss how to instantiate the sharing proof \(\textsf{Pf}_{\textsf{Sh}}\), which we consider the main technical challenge of the PVSS construction. Recall this is a zero knowledge proof for the language
As we have mentioned before, we use the overall idea from YOLO YOSO [11], which in turn consists in using the SCRAPE check from Theorem 1 in an efficient way which yields a constant size (in n) proof, but we will need to do adjustments to this strategy.
The idea from [11], translated to our class group framework, is as follows: if we sample a random polynomial \(m^*\in \mathbb {Z}_q[X]_{\le n-t-k+1}\) then for any correct sharing (\(\sigma _i=p(\alpha _i)\) with \(\deg p(X)\le t\)) we must have \(\sum _{i=1}^n \sigma _i\cdot v_i\cdot m^*(\alpha _i)=0\) in \(\mathbb {Z}_q\) for the \(v_i\)’s defined in Theorem 1.
We embed \(w_i=v_i\cdot m^*(\alpha _i)\in \mathbb {Z}_q\) as integers in \([q-1]\), and compute the products \(U=\prod _{i=1}^n \textsf{pk}_i^{w_i}\) and \(V=\prod _{i=1}^n B_i^{w_i}\). If the \(B_i\)’s are correct then \(V=\prod _{i=1}^n{\textsf{pk}_i}^{rw_i}f^{\sigma _iw_i}\) but the second term cancels out because \(\sum _{i=1}^n \sigma _i w_i=0\mod q\) (recall f is of order q). So then \(V=U^r\) which can be proved using a proof of discrete logarithm equality with \(R=g_q^r\). If the \(\sigma _i\)’s are not valid, with large probability \(\sum _{i=1}^n \sigma _i w_i\ne 0\mod q\) (by Theorem 1), the F-part of the product does not cancel out, and the proof will not pass.
However, there is a problem that did not appear in the setting of [11]: it may be that a malicious prover sets \(B_i=(H_i\textsf{pk}_i^r)\cdot f^{\sigma _i}\), with correct shares \(\sigma _i\) but where \(H_i\ne 1\) are elements in \(\hat{G}^q\) such that, when computing V the product \(\prod H_i^{w_i}\) cancels out and this is not caught by the proof.
We solve this problem as follows: we randomize further the values \(w_i\) by replacing them with \(w'_i=w_i+c_iq\) for some random \(c_i\in [C]\). This does not affect the F-part of the equation, as we are adding a multiple of q, but as we will see the prover can only pass this test with high probability by either setting all \(H_i=1\) (and then the shares are correct) or by breaking the rough order assumption from [6]. In addition, this modification does not affect the communication complexity, while the computation only increases slightly by computing n products and sums of integers. The proof \(\varPi _{\textsf{Sh}}\) of correct sharing is presented in Fig. 4.
To prove the soundness of \(\varPi _{\textsf{Sh}}\) we first need the following lemma.
Lemma 3
Let \(H_i\in \hat{G}^q\) be elements in \(\hat{G}^q\) such that there is at least one element \(H_j\ne 1\). Let \(w_i\in \mathbb {Z}\). Sample \((c_1,\dots ,c_n)\leftarrow _{\$}[C]^{n}\) for some integer \(C>1\). Then if \(H_j\) has order \(\ge C\), the probability that \(\prod _{i=1}^{n} H_i^{w_i+c_iq}=1\) is at most 1/C.
Proof
Without loss of generality, we assume \(j=1\), i.e. the order of \(H_1\) is at least C. Then fix any \((c_2,\dots ,c_n)\in [C]^{n-1}\) and consider the quantities \(M_c=H_1^{w_1+cq}\prod _{i=2}^{n}H_i^{w_i+c_iq}\). Clearly if \(M_c=M_{c'}\) for \(c\ne c'\) then \(1=M_c\cdot M_{c'}^{-1}=H_1^{(c-c')q}\). But since the order of \(\hat{G}^q\) is coprime to q, then \(H_1^{(c-c')}=1\), a contradiction with the order of \(H_1\) (since \(|c-c'|\le C-1\)). Therefore at most one \(M_c\) can equal 1. Since this is for any \((c_2,\dots ,c_{n-1})\in [C]^{n-1}\) we obtain the lemma.
Theorem 7
In the random oracle model, and assuming \(\texttt {RO}_C\) is hard for \(\textsf{CLGen}\), \(\varPi _{\textsf{Sh}}\) in Fig. 4 is a proof for the relation \(\mathcal {R}_{\textsf{Sh}}\) with soundness error \(\epsilon _{\textsf{DLEQ}}+1/C+1/q+\textsf{negl}(\lambda )\), where \(\epsilon _{\textsf{DLEQ}}\) is the soundness error of \(\texttt {NIZK}_{\textsf{DLEQ}}\). It is zero knowledge assuming \(\texttt {NIZK}_{\textsf{DLEQ}}\) is.
Proof
The proof is shown in the full version [10].
Remark 2
By [22], \(\varPi _{\textsf{Sh}}\) is simulation sound in the random oracle model.
Discrete Logarithm Knowledge and Discrete Logarithm Equality. We have seen that \(\texttt {NIZK}_{\textsf{Sh}}\), and hence the sharing distribution algorithm \(\textsf{qCLPVSS}.\textsf{Share}\), can be instantiated by \(\varPi _\textsf{Sh}\) as long as we have a proof \(\texttt {NIZK}_{\textsf{DLEQ}}\) of discrete logarithm equality. Moreover, we also need \(\texttt {NIZK}_{\textsf{DLEQ}}\) for the sharing decryption \(\textsf{DecShare}\). In both cases, we do not need a proof of knowledge of the exponent, so we can use \(\varPi _{\textsf{LinCL}}\) in Fig. 3. This proof requires the \(\texttt {RO}_C\) assumption, but we already need this assumption for \(\varPi _{\textsf{Sh}}\) anyway.
Finally, we do need a proof of knowledge \(\texttt {NIZKPoK}_{\textsf{DL}}\) of discrete logarithm in the key generation algorithm \(\textsf{qCLPVSS}.\textsf{KeyGen}\). We have listed two options in Sect. 2.3: either we use \(\varPi _{\textsf{DL1}}\), which has a higher complexity but which does not require hardness assumptions and can be applied regardless of how \(g_q\) is chosen; or we use \(\varPi _{\textsf{DL2}}\) which relies on the \(\texttt {LO}_C\) and \(\texttt {SR}\) assumptions and where we need to slightly modify the setup to replace \(g_q\) by a randomized \(g'_q=g_q^{\rho }\) for a random \(\rho \) which the adversary cannot control. We remark that, although \(\varPi _{\textsf{DL2}}\) only guarantees witness extraction for the slightly different relation \(\mathcal {R'}_{DL}\) where only knowledge of integers \(\rho _0\) and \(\rho _1\) with \(g_q^{2^{-\rho _0}\rho _1}=\textsf{pk}_i\) is guaranteed, this is not really a big problem for us: the one place where we need extraction of the exponent is in the proof of Theorem 6, and there we can replace the extracted \(\textsf{sk}_i\) by \({2^{-\rho _{i,0}}}{\rho _{i,1}}\) and use the fact that square roots in \(G^q\) are computed efficiently.
3.3 Complexity
We focus on the communication complexity of \(\textsf{qCLPVSS}\), since this is usually the main bottleneck in PVSS applications. Let \(\kappa \) be a statistical security parameter for soundness, zero knowledge (so both soundness error and statistical distance in the zero knowledge simulation are bounded by \(2^{-\kappa }\)), and also so that we instantiate \(\mathcal {D}_q\) by sampling uniformly in \([2^{\kappa }\bar{s}]\) (see Sect. 2.2).Footnote 7
-
\(\textsf{qCLPVSS}.\textsf{KeyGen}\): 1 element in G and \(\sim \kappa ^2+\kappa \log \kappa \) bits (using \(\varPi _{\textsf{DL1}}\)) or \(\sim 3\kappa +\log (\bar{s})\) (using \(\varPi _{\textsf{DL2}}\)) bits per party.
-
\(\textsf{qCLPVSS}.\textsf{Dist}\): \(n+1\) elements in G and \(\sim 3\kappa +\log (\bar{s})\) bits
-
\(\textsf{qCLPVSS}.\textsf{DecShare}\): \(\sim 3\kappa +\log (\bar{s})+\log q\) bits (per party)
Moreover, the encrypted shares are n CL-\(\texttt {HSM}\) ciphertexts (where we only send R once) and may benefit from compression techniques [5].
Although we do not estimate the computational complexity in details, the main point of our construction is that it maintains the linear complexity in terms of group operations that was achieved in previous works [8, 9, 11]. While group operations on class groups have higher complexity than over groups defined on elliptic curves, the concrete times estimated in [5] show that the overhead in computation time is of about an order of magnitude.
Comparison with YOLO YOSO [11]. The PVSS scheme in YOLO YOSO requires essentially the same amount of group operations computation and group elements communication. Since our scheme operates over class groups, it clearly has an overhead in relation to elliptic curve implementations of YOLO YOSO as estimated in [5]. However, we achieve more flexibility in being able to retrieve the original shared secret s (or the result \(s'\) of linear operations on multiple secrets), whereas YOLO YOSO only allows for obtaining \(g^s\) (or the result \(s'\) of linear operations on multiple secrets). Moreover, we prove the IND-2-security notion from [31], whereas YOLO YOSO only shows the weaker IND-1-security also from [31], although we think it can also be proved IND-2-secure. In contrast, previous (and less efficient) PVSS using similar techniques [8, 9]are only IND-1. This is because these are based on a OW-CPA secure encryption scheme that allows for the necessary linear operations used in the NIZKs of sharing correctness.
Comparison with [32]. The work [32] constructs a PVSS scheme from class groups, motivated by distributed key generation. The shares are encrypted in the same way as ours (namely the dealer sends \((R, (B_i)_{i=1}^n )\). However, our scheme presents several advantages: the remaining communication of the sharing phase (the size of the proof \(\textsf{Pf}_{\textsf{Sh}}\)) is independent of n and t, while they require to send commitments to the t coefficients of the polynomial, as well as somewhat larger proofs. Moreover, our PVSS achieves the strong IND-2-security property, while their construction does not satisfy the notion of indistinguishability of secrets, but a weaker notion of privacy that allows leakage. This leakage is fine for their DKG application, but it may not be adequate in other applications.
4 Application: Distributed Key Generation
We extend \(\textsf{qCLPVSS}\) to construct a distributed key generation protocol for a given cyclic group \(\mathbb {H}\) of prime order q where DDH is assumed to be hard (e.g. an elliptic curve group). We assume a static adversary that can corrupt at most \(t\le \frac{n-1}{2}\) parties. Our goal is for parties to generate partial public keys \(\textsf{tpk}_i=h^{p(\alpha _i)}\) and a global public key \(\textsf{tpk}=h^{p(\beta )}\), where each party i privately knows \(\textsf{tsk}_i=p(\alpha _i)\). The global secret key is implicitly defined as \(\textsf{tsk}=p(\beta )\).
We will present two constructions of discrete key generation: the first one has two rounds of communication but has the property that the public key can not be biased by the adversary. The second is a non-interactive protocol (only one round of communication) but a rushing adversary can bias the public key. Note this is unavoidable for one-round distributed key generation (see [33]).
4.1 Two-Round DKG with Unbiasable Public Key
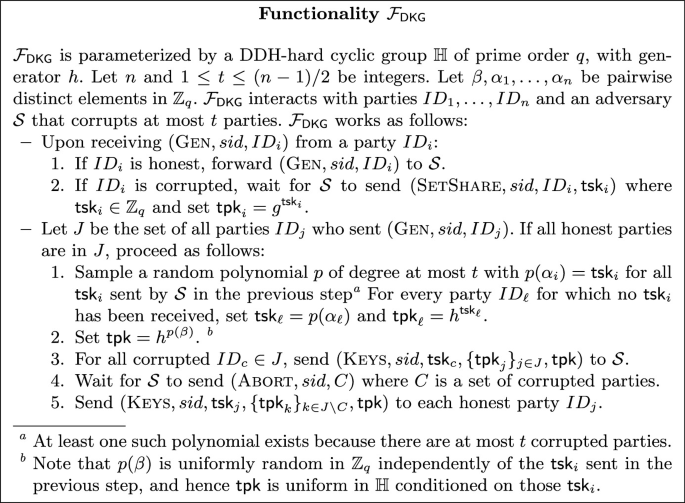
In this section we will implement the functionality \(\mathcal {F}_{\textsf{DKG}}\) in Fig. 5. Note that when interacting with this functionality, the adversary can decide on the threshold partial secret keys \(\textsf{tsk}_i\) of the corrupted parties. But the global secret key \(\textsf{tsk}\) is chosen by the functionality uniformly at random and independently of these \(\textsf{tsk}_i\), and hence the adversary has no control on the threshold public key \(\textsf{tpk}\).
The strategy follows the general template by Katz [33], using our PVSS. Every party PVSSs a contribution \(s_j\) to the secret key. This determines a set \(\mathcal {Q}\) of parties whose sharing proofs pass the check. Parties define their \(\textsf{tsk}_i\) summing the shares received from parties in \(\mathcal {Q}\). In the second round, parties publish \(\textsf{tpk}_i=h^{\textsf{tsk}_i}\) and prove this is consistent with the encrypted shares received before.
Theorem 8
Under the \(\texttt {DDH}\text{- }\!\texttt {f}\) (for privacy of \(\textsf{qCLPVSS}\)) and \(\texttt {RO}_C\) (for verifiability of \(\textsf{qCLPVSS}\) and simulation soundness of \(\varPi _\textsf{Sh}\) and \(\varPi _{\textsf{LinCL}}\)) assumptions the protocol \(\varPi _{\textsf{DKG}}\) in Fig. 6 realizes \(\mathcal {F}_{\textsf{DKG}}\) securely in the random model in the presence of a malicious static adversary corrupting \(t\le \frac{n-1}{2}\) parties.
Proof
The proof is shown in the full version [10].
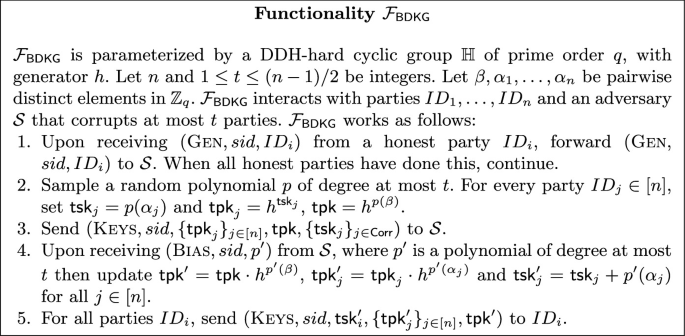
4.2 One-Round Biasable Public-Key Version
We now show a protocol that implements the functionality in Fig. 7 in one round of communication. In this case, the functionality allows the adversary to bias the public key: the functionality sends some “temporary” public keys \(\textsf{tpk}\), \(\{\textsf{tpk}_i\}_{i\in [n]}\) as well as temporary secret keys \(\textsf{tsk}_i\) for the corrupted parties, and then the adversary can choose to update the secret sharing polynomial by adding a contribution \(p'(X)\). This reflects the fact that in a one-round real protocol an adversary can wait until all honest parties have spoken, see all information it is allowed to, and in that moment then make one or more corrupted parties execute the PVSS honestly with sharing polynomials adding to some chosen \(p'(X)\).
As in the two-round protocol, every party j shares a secret \(s_j\) with the PVSS, sending \(R_j=g_q^{r_j}\) \(B_{j,i}=\textsf{pk}_i^{r_j} f^{\sigma _{j,i}}\) where \(\sigma _{j,i}=p_j(\alpha _i)\) are Shamir shares of \(p_j(\beta )=s_j\). But now, they also publish the values \(D_{j,i}:=h^{\sigma _{j,i}}\in \mathbb {H}\). This allows every party to eventually compute the i-th threshold public key as \(\textsf{tpk}_i=\prod _{j\in \mathcal {Q}} h^{\sigma _{j,i}}\) where \(\mathcal {Q}\) is again the set of parties that created the sharing honestly.
To be included in \(\mathcal {Q}\), party j needs to prove not only that \((R_j, B_{j,i})\) form a correct PVSS sharing but also that \(B_{j,i}\) and \(D_{j,i}\) are consistent. In other words, we will need a NIZK proof \(\textsf{Pf}_{\textsf{ExtSh}}\) for the relation
We show how to accomplish this with a constant-size proof next.
As in \(\textsf{qCLPVSS}\), we can reduce testing whether \(B_{i}\) are of the correct form with respect to R (i.e. \(B_{i}=\textsf{pk}_i^r f^{p(\alpha _i)}\) for \(p(X)\in \mathbb {Z}_q[X]_{\le t}\) and where \(r\in \mathbb {Z}\) is such that \(g_q^r\)) to a DLEQ proof \(g_q^r=R\), \(U^r=V\). Moreover, thanks to the SCRAPE test, verifiers can locally check if \(D_{i}=h^{\hat{p}(\alpha _i)}\) for some \(\hat{p}\in \mathbb {Z}_q[X]_{\le t}\).
We still need to guarantee that \(p(X)=\hat{p}(X)\), i.e. the shares hidden by \(B_i\) and \(D_i\) are the same. It is enough to prove that \(p(\alpha _i)=\hat{p}(\alpha _i)\) for all \(i\in [t+1]\). We can do this by testing \(\sum _{i=1}^{t+1} e_i p(\alpha _i)=^?\sum _{i=1}^{t+1} e_i \hat{p}(\alpha _i)\) for random \(e_1,\dots ,e_{t+1}\in \mathbb {Z}_q\) sampled via the random oracle. This would guarantee the property with probability \(1-1/q\) over the random choice of the \(e_i\).
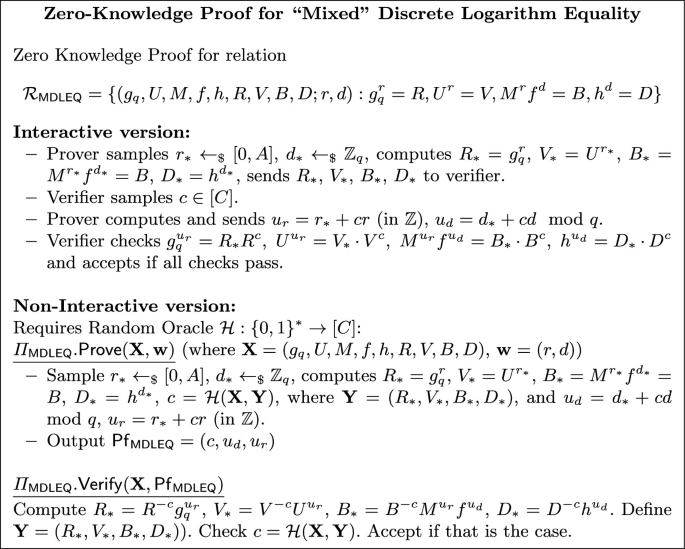
To test this we define \(D=\prod _{i=1}^{t+1} D_i^{e_i}\) and \(B=\prod _{i=1}^{t+1} B_i^{e_i}\), \(M=\prod _{i=1}^{t+1} \textsf{pk}_i^{e_i}\) (all of which can be computed publicly) and \(d=\sum _{i=1}^t e_i p(\alpha _i)\) (computed privately by the prover). If the prover has been honest then \(M^rf^d=B\). This suggests we can reduce the problem to proving existence of r in \(\mathbb {Z}\) and d in \(\mathbb {Z}_q\) with \(g_q^r=R\), \(U^r=V\), \(M^rf^d=B\), \(h^d=D\). We will indeed prove this is sound. Finally, this last statement can then be addressed with a proof similar to the \(\varPi _{\textsf{LinCL}}\) in Sect. 2.3, with the only difference that h, D are in a different group and d is in \(\mathbb {Z}_q\). We remark this type of “mixed” statements have already been addressed in similar ways in papers such as [6, 13, 14].
We start by presenting this last proof, which we call \(\varPi _\textsf{MDLEQ}\) in Fig. 8. Again, as in other similar protocols, the proof is paramtetrized by \(C,A\in \mathbb {N}\) and to guarantee zero knowledge, we need that the witness is in an interval \([-S,S]\) and CS/A is negligible.
Theorem 9
The interactive proof in Fig. 8 has soundness error \(1/C+\textsf{negl}(\lambda )\) if the \(\texttt {RO}_C\) assumption holds. It is statistically zero-knowledge if the witness r is in \([-S,S]\) and CS/A is negligible. By the Fiat-Shamir heuristic, the non-interactive version has the same properties in the random oracle model.
We use \(\varPi _{\textsf{MDLEQ}}\) as a building block for the proof \(\varPi _{\textsf{ExtSh}}\), Fig. 9.
Theorem 10
In the random oracle model, and assuming \(\texttt {RO}_C\) is hard for \(\textsf{CLGen}\), \(\varPi _{\textsf{ExtSh}}\) ( Fig. 9) is a simulation sound proof for the relation \(\mathcal {R}_{\textsf{ExtSh}}\) with soundness error \(\epsilon _{\textsf{MDLEQ}}+1/C+3/q+\textsf{negl}(\lambda )\), where \(\epsilon _{\textsf{MDLEQ}}\) is the soundness error of \(\varPi _{\textsf{MDLEQ}}\). If we use the same C in \(\varPi _{\textsf{MDLEQ}}\) as in this proof, the soundness error is \(2/C+3/q+\textsf{negl}(\lambda )\). Moreover, it is zero-knowledge assuming \(\varPi _{\textsf{MDLEQ}}\) is.
Finally, we present our one-round DKG protocol in Fig. 10.
Theorem 11
Under the \(\texttt {DDH}\text{- }\!\texttt {f}\) (for privacy of \(\textsf{qCLPVSS}\)) and \(\texttt {RO}_C\) (for verifiability of \(\textsf{qCLPVSS}\) and simulation soundness of \(\varPi _{\textsf{LinCL}}\)) assumptions the protocol \(\varPi _{\textsf{BDKG}}\) in Fig. 10 realizes \(\mathcal {F}_{\textsf{BDKG}}\) securely in the random model in the presence of a malicious static adversary corrupting \(t\le \frac{n-1}{2}\) parties.
The proofs of Theorems 9, 10 and 11 are presented in the full version [10].
Communication Complexity and Comparison. In Table 1 we list the communication complexities of our two protocols, and compare them to the currently best round-efficient distributed key generation protocols for the cases of biasable and unbiasable public keys, which are both based on Paillier encryption. For the one-round, biasable public key case, we use the Fouque-Stern [23] protocol. For the two-round case, we use the suggested instantiation with Paillier from [33], where we instantiate the NIZKs as in Fouque-Stern. We observe that the communication is dominated by the first summand and that therefore for a moderately large amount of parties, our DKG protocol will communicate less information as long as \(k_{\hat{G}}\) is somewhat smaller than \(3k_N\). Current security estimations ( [5, 21]) indicate this is the case for reasonable security parameters, e.g. 128-bit security. In fact, note that the dominating factor in our protocol consists of the \(n^2\) share encryptions (n per party), which are in fact roughly \(\frac{1}{2}n^2\) CL-HSM ciphertexts (since \(R_j\) is common to all encryptions by party j), the Paillier based constructions communicate \(3n^2k_N\) bits (\(\sim \frac{3}{2} n^2\) Paillier ciphertexts) and [5] estimates each CL-ciphertext to be 1.5 to 2.3 shorter than a Paillier ciphertext depending on the security parameter and for q of 224 bits. Hence, our communication is around 4.5 to 7 times smaller than [23, 33].
5 Application: YOSO MPC
In the YOSO model, parties can only speak once, i.e. after each party sends a message it can no longer participate in the execution. Moreover, the next committee of parties that take over the execution is selected at random and remains anonymous until they act. This requires a mechanism for transferring the secret state kept by each party in the comittee responsible for the current round to the committee responsible to the next round. As observed in [26], starting from the protocol [19] is a promising approach for keeping this state to a minimum. In the CDN protocol, the only secret state that parties must hold throughout the execution consists of shares of a secret key for a linearly homomorphic threshold encryption scheme, instead of requiring parties to hold shares of each intermediate gate output. In a recent work [6], linearly homomorphic threshold encryption based on the CL-framework was leveraged to realize this approach with a transparent setup by constructing a suitable DKG and a re-sharing protocol that allows for transferring secret key shares among committees (assuming receiver anonymous communication channels).
As a first step, we endow our PVSS scheme \(\textsf{qCLPVSS}\) with a publicly verifiable re-sharing scheme in order to construct an efficient mechanism for transfering secret state among committees in the YOSO model. This re-sharing mechanism already improves on the efficiency of the one proposed in [6]. We only need to publish a set of encrypted shares and a NIZK of re-sharing validity as many elements of \(\mathbb {Z}_q\) as encrypted shares, whereas the protocol of [6] has each committee execute one VSS instance towards the next committee and one towards the second next committee. Later on, we show how the efficient encryption to the future scheme of YOLO YOSO can be combined with this approach to realize the full communication infrastructure needed to transfer state among committees.
5.1 Resharing
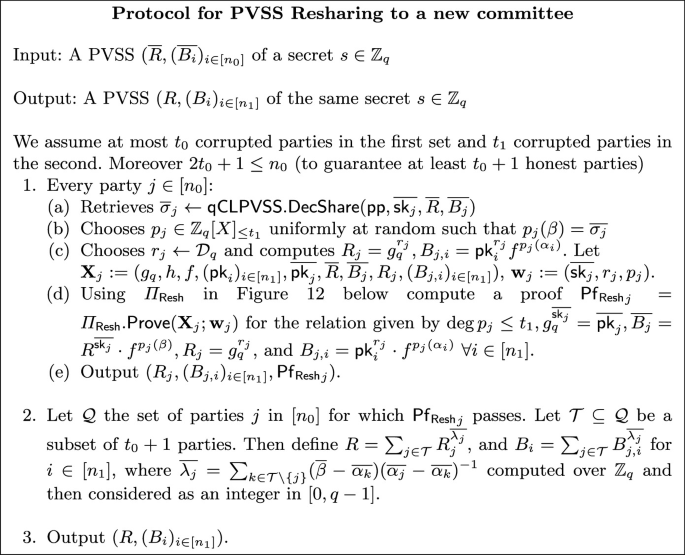
We consider how a set of parties who have a correct PVSS sharing of a secret with \(\textsf{qCLPVSS}\) can reshare this to a new set of parties. In the following we assume the case \(k=1\) (one secret in \(\mathbb {Z}_q\)) and we consider a starting set of \(n_0\) parties, with privacy threshold \(t_0\) and we denote their evaluation points \(\overline{\alpha _1},\dots ,\overline{\alpha _{n_0}}\) for the shares and \(\overline{\beta }\) for the secret. Moreover, let \(\overline{\textsf{pk}_i},\overline{\textsf{sk}_i}\) their keys. Meanwhile for the next set of parties we have respectively \(\alpha _1,\dots ,\alpha _{n_1}\), \(\beta \) and \(\textsf{pk}_i\), \(\textsf{sk}_i\) respectively. Now given a secret s shared with degree-\(t_0\) Shamir secret sharing, with shares \(\overline{\sigma _{i}}\) for \(i\in [n_0]\) we know that, for any set \(\mathcal {T}\) of size \(t_0+1\), \(s=\sum _{i\in T} \overline{\lambda _i}\overline{\sigma _i}\) where \(\overline{\lambda _i}=L_i(\beta )\) for \(L_i=\textrm{Lag}_{i,\mathcal {T},{(\overline{\alpha _i})}}\), i.e. \(\overline{\lambda _i}=\prod _{j\in \mathcal {T}\setminus \{i\}}(\overline{\beta }-\overline{\alpha _j})(\overline{\alpha _i}-\overline{\alpha _j})^{-1}\). Since Shamir secret sharing is linear, it is enough that such a set \(\mathcal {T}\) correctly reshare their shares to the new committee of parties: party i, having received \(\sigma _{j,i}\) as a share of \(\overline{\sigma _j}\) for each \(j\in \mathcal {T}\), can then compute \(\sum _{i\in \mathcal {T}} \overline{\lambda _i}\sigma _{j,i}\) and by linearity this will form a new sharing of s.
Note that in PVSS, we have the advantage that there is no need for dispute resolution: everyone can compute \(\mathcal {T}\) by themselves, provided that there is a proof of correct sharing. This enables its use in the YOSO model, as share receivers do not need to speak at that point. We do need that there are at least \(t_0+1\) honest parties in the first set, i.e. \(2t_0+1\le n\).
The crux of the protocol is proving a correct resharing. If \((\overline{R},(\overline{B}_j)_{j\in [n_0]})\) is the original sharing, party j will create a polynomial with \(p_j(\beta )=\overline{\sigma _{j}}\), use \(\textsf{qCLPVSS}\) for creating a sharing \((R_j, B_{j,i})\) where the \(B_{j,i}\) encrypt \(p_j(\alpha _i)\) and show not only correctness of this sharing, but also that \((\overline{R},\overline{B}_j)\) decrypts to \(p_j(\beta )\).
We show the resharing protocol in Fig. 11 and later we explain the proof of resharing in more detail below. As for security, note that the IND2 security property of the PVSS directly guarantees that a set containing at most \(t_0\) parties of the first committee and \(t_1\) parties of the second can still not distinguish between sharings of two secrets. The soundness of the proofs will guarantee that a party is included in \(\mathcal {Q}\) if they have reshared their share correctly. From \(\mathcal {Q}\) parties can then determine \(\mathcal {T}\).
We now detail the proof of resharing \(\varPi _{\textsf{Resh}}\)(Figure 12). Consider
This is the usual \(\mathcal {R}_{\textsf{Sh}}\) augmented with the fact that the secret \(p(\beta )\) is the value committed by \((\overline{\textsf{pk}}, \overline{B})=(g_q^{\overline{\textsf{sk}}},\overline{R}^{\overline{\textsf{sk}}}\cdot f^{p(\beta )})\). We will use the SCRAPE test, now applied to the \(n+1\) evaluation points \(\beta ,\alpha _1,\dots ,\alpha _n\). We rename \(\alpha _0:=\beta \) for simplicity. Then we need to sample \(m^*\) of degree \(n-t-1\) (rather than \(n-t-2\) as before), and define \(v_i\), now for all \(i\in [0,n]\) and including \(\alpha _0\). Given \(w_i=m^*(\alpha _i)\cdot v_i\), the SCRAPE test implies \(\sum _{i=0}^n p(\alpha _i)w_i=0\) for any p of \(\deg p\le t\).
Now if we compute \(U=\prod _{i=1}^n \textsf{pk}_i\) and \(V=\prod _{i=1}^n B_i^{w_i}\) as in previous proofs, we can eventually reduce the task to showing existence of \(r,\overline{\textsf{sk}}\) with \(g_q^r=R\), \(g_q^{\overline{\textsf{sk}}}=\overline{\textsf{pk}}\) and \(U^r\cdot (\overline{R}^{w_0})^\textsf{sk}=V\cdot \overline{B}^{w_0}\) which can be addressed with the proof \(\varPi _{\textsf{LinCL}}\) (Fig. 3, Sect. 2.3). However, there is the same problem with soundness as in Sect. 3.2, caused by the fact that the adversary could have concocted \(B_i=\textsf{pk}_i^r\cdot f^{p(\alpha _i)}\cdot H_i\) (and now also \(\overline{B}=\overline{R}^{\overline{\textsf{sk}}}\cdot f^{p(\beta )}\cdot H_0\)) so that \(\prod _{i=0}^n H_i^{w_i}\) cancels out. This is solved exactly in the same way as in Sect. 3.2 by randomizing \(w'_i=w_i+c_iq\) and using the rough order assumption.
Theorem 12
In the random oracle model, and assuming \(\texttt {RO}_C\) is hard for \(\textsf{CLGen}\), \(\varPi _{\textsf{Resh}}\) in Fig. 12 is a proof for the relation \(\mathcal {R}_{\textsf{Resh}}\) with soundness error \(\epsilon _{\textsf{LinCL}}+1/C+1/q+\textsf{negl}(\lambda )\), where \(\epsilon _{\textsf{LinCL}}\) is the soundness error of \(\texttt {NIZK}_{\textsf{LinCL}}\). It is zero knowledge assuming \(\texttt {NIZK}_{\textsf{LinCL}}\) is.
Proof
The proof follows analogously to Theorem 7, with the changes above.
5.2 Realizing Efficient YOSO MPC
Building upon our \(\textsf{qCLPVSS}\) PVSS scheme and the associated resharing scheme in Fig. 11, we realize an efficient YOSO MPC protocol by combining the DKG and preprocessing/online phases from [6] with our PVSS. The protocol of [6] first generates a shard key for a linearly homomorphic threshold encryption scheme based on the CL-framework, which is then used to generate encrypted Beaver triples. In an online phase, parties use distributed decryption to obtain the necessary information for evaluating private multiplications using the preprocessed encrypted Beaver triples. However, at every round, the current committee of parties must reshare the secret key towards the next committee. We aim at replacing the resharing scheme of [6] with our scheme from Fig. 11.
At first, we assume we have public keys for the next committee despite it being anonymous, and later argue about how to remove this assumption. Each party in the first committee to obtain shares of the secret key via the DKG of [6] converts them into shares of our \(\textsf{qCLPVSS}\) scheme. This can be done using standard tricks for share conversion or simply by a single execution of an inefficient YOSO MPC that publishes \(\textsf{qCLPVSS}\) shares given shares in a different format. Once a committee has \(\textsf{qCLPVSS}\) shares of the secret key, it can use our resharing scheme from Fig. 11 to efficiently transfer those to the next committee at every round of the MPC protocol of [6].
This simple application of our resharing scheme still requires each committee to know public keys for the next random anonymous committee. While this could be done by means of Random-index RPIR [28] or ideal receiver anonymous communication channels (RACC), we would like to perform the necessary encryption towards the next anonymous committee in a more efficient way. In order to do so, one can use the YOLO YOSO [11] encryption to the future scheme based on mixnets with publicly verifiable proofs of shuffle correctness (and the associated scheme for authententication from the past). These schemes allows for encrypting a message under a public key associated to a randomly chosen party without learning their identity, later allowing the recipient to sign messages by proving that they indeed received the ciphertext. Since the YOLO YOSO construction can be realized from proof of correctness shuffle, it can be implemented in our setting by using a proof system [2] that works over linearly homomorphic encryption schemes, such as those in the CL-framework. Hence, we can obtain a more efficient realization of YOSO MPC based on the protocol of [6] and our PVSS scheme with resharing \(\textsf{qCLPVSS}\) that only uses transparent setup and does not require ideal RACCs.
Notes
- 1.
Up to a constant due to the time for group operations and size for group elements in class groups being higher than those for DDH-hard groups based on elliptic curves.
- 2.
In coding-theoretic this set is the dual code to the Reed-Solomon code formed by the evaluations of polynomials of degree \(\le d\).
- 3.
As well as for using the ZK proof protocol from [6] which we show in next section.
- 4.
The proofs were in fact introduced for slightly more involved relations, but for simplicity we adapt them for just proving knowledge of discrete logarithm.
- 5.
Notation: To avoid confusion with the group \(G^q\) of q-th powers of elements from G, we denote the direct product of m copies of G, for \(m\in \mathbb {N}\), as \((G)^m\).
- 6.
Recall, that by definition of \(\textrm{Lag}_{}\), \(L_i(X)=\prod _{j\in \mathcal {T}'\setminus \{i\}}\frac{X-\alpha _j}{\alpha _i-\alpha _j}\).
- 7.
In practice we consider \(\kappa =40\) is reasonable.
References
Acharya, A., Hazay, C., Kolesnikov, V., Prabhakaran, M.: SCALES - MPC with small clients and larger ephemeral servers. In: Kiltz, E., Vaikuntanathan, V. (eds.) TCC 2022. LNCS, vol. 13748, pp. 502–531. Springer, Heidelberg (2022). https://doi.org/10.1007/978-3-031-22365-5_18
Bayer, S., Groth, J.: Efficient zero-knowledge argument for correctness of a shuffle. In: Pointcheval, D., Johansson, T. (eds.) EUROCRYPT 2012. LNCS, vol. 7237, pp. 263–280. Springer, Heidelberg (2012). https://doi.org/10.1007/978-3-642-29011-4_17
Benhamouda, F., et al.: Can a public blockchain keep a secret? In: Pass, R., Pietrzak, K. (eds.) TCC 2020. LNCS, vol. 12550, pp. 260–290. Springer, Heidelberg (2020). https://doi.org/10.1007/978-3-030-64375-1_10
Boudot, F., Traoré, J.: Efficient publicly verifiable secret sharing schemes with fast or delayed recovery. In: Varadharajan, V., Yi, M. (eds.) ICICS 1999. LNCS, vol. 1726, pp. 87–102. Springer, Heidelberg (1999). https://doi.org/10.1007/978-3-540-47942-0_8
Bouvier, C., Castagnos, G., Imbert, L., Laguillaumie, F.: I want to ride my BICYCL : BICYCL implements cryptography in class groups. J. Cryptol. 36(3), 17 (2023)
Braun, L., Damgård, I., Orlandi, C.: Secure multiparty computation from threshold encryption based on class groups. In: Handschuh, H., Lysyanskaya, A., (eds.) Advances in Cryptology - CRYPTO 2023 - 43rd Annual International Cryptology Conference, CRYPTO 2023, Santa Barbara, CA, USA, August 20-24, 2023, Proceedings, Part I, vol. 14081. LNCS, pp. 613–645. Springer, Cham (2023). https://doi.org/10.1007/978-3-031-38557-5_20
Campanelli, M., David, B., Khoshakhlagh, H., Konring, A., Nielsen, J.B.: Encryption to the future - a paradigm for sending secret messages to future (anonymous) committees. In: Agrawal, S., Lin, D. (eds.) ASIACRYPT 2022. LNCS, vol. 13793, pp. 151–180. Springer, Heidelberg (2022). https://doi.org/10.1007/978-3-031-22969-5_6
Cascudo, I., David, B.: SCRAPE: scalable randomness attested by public entities. In: Gollmann, D., Miyaji, A., Kikuchi, H. (eds.) ACNS 17. LNCS, vol. 10355, pp. 537–556. Springer, Heidelberg (2017). https://doi.org/10.1007/978-3-319-61204-1_27
Cascudo, I., David, B.: ALBATROSS: publicly attestable batched randomness based on secret sharing. In: Moriai, S., Wang, H. (eds.) ASIACRYPT 2020. LNCS, vol. 12493, pp. 311–341. Springer, Heidelberg (2020). https://doi.org/10.1007/978-3-030-64840-4_11
Cascudo, I., David, B.: Publicly verifiable secret sharing over class groups and applications to DKG and YOSO. Cryptology ePrint Archive, Paper 2023/1651 (2023). https://eprint.iacr.org/2023/1651
Cascudo, I., David, B., Garms, L., Konring, A.: YOLO YOSO: fast and simple encryption and secret sharing in the YOSO model. In: Agrawal, S., Lin, D. (eds.) ASIACRYPT 2022. LNCS, vol. 13791, pp. 651–680. Springer, Heidelberg (2022)
Cascudo, I., David, B., Shlomovits, O., Varlakov, D.: Mt. random: multi-tiered randomness beacons. In: Tibouchi, M., Wang, X., (eds.) Applied Cryptography and Network Security - 21st International Conference, ACNS 2023, Kyoto, Japan, June 19-22, 2023, Proceedings, Part II, vol. 13906, LNCS, pages 645–674. Springer, Cham (2023.) https://doi.org/10.1007/978-3-031-33491-7_24
Castagnos, G., Catalano, D., Laguillaumie, F., Savasta, F., Tucker, I.: Two-party ECDSA from hash proof systems and efficient instantiations. In: Boldyreva, A., Micciancio, D. (eds.) CRYPTO 2019. LNCS, vol. 11694, pp. 191–221. Springer, Heidelberg (2019). https://doi.org/10.1007/978-3-030-26954-8_7
Castagnos, G., Catalano, D., Laguillaumie, F., Savasta, F., Tucker, I.: Bandwidth-efficient threshold EC-DSA. In: Kiayias, A., Kohlweiss, M., Wallden, P., Zikas, V. (eds.) PKC 2020. LNCS, vol. 12111, pp. 266–296. Springer, Heidelberg (2020). https://doi.org/10.1007/978-3-030-45388-6_10
Castagnos, G., Imbert, L., Laguillaumie, F.: Encryption switching protocols revisited: Switching modulo \(p\). In: Katz, J., Shacham, H. (eds.) CRYPTO 2017. LNCS, vol. 10401, pp. 255–287. Springer, Heidelberg (2017). https://doi.org/10.1007/978-3-319-63688-7_9
Castagnos, G., Laguillaumie, F.: Linearly homomorphic encryption from DDH. In: Nyberg, K., (ed.) Topics in Cryptology - CT-RSA 2015, The Cryptographer’s Track at the RSA Conference 2015, San Francisco, CA, USA, April 20-24, 2015. Proceedings, vol. 9048, LNCS, pp. 487–505. Springer, Cham (2015). https://doi.org/10.1007/978-3-319-16715-2_26
Castagnos, G., Laguillaumie, F., Tucker, I.: Practical fully secure unrestricted inner product functional encryption modulo \(p\). In: Peyrin, T., Galbraith, S. (eds.) ASIACRYPT 2018. LNCS, vol. 11273, pp. 733–764. Springer, Heidelberg (2018). https://doi.org/10.1007/978-3-030-03329-3_25
Choudhuri, A.R., Goel, A., Green, M., Jain, A., Kaptchuk, G.: Fluid MPC: secure multiparty computation with dynamic participants. In: Malkin, T., Peikert, C. (eds.) CRYPTO 2021. LNCS, vol. 12826, pp. 94–123. Springer, Cham (2021). https://doi.org/10.1007/978-3-030-84245-1_4
Cramer, R., Damgård, I., Nielsen, J.B.: Multiparty computation from threshold homomorphic encryption. In: Pfitzmann, B. (ed.) EUROCRYPT 2001. LNCS, vol. 2045, pp. 280–299. Springer, Heidelberg (2001)
David, B., et al.: Perfect MPC over layered graphs. In: Handschuh, H., Lysyanskaya, A., (eds.), Advances in Cryptology - CRYPTO 2023 - 43rd Annual International Cryptology Conference, CRYPTO 2023, Santa Barbara, CA, USA, August 20-24, 2023, Proceedings, Part I, vol. 14081, LNCS, pp. 360–392. Springer, Cham (2023). https://doi.org/10.1007/978-3-031-38557-5_12
Dobson, S., Galbraith, S.D., Smith, B.: Trustless unknown-order groups. Math. Cryptol. 1(2), 25–39 (2022)
Faust, S., Kohlweiss, M., Marson, G.A., Venturi, D.: On the non-malleability of the Fiat-Shamir transform. In: Galbraith, S.D., Nandi, M. (eds.) INDOCRYPT 2012. LNCS, vol. 7668, pp. 60–79. Springer, Heidelberg (2012). https://doi.org/10.1007/978-3-642-34931-7_5
Fouque, P.-A., Stern, J.: One round threshold discrete-log key generation without private channels. In: Kim, K. (ed.) PKC 2001. LNCS, vol. 1992, pp. 300–316. Springer, Heidelberg (2001). https://doi.org/10.1007/3-540-44586-2_22
Fujisaki, E., Okamoto, T.: A practical and provably secure scheme for publicly verifiable secret sharing and its applications. In: Nyberg, K. (ed.), EUROCRYPT 1998, vol. 1403, LNCS, pp. 32–46. Springer, Heidelberg (1998). https://doi.org/10.1007/BFb0054115
Gennaro, R., Jarecki, S., Krawczyk, H., Rabin, T.: Secure distributed key generation for discrete-log based cryptosystems. In: Stern, J. (ed.) EUROCRYPT 1999. LNCS, vol. 1592, pp. 295–310. Springer, Heidelberg (1999)
Gentry, C., et al.: YOSO: you only speak once - secure MPC with stateless ephemeral roles. In: Malkin, T., Peikert, C., (eds.) CRYPTO 2021, Part II, vol. 12826, LNCS, pp. 64–93. Springer, Heidelberg (2021)
Gentry, C., Halevi, S., Lyubashevsky, V.: Practical non-interactive publicly verifiable secret sharing with thousands of parties. In: Dunkelman, O., Dziembowski, S. (eds.) EUROCRYPT 2022, Part I, vol. 13275, LNCS, pp. 458–487. Springer, Heidelberg (2022). https://doi.org/10.1007/978-3-031-06944-4_16
Gentry, C., Halevi, S., Magri, B., Nielsen, J.B., Yakoubov, S.: Random-index PIR and applications. In: Nissim, K., Waters, B. (eds.) TCC 2021. LNCS, vol. 13044, pp. 32–61. Springer, Heidelberg (2021). https://doi.org/10.1007/978-3-030-90456-2_2
Groth, J.: Non-interactive distributed key generation and key resharing. Cryptology ePrint Archive, Paper 2021/339 (2021). https://eprint.iacr.org/2021/339
Gurkan, K., Jovanovic, P., Maller, M., Meiklejohn, S., Stern, G., Tomescu, A.: Aggregatable distributed key generation. In: Canteaut, A., Standaert, F.-X. (eds.) EUROCRYPT 2021. LNCS, vol. 12696, pp. 147–176. Springer, Heidelberg (2021). https://doi.org/10.1007/978-3-030-77870-5_6
Heidarvand, S., Villar, J.L.: Public verifiability from pairings in secret sharing schemes. In: Avanzi, R.M., Keliher, L., Sica, F., (eds.) SAC 2008, vol. 5381, LNCS, pp. 294–308. Springer, Heidelberg (2009). https://doi.org/10.1007/978-3-642-04159-4_19
Kate, A., Mangipudi, E.V., Mukherjee, P., Saleem, H., Aravinda, S., Thyagarajan, K.: Non-interactive VSS using class groups and application to DKG. Cryptology ePrint Archive, Paper 2023/451 (2023). https://eprint.iacr.org/2023/451
Katz, J.: Round optimal robust distributed key generation. Cryptology ePrint Archive, Paper 2023/1094 (2023). https://eprint.iacr.org/2023/1094
Pedersen, P.T.: A threshold cryptosystem without a trusted party (extended abstract) (rump session). In: Davies, D.W. (ed.) EUROCRYPT 1991. LNCS, vol. 547, pp. 522–526. Springer, Heidelberg (1991). https://doi.org/10.1007/3-540-46416-6_47
Rachuri, R., Scholl, P.: Le Mans: dynamic and fluid MPC for dishonest majority. In: Dodis, Y., Shrimpton, T. (eds.) CRYPTO 2022. LNCS, vol. 13507, pp. 719–749. Springer, Heidelberg (2022). https://doi.org/10.1007/978-3-031-15802-5_25
Ruiz, A., Villar, J.L.: Publicly verifiable secret sharing from Paillier’s cryptosystem. In: WEWoRC 2005–Western European Workshop on Research in Cryptology (2005)
Schoenmakers, B.: A simple publicly verifiable secret sharing scheme and its application to electronic. In: Wiener, M.J. (ed.) CRYPTO 1999. LNCS, vol. 1666, pp. 148–164. Springer, Heidelberg (1999). https://doi.org/10.1007/3-540-48405-1_10
Stadler, M.: Publicly verifiable secret sharing. In: Maurer, U.M. (ed.) EUROCRYPT 1996. LNCS, vol. 1070, pp. 190–199. Springer, Heidelberg (1996). https://doi.org/10.1007/3-540-68339-9_17
Tucker, I.: Functional encryption and distributed signatures based on projective hash functions, the benefit of class groups. (Chiffrement fonctionnel et signatures distribuées fondés sur des fonctions de hachage à projection, l’apport des groupes de classe). Ph.D. thesis, University of Lyon, France (2020)
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2024 International Association for Cryptologic Research
About this paper
Cite this paper
Cascudo, I., David, B. (2024). Publicly Verifiable Secret Sharing Over Class Groups and Applications to DKG and YOSO. In: Joye, M., Leander, G. (eds) Advances in Cryptology – EUROCRYPT 2024. EUROCRYPT 2024. Lecture Notes in Computer Science, vol 14655. Springer, Cham. https://doi.org/10.1007/978-3-031-58740-5_8
Download citation
DOI: https://doi.org/10.1007/978-3-031-58740-5_8
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-031-58739-9
Online ISBN: 978-3-031-58740-5
eBook Packages: Computer ScienceComputer Science (R0)