CCNA Notes
CCNA Notes
Uploaded by
Allay DesaiCopyright:
Available Formats
CCNA Notes
CCNA Notes
Uploaded by
Allay DesaiOriginal Description:
Original Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Copyright:
Available Formats
CCNA Notes
CCNA Notes
Uploaded by
Allay DesaiCopyright:
Available Formats
DAY1
CHAPTER 1
Pg 16 OSI Model
Session layer: Provides dialog control. Keeps all the info separate.
Upper layers (software) Application, Presentation and Session
Layer 4 Transport layer: End to end communication. Host to Host. Connection oriented communication
Pg 19 Connection oriented programing (The features below dont need to be known in depth)
- Flow Control: Send data as fast as possible
- Windowing: Controls how much info need to flow
- Acknowledgment: Guarantees that data sent is received.
3 way hand shake required for connection oriented programing. SYN, SYN/ACK, ACK.
Pg 23 Network Layer or Layer 3. Routers, firewall and IP routing
Layer 2
NOTE: Bridge and Switch is the same and both use MAC address. Will be used interchangeably in exam.
Layer 1 Contains dum devices with communication in binary (electrical pulse).
Network card: layer 1 and Layer 2
Wireless access point: Layer 1 and Layer 2
Ethernet Network in Review
Collision domain: A network where only 1 host gets to transmit at a time.
Eg: In a Hub there is collision domain. Communication using broadcast message.
EXAM: Find no of collision domains and Broadcast domains
Pg 44 : Broadcast domain
NOTE: Switch creates 1 broadcast domain by default and 1 collision domain for every port
Every port on switch has collision domain.
NOTE: Routers create an internetwork and an internetwork connects broadcast domains.
So every port on the router has a broadcast domain
CSMA/CD: Handles collisions for us. Hubs (layer 1) use them the most! Switches wont need it.
CSMA/CD doesnt know who is talking so it assigns time to every host. Sends Jam signal and assigns
random time to every host to transmit.
Pg 47
Half duplex: 1 way communication. Can only send or receive at a time.
Full Duplex: 2 way communication. Can receive and transmit at a time.
If a half-duplex device connects to Full duplex then it will work in half duplex thus inconsistent network
You need to configure either full or half duplex. Auto is not acceptable.
Pg 49:
Mac Address <-> Ethernet address
How mac address is formed?
48 bits, vendor assigns only 24 bits
Binary to decimal
Bit 0 or 1
Byte 8 bits (IPV4 Address)
Nibble 4 bits (IPV6, MAC address)
128 64 32 16 8 4 2 1
1 1 0 0 0 0 1 1 -> 195
Pg 52: Table of hexa, Decimal and binary
Pg 54: Ethernet frame
PDU for layer 2 is a frame. Datalink layer does framing.
Every frame has a source and destination MAC Address. Every frame has a FCS (Frame check), tells if the
host received everything.
NOTE: Switches learn from source MAC address for routing table.
Pg 56: Learn the cable names. Twisted pair, co axial and
[Speed Base Type]
10 Base T- 10 mbps (Left) and Twisted pair (Right). T with anything still means twisted pair.
100 Base FX- Fiber (right) so if no T then fiber cable
Coax Number to the right of base then it is coax
1000Base-CX = Copper twisted-pair (Exception to above rules)
Pg 59:
Ethernet Cabline
Straight through cable used to connect unlike device (hub to router, computer to router)
Device that has an ip address to device that doesnt have an ip address. Eg Switch and hub not possible
both dont have an IP
Crossover cable: When both the devices have or lack an IP. Eg Hub to hub, Hub to switch
Pg 62:
Rolled Cable: It is used to console to a router or switch
RJ 45 and Serial (DB9, RS232)
PG 67: Data Encapsulation
LAYER PDU ADDRESS
Upper layer - software
Transport Segment - port no
Network Packet IP Address
Data Link Frame MAC Address
Physical Bits - None
Pg 68: Fig PDU and layer addressing
Note: De-encapsulation : its the reverse process. Read Carefully!!
Pg 71: CISCO Hierarchical Model
Core : Layer 3 switches and Backbone
Distribution Layer (CCNA): Routing
Access: Switches
CHAPTER 3 TCP/IP
DOD Model is same as TCP/IP model
Pg 90: Comparison of the two models
Drag and Drop Question: place in order or compare the two models
Process / Application: 8 features
Telnet: Remotely access. Not secure and everything is in plain text. Port 23.
Pg 92: Secure Shell (SSH): Remotely connect a host securely. Port 22
File transfer protocol(FTP): Port 20 and port 21 (Feature rich). Robust file transfer protocol
- User accounts
- Groups
- Pass and permissions
TFTP: Light weight file transfer protocol. Feature less. Push or pull files. Port 69
Pg 94: SNMP allows the server to get information about the host on the server. Simple Network
Management Protocol. Port 161
Pg 95: Http it is used to serve web pages on port 80
Pg 96: Https It serves web pages securely Port 443
NTP: Allows the host to synchronize time with its server. This is important because all authentication is
time based.
Pg 97: Domain Name Server (DNS) Resolves a name (FQDN) to an IP. FQDN Fully Qualified Domain
Name. Port 53
Pg 98L DHCP provides information Port 67.
Bootstrap P
DHCP is used by device who has an operating system
User for host who do not have an operating system.
Pg 100 APIPA: Assigns a host IP Address when DHCP server is not available. Eg 169.254.x.x Can not be
used to connect to the internet. Only works with a local network. (Broadcast domain).
All protocols mentioned above are layer 7.
HOST TO HOST LAYER <-> Transport layer
Pg 105: TCP & UDP Differences
- Each TCP segment has a sequence number
- UDP Video streaming, high bandwidth application. It adds source and dest port
- TCP is known for reliability due to sequence no and acknowledgment
- TCP is connection-oriented.
- UDP is low overhead, doesnt add much to your data.
- Knowing this difference is imp for exam
Pg 109: Table Key Protocols that use TCP and UDP
- UDP: SNMP TFTP DNS BooTPS/DHCP, NTP
- DNS is both UDP and TCP
Pg 110: Internet Layer <-> Network Layer
At the internet layer every packet gets a IP header. Contains Source and Dest IP.
Pg 113 Table 3.3 not needed
Pg 114 ICMP: Lets you get a status on unicast. Unicast is when you communicate one to one.
Eg: Ping uses ICMP to communicate.
Eg: Trace route uses ICMP to get a hop count
Pg 117: Address Resolution Protocol resolves an IP address to MAC address. Done by the host.
Pg 118: IP ADDRESS, Layer 3
IP Address: 32 bits
Octet: 8bits
Eg: 192.168.50.40
1
st
octate Size Subnet Mask
Class A 1-126 16.7 M 255.0.0.0
Class B 128-191 65 K 255.255.0.0
Class C 192-223 254 255.255.255.0
1
st
2
nd
3
rd
4
th
Network Host
Class A Network Host Host Host 8 24
Class B Network Network Host Host 16 16
Class C Network Network Network Host 24 8
128 64 32 16 8 4 2 1
1 1 1 1 1 1 1 1 255
Block = 2^n (No of host bits), 2^24 = 16,777,216. No of address you can have in that network.
Usable Hosts add = 2^n - 2
NOTE: Every network reserve 2 addresses, Network address and Broadcast address.
Network All host bits are off, First Address
Broadcast All host bits are on, Last Address
Eg:
IP Address: 192.168.111.99 72.59.10.25
Network Address: 192.168.111.0 72.0.0.0
Broadcast Address: 192.168.111.255 72.255.255.255
Pg 120: Summary of classes
Pg 125: Private IP Address
- Class A starts with 10
- Class B Start 172.16 to 172.31
- Class C starts with 192.168
Pg 126: Loopback address starts with 127.x.x.x
Layer 2 broadcast address #FFFFFFFFFFFF
Layer 3 broadcast address 255.255.255.255
Broadcast is one to everyone.
Unicast is one to one.
Multicast is one to many
All multicast address starts with 224.x.x.x
CHAPTER 4 EASY SUBNETTING
Benefits to subnetting
- Minimize Broadcast (Since each subnet will have its Broadcast message)
- Optimizing network performance (All users wont receive clutter of messages)
- Simplified Management (Easier when network spans over large geographical location)
- Security (Security between subnets)
Pg 144 Cidr, representation of subnet mask.
Eg:
192.168.50.0/24
We need 2 subnets
Thus, 2^n = 2 => n = 1
We now add 1 more network bit => 192.168.50.0/25
Host Bits = 32-25 = 7
Block = 2^7, Usable size = 2^7-2
Trick
CIDR Block Mask no of subnets
/24 256 .0 1
/25 128 .128 2
/26 64 .192 4
/27 32 .224 8
/28 16 .240 16
/29 8 .248 32
/30 4 .252 64
Network Address 1
st
2
nd
Broadcast
Starts with 0 1+Network 1-Broadcast 1- Next network address
+ Block size
NOTE: Your last network address must be 256 otherwise wrong calc. Dont use that! Just to check
Eg 192.168.99.0/24 we need 8 subnets?
CIDR : /27
Block : 32
Mask: 255.255.255.224
Network 1
st
2
nd
Broadcast
.0 .1 .31 .32
.32 .33 .62 .63
.64 .65
.96 .97
.128 .129
.160 .
.192
.224
.256
Note: Your last subnet will have the same network address as your subnet mask. Eg: 224
/20 4096
/21 2048
/22 1024
/23 512
/24 256 .0 1
/25 128 .128
/26 64 .192
/27 32 .224
/28 16 .240
/29 8 .248
/30 4
Subnetting for CLASS B
172.100.0.0/16 to 172.100.0.0/22
CIDR:/22
Block: 1024
Mask:255.255.252.0
# of subnets = 64
Network Add = 256-Mask 3
rd
octate = 256-252 = 4
N 1
st
Last B
0.0 These are calculated same way as before
4.0
8.0
12.0
..64 more
CHAPTER 5
Pg 182: VLSM Subnetting
VLSM is the least wasteful of IP Addresss when you subnet.
Eg: 192.168.5.0/24
# of host
A: 5
B: 90
C:16
Subnet in size order
Network Router IP Mask Block
B .0/25 .1 (Network +1) .128 (From table) 128 (find where can you
fit the requirement)
C .128/27
(Prev network + Block)
.129 .224 32
A .160/29 .161 .248 8
As you can see in VLSM each subnet gets its own size and cider etc
Eg:192.168.57.0 /27
A 100
B 2
C 12
D 31
E 4
Network Router IP Mask Block
A .0/25 .1 .128 128
D .128/26 .129 .192 64
C .192/28 .193 .240 16
E .208/29 .209 .248 8
B .216/30 .217 .252 4
Note: Default gateway is the same as router IP
DAY 2
Eg:
192.168.101.0/24 and we need 8 subnets
New prefix = /27
Mask = .224
Block =32
Network 1
st
Last Broadcast
.0 .1 .30 .31
.32 .33 .62 .63
.64 .95
.96 .127
.128
Eg:
172.20.0.0/16 and we need 8 subnets
New Prefix = /19
Mask = .224.0
Block = 8192
Thus increment = 256-224 = 32 (magic no 3
rd
octate of mask)
SUMMARIZATION
To make routing table more efficient summarization is used.
Eg: 172.25.10.0/24, 172.25.11.0/24, 172.25.12.0/24 These 3 are connected to a router.
The router tells its neighbor a summarized address such as 172.25.0.0/16
If we have the following 3 address:
172.20.0.0/19
172.20.32.0/19
172.20.64.0/19
NOTE: The cider of the summary has to be smaller than cider of the network. Dont take an IP out of its
class.
Summarized add 1 = 172.20.0.0/16
Eg: Class A address has been subnetted into class B
10.10.0.0/16
10.20.0.0/16
10.30.0.0/16
Summarize the above addresses. For summary address all the addresses have to be included in the first
subnet range.
10.0.0.0/8 (This is keeping the 1
st
octate locked)
10.0.0.0/11 ( 10.0.0.0 10.31.255.255, As you can see all 3 addresss above are included within the first
subnet range)
IOS BASIC
You can access the IOS by various Access Lines
- Console line (Rj45 DB9 OR Rolled cable)
- Auxiliary line is back up network, for modem access using phone line.
- Telnet / SSh
Router modes:
- User EXEC mode >
- Privilege mode , enable => #, disable (sends you back to user mode)
- Global mode, config # configure terminal, exit (sends you back to privilege mode)
NOTE: Would you like to enter initial config mode? Ans: NO!
Shortening commands: try adding letters till you get it to work. Eg en , disa
Router (config)# hostname juan (Change router name)
Router (config)# enable password cisco (Puts a pass for privilege mode)
Router# show running-config
NOTE: Enable pass is not an encrypted pass, its in clear text
Router (config)#no enable password (removes the configuration)
Router (config)# enable secret cisco (puts an encrypted pass on privilege mode)
How to protect your console line:
Router (config)# line console 0 (it will always be zero, since only 1 physical port)
Router (config-line)# password cisco
Router (config-line)# login
Router (config-line)#exit
How to protect your auxiliary line:
Router (config)# line aux 0
Router (config-line)# password cisco
Router (config-line)# login
Router (config-line)#exit
How to protect your vty line: (telnet or ssh)
Router (config)# line vty 0 4 (limits the no of sessions to 4)
Router (config-line)# password cisco
Router (config-line)# login
Router (config-line)#exit
NOTE: lines do not support encryption. But we can use a different command that will encrypt all
passwords.
Router (config)# service password-encryption (ser pass)
NOTE: When you disable the above command. It will do nothing to current pass. None of the passwords
will be decrypted. But new passwords will not be encrypted.
How do we setup a banner or welcome message?
Router (config)# banner motd $Welcome to router 14$ (message of the day, everyone sees it)
NOTE: you have to start and end with the delimiter (some character Eg X, $ etc).
How to setup an interface?
Router# Show interfaces (Shows all the info of interface)
Router# show ip interface brief (Shows a brief version of previous command)
Router# config t
Router (config)# interface fastethernet 0/0 (Connect to an interface)
Router (config-if)# ip address 192.168.50.1 255.255.255.0 (assigns the ip address and mask)
Router (config-if)# description LAN link to accounting (Descriptive tag)
Router (config-if)# no shutdown
Router (config)# sh ip int brief
NOTE: Status up and Protocol down => Layer 1 issue or its a cable issue.
If we configure another interface to the same network it will give an error. Eg: 192.168.50.1 and
192.168.50.2 are the same network but different ip. Every interface needs to have a different network
address or subnet Eg: 192.168.51.1
If you want to run a privilege command in global you can do it as follows:
Router (config-if)# do sh ip int b
NOTE: if you are in global config mode and want to use privilege command using do, ? wont work
Now we need to save all the config we just did.
Router# copy running-config startup-config
When asked for filename [asdas]? Press enter
How do I verify if change has been made?
Router# show startup-config
To erase all configurations
Router# erase startup-config (Will erase nvram containing config file)
If asked to clear the running config. You erase the start-up and reboot.
Router Components
ROM ( Bootstrap, POST, Mini-ios, ROMMON, Config register)
Flash (cisco IOS, .bin file)
RAM (running config)
NVRAM (startup config)
NOTE: Always have a backup of your ios and config files
To make a copy outside of the router
SYNTAX: Copy [From] [To]
Router# Copy running-config tftp
Then enter the remote host address and destination file name
Thus copy is used for back up
Now if my router is broken and I need to use the back up
Router# copy tftp startup-config
Upgrade or back up operating system
Copy tftp flash OR copy flash tftp
NOTE: once you buy a router cisco gives you 90 days to download ios from them
Password reset
Have to be done using console. No telnet and ssh
- To interrupt the boot its ctrl+Break
- Takes you to mini ios with prompt rommon>
- Change the configure register to 0x2142 bypasses the nvram which has the startup config
- Rommon> confreg 0x2142
- Reset router, Rommon> reset
- Enter privilege mode, enable (no password needed)
- Copy start-up config running-config
- Change password for all (global mode)
- Change the config register to 0x2102, Router (config)# config-register 0x2102 (default boot)
- Copy running-config startup-config (save)
CHAPTER 8: ROUTING
192.168.200.10/24, Class C
192.168.201.10/24, Class C
But these two are in different domains. Each network is a broadcast domain.
Static route:
Router (config)# ip route destination-network subnet-mask nexthop-address administrative_distance
permanent
- Router> Enable
- Router# Config t
- Router(config)# Hostname R1
- Router(config)# Do sh ip int brief
- Router(config)# Int f0/0
- Router(config-if)# Ip add 192.168.100.1 255.255.255.0
- Router(config-if)# No shut
- Router(config-if)# Exit
- Router(config)# Int s0/0
- Router(config-if)# Ip add 192.168.50.1 255.255.255.0
DTE and DCE on smart cable (Real world you will always be DTE if getting line from provider)
NOTE: If you are the DCE then you need to configure the line speed as well.
- Router(config-if)# No shut
- Router(config-if)# Clock rate 64000 (always this value)
- Router(config-if)# Do show history (shows you the last 10 commands)
- Router(config-if)# Exit
- Router(config)# Sh ip int brief
(Ping your interfaces to check first)
- Router# Ping 192.168.50.1
- Router# Ping 192.168.100.1
- Router(config)# Ip route 192.168.200.0 255.255.255.0 192.168.50.2
- Router(config)# Exit
- Router# Show ip route (shows routing table)
DAY 3
Router (config)# ip route destination-network subnet-mask nexthop-address administrative_distance
permanent
- Lowest administrative distance is the best path. Default administrative distance of static route is
1
- When you add permanent to a route it always keeps the route in the table.
- For next-hop address you could use the exit interface name instead.
Eg: Ip route 192.168.200.0 255.255.255.0 s0/0
NOTE: Flapping is when the interface keeps going up and down. In such a case permanent is useful.
Now to set a default route: (The gateway of last resort)
Ip route 0.0.0.0 0.0.0.0 192.168.50.1 (only set the next hop or exit interface (s0/0))
A 3 B 7 C 6 D
1 2 4 5
C1 C3 C7
C3 C2 C4
S2 S1 C6
S7 S1
S6
S4
S5
NOTE: Every network needs to have an entry in the routing table.
Since router A has only 1 exit point or called a stub router, we can set a default route to push all traffic
towards 3.
DYNAMIC ROUTING PROTOCOLS
- EGP (Exterior Gateway Protocols), used to route WAN, Between AS
- IGP (Interior Gateway Protocols), use to route LAN or an Autonomous system (AS)
o Distance Vector Measures by hops, limited to 15 hops, unreachable after
o Link state- Bandwidth (of the interface port) based, unlimited hops
Distance vector
NOTE: Slowest link is the speed of your network.
Link state always opts for the fastest path
Pg 387: CH 9 OSPF & RIP comparison
- RIPv1 is not multicast, broadcast based. Every 30 mins. No subnetting.
- As the router populates the routing table its is converging. Once the table is complete is has
converged.
- RIP has slow convergence since it is timer based. If I setup a new interface it takes 30 secs for
every hop to know.
- RIP1 has no summarization
- RIP2 is multicast based but still slow convergence.
- OSPF measures speed or bandwidth and converges fast because it is event triggered based. So if
a network is down, it start informing everyone about it. Dijkstra
- EIGRP cisco proprietary protocol, comb of bandwidth hops and delay. It is processor intensive.
- DUAL (Diffusing Update Protocol)
OSPF (Open short path first) (Important features, learn them!)
- Fast convergence since its trigger based update.
- OSPF supports VLSM/CIDR
- Open standard works on any enterprise class router
- Efficient routing table update. So if 5 things happen. It will send an update containing all 5
changes.
- Supports hierarchical design
NOTE: triggered update only sends the update.
Pg 389: OSPF Terms
- Link
- Adjacency: No information shared until adjacency is formed
- Router ID: set it, highest ip on loopback, highest ip on a physical interface
- DR: only 1 DR in an area, adj to every router. Receives routing update and sends routing update
- BDR: adj to all routers, receives all routing update
- If DR comes back BDR remains to be the DR
- Election of DR and BDR are based on priority. Highest priority is DR and second highest is BDR
- If priority match then chosen based on highest router Id.
- Hello Protocol: used to form and maintain (40sec) adjacency
- Link State Advertisements (LSA)
- Neighborship database: list of all ospf routers (you just have to be adjacent to the DR and BDR)
- Topological database: List of all ospf routes
- OSPF Area
- Broadcast (WAN) and Non-broadcast (Frame relay)multi-access: These networks require DR and
BDR.
- Point to point / point to multipoint: Do not require the use of a DR or BDR
Router 1 Router 2
R1(config)# router ospf
R1(config-router)# router-id 1.1.1.1
Now we advertise the networks connected to this router
Network network_address wildcard_mask area_no
R1(config-router)# network 192.168.50.0 0.0.0.255 area 0
Wildcard mask is opp of subnet mask
/24
255.255.255.255
(-) 255.255.255.0
= 0.0.0.255
/25
255.255.255.255
(-) 255.255.255.127
= 0.0.0.128
R1(config-router)# passive-interface f0/0 (it will not send out or receive routing table updates from that
interface)
NOTE: never make serial passive since thats how you connect to other routers, only make fast Ethernet
passive. Also make connection to the internet passive. Since you dont want to adv on int or receive
updates from there.
Pg 407:
Show ip ospf database shows you the neighborship database
Link Id is other routers router id
ADV Router is the router that told you about the link id
Age how long the router has been adjacent to you.
Pg 408:
Show ip ospf interface [interface name]
Ip address of the interface
Priority, higher is better in ospf. Default priority is 0
DR ID
BDR ID
Hello every 10 seconds and Dead timer for 40 seconds. If not heard in 40 seconds then considered
broken. Wait 40 sec to tell others.
Pg 409: info list
Sh ip ospf neighbor (only directly connected)
State: Loading means something might be wrong otherwise it will be full.
Address of interface
Show ip protocols
Show ip ospf
Show ip ospf database
Show ip ospf neighbor
Show ip route
Multi-Area OSPF
Types of routers
Backbone Router (BR): any router in area 0
Area Border Router (ABR): a router that has interface in more than 1 area.
Internal Routers (IR): Routers that have all the interfaces within an area
Autonoms System Boundry Router (ASBR): atleast one interface is connected to another AS or external
network
We use multi-area design to reduce LAS flooding, and optimize performance
Pg 785:
EIGRP
Supports IPV4 and IPV6, VLSM/CIDR (subnetting), discontiguous networks (having ip with different class
in same network)
Efficient neighbor discovery
- Hello or ack received
- AS no have to match
- Identical metrics (K values)
RTP Reliable Transport Protocol, reliable multi-task
NOTE: OSPF sends updates using LSA
DUAL Diffusing Update algorithm
EIGRP assigns a feasible distance to the route. A route with lower FD is considered better.
Reported or Advertised distance: Your neighbors FD.
Reported or advertised distance is always lower than FD i.e. AD<FD
Successor is the route with lowest FD
Feasible Successor is all the other routes that are not successor. Can store up to 16 FS
Neighbor table: Directly connected eigrp routers
Topology table: List of all EIGRP FS and Successor
Split Horizon: Router will not send information back on the same route. Routing table never comes back
the way it came from (same interface).
Configuring EIGRP:
R1(config)#router eigrp 10
R1(config-router)# network 192.168.50.0
R1(config-router)# network 192.168.100.0
R1(config-router)# passive-interfaces f0/0
Pg 12: EIGRP show commands
Sh ip eigrp neighbors
Sh ip eigrp interfaces
Sh ip route
x.x.x.x [default Administrative Dist (90) / Metric (FD)] via next_hop age_of_route exit_interface
Pg 815:
Show ip eigrp topology
NOTE: Only way you have more than 1 successor is if they have same FD
x.x.x.x, x successors, FD is x via x.x.x.x [FD / Advertised Dist]
Pg 816:
Show ip eigrp traffic
NOTE: default eigrp hop count is 100. We can set it up to 255. Also by default auto summarization is
turned on
Default maximum path is 4 and up to 16
Will show networks you advertise
Show ip protocols
Show ip eigrp events
Log og eigrp events
Why do we disable auto summarization in EIGRP?
192.168.50.0/29
192.168.50.8/29
192.168.50.16/29
192.168.50.24/29
192.168.50.32/29
192.168.50.40/29
EIGRP summarizes to class of the IP. So both routers will summarize to the same address that is
192.168.50.0/24. Thus we turn it off.
DAY 4
IP V6
- 128 bits -> 3.4 x 10^38 no of addresses
- IPSec ->Built in
- Multicast based, no broadcast feature. Better performance
- Broadcast replaced by Anycast
- Anycast: one to nearest
- Plug-n-play: IPV6 LAN configured without DHCP server (configuration)
- Auto-configuration: auto assign ip using prefix
- 8 fields
- 16 bits per field
- It is classless
- First 64 bits is prefix (network bits)
o First 48 bits is internet IP, given by provider
o Next 16 bits is subnet-id
- Next 64 bits for interface id (host)
2001:0db8:3c4d:0012:0000:0000:1234:56ab
Short form for it
- Drop leading zeros
- 4 zeros can become 1 zero
- 4 zeros can also be replaced by :: but can be done only once in the address
2001:db8:3c4d:12:0:01234:56ab
2001:db8:3c4d:12::1234:56ab
IPV6 loopback address:
0000:0000:0000:0000:0000:0000:0000:0001 <=> ::1
Eg:
2001:0000:0000:0012:0000:0000:1234:56ab 2001:0:0:12::1234:56ab
Configuring IPV6
Manual approach:
R1(config)# int f0/0
R1(config)# ipv6 address 2001:0db8:3c4d:0012:0000:0000:1234:56ab/64
NOTE: cider can be max 64 not bigger
NOTE: Every IPV6 interface will have minimum of 2 addresses.
Link-local address:
R1(config)# int f0/0
R1(config)# ipv6 enable
To verify:
Replace any ip command with ipv6
Auto assign IPv6
R1(config)# int f0/0
R1(config)# ipv6 address 2001:db8:3c4d:1::/64 eui-64
Eui is an identifier fills the last 64 bits
R1# show ipv6 interface brief
R1# FastEthernet0/0 [ /protocol]
Linklocal add
Auto assigned address
Auto configuration EUI
Adds FFFE
Flips 7
th
bits of MAC address
902B.34A4.E25A
922B:34FF:FEA4:E25A:
First 6 char FFFE last 6 char and 7
th
bit flipped
8 4 2 1
1 0 0 1 9
0 0 1 (7
th
bit flipped) 0 0 -> 2
0 0 1 0 2
1 0 1 1 B
IPV6 types
Unicast:
Global unicast (Public IPs), 2000::/3
Unique Local (Private IPs), FC00::/7
Link local address: Auto assigned FE80::/10 for LAN use only
Multicast: One to Many, FF0::/8
Anycast: one to nearest, nearest interface in terms of routing distance. Replaces broadcast
IPv6 protocol:
DHCPV6: Host configuration, Will give first 64
ICMPV6: same as V4
NDP: Neighbor discovery Protocol
- Determines the MAC address of neighbors
- RS FF.., RA FF02::1, NS, NA, DAD
Routing protocols:
RIPng
OSPFv3
EIGRPv6
Protocols are all same except name.
IPv6 Migrating Technique
Dual Stacking: Having both IPv4 and IPv6
6to4 Tunnel: IPV6 <-> IPV4 creates separate routes for IPv4 and IPv6
NAT-PT (Protocol Translation): Translates at router IPv4 <-> IPv6
NOTE: R1(config)# ipv6 unicast-routing, enables ipv6 routing
Static routing:
Ipv6 route network_address/cider next_hop_add
Routing protocol (ospf):
R1(config)# Ipv6 unicast-routing (needed to enable ipv6 routing)
R1(config)# Ipv6 router ospf 1
R1(config)# router-id 1.1.1.1xd
R1(config)# int f0/0
R1(config)# ipv6 ospf 1 area 0
R1(config)# int s0/0
R1(config)# ipv6 ospf 1 area 0
NOTE: View slides for ipv6 commands on dynamic routing.
Chapter 12 ACL
Pg 503: secured network
Access List: List of rules, controls packet flow
ACL lets you filter traffic off IP add or port numbers
- Rules applied in the order written
- Can only apply to one rule
- Discards packets if doesnt matches any rule
Note: you must match a rule to enter
Standard ACL worries about only where coming from not where going to. Source IP, block/permit
packets from an entire network subnet
Extended can block based of 4 conditions: IP add, Protocol, Port
Named Access list
Can only be named or extended
NOTE: use finger to trace the route, if going in or going out.
Pg 505: Guidelines
- Interface can have only one inbound and one outbound
- More specific route at the top of list (due to order) Eg host is more particular then network.
o Write host rules first then network rules
- New rules always at bottom
- To remove an ACL, delete ACL and redo without the one you dont need. (use notepad)
- Implicit denial: use permit any to allow everyone and focus on who to deny
- Make sure to apply the ACL to interface
- Router will not write an ACL to block a packet from another router. Only hosts.
- Standard access list close to dest. Will block all at source
- Extended access list at source. Since its specific.
Control sales from going into finance
(permit a host and deny a network)
Standard access list can use only numbers between 1-99
Access-list no permit/deny network_add/host wildcard/host_add
Access list
!Standard (comment)
Access-list 10 permit host 192.168.100.10 (Allowing Host A)
Access-list 10 deny 192.168.100.0 0.0.0.255 (Blocking Sales network)
Access-list 10 permit any (Allowing everyone else)
ip access-group no direction
Applying to router
Router(config)# int s0/0
Router(config-if)# ip access-group 10 out (Applies to serial interface 0/0 outgoing)
NOTE: make sure you test!!!
Extended access list can use only numbers between 100-199
Access-list no permit/deny tcp/udp/ip source dest eq port_no
!Extended (comment)
Access-list 110 permit tcp host 192.168.100.10 host 192.168.200.50 eq 80 (permits host A)
Access-list 110 deny tcp 192.168.100.0 0.0.0.255 host 192.168.200.50 eq 80 (denies sales network)
Access-list permit ip any any (allow anything, if we miss this no routing protocols, all ports)
Applying to router
Router(config)# Int f0/0
Router(config-if)# Ip access-group 110 in
Named ACL
!Name Standard
Ip access-list standard DenySales
Permit host 192.168.100.10
Deny 192.168.100.0 0.0.0.255
Permit any
exit
Int s0/0
Ip access-group DenySales out
!Name Extended (comment)
Ip access-list Extended DenyToWeb
permit tcp host 192.168.100.10 host 192.168.200.50 eq 80 (permits host A)
deny tcp 192.168.100.0 0.0.0.255 host 192.168.200.50 eq 80 (denies sales network)
permit ip any any (allow anything, if we miss this no routing protocols, all ports)
exit
R# show access-list
R(config)# no access-list no
Write the ACL in global first then apply in interface
Lab on Access list
!Standard
access-list 5 permit host 192.168.50.10
access-list 5 deny 192.168.50.0 0.0.0.255
access-list 5 permit any
!Extended
access-list 105 permit tcp host 192.168.250.240 host 192.168.40.10 eq 80
access-list 105 deny tcp 192.168.250.0 0.0.0.255 host 192.168.40.10 eq 80
access-list 105 permit ip any any
Day 5
Network Address Translation (NAT)
- Translates 1 IP to Another
- Minimizes IP Conflicts
- Only one configuration of router required for internet access. Easier connection
- Eliminates address renumbering
- NAT makes routing slower due to the need for translation
- Lack of end to end traceability. In real world this could be a security adv
- Certain apps wont work with it. Voice over IP (VOIP)
Static NAT
- One to one translation
- Done for Host that need to be reachable from outside
- R1(config)# ip nat inside source static 192.168.100.10(web server) 64.10.10.10(given by provider
- R1(config)# int f0/0
- Ip nat inside
- R1(config)# int s0/0/0
- Ip nat outside
- Direction of translation needs to be defined!
Dynamic NAT
- Many to many
- Create your pool
- Ip nat pool TIA(name) 79.10.10.2 79.10.10.250(range) netmask 255.255.255.0(subnet mask)
- Hosts that can use the range of public ip above
- Access-list 1 permit 192.168.100.0 0.0.0.255
- Assign range to list
- Ip nat inside source list 1 pool TIA
- Directions need to be set!
- R1(config)# int f0/0
- Ip nat inside
- R1(config)# int s0/0/0
- Ip nat outside
NOTE: in real world this is not feasible since if you hosts are more than available range of public ips
then remaining will not get access.
Overloading (PAT/PNAT)
- Many to one
- Tracks you by port number. Your comp makes up a port no. For each host it makes a temp
routing table. Overwhelms router.
- Create pool
- Ip nat pool MEGAPATH(name) 24.1.10.1 24.1.10.1 netmask 255.255.255.0
- We can have more than 1 IP in a NAT pool
- Create list
- Access-list 2 permit 192.168.100.0 0.0.0.255
- Now assign to eachother
- Ip nat inside source list 2 pool MEGAPATH overload (forgetting overload will make it dynamic)
- Set direction as before
NAT Names
- Inside local (Host addresss)
- Inside global (address of router connecting to Internet)
- Outside global (add of service provider)
- Outside local (local address at the service provider)
CHAPTER 10: SWITCHES
- Learns MAC address:
o Initially MAC address table is empty
o Host A sends data to switch, switch learns from source mac add
o When switch doesnt know dest MAC add it performs a flood asking who has the dest
MAC add. It doesnt send the flood message to the link it got frame from.
o Host B replies to the flooding message thus switch learns.
o DHCP discovery broadcast as soon as you turn on the switch
- CAN Table, MAC add table, forward/filter table: Mac add Port no
- Forward/filter decision: doesnt send back a flooding message back to the link where the initial
message comes from.
- Loop avoidance using Spanning Tree Protocol
Spanning Tree Protocol
- Avoid loops on switches and bridges using STP Algorithm
- Database of every port switch has and how it should use it
- Broadcast storm: continuous flooding. All switch lights turn on and off at the same time
- Root bridge: name given to the switch that controls all other switches. Lowest priority becomes
root bridge. If same priority lowest mac address becomes root bridge
- Default priority 32768. Lowest we can make it is 0 (lowest priority), next one after that is 4096
(increments), next 8192 and so on.
- Non-root bridges: all other
- BPDU: Bridge Protocol Data Unit. Switch exchange info
- Bridge Id: identification for spanning tree => Bridge id = Priority + VLAN-ID. Switch with lowest
bridge id is the root bridge
- Port cost: every port gets a cost based on bandwidth
- Path cost: aggregate of port cost. Cost of multiple links
- Root Port: Best port to use to talk to it. Port with lowest cost leading to the root bridge. (port
with highest bandwidth). Every switch has one.
- Designated port: port with lower cost leading to another switch. Port marked to forward frame.
Need to be designated to forward frames
- Non Designated Port: Not allowed to forward frame. Potential to cause a loop.
- Blocked port: NDP will become blocked. still listens to BPDU. Prevents flood from happening
(imp!)
- Spanning Tree Protocol Port states
o By default switch ports are on unlike router
o Disabled: administratively down (by default on)
o Blocking: switch ports are in blocking by default
o Listening: cannot forward only listening for BPDU
o Learning: Learns MAC add for 15sec
o Forwarding: only state that allowed to send and receive frames.
o 50 sec from blocking to forwarding
- Types of spanning tree
o IEEE 802.1d: original that takes 50s
o PVST+: Per VLAN Spanning Tree, each spanning tree will get its own root bridge. VLAN
makes it fast
o IEEE 802.1w: Faster version 30s. RapidSTP
o Rapid PVST+: Same as above but with per VLAN
- PortFast and BPDU Guard
o PortFast: never go into blocking, only forwarding. When Interface connected to a single
host. Dont have to wait for 30s to go from blocking to forwarding.
o BPDU guard: port will go into shutdown if a BPDU received. Incase the host is removed
and a switch or other device is connected. Creates a potential to form a loop
EtherChannel
Allows you to combine interfaces to combine their bandwidth.
Channel up to 7 ports in cisco
3 requirements: Duplexing (full or half), Speed (same bandwidth), Encapsulation. Basically need to be
identical.
VLAN:
Break a switch into multiple broadcast domains. Similar to subnetting but at layer 2.
- Access port : carries traffic
- Carries traffic for 1 VLAN and 1 Voice
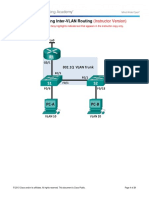
Refer to figure.
Routing between Vlans
VLANs communicate using layer 3 router
Router on stick (ROAS): has performance problem since all vlan go thru the same interface. Used
primarily when more than 20 vlans.
Sub interface is a fake interface of the original interface. Eg: g0/0 -> g0/0.1
G0/0
G0/0.1: encap dot1q V3
Switch side you trunk and on the router side you encapsulate.
Port Security:
Switch(config)# int f0/1
Switch(config-if)# switchport port-security maximum 1 (controls the number of MAC address)
Switch(config-if)# switchport port-security mac-address sticky
(Learn the first MAC address you see and only allow that)
CHAPTER 21 WAN
Customer premises quipment (CPE): equipment at your location that connects you to your provider.
Demarcation Point: where your provider line physically ends.
Local Loop: Many nodes provider have in your area. Eg: light poles, sewers etc.
Toll network: Trunk line inside WAN. Everyone pays, no one gets for free. When you leave your
providers network you enter toll
CSU/DSU only required when Tseries connection.
T1 E1 and T3 are copper connection. Slow when compared to fiber.
The optical carrier (OC) lines or sonic lines are fiber lines.
Sonic synchronous optical network
Connection types
Dedicated lines are point to point connections. They are expensive since dedicated.
Circuit switching is telephone network. Eg: Dial up and ISDN
Packet switch: relies on routers to switch the packet. At home dsl and cable is packet switch.
X.25
ATM (Asynchronous Transfer Mode)
Frame Relays
Packet switch services are the cheapest services.
Configure WAN:
NOTE: Always encapsulate you WAN
Encapsulation
PPP dedicated line
Frame relay frame relay line
HDLC - Cable (others)
PPP is WAN protocol but is also an Authentication method
Password Authentication Protocol (PAP) not secure, authenticates in plain text.
Challenge Handshake Authentication Protocol (CHAP) is secure
FRAME RELAY:
Packet switch
Runs on layer 3 switches. Configuration not required but need to know how to connect to it
Advantage of being cheaper or affordable than dedicated links.
Access rate: is max speed of frame relay line.
Committed Information Rate (CIR): Maximum guaranteed speed of Frame relay service.
Burst: is when you go over your CIR. Burst packets are discard eligible. Since burst will cause congestion.
Pg 926: Frame relay encapsulation
Frame relay for cisco or frame relay for ietf.
Encap frame-relay (default is cisco encap)
Encap frame-relay cisco (that is wrong)
Encap frame-relay ietf (for ietf)
Your provider informs which one to use.
Frame relay creates virtual circuit. Similar to TCP which creates a temporary virtual circuit during 3 way
handshake. But frame relay has a permanent virtual circuit (PVC).
This PVC gets a unique identifier called Data link connection Identifier (DLCI). Provided by service
provider.
Pg 928: consider Fig 21.18 Use of DLCI. Every router uses its own DLCI to send
Local Management Interface (LMI) keeps the interface alive for sending data. Helps with multicasting
AIC to DLCI. Global addressing keeps track of all the DLCI and where they go. Status of virtual circuit,
configuring LMI is a must.
NOTE: Frame-relay types and lmi types are different.
Frame relay types
LMI types
Cisco
Ansi
Q933a
Show frame.relay map OR sh frame map
FENC: Backward explicit congestion, they are bursting at you
BECN: Forward explicit congestion, when you are bursting at your provider.
Frame relay question are similar to 9tut.
VPN (Virtual Private Network)
Major drawback is speed. To secure all data we mask it so much.
Broadband technology.
Types:
- Remote Access: one host from outside is connecting back to inside (host to network)
- Site to site: one of my LAN to the internet through another LAN (network to network)
- Extranet VPN: Pay 3
rd
party to configure VPN on cloud. Team viewer, go to meeting is an
example. (network to someone else network back to your network)
VPN tunneling protocols:
L2F: cisco protocol
PPTP: microsoft protocol
L2TP: fusion of cisco and Microsoft
GRE: cisco only. Works only from cisco to cisco
IPsec Transforms (security protocol)
IPsec is not a tunneling protocol but it secures a tunnel.
Focus on Frame relay. WAN section and frame relay section on 9tut.
DHCP Configuration:
Creates a dhcp pool
Can give out ips from that network except the .1-.10 excluded in first line
Each host gets this as their default gateway
dns-server 4.4.4.4
lease day hours mins
Most people dont run dhcp on their router. They run a DHCP relay or DHCP forward.
IP helper address 10.10.10.254
Show ip dhcp binding -> shows which host has which ip
Show ip dhcp pool -> Shows all the ip in the pool and marks which have been leased out.
Show ip dhcp server statistics
Show ip dhcp conflict -> it shows if a host is assigned a static ip assigned to another host
Network Time Protocol (NTP)
Router to synch with NTP server
Ntp server ip_add version no
Cisco Discovery Protocol (CDP)
Allows a cisco device to communicate with another directly connected cisco device
Show cdp -> shows config ofcdp
Sh cdp neighbors
Interface how connected to local, port id what port connected to on local
Sh cdp neighbors detail
Entry add- ip add of that device, Version version of IOS on neighbor
CDP is cisco proprietary. CDP is licensed to other companies.
LLDP is an open standard for what CDP does.
Resolving hostnames
Host names can be resolved using host tables. Alternative to DNS
Eg: ip host SW-2 10.100.128.9 (assigns name to IP, which can be used later
Domain Name Service (DNS)
Ip domain-lookup -> resolve a name to an ip
Turn it off: no ip domain-lookup (on by default)
Ip name-server 4.4.4.4
Ip domain-name lammle.com
CHAPTER 17 Client redundancy
Pg 701: Fig 17.
FHRP (Protocol)
We need two physical router for this to possible
We thus we create a virtual router and have them talk to eachother.
1 physical and two virtual router
Virtual routers configured on all physical routers.
HSRP is cisco proprietary and supports up to 8 physical routers for redundancy. But only 1 will be active
and 7 will be back up. No load balancing in HSRP.
- Active router (only 1 active router)
- Standby router (rest of them)
- Virtual router (on all physical routers)
- Routers (any routers on the network that are not part of HSRP)
Virtual MAC Address
0000.0c07.ac0a
0000.0c Vendor Id
07.ac HSRP
Only last 8 bits have variation or 2 bytes
VRRP Does not load balance.
Pg 715: since it doesnot load balance there is only 1 router active and it is called the master router.
The ones not forwarding are called back up routers.
Gateway Load balancing Protocol (GLBP)can do load balancing: Can support only 4 routers.
GLBP AVG Active virtual gateway. Boss of all the other routers. Packets from host get sent to
GLBP AVF All other routers. They can forward packets.
- Load sharing
- Multiple virtual routers (1 for subnet).
- Preemption can switch based on work load
- Efficient resource utilization
SYS LOGS:
By default cisco router log to the console. It is useful to store this log on a server to view later.
Pg 722: Table 17.1 Important!!
Severity number higher includes everything lower
Pg 725: Logging 172.16.10.1 (sending logs to your syslog server)
Pg 726: SNMP (information about systems on the network)
SNMP V1 is not secure, authentication in plain text.
SNMP V2 also supports plain text authentication. We can do GET Bulk, many questions at once
SNMP V3 does everything SNMP V2 does but with encryption. Best!
Management Information Base (MIB)
MIB is the server that has all the information.
Net flow : it is only about network traffic
Pg 731: memorize all points
THE END
You might also like
- Network Security All-in-one: ASA Firepower WSA Umbrella VPN ISE Layer 2 SecurityFrom EverandNetwork Security All-in-one: ASA Firepower WSA Umbrella VPN ISE Layer 2 SecurityNo ratings yet
- CCNA 3 Case Study (1sem SY14-15)Document6 pagesCCNA 3 Case Study (1sem SY14-15)Juan Carlos DeLeon Gomez100% (2)
- Cheat Sheet For CCNP 350-401Document2 pagesCheat Sheet For CCNP 350-401Hakim QaradaghiNo ratings yet
- CCNAv7 - Enterprise Networking, Security, and Automation Final ExamDocument66 pagesCCNAv7 - Enterprise Networking, Security, and Automation Final ExamsinkuNo ratings yet
- 9.3.1.4 Packet Tracer - Skills Integration Challenge Instructions PDFDocument3 pages9.3.1.4 Packet Tracer - Skills Integration Challenge Instructions PDFJaime RicardoNo ratings yet
- Predictable Revenue Guide To Tripling Your Sales Parts 1 4 PDFDocument145 pagesPredictable Revenue Guide To Tripling Your Sales Parts 1 4 PDFPaulo De Tarso BarrosNo ratings yet
- Quick IPv4 Addressing and Subnetting by OlivoyDocument27 pagesQuick IPv4 Addressing and Subnetting by OlivoyviladroNo ratings yet
- Number: 350-401 Passing Score: 825 Time Limit: 140 Min File Version: 1.0Document45 pagesNumber: 350-401 Passing Score: 825 Time Limit: 140 Min File Version: 1.0MacKenzie KymberNo ratings yet
- CCNA 2 (v5.1 + v6.0) Final Exam Answers FullDocument50 pagesCCNA 2 (v5.1 + v6.0) Final Exam Answers Fullmuhammad hafis100% (1)
- QADocument9 pagesQAkiet eduNo ratings yet
- CCNA Answers - CCNA Exam - CCNA ExamsDocument30 pagesCCNA Answers - CCNA Exam - CCNA ExamsMihai Gheorghe100% (1)
- BGP Question and AnswersDocument19 pagesBGP Question and AnswersCabdalla100% (1)
- Shortnote LabDocument22 pagesShortnote LabSamiNo ratings yet
- CCNA Exam NotesDocument33 pagesCCNA Exam NotesMuhd IrfanNo ratings yet
- WAN TECHNOLOGY FRAME-RELAY: An Expert's Handbook of Navigating Frame Relay NetworksFrom EverandWAN TECHNOLOGY FRAME-RELAY: An Expert's Handbook of Navigating Frame Relay NetworksNo ratings yet
- CISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkFrom EverandCISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkNo ratings yet
- Cisco Network Administration Interview Questions: CISCO CCNA Certification ReviewFrom EverandCisco Network Administration Interview Questions: CISCO CCNA Certification ReviewRating: 4.5 out of 5 stars4.5/5 (6)
- Ethernet Networks: Design, Implementation, Operation, ManagementFrom EverandEthernet Networks: Design, Implementation, Operation, ManagementRating: 4 out of 5 stars4/5 (1)
- LEARN MPLS FROM SCRATCH PART-A: A Beginner's Guide to Next Level of NetworkingFrom EverandLEARN MPLS FROM SCRATCH PART-A: A Beginner's Guide to Next Level of NetworkingNo ratings yet
- CCNA 200-301 Practice ExamDocument208 pagesCCNA 200-301 Practice Examnws.pdfNo ratings yet
- Cisco IPSec VPN Configuration - IPSec For VPNDocument19 pagesCisco IPSec VPN Configuration - IPSec For VPNsmsomeksa7No ratings yet
- CCNA 200-301 OCG Study NotesDocument86 pagesCCNA 200-301 OCG Study NotesAbdullah IftikharNo ratings yet
- 4.3.8 Packet Tracer - Configure Layer 3 Switching and Inter-VLAN Routing - ILMDocument6 pages4.3.8 Packet Tracer - Configure Layer 3 Switching and Inter-VLAN Routing - ILMJhonathanNo ratings yet
- Cisco Wireless LAN Controller Configuration Guide, Release 7.2Document1,070 pagesCisco Wireless LAN Controller Configuration Guide, Release 7.2ysmeniaNo ratings yet
- 7.1.6 Lab - Use Wireshark To Examine Ethernet FramesDocument7 pages7.1.6 Lab - Use Wireshark To Examine Ethernet FramesJose Enrique Toledo FelipeNo ratings yet
- Cisco VPNDocument123 pagesCisco VPNChinni ChiNo ratings yet
- Cisco CCENT ICND1Document243 pagesCisco CCENT ICND1frankcalucciNo ratings yet
- CCNP SwitchDocument78 pagesCCNP Switchshalem123No ratings yet
- Lab - Troubleshooting Inter-VLAN Routing (Instructor)Document21 pagesLab - Troubleshooting Inter-VLAN Routing (Instructor)eztog006No ratings yet
- OSPF Hub-And-Spoke Configuration ExamplesDocument11 pagesOSPF Hub-And-Spoke Configuration Examplesabdallah18No ratings yet
- Cisco IOS Quick Reference Cheat Sheet 2.0Document9 pagesCisco IOS Quick Reference Cheat Sheet 2.0crissdemonNo ratings yet
- Number: 200-301 Passing Score: 800 Time Limit: 120 Min File Version: 0Document11 pagesNumber: 200-301 Passing Score: 800 Time Limit: 120 Min File Version: 0Geekware PeruNo ratings yet
- CCNA 1 Final Exam Answers 2019 (v5.1+v6.0) Introduction To NetworksDocument67 pagesCCNA 1 Final Exam Answers 2019 (v5.1+v6.0) Introduction To NetworksJamal ZaghmoutNo ratings yet
- Cisco Router CommandsDocument6 pagesCisco Router CommandsaCoeKwTF100% (1)
- 350 401 ENCORE v1.1 PDFDocument4 pages350 401 ENCORE v1.1 PDFbeloow beloow100% (1)
- NEW Cisco CCNA 200-125 Exam Dumps Latest Version 2019 For Free PDFDocument244 pagesNEW Cisco CCNA 200-125 Exam Dumps Latest Version 2019 For Free PDFJorge Enrique Cortez BastidasNo ratings yet
- Ccie R&S 400-101 - 779 Q&aDocument604 pagesCcie R&S 400-101 - 779 Q&aSalmanShahNo ratings yet
- Juniper (JNCDA) Voucher Assessment TestDocument8 pagesJuniper (JNCDA) Voucher Assessment TestTRYST CHAMANo ratings yet
- Answer:: Free Exam/Cram Practice Materials - Best Exam Practice MaterialsDocument23 pagesAnswer:: Free Exam/Cram Practice Materials - Best Exam Practice MaterialshetrurospiNo ratings yet
- Lab 3.2.1 Configuring EIGRP Routing: ObjectiveDocument5 pagesLab 3.2.1 Configuring EIGRP Routing: ObjectiveguijjouNo ratings yet
- Cisco Basic CCNA Lab Setup InstructionsDocument6 pagesCisco Basic CCNA Lab Setup InstructionstouzogNo ratings yet
- 300-101 CCNP Route Exam QuestionsDocument108 pages300-101 CCNP Route Exam QuestionsCesar Morera Alpizar89% (18)
- Cisco CCNA Exam - Are You Ready - Take This 10-Question Quiz To Find OutDocument9 pagesCisco CCNA Exam - Are You Ready - Take This 10-Question Quiz To Find Outpopcorn20156106No ratings yet
- Lab01 Basic VOIP ConfigurationDocument8 pagesLab01 Basic VOIP ConfigurationMohammed ElmadaniNo ratings yet
- CCNA 1 Final 2012 Exam AnswersDocument65 pagesCCNA 1 Final 2012 Exam Answerserzza storeNo ratings yet
- CCNP Enterprise Core Networking ENCOR ENARSI Product OverviewDocument20 pagesCCNP Enterprise Core Networking ENCOR ENARSI Product OverviewChimz Kabunda100% (2)
- Chapter2 - VirtualizationDocument12 pagesChapter2 - VirtualizationAfia Kamran100% (1)
- Datacom 2500Document152 pagesDatacom 2500L (R)No ratings yet
- CCNA 1 (v5.1 + v6.0) Chapter 2 Exam Answers Full PDFDocument16 pagesCCNA 1 (v5.1 + v6.0) Chapter 2 Exam Answers Full PDFderejeNo ratings yet
- PASSLEADER BY aNTON DUMP CCNA SECDocument36 pagesPASSLEADER BY aNTON DUMP CCNA SECAlex UrquijoNo ratings yet
- ENCOR Main PDFDocument350 pagesENCOR Main PDFChirita Alexandru MihaiNo ratings yet
- Cisco CCNA Routing and Switching 200-120 Official Cert Guide LibraryDocument3 pagesCisco CCNA Routing and Switching 200-120 Official Cert Guide LibrarytheachieverNo ratings yet
- OSPF Routing FundamentalsDocument4 pagesOSPF Routing FundamentalsAkhilesh KumarNo ratings yet
- CISCO Access Lists Workbook Student Version 1.2Document69 pagesCISCO Access Lists Workbook Student Version 1.2Krystal MeethNo ratings yet
- Lan Switching and SecurityDocument13 pagesLan Switching and SecuritybikkerNo ratings yet
- Using GNS3 For Switching LabsDocument7 pagesUsing GNS3 For Switching LabskinyNo ratings yet
- Final Discovery 3 100%Document20 pagesFinal Discovery 3 100%Trần Ngọc Ngàn100% (2)
- JNTU World: Part - A (Short Answer Questions)Document22 pagesJNTU World: Part - A (Short Answer Questions)Vinay KandulaNo ratings yet
- Isro-Cse-Syllabus - 7766d43bDocument2 pagesIsro-Cse-Syllabus - 7766d43bAM004 Muthu PandiNo ratings yet
- EtoDocument44 pagesEtopraveen0110100% (1)
- Jazz PackagesDocument10 pagesJazz Packageswaqar aliNo ratings yet
- Ats - Sekum Internet Connection: 192.168.10.xxx 192.168.10.xxx 192.168.2.xxxDocument1 pageAts - Sekum Internet Connection: 192.168.10.xxx 192.168.10.xxx 192.168.2.xxxHir TahirNo ratings yet
- User Manual - Ender-3S - ENDocument16 pagesUser Manual - Ender-3S - ENEnache DanielNo ratings yet
- AVEVA White Paper Instrumentation Aug2010 PDFDocument9 pagesAVEVA White Paper Instrumentation Aug2010 PDFFIRMANSYAHNo ratings yet
- Set Up and Solve Your PDE Problem - MATLAB & SimulinkDocument3 pagesSet Up and Solve Your PDE Problem - MATLAB & SimulinkNguyễn Thành CôngNo ratings yet
- Provisioning Module Developer Docs - WHMCS DocumentationDocument13 pagesProvisioning Module Developer Docs - WHMCS DocumentationJayBeeDeNo ratings yet
- Microprocessor Project: Digital WatchDocument26 pagesMicroprocessor Project: Digital WatchvirgiladrianNo ratings yet
- Asccend Rta v1.0Document0 pagesAsccend Rta v1.0Christopher GrahamNo ratings yet
- Romberg Rule of Integration: Major: All Engineering Majors Authors: Autar Kaw, Charlie BarkerDocument27 pagesRomberg Rule of Integration: Major: All Engineering Majors Authors: Autar Kaw, Charlie BarkerprasenajitaNo ratings yet
- Cloud Computing Chapter 10Document42 pagesCloud Computing Chapter 10ghar_dashNo ratings yet
- Information Week 500 2010 Full Report 8758322 3Document97 pagesInformation Week 500 2010 Full Report 8758322 3zain.aziz761227No ratings yet
- Scalable Modified Kneser-Ney Language Model EstimationDocument7 pagesScalable Modified Kneser-Ney Language Model EstimationPete aaNo ratings yet
- SS ZG653: Software Architecture: Introduction To The CourseDocument9 pagesSS ZG653: Software Architecture: Introduction To The CourseBalajiNo ratings yet
- Are A Phreak???: Nazi A Challenge To HackersDocument6 pagesAre A Phreak???: Nazi A Challenge To HackersBobHoskinsNo ratings yet
- NSS_BNSK459_Report_TEMPLATEDocument8 pagesNSS_BNSK459_Report_TEMPLATEsapnakamthaneNo ratings yet
- (Manual) : For LOCALDocument63 pages(Manual) : For LOCALDaniel MorenoNo ratings yet
- 6.control System Stability - NotesDocument24 pages6.control System Stability - NotesVeNkat Seshamsetti100% (1)
- LSB Image StegnographyDocument12 pagesLSB Image Stegnographyshaikhibrahim_951No ratings yet
- Dna ComputingDocument16 pagesDna Computingapi-3741442No ratings yet
- SQL Server 2000 EditionsDocument14 pagesSQL Server 2000 Editionskkhan19809633No ratings yet
- Siddharth K. Joshi Full Stack Developer: Technical SkillsDocument4 pagesSiddharth K. Joshi Full Stack Developer: Technical SkillsAnonymous N1CBbLVzUNo ratings yet
- Gianluca Hotz: SQL Server ModernizationDocument74 pagesGianluca Hotz: SQL Server ModernizationBee BumbleNo ratings yet
- Unix Case StudyDocument24 pagesUnix Case StudyJaikumar GuwalaniNo ratings yet
- Daa 2019 SyllabusDocument3 pagesDaa 2019 Syllabusmemoriesbringback121No ratings yet
- AN708 Series Intelligent Temperature Controller/ Adjustor User's ManualDocument8 pagesAN708 Series Intelligent Temperature Controller/ Adjustor User's ManualChaker Abdellatif100% (1)