1. Introduction
Wireless sensor networks (WSN) are widely used and explored in computer environments everywhere. Advances in electronics and wireless technology have led to the development of low-cost miniature sensors.1 The smaller sensors control the integrated power because they are powered by unique batteries that are easy to replace. As a result of these restrictions, much has been done to control the sensors’ power consumption, increase their service life, and extend network life.2 WSN aims to manage the environment, health services and military care. WSNs have multiple detection locations with CPU memory, but are only a short distance away. In native applications, sensors send important information to general and focal weather areas. Take each other on an Emerging Community Tour and submit verified information to Central Point Station Synchronization. The integration plan3,4 is a way of bridging the gap between the social origins and purposes of controlled sensitive information. The implementation of WSN mainly depends on control programs that directly control the timing of the network operation. The main purpose of the routing algorithm is to increase the reliability and timeliness of the WSN by using sensor terminals with limited resources such as limited power, slow processor, and connection bandwidth.5 Cluster routing6,7 is a great way to reduce the power consumption of a cluster. Therefore, some research has been done on cluster-based routing algorithms. The popular clustering protocol, called LEACH8 which provides two-phase operations based on a single-layer network using clusters. The reach node subgroup is selected as the cluster node, and the cluster node connects the adjacent nodes to the panel. However, this has some limitations.
Remote Cluster die faster than nearby ones as the cluster head (CH) uses more power than the nearest base station (BS). LEACH affects load balance and shorten network life due to its own limitations9 and due to data transfer depends on the importance of information. Recently, hierarchical routing protocols have been widely used in WSN power systems10,11 who divide the network into groups, with each containing a CH, which is an intermediate between the nodes of the cluster, also known as the BS nodes. CH has a high energy level in the cluster which collects data and integrates it with BS to reduce overall network power consumption.12
To date, energy-efficient routing protocols have been developed. Different routing algorithms use different methods to make the network run efficiently and reliably. A two-tier distributed fuzzy logic based protocol (TTDFP)13 is used to extend the life of a multi-level WSN through grouping and routing functions. Use the traffic and energy aware routing (TEAR)14 program to improve the environmental energy model and stability period. The step-by-step clustering hierarchical routing algorithm is based on the K-Means method (K-CHRA),15 which measures the power and data transfer during the operation of mobile devices.
The enhanced balanced energy efficient network-integrated super-heterogeneous (E-BEENISH)16 integrates routing protocols that analyze cluster contacts and the power consumption of different WSNs. FLEC17 solves a clustering algorithm based on obscure logic by extending the network runtime,18 allowing the CH to be selected correctly. The clustering algorithm uses the advanced artificial bee colony (ABC) algorithm,19 which improves energy efficiency and network performance. Three energy saving two-phase panel protocols have been proposed namely a shortest grid routing (SGR), partitioned super grid direct routing (PSDR), and shortest super grid routing (SSR)20 for individual wind turbines.20
Our contributions. For further enhancement in routing protocol, we propose an energy efficient cluster based routing protocol for WSN using hybrid optimization algorithm (EEC-HO). Herein, the proposed EEC-HO routing protocol aims to prolong network lifetime and enhance the throughput of this protocol with recent trended applications. The rest of the work is configured as follows: In Part 2, we review current energy efficient routing protocols for WSNs. The fault mode and network model are discussed in this section. 3. In Section 4, we discuss the operation of the proposed EEC-HO routing protocol. Simulation results of specific and existing routing protocols are discussed in the comparative analysis section. 5. Finally, the paper ends with a conclusion in section 6.
2. Related works
Over the past few years, much research has been done on WSN’s energy-efficient routing protocols using optimization techniques from around the world. The literature is summarized in various aspects and summarized in Table 1.
The selected path is compute using different metrics and using ant colony optimization (ACO), which selects the optimal path using optimal design metrics.21 Gateway grouping is a routing protocol based on the clustering energy-efficient center (GCEEC),22 which selects the location of the CH centroid and selects the gateway nodes from each cluster. The gateway terminal reduces the load of data from the CH terminals and sends it to the database station. This protocol rotates CH selectively in an efficient location, i.e., near the power center level of the cluster, reducing the power consumption of the cluster sensor nodes and increasing CH coverage.
Ensure efficient operation by providing QoS-based energy efficiency protocol (QoS-EE),23 due to energy consumption and delays. Protocol systems balance network life, reduce network power consumption, duplication, and increase the validity and integrity of information. The trust-based and energy-efficient hierarchical routing protocol (LEACH-TM) is proposed based on trust management.24 With LEACH-TM, the number of nodes in CH can be used to better manage energy efficiency and to avoid excessive node power consumption. At the same time, LEACH -TM introduced a trust management program to protect against internal attacks. The step-by-step selection of energy storage CH is carried out using the hybrid CI-ROA25 optimization model. In addition, Selecting the optimal CH prolongs the life of the non-linear target function. CH to load data packets on the target to improving an FLC can increase its rule base and improve the efficiency of the grouping process.26 The WSN proposed an operating system based on a genetic algorithm (GA).27 Divide the network area into optimal number groups, which creates a path for synchronous activity. The GA process determines the optimal shell locations along the path of each cluster. Mobile sync configures optimal sync locations, collects data from the respective groups of nodes, uses low node power to transmit optimal synchronization location data. The number of GA chromosomes begins to determine the optimal position for cluster deposition.
The WSN recommends hybrids metahoristic cluster-based routing technique (HMBCR).28 For the optimal route, the water wave with trekking is ideal. The Trust estimation based routing scheme (ETERS)29 includes powerful ways to reduce internal attacks such as abuse, CIBIL, selective fragmentation, enforcement, black/gray hole attacks. Sensitivity several belief methods are used to analyze the reliability of the observed data. The function of CH selection utilizes the optimal design metrics with the help of cluster member data. The routing model is based on energy security and reliability, sending data packets to the recipient via the ant-lion high-speed whale optimization algorithm (E-ALWO).30 This E-ALWO model performs the routing process via CH, so the control-based ALWO algorithm is used to select power and delay CH. The best security system used in the data transfer process is based on compatibility measurements using the E-ALWO algorithm.
3. Problem methodology and Network model
3.1. Problem methodology
Yun et al.31 have proposed a Q-learning-based data-aggregation-aware energy-efficient routing (Q-DAEER) algorithm. Q-DAEER upgrade learning is used to maximize the reward defined by sensor type data acquisition capability, communication power, and sending/receiving residual power of each sensor. Reward functions define changes in the data integration dynamics of each node’s energy node, neighbors, and types. Simulations were performed to validate state-of-art Q-DAEER protocol with the different performance metrics. Recovering damaged touchpad batteries is not an easy task. As the sensor modules cannot perform in low power the network failure of the sensor terminal affects network performance and shortens network uptime. Energy-based cluster head selection overloads each CH, that causes CH to break down quickly. This increases the power consumption of the terminals, leading to communication gaps and delays in data transfer. Node distance from BS and residual power are important factors in selecting a node transfer node in the contact range. As a result, public Internet access points are created on the network when the relay cluster head fails during data transfer. When developing routing protocols for the WSN, it is important to consider energy saving technologies which increases network uptime, number of operating nodes in the region and create higher pocket-sized distribution rates to control optimal data transfer. The main contributions of proposed energy efficient cluster based routing protocol (EEC-HO) is summarized as follows:
-
An improved Aquila optimization with fuzzy (IAO-Fuzzy) model is introduced for optimal and efficient cluster formation and cluster head (CH) computation.
-
After that, the hybrid beetle search induced decision making (BSDM) algorithm for optimal next neighbor selection to transfer data transfer between two nodes.
3.2. Network Structure of proposed model
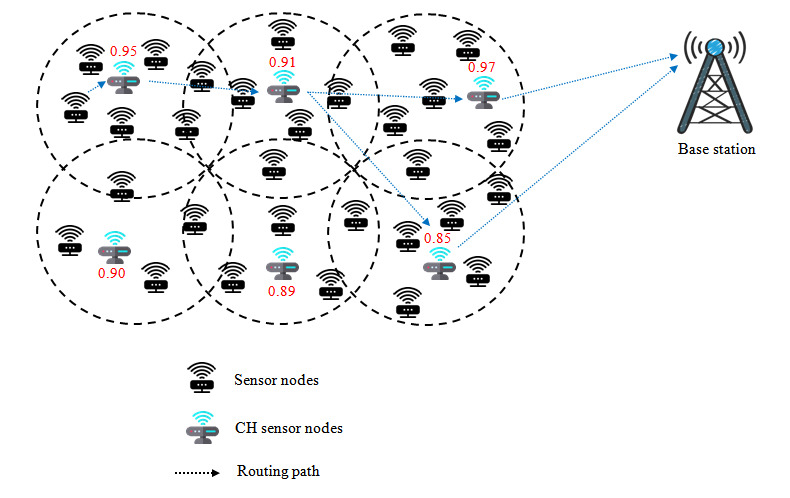
In this proposed model, the different sensors have randomly placed in the network with the emit radiation at approximately square intervals to continuously monitor, as shown in Figure 1. The sensor nodes handle both sensing and receiving data from local network environment. Groups network models and CH selection using a reliable computational model. The path calculation is then computed using a hybrid optimization algorithm.
4. Proposed Methodology
In this section, we first discuss the working process of clustering which consist of cluster formation and CH selection. Then, we explain the process of trust computation which is used to compute optimal path.
4.1. Clustering using improved Aquila optimization with fuzzy (IAO-Fuzzy) model
4.1.1. Cluster formation
Aquila Optimizer (AO) is the latest mass intelligence algorithm that reflects Aquila’s hunting techniques for different victims. Faster hunting methods reflect the overall research capabilities of the algorithms, while slower ones utilize the capabilities of the local algorithm. Based on this inspiration, we have developed the improved Aquila optimization (IAO) algorithm used to build teams in this task. The following design parameters are used to create the cluster: location, distance between node-BS, and signal strength received. First, the IAO algorithm starts by defining the initial value of the set of n individuals as follows:
yIJ=R1×(ubJ−lbJ)+lbJ,I=1,2,……,nJ=1,2,……,dim
where is a random value consisting of ∈ [0, 1]. and Mark the bottom and top edges of the J scale, respectively. Like other transformational technologies, AO has two stages to innovate existing individuals, namely research and exploitation. When the training phase begins there are two modes
x1(T+1)=xbest(T)×(1−TT)+(xm(T)−xbest(T)∗rand)
where T is the total number of iterations. is best recurrence ever obtained in T is the current iteration the element used to control the search during the research phase. In addition, it is one of the individual averages and is calculated as:
xm(T)=1nn∑I=1x(T),∀J=1,2,…,dim
IAO algorithm depends on the use of the Levy flight distribution to renew the existing person according to the following relation.
x2(T+1)=xbest(T)×levy(d)+xr(T)+(Y−X)∗rand
where denotes a random chosen separate. refers to the Levy flight delivery defined as:
levy(d)=S×U×σ|V|1/β,σ=(Γ(1+β)sine(πβ2)Γ(1+β2)×β×2(β−12))
where and are continuous values, and refer to random numbers produced from In Equation (10), and are used to pretend the spiral outline as,
Y=R×cos(θ),X=R×sin(θ)
R=R1+u×D1,θ=−ω×d1+θ1,θ1=3×π2
where r1 ∈ [0, 20] is a random value. Smaller values indicate and It depends on the best solution used and the average individual location which is:
x3(T+1)=(xbest(T)×xm(T))×α−rand+((ub−lb)×rand+lb)×δ
where rand ∈ [0, 1] denotes random number. α and δ denote the mistreatment alteration parameters. The second exploitation technique depends on and excellence function.
x4(T+1)=qf×xbest(T)−(g1×x(T)×rand−g2×levy(d)+rand×g1
where the chief aim of using qf is to equilibrium the search approaches, and it is defined as:
qf(T)=T2×rand()−1(1−t)2
where represents dissimilar motions applied to track the best solution as follows:
g1=2×rand()−1
where is reduced from 2 to 0, and it is expressed as,
g2=2×(1−Tt)
where rand characterizes a random charge. The working process of cluster formation is described in Algorithm 1.
4.1.2. CH selection
We need the decision making technique for cluster head (CH) selection which need following design metrics are energy consumption, data transfer rate, average quality of data transfer rate and congestion rate. Here, we introduce fuzzy model for CH selection. If we take the N decision criterion (DC) for the decision problem, we need to make a pairing comparison and then, make such a comparison based on the preferences of the decision maker in simple language. Fuzzy model use linguistic terminology to compare ambiguous references to good and bad criteria. The design comparison matrix can be created as a result of comparison as follows.
˜a=(DA1DA2⋮DAM)[˜A11˜A12⋯˜A1N˜A21˜A22⋱˜A2N⋮⋮⋮˜AM1˜AM1⋯˜AMN] (DC1DC2⋯DCN)
where is substitute set and is decision matrix with the fixed network area, depicts fuzzy comparative metrics over J. Furthermore, the better criteria are the worse criteria for ambiguous reference comparisons. The Fuzzy model consists following six stages are,
1. Initialize decision criteria set
This position is governed by the Decision criteria (DC). Suppose there is an “N” final criterion, i.e.,
2. Compute Best/Worst DC
This position does not require comparison. The decision maker usually sets the best and worst criteria.
3. Use linguistic terminology to better define the ambiguous choice of criteria above all other criteria.
The criteria best defined by the decision maker are compared to all other criteria using the linguist’s terminology. The resulting optimal vector is assumed as follows,
˜ab=(˜Ab1,˜Ab2,˜Ab3,…..,˜Abn)
where defines optimal vector where points the ambiguous priority of criterion B for the criterion of best result over all other criteria is J.
4. Use linguistic terminology to determine the vague advantage over the worst of all other criteria.
It is necessary to set ambiguous preferences for all other criteria using the worst language terms mentioned at this stage. This way we get the autumn slow optimal vector.
˜aW=(˜AW1,˜AW2,˜AW3,…,˜AWn)
where defines optimal vector which points to J should give vague priority to criteria other than the worst criteria.
5. Define optimal and
The form of TFNs, indicate vague preferences for better standards for others, e.g. denoting uncertainty and options for worst solution from others in the form of TFNs, e.g. So, we use the equation with the fourth definition. Then, we get a distinctly good vector and a sharp other-bad vector as follows.
cbTo=cb=(Cb1,Cb2,Cb3,……,CbN)
coTw=cW=(CW1,CW2,CW3,……,CWN)
6. Calculate the optimal weights
The optimal best and worst solution is further filtered using different weight function which can derive from the supreme absolute difference and for all J is minimized. The nonlinearly unnatural optimization problematic can be expressed as follows.
MinMax{|WbWJ−CbJ|,|WJWw−CJW|}
where define control variable using Then, above equation is altered by the subsequent non-linear programming problem.
S.T.{|WbWJ−CbJ|≤ξ,forall J|WbWJ−CbJ|≤ξ,forall J∑JWJ=1,WJ≥0,forall J
Finally, the proposed Fuzzy model is used to compute the optimal weight and the heighted optimal weight is considered as CH of each cluster in the network.
4.2. Optimal path selection using hybrid beetle search induced decision making algorithm
For selecting best essential attributes for best optimal path selection, we introduce hybrid beetle search induced decision making (BSDM) algorithm in this paper. Beetle antennae search (BAS) algorithm is naturally understand the process of optimization without knowing the particular type of the function and gradient information. Inspired by the floating optimization algorithm, BSDM further improved the algorithm by forming an individual into a group. Address: Each beetle will be displayed graphically from one G to another or from the BS. Set the Gk Gateway to the BS gateway closest to Gd, indicating that Gd is sending data to Gk. The routing path is drawn in an equation,
Gk=I(SetNextg(Gk),m)
where is an indexing function which returns index of mth gateway from and The fitness of routing is evaluated as follows:
FitRouting=Max(C1DTotal∗W1+GHop∗W2)
Here, and are proportional constants. is defined as the total length that passes through the gates,
DTotal=n∑i=1D(Gi,Nextg(Gi))
Additionally, is defined as the total number of gate hops in the network,
GHop=n∑i=1NextgCount(Gi)
Update Solution: This shows the speed at which the beetle eats This shows the individual effects of beetles and thus shows the extreme value of the population. The mathematical model for imitating his behavior is as follows;
Pk+1is=Pkis+ρQkis+(1−ρ)εkis
when represents the number of current changes, indicates the velocity of the beetle, denotes the positive constant, and indicates the increase in the beetle’s level motion. Here, the speed formula is mathematically explained as follows;
Qk+1is=ωQkis+c1r1(Xkis−Pkis)+c2r2(Xkgs−Pkgs)
where, and represent two optimistic constants, and represents optimal weight with the range of and the inertial optimal weight of In this work, we follow the strategy of reducing the weight of the recession, which is mathematically illustrated as follows;
ω=ωmax−ωmax−ωminK∗k
where, and denote the minimum as well as maximum value of and denotes the present number of iterations as well as the maximum number of iterations. Here, the decision function is mathematically defined as the incremental function expressed in the following way;
εk+1is=δk∗Qkis∗sign(f(Pkrs)−f(Pkls))
At this point, we extend the update resolution to a higher level. Here, degrees indicate size. The search behavior of the right antenna and the left antenna is expressed as follows:
Pk+1rs=Pkrs+Qkis∗d/2
Pk+1ls=Pkrs−Qkis∗d/2
Here, the BSDM algorithm first starts a series of random solutions. The search region is updating its site based on its own search engine, which is currently the best solution. The combination of these two factors can not only accelerate the continuum of population growth, but also subject people to more sustainable local optimization when dealing with multiple issues. The solution will be updated until a better solution or routing path is found. Once the optimal solution is reached, the algorithm will shut down.
5. Results and Performance analysis
The effectiveness of the EEC-HO routing protocol has been evaluated using two different simulation scenarios. The result of the proposed EEC-HO routing protocol is compared with existing SPR, SPRwDA and Q-DAEER routing methods. The simulation results of proposed EEC-HO routing protocol is compared with those existing state-of-art protocols different quality metrics.
5.1. Simulation Setup and Scenario
A specific EEC-HO routing protocol runs on the Intel Core i3 processor, installed and tested on a network simulator (NS-2) with 4GB of RAM. We estimate the number of detection nodes as 100, 200, 300, 400 and 500. The 200m × 200m sensitivity zone has approximately multiple sensor nodes. The initial energy levels of the nodes are evenly distributed [2J, 2,5J]. The maximum transmission range of the terminals is estimated at 150 remote units (two). The average remaining WSN power for WSN nodes is 1 J power. Table 2 describes the prototype structure of the proposed system.
-
Scenario 1: In this test, we convert the number of sinus nodes from 100 to 500 using the standard network size used to analyze the quality of the data transmission.
-
Scenario 2: In this experiment, the number of rounds simulated in the standard detection terminal used to analyze the performance of the EEC-HO routing protocol was changed from 1000 to 5000.
5.2. Comparative analysis
5.2.1. Scenario 1: Impact of node density
In this scenario, we vary the number of senor nodes as 100, 200, 300, 400 and 500 with the fixed network size as 200m×200m which used to analyze the quality of data transfer. The results of proposed EEC-HO routing protocol is compared with the existing state-of-art protocols are energy consumption, network lifetime, average hop count, throughput and number of dead nodes.
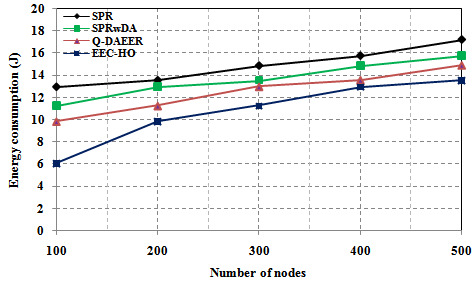
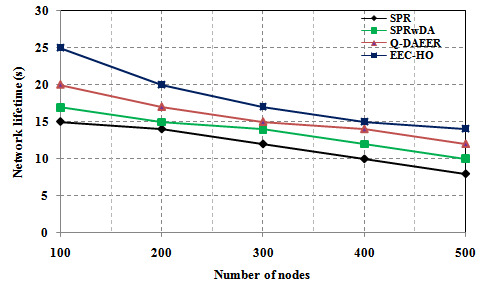
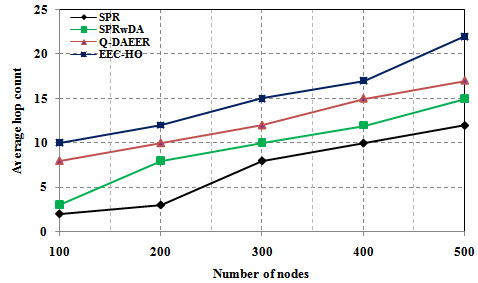
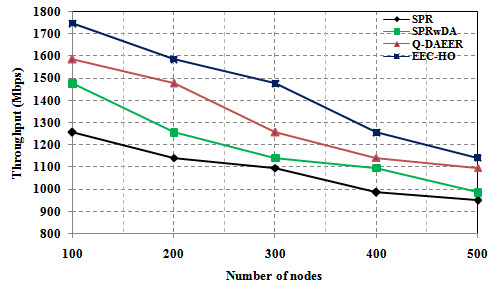
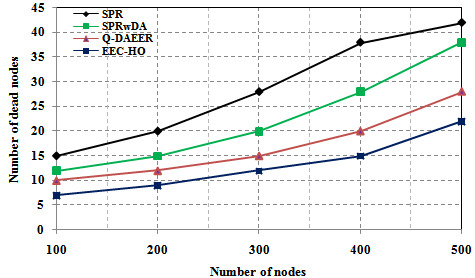
Figure 2 shows a power consumption comparison between the proposed routing protocols and the current protocols. The graph clearly shows that the power consumption of the specified EEC-HO routing protocols is 53.174%, 46.069% and 38.419%, respectively, compared with the SPR, SPRwDA and Q-routing routing protocols. Tire. Figure 3 shows a network lifecycle comparison between specific routing protocols and current protocols. The graph clearly shows that the network life of the proposed EEC-HO routing is 40,000%, 32,000% and 20,000% longer than the related SPR, SPRwDA and Q-DAEER routing protocols. Figure 4 shows the average number of hops and a comparison between the specified routing protocol and the current protocol. The graph clearly shows that the average number of hops for the EEC-HO specific routing is 80,000%, 70,000% and 20,000% higher than the corresponding SPR, SPRwDA and Q-DAEER routing protocols. Figure 5 shows a performance comparison between the proposed routing protocols and the current ones. The graph clearly shows that the routing efficiency recommended by EEC-HO is 28.130%, 15.495% and 9.262% higher than the corresponding SPR, SPRwDA and Q-DAEER routing protocols. Figure 6 shows a comparison of the number of dead nodes between the proposed and existing routing protocols. The graph clearly shows that the number of dead routes of EEC-HO compared with routing protocols SPR, SPRwDA and Q-DAEER is 53.333%, 41.667% and 30,000% respectively.
5.2.2. Scenario 2: Impact of Simulation rounds
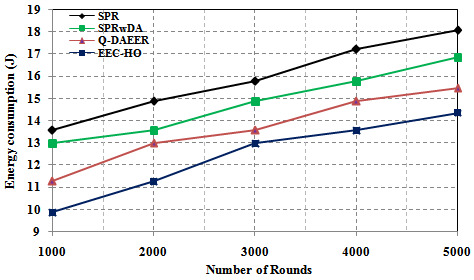
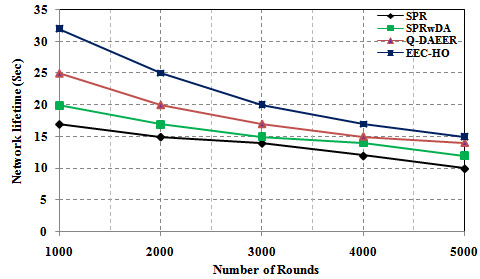
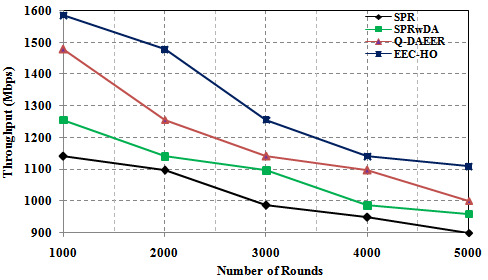
In this case, the number of simulation circuits used to analyze the performance of the EEC-HO routing protocol will be changed to 1000, 2000, 3000, 4000, 5000 and the standard detection terminal to 500. The results of the proposed EEC-HO routing protocol are compared with existing complex protocols such as power consumption, network life, average hop count, performance, and dead node count. Figure 7 shows a comparison of power consumption between proposed and existing routing protocols. The graph clearly shows that the power consumption of the proposed EEC-HO routing protocols is 27.266%, 23.960% and 12.422% lower, respectively, than the SPR, SPRwDA and Q-router protocols. DAEER. Figure 8 shows a network lifecycle comparison between the proposed routing protocols and the current ones. The graph clearly shows that the network life of the proposed EEC-HO routing is 46.875%, 37.50% and 21.875% longer than the corresponding SPR, SPRwDA and Q-DAEER routing protocols.
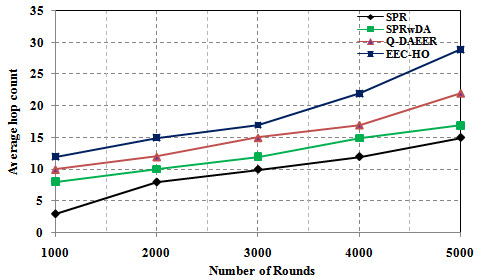
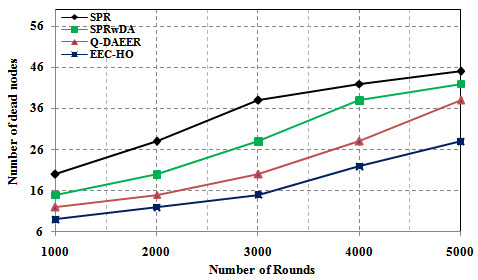
Figure 9 shows the average number of hops and compares the proposed and existing routing algorithms. The graph clearly shows that the average number of hops for the EEC-HO specific routing is 75,000%, 33.333% and 16.667% higher than the related SPR, SPRwDA and Q-DAEER routing protocols. Figure 10 shows a performance comparison between the proposed routing protocols and the current ones. The graph clearly shows that the recommended routing efficiency of EEC-HO is 28.040%, 20.794% and 6.868%, respectively, compared to the routing protocols SPR, SPRwDA and Q-DAEER. Figure 11 shows a comparison of the number of dead nodes between the proposed and existing routing protocols. The graph clearly shows 55,000%, 40,000%, and 25,000% EEC-HO original dead notes compared to SPR, SPRwDA and Q-DAEER routing protocols.
6. Conclusion
We have proposed an energy efficient cluster based routing protocol (EEC-HO) for WSNs using hybrid optimization algorithm. The major contributions of proposed EEC-HO routing protocol is summarized as follows:
-
An improved Aquila optimization with fuzzy (IAO-Fuzzy) model is proposed for optimal and efficient cluster formation and cluster head (CH) computation.
-
The hybrid beetle search induced decision making algorithm is used for optimal next neighbor selection to transfer data transfer between two nodes.
Finally, we observed that the effectiveness of proposed EEC-HO routing protocol is very effective in terms of energy consumption, network lifetime, average hop count, throughput and number of dead nodes with respect to impact node density and number of simulation scenario respectively.