Redundant Internet 3.1.1
Redundant Internet 3.1.1
Uploaded by
mochamad arifinCopyright:
Available Formats
Redundant Internet 3.1.1
Redundant Internet 3.1.1
Uploaded by
mochamad arifinOriginal Description:
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Copyright:
Available Formats
Redundant Internet 3.1.1
Redundant Internet 3.1.1
Uploaded by
mochamad arifinCopyright:
Available Formats
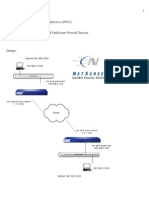
Dual ISP Branch Office Configuration
This document describes the steps to configure a dual ISP configuration for a Branch office. In
this scenario an office is connected to two ISPs and redundancy for outbound connectivity is
desired. This configuration uses a combination of static routing, policy based forwarding (PBF),
and destination interface based source NAT translation. This solution provides automatic
outbound Internet redundancy without the need for BGP routing protocol between ISPs.
The static default route will be configured to point to the backup ISP. A PBF rule with path
monitoring will be used to route traffic out to the primary ISP. If the path monitor finds the
primary PBF path is no longer available, traffic will automatically begin flowing over the backup
static default route.
Two source NAT rules will be configured to make sure the outbound traffic is source translated
to the correct IP address depending on the egress interface (primary or backup).
Prerequisites
• PANOS 3.1.1 and above
PANOS 3.1 1 version 1.4
Part 1: Configuration
1. Configure both Internet-facing interfaces in the same zone (e.g. Untrust)
set network interface ethernet ethernet1/1 layer3 ip 192.0.2.1/30
set network interface ethernet ethernet1/2 layer3 ip 192.0.2.253/30
set network interface ethernet ethernet1/3 layer3 ip 10.1.1.1/24
set zone Trust network layer3 ethernet1/3
set zone Untrust network layer3 ethernet1/1
set zone Untrust network layer3 ethernet1/2
2. Configure a static default route within your Virtual Router to you backup ISP
set network virtual-router router routing-table ip static-route default
destination 0.0.0.0/0
set network virtual-router router routing-table ip static-route default
metric 1
set network virtual-router router routing-table ip static-route default
nexthop ip-address 192.0.2.254
PANOS 3.1 2 version 1.4
3. Configure a PBF rule that forces all traffic from the trust Zone to any address other than
the local subnet(s) to use the primary ISP link. Make sure to negate the local subnet(s) in
the Destination Address for best results.
set rulebase pbf rules rule1 from zone Trust
set rulebase pbf rules rule1 source any
set rulebase pbf rules rule1 destination 10.1.1.0/24
set rulebase pbf rules rule1 service any
set rulebase pbf rules rule1 action forward egress-interface
ethernet1/1
set rulebase pbf rules rule1 action forward nexthop ip-address
192.0.2.2
set rulebase pbf rules rule1 source-user any
set rulebase pbf rules rule1 application any
set rulebase pbf rules rule1 negate-destination yes
4. Configure Path Monitoring on the PBF rule so it will only be active as long as the next
hop (or some other IP beyond the next hop) is available. You can use the default monitor
profile or configure a new one. If you leave the Target IP address blank the next-hop will
be monitored.
set rulebase pbf rules rule1 action forward monitor profile default
set rulebase pbf rules rule1 action forward monitor disable-if-
unreachable yes
PANOS 3.1 3 version 1.4
5. Configure two NAT rules to translate the source address for outbound Internet traffic.
Make sure the source address is correct for each egress interface.
set rulebase nat rules Primary from Trust
set rulebase nat rules Primary to Untrust
set rulebase nat rules Primary source any
set rulebase nat rules Primary destination any
set rulebase nat rules Primary service any
set rulebase nat rules Primary to-interface ethernet1/1
set rulebase nat rules Primary source-translation dynamic-ip-and-port
interface-address interface ethernet1/1
set rulebase nat rules Primary source-translation dynamic-ip-and-port
interface-address ip 192.0.2.1/30
set rulebase nat rules Backup from Trust
set rulebase nat rules Backup to Untrust
set rulebase nat rules Backup source any
set rulebase nat rules Backup destination any
set rulebase nat rules Backup service any
set rulebase nat rules Backup to-interface ethernet1/2
set rulebase nat rules Backup source-translation dynamic-ip-and-port
interface-address interface ethernet1/2
set rulebase nat rules Backup source-translation dynamic-ip-and-port
interface-address ip 192.0.2.253/30
6. Don’t forget your security policy to allow the outbound traffic and commit your
configuration.
set rulebase security rules rule1 from Trust
set rulebase security rules rule1 to Untrust
set rulebase security rules rule1 source any
set rulebase security rules rule1 destination any
set rulebase security rules rule1 service any
set rulebase security rules rule1 application any
set rulebase security rules rule1 source-user any
set rulebase security rules rule1 action allow
PANOS 3.1 4 version 1.4
Part 2: Testing
1. Start a continuous ping out to the Internet. Do a “show session id xxx” to see the details
of the ping session. While the primary link is available the session should be showing the
PBF rule active and the primary Internet link being used. Also, the correct source NAT
address should be displayed.
admin@PA-2050> show session all
-------------------------------------------------------------------------------
ID/vsys application state type flag src[sport]/zone/proto (translated IP[port])
dst[dport]/zone (translated IP[port]
-------------------------------------------------------------------------------
39/1 ping ACTIVE FLOW NS 10.1.1.100[1]/Trust/1 (192.0.2.1[1])
4.2.2.2[1]/Untrust (4.2.2.2[1])
admin@PA-2050> show session id 39
session 39
c2s flow:
source: 10.1.1.100[Trust]
dst: 4.2.2.2
sport: 1 dport: 1
proto: 1 dir: c2s
state: INIT type: FLOW
ipver: 4
src-user: unknown
dst-user: unknown
PBF rule: rule1(1)
s2c flow:
source: 4.2.2.2[Untrust]
dst: 192.0.2.1
sport: 1 dport: 1
proto: 1 dir: s2c
state: INIT type: FLOW
ipver: 4
src-user: unknown
dst-user: unknown
start time : Tue Mar 16 07:08:22 2010
timeout : 6 sec
total byte count : 148
layer7 packet count : 2
vsys : vsys1
application : ping
rule : rule1
session to be logged at end : yes
session in session ager : no
session sync'ed from HA peer : no
address/port translation : source
nat-rule : Primary(vsys1)
layer7 processing : enabled
URL filtering enabled : no
ingress interface : ethernet1/3
egress interface : ethernet1/1
session QoS rule : default (class 4)
PANOS 3.1 5 version 1.4
2. Show the PBF rule to make sure it is active and forwarding packets out the Primary
Internet interface.
admin@PA-2050> show pbf rule all
Rule ID State Action Egress IF NextHop Status
========== ===== ======== ======== =============== ================ ======
rule1 1 Active Forward ethernet1/1 192.0.2.2 UP
admin@PA-2050> show pbf rule name rule1
Rule: rule1(1)
State: Active
Action: Forward
Egress IF: ethernet1/1
NextHop: 192.0.2.2
Monitor IP: 192.0.2.2
Rule Status: UP
Monitor: Action:Fail-Over, Interval:3, Threshold:5
Stats: KA sent:194, KA got:177, Packet Matched:65915
PANOS 3.1 6 version 1.4
3. Unplug the primary link and find another new session with the “show session id xxx”
command. You should now see the PBF rule is no longer used, the backup egress
interface being used, and the backup source NAT address being used.
admin@PA-2050> show session all
-------------------------------------------------------------------------------
ID/vsys application state type flag src[sport]/zone/proto (translated IP[port])
dst[dport]/zone (translated IP[port]
-------------------------------------------------------------------------------
257/1 ping ACTIVE FLOW NS 10.1.1.100[1]/Trust/1 (192.0.2.253[1])
4.2.2.2[200]/Untrust (4.2.2.2[200])
admin@test2050> show session id 257
session 257
c2s flow:
source: 10.1.1.100[Trust]
dst: 4.2.2.2
sport: 1 dport: 200
proto: 1 dir: c2s
state: INIT type: FLOW
ipver: 4
src-user: unknown
dst-user: unknown Notice no PBF rule listed here
s2c flow:
source: 4.2.2.2[Untrust]
dst: 192.0.2.253
sport: 200 dport: 1
proto: 1 dir: s2c
state: INIT type: FLOW
ipver: 4
src-user: unknown
dst-user: unknown
start time : Tue Mar 16 07:13:37 2010
timeout : 6 sec
total byte count : 74
layer7 packet count : 1
vsys : vsys1
application : ping
rule : rule1
session to be logged at end : yes
session in session ager : no
session sync'ed from HA peer : no
address/port translation : source
nat-rule : Backup(vsys1)
layer7 processing : enabled
URL filtering enabled : no
ingress interface : ethernet1/3
egress interface : ethernet1/2
session QoS rule : default (class 4)
4. You will now see the PBF rule is inactive
admin@PA-2050> show pbf rule all
Rule ID State Action Egress IF NextHop Status
========== ===== ======== ======== =============== ================ ======
rule1 1 Disabled Forward ethernet1/1 192.0.2.2 DOWN
PANOS 3.1 7 version 1.4
You might also like
- 01 Connecting Things 2.01 Chapter1-STUDENT 2Document22 pages01 Connecting Things 2.01 Chapter1-STUDENT 2ShafinNo ratings yet
- Filtronic-OrpheusRev 2 0Document3 pagesFiltronic-OrpheusRev 2 0Eduardo Aguilar0% (1)
- Splintering UrbanismDocument512 pagesSplintering UrbanismJ00K3RNo ratings yet
- Configuring VXLAN BGP EVPNDocument13 pagesConfiguring VXLAN BGP EVPNEmailiftekhar100% (2)
- Configuring OSPF Brandon&KatieDocument8 pagesConfiguring OSPF Brandon&KatieLuis GonzalezNo ratings yet
- Lab 8Document6 pagesLab 8Tomas Rodriguez RamirezNo ratings yet
- Ios Nat LBDocument7 pagesIos Nat LBJorge Mosquera RNo ratings yet
- Comando Gns 3Document145 pagesComando Gns 3NeycerAnchundiaNo ratings yet
- Jncia Lab MannualDocument34 pagesJncia Lab MannualAsad Naqvi100% (2)
- Netscreen - VPN Troubleshooting.Document31 pagesNetscreen - VPN Troubleshooting.Amandeep SinghNo ratings yet
- iIOS NAT Load-Balancing With Optimized Edge Routing For Two Internet ConnectionsDocument7 pagesiIOS NAT Load-Balancing With Optimized Edge Routing For Two Internet ConnectionsCesar Rene Parada FloresNo ratings yet
- Route Leaking in MPLS/VPN Networks: Document ID: 47807Document5 pagesRoute Leaking in MPLS/VPN Networks: Document ID: 47807a3172741No ratings yet
- RIPv2 Part 2Document10 pagesRIPv2 Part 2nurinNo ratings yet
- CCNA CommandsDocument12 pagesCCNA CommandsAnjanava KumarNo ratings yet
- 6.2.3.8 LabDocument10 pages6.2.3.8 LabAutumn TillmanNo ratings yet
- 19-Troubleshooting Basic Network Services IDocument17 pages19-Troubleshooting Basic Network Services Imansoorali_afNo ratings yet
- Module 8 - Policy Based Routing: ISP/IXP Networking Workshop LabDocument15 pagesModule 8 - Policy Based Routing: ISP/IXP Networking Workshop LabmaracyberstationNo ratings yet
- CCNA All CommandDocument17 pagesCCNA All CommandwilsonhoeNo ratings yet
- Cisco IOS Security TemplateDocument10 pagesCisco IOS Security TemplateshankerunrNo ratings yet
- CCNP - FlashcardsDocument19 pagesCCNP - Flashcardsnacho_456No ratings yet
- Lab 7.7.3 Configuring IS-IS Over Frame Relay: AlternateDocument8 pagesLab 7.7.3 Configuring IS-IS Over Frame Relay: AlternateKishore Reddy KandiNo ratings yet
- Oa - Poe JR1 01 C9200LDocument8 pagesOa - Poe JR1 01 C9200LNguyen Quoc NhanNo ratings yet
- How To Update Bottos SupernodeDocument7 pagesHow To Update Bottos SupernodesgoiikNo ratings yet
- Basic Router Configuration: Honolulu Community College Cisco Academy Training Center Semester 2Document19 pagesBasic Router Configuration: Honolulu Community College Cisco Academy Training Center Semester 2elia maulaNo ratings yet
- Default Passive Interface FeatureDocument6 pagesDefault Passive Interface FeatureKiril KirovNo ratings yet
- Rphy System Bring UpDocument6 pagesRphy System Bring Upsoxfarxaway777No ratings yet
- Quick CommandsDocument9 pagesQuick CommandsMark WoffardNo ratings yet
- Take Assessment - CCENT Practice Certification Exam # 1 - CCNA Exploration: Accessing The WAN (Version 4.0)Document5 pagesTake Assessment - CCENT Practice Certification Exam # 1 - CCNA Exploration: Accessing The WAN (Version 4.0)marksafwatNo ratings yet
- Verificacion de NatDocument10 pagesVerificacion de NatJuanan PalmerNo ratings yet
- Cisco Training - 03 OSPFDocument23 pagesCisco Training - 03 OSPFIrfan Irawan CbnNo ratings yet
- OSPF Authentication II: Objective Lab TopologyDocument9 pagesOSPF Authentication II: Objective Lab TopologyTomas Rodriguez RamirezNo ratings yet
- VLSM and Static RoutingDocument12 pagesVLSM and Static RoutingPhong Duong Tan NhatNo ratings yet
- IPsec VPN Is Up But Network Is Not ReachableDocument2 pagesIPsec VPN Is Up But Network Is Not ReachableAyan NasNo ratings yet
- Routing ModuleDocument34 pagesRouting ModulechinthasreenivasaraoNo ratings yet
- CCENT Practice Certification Exam 1Document20 pagesCCENT Practice Certification Exam 1INGCESARCol0% (1)
- 20170140118-Dokumentasi Chapter9Document10 pages20170140118-Dokumentasi Chapter9abdi brillianNo ratings yet
- 28.1.5 Lab - Use Restconf To Access An Ios Xe Device - IlmDocument18 pages28.1.5 Lab - Use Restconf To Access An Ios Xe Device - IlmTRYST CHAMANo ratings yet
- Mpls l3vpn On Huawei Routers PDFDocument9 pagesMpls l3vpn On Huawei Routers PDFAli AzanNo ratings yet
- Hillstone All Series Device Troubleshooting and Debug GuideDocument134 pagesHillstone All Series Device Troubleshooting and Debug GuideWAMS FILE100% (1)
- Configuring VXLAN BGP EVPN 1638491341Document13 pagesConfiguring VXLAN BGP EVPN 1638491341Navid NaeimiNo ratings yet
- Lab 8 5 2bDocument6 pagesLab 8 5 2bsilindeanNo ratings yet
- 01 Ospf ConfigDocument21 pages01 Ospf Configgabi_marisNo ratings yet
- Verifying NAT Operation and Basic NAT TroubleshootingDocument10 pagesVerifying NAT Operation and Basic NAT TroubleshootingcsystemsNo ratings yet
- NAT Virtual InterfaceDocument14 pagesNAT Virtual InterfaceitacquaNo ratings yet
- 28.1.5 Lab - Use RESTCONF To Access An IOS XE DeviceDocument16 pages28.1.5 Lab - Use RESTCONF To Access An IOS XE DeviceTorres C.No ratings yet
- 6.2.3.10 Lab - Troubleshooting Multiarea OSPFv2 and OSPFv3Document11 pages6.2.3.10 Lab - Troubleshooting Multiarea OSPFv2 and OSPFv3SeptimanjaniNo ratings yet
- Debug Commands - NewDocument36 pagesDebug Commands - Newshank26No ratings yet
- SOP For Cisco Router TroubleshootDocument13 pagesSOP For Cisco Router TroubleshootHeera Singh100% (1)
- CCNP RouteDocument65 pagesCCNP RouteMashud Ashraf BarbhuiyaNo ratings yet
- EzVPN, Configure, TroubleshootDocument13 pagesEzVPN, Configure, TroubleshootAlviso1No ratings yet
- Cisco Exploration 2Document8 pagesCisco Exploration 2amjikbookNo ratings yet
- Howto Openbsd-Queuing v4.0.0Document10 pagesHowto Openbsd-Queuing v4.0.0tiemenwerkman3540No ratings yet
- Jncis-Sec (Nat) - My Tech Notes & JuniperDocument7 pagesJncis-Sec (Nat) - My Tech Notes & JuniperlatheeshttNo ratings yet
- Lab 7-Static IPv4 and IPv6Document7 pagesLab 7-Static IPv4 and IPv6Kanwar ZainNo ratings yet
- Hillstone All Series Device Troubleshooting and Debug GuideDocument128 pagesHillstone All Series Device Troubleshooting and Debug GuideArief FadilahNo ratings yet
- ASLogDocument6 pagesASLogLucian MormogeacNo ratings yet
- CISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkFrom EverandCISCO PACKET TRACER LABS: Best practice of configuring or troubleshooting NetworkNo ratings yet
- LEARN MPLS FROM SCRATCH PART-B: A Beginners guide to next level of networkingFrom EverandLEARN MPLS FROM SCRATCH PART-B: A Beginners guide to next level of networkingNo ratings yet
- Network with Practical Labs Configuration: Step by Step configuration of Router and Switch configurationFrom EverandNetwork with Practical Labs Configuration: Step by Step configuration of Router and Switch configurationNo ratings yet
- WAN TECHNOLOGY FRAME-RELAY: An Expert's Handbook of Navigating Frame Relay NetworksFrom EverandWAN TECHNOLOGY FRAME-RELAY: An Expert's Handbook of Navigating Frame Relay NetworksNo ratings yet
- 10-Security-Threat-Modeling (Noppa)Document19 pages10-Security-Threat-Modeling (Noppa)dont4getNo ratings yet
- Network Engineer Resume Profile - Hire IT People 3Document1 pageNetwork Engineer Resume Profile - Hire IT People 3PRAGNA DXNo ratings yet
- Telecommunication Network Lecture NotesDocument51 pagesTelecommunication Network Lecture Notesmuhabamohamed21No ratings yet
- Speech Coding TechniquesDocument38 pagesSpeech Coding TechniquesAhmedNo ratings yet
- ARM920T-based Microcontroller AT91RM9200: FeaturesDocument41 pagesARM920T-based Microcontroller AT91RM9200: Featuresnskprasad89No ratings yet
- Cyber Security PresentationDocument11 pagesCyber Security PresentationAncddddNo ratings yet
- Cooperative Ambient Backscatter System A Symbiotic Radio Paradigm For Passive IoTDocument4 pagesCooperative Ambient Backscatter System A Symbiotic Radio Paradigm For Passive IoTsaiprudhvi000No ratings yet
- 01 GSM BSS Network KPI (MOS) Optimization ManualDocument37 pages01 GSM BSS Network KPI (MOS) Optimization ManualHossein NazariNo ratings yet
- USB Performance Analysis of Bulk TrafficDocument50 pagesUSB Performance Analysis of Bulk TrafficNeneFINo ratings yet
- Junos Space Security DirectorDocument346 pagesJunos Space Security DirectorZhivko GeorgievNo ratings yet
- Atsam4l PDFDocument1,207 pagesAtsam4l PDFBárbara CastilhoNo ratings yet
- High RTWP 3GDocument3 pagesHigh RTWP 3GHTMNo ratings yet
- Brochure SRT 4930L - enDocument2 pagesBrochure SRT 4930L - ensanitahir100% (1)
- Isilon Adminstration and ManagementDocument589 pagesIsilon Adminstration and ManagementrakeshNo ratings yet
- BSSPAR1: Chapter 10 Multi-BCF and Common BCCH: RN2010AEN14GLN0Document22 pagesBSSPAR1: Chapter 10 Multi-BCF and Common BCCH: RN2010AEN14GLN0sabagh_55No ratings yet
- Causes & CountersDocument186 pagesCauses & CountersMuhammad Bilal JunaidNo ratings yet
- NS2Document11 pagesNS2Nikumani ChoudhuryNo ratings yet
- SPO 1400 Basic Commissioning and Basic Operation 3Document11 pagesSPO 1400 Basic Commissioning and Basic Operation 3farzad.aminzadeNo ratings yet
- 02 Huawei RAN KPI & Counter R12Document28 pages02 Huawei RAN KPI & Counter R12Maman SuryamanNo ratings yet
- Abcom Ipbox 9000 HD Plus: HDTV Via DVB-S, Dvb-S2, DVB-C or DVB-TDocument5 pagesAbcom Ipbox 9000 HD Plus: HDTV Via DVB-S, Dvb-S2, DVB-C or DVB-TAlexander WieseNo ratings yet
- Home AutomationDocument18 pagesHome AutomationSahil PundNo ratings yet
- @@TETRA ReferencesDocument18 pages@@TETRA ReferencesmicrajacutNo ratings yet
- PLP-High Speed Optical PHY Product Selection Guide-BC-0605EN - 030322 - FinalDocument3 pagesPLP-High Speed Optical PHY Product Selection Guide-BC-0605EN - 030322 - FinalMohammad ShNo ratings yet
- Seminar Automatic Meter Reading SystemDocument4 pagesSeminar Automatic Meter Reading SystemManu Krishnan100% (1)
- Asr 903 RSPDocument8 pagesAsr 903 RSPnitesh dayamaNo ratings yet
- Intro To UartsDocument23 pagesIntro To UartsSainadh Yerrapragada100% (1)
- Sepura Terminals InsightDocument20 pagesSepura Terminals InsightDyego FelixNo ratings yet