0 ratings0% found this document useful (0 votes)
15 viewsCNS Unit-III
CNS Unit-III
Uploaded by
Radha RaniThe document discusses principles of public-key cryptosystems. It explains that public-key encryption uses a pair of keys - a public key for encryption and a private key for decryption. It also discusses key components like plaintext, ciphertext, encryption and decryption algorithms. Additionally, it covers uses of public-key cryptosystems like encryption, digital signatures and key exchange. Specific public-key cryptosystems like RSA are explained along with concepts like key management and distribution.
Copyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
CNS Unit-III
CNS Unit-III
Uploaded by
Radha Rani0 ratings0% found this document useful (0 votes)
15 views41 pagesThe document discusses principles of public-key cryptosystems. It explains that public-key encryption uses a pair of keys - a public key for encryption and a private key for decryption. It also discusses key components like plaintext, ciphertext, encryption and decryption algorithms. Additionally, it covers uses of public-key cryptosystems like encryption, digital signatures and key exchange. Specific public-key cryptosystems like RSA are explained along with concepts like key management and distribution.
Copyright
© © All Rights Reserved
Available Formats
PDF, TXT or read online from Scribd
Share this document
Did you find this document useful?
Is this content inappropriate?
The document discusses principles of public-key cryptosystems. It explains that public-key encryption uses a pair of keys - a public key for encryption and a private key for decryption. It also discusses key components like plaintext, ciphertext, encryption and decryption algorithms. Additionally, it covers uses of public-key cryptosystems like encryption, digital signatures and key exchange. Specific public-key cryptosystems like RSA are explained along with concepts like key management and distribution.
Copyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
Download as pdf or txt
0 ratings0% found this document useful (0 votes)
15 views41 pagesCNS Unit-III
CNS Unit-III
Uploaded by
Radha RaniThe document discusses principles of public-key cryptosystems. It explains that public-key encryption uses a pair of keys - a public key for encryption and a private key for decryption. It also discusses key components like plaintext, ciphertext, encryption and decryption algorithms. Additionally, it covers uses of public-key cryptosystems like encryption, digital signatures and key exchange. Specific public-key cryptosystems like RSA are explained along with concepts like key management and distribution.
Copyright:
© All Rights Reserved
Available Formats
Download as PDF, TXT or read online from Scribd
Download as pdf or txt
You are on page 1of 41
Unit-III
Principles of Public –Key Cryptosystems
Public-key encryption scheme has six ingredients
1. Plaintext: readable message or data
2. Encryption algorithm: performs various transformations on
the plaintext.
3. Public and private keys: pair of keys, one is used for
encryption, the other is used for decryption.
4. Ciphertext: scrambled message
5. Decryption algorithm: accepts the ciphertext and the
matching key and produces the original plaintext.
Public Key Encryption
Authentication
Public-Key Cryptosystem: Secrecy
Public-Key Cryptosystem: Authentication
Classification of uses of public-key
cryptosystems
1. Encryption/Decryption
2. Digital Signature
3. Key exchange
RSA – Rivest-Shamir-Adleman
Block cipher
Plaintext and ciphertext are integers between 0 and n - 1
for some n.
A typical size for n is 1024 bits, that is, n is less than 21024
Block size is I bits, where 2i < n ≤ 2i+1
Plaintext block M and ciphertext block C
C = Me mod n
M = Cd mod n
RSA Algorithm
RSA Example
For this example, the keys were generated as follows
1. Select two prime numbers, p = 17 and q = 11
2. Calculate n = pq = 17 × 11 = 187
3. Calculate Φ (n) = (p - 1)(q - 1) = 16 × 10 = 160
4. Select e such that e is relatively prime to Φ (n) = 160 and less
than f(n); we choose e = 7
5. Determine d such that de = 1(mod 160) and d < 160 The
correct value is d = 23, because 23 × 7 = 161 = (1 × 160) + 1;
d can be calculated using the extended Euclid’s algorithm
6. The resulting keys are public key PU = {7, 187} and private key
PR = {23, 187}
For encryption, we need to calculate C = 887 mod 187
For decryption, we calculate M = 1123 mod 187
Key Management
The distribution of public keys
The use of public-key encryption to distribute secret keys
Distribution of public keys
1. Public announcement
2. Publicly available directory
3. Public-key authority
4. Public-key certificates
1. Public announcement
Participant can send his or her public key to any other
participant or broadcast the key to the community at
large
Convenient but Anyone can forge such a public
announcement and pretend to be user A and send a
public key to another participant or broadcast such a
public key
2. Publicly available directory
The authority maintains a directory with a {name, public
key} entry for each participant.
Each participant registers a public key with the directory
authority.
Registration is in person/secure authenticated communication.
A participant may replace the existing key with a new one
at any time
Participants could also access the directory electronically.
3. Public-key authority
1. A sends a timestamped message to the public-key authority
containing a request for the current public key of B.
2. The authority responds with a message that is encrypted using
the authority's private key, PRauth
B's public key, PUb which A can use to encrypt messages destined for B
The original request, to enable A to match this response
The original timestamp, so A can determine that this is not an old message
3. A stores B's public key and also uses it to encrypt a message to B
containing an identifier of A (IDA) and a nonce (N1), which is used
to identify this transaction uniquely.
4. B retrieves A's public key from the authority in the same manner
as A retrieved B's public key.
6. B sends a message to A encrypted with PUa and containing A's
nonce (N1) as well as a new nonce generated by B (N2)
presence of N1 in message assures A that the correspondent is B.
7. A returns N2, encrypted using B's public key, to assure B that its
correspondent is A.
3. Public-key authority
4. Public-key certificates
Use certificates that can be used by participants to exchange
keys without contacting a public-key authority
Certificate consists of a public key plus an identifier of the key
owner, with the whole block signed by a trusted third party.
The third party is a certificate authority, such as a government agency or
a financial institution, that is trusted by the user community
A user can present his or her public key to the authority in a secure
manner, and obtain a certificate
The user can then publish the certificate
Anyone needed this user's public key can obtain the certificate and
verify that it is valid by way of the attached trusted signature
A participant can also convey its key information to another by
transmitting its certificate
Other participants can verify that the certificate was created by the
authority
Public-key certificates
Simple Secret Key Distribution
1. A generates a public/private key pair {PUa, PRa} and
transmits a message to B consisting of Pua and an identifier
of A, IDA.
2. B generates a secret key, Ks, and transmits it to A,
encrypted with A's public key.
3. A computes D(PRa, E(PUa, Ks)) to recover the secret key.
Because only A can decrypt the message, only A and B will
know the identity of Ks.
4. A discards PUa and PRa and B discards PUa.
Diffie-Hellman Key Exchange
Diffie-Hellman Key Exchange
Authentication Requirements
Attacks identified are
1. Disclosure
2. Traffic analysis
3. Masqurade
4. Content modification
5. Sequence modification
6. Timing modification
7. Source repudiation
8. Destination repudiation
Measures to deal with items 3 through 6 in the foregoing list are
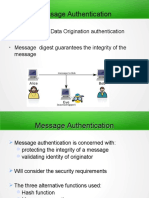
generally regarded as message authentication.
Message authentication is a procedure to verify that received
messages come from the alleged source and have not been altered.
Message authentication may also verify sequencing and timeliness.
Authentication Functions
Any message authentication or digital signature
mechanism has two levels of functionality.
At the lower level, there must be some sort of function
that produces an authenticator: a value to be used to
authenticate a message.
This lower-level function is then used as a primitive in a
higher-level authentication protocol that enables a
receiver to verify the authenticity of a message.
Authentication Functions
Functions that may be used to produce an authenticator.
These may be grouped into three classes
1. Message encryption: The ciphertext of the entire message
serves as its authenticator
2. Message authentication code (MAC): A function of the
message and a secret key that produces a fixed-length value
that serves as the authenticator
3. Hash function: A function that maps a message of any length
into a fixed-length hash value, which serves as the
authenticator
1. Authentication Functions: Message
Encryption
2. Authentication Functions: MAC
Message authentication
2. Authentication Functions: MAC
Message authentication and confidentiality: authentication
tied to plaintext
2. Authentication Functions: MAC
Message authentication and confidentiality: authentication
tied to ciphertext
3. Authentication Functions: Hash Functions
Variety of ways in which a hash code can be used to
provide message authentication
1. The message plus concatenated hash code is encrypted
using symmetric encryption.
2. Only the hash code is encrypted, using symmetric
encryption
3. Authentication Functions: Hash Functions
3. Only the hash code is encrypted, using public-key
encryption and using the sender's private key.
4. If confidentiality as well as a digital signature is desired,
then the message plus the private-key encrypted hash
code can be encrypted using a symmetric secret key.
3. Authentication Functions: Hash Functions
5. It is possible to use a hash function but no encryption
for message authentication.
6. Confidentiality can be added to the approach of (5) by
encrypting the entire message plus the hash code.
Message Authentication Codes
A MAC, also known as a cryptographic checksum, is
generated by a function C of the form
MAC = C(K, M)
where
M is a variable-length message,
K is a secret key shared only by sender and receiver, and
C(K,M) is the fixed-length authenticator.
The MAC is appended to the message at the source at a time
when the message is assumed or known to be correct.
The receiver authenticates that message by recomputing
the MAC.
Requirements of MACs
MAC function should satisfy the following requirements:
If an opponent observes M and C(K, M), it should be
computationally infeasible for the opponent to construct a
message M' such that C(K, M') = C(K, M).
C(K, M) should be uniformly distributed in the sense that for
randomly chosen messages, M and M', the probability that C(K, M)
= C(K, M') is 2n, where n is the number of bits in the MAC.
Let M' be equal to some known transformation on M. That is, M' =
f(M). For example, f may involve inverting one or more specific
bits. In that case, Pr[C(K, M) = C(K, M')] = 2n.
Hash Functions
A hash value h is generated by a function H of the form
h = H(M)
where
M is a variable-length message and
H(M) is the fixed-length hash value.
The hash value is appended to the message at the source
at a time when the message is assumed or known to be
correct.
The receiver authenticates that message by recomputing
the hash value. Because the hash function itself is not
considered to be secret, some means is required to
protect the hash value
Security of Hash Functions and Macs
As with symmetric and public-key encryption, we can
group attacks on hash functions and MACs into two
categories:
1. Brute-force attacks and
2. Cryptanalysis
Security of Hash Functions and Macs
Brute-Force Attacks
Hash Functions
The strength of a hash function against brute-force attacks depends
solely on the length of the hash code produced by the algorithm.
Message Authentication Codes
A brute-force attack on a MAC is a more difficult undertaking
because it requires known message-MAC pairs.
Cryptanalysis
The way to measure the resistance of a hash or MAC algorithm
to cryptanalysis is to compare its strength to the effort
required for a brute-force attack.
That is, an ideal hash or MAC algorithm will require a
cryptanalytic effort greater than or equal to the brute-force
effort.
Digital Signatures
Message authentication protects two parties who exchange messages
from any third party.
However, it does not protect the two parties against each other.
Several forms of dispute between the two are possible.
Suppose that John sends an authenticated message to Mary,
Consider the following disputes that could arise:
1. Mary may forge a different message and claim that it came from
John. Mary would simply have to create a message and append an
authentication code using the key that John and Mary share.
2. John can deny sending the message. Because it is possible for Mary
to forge a message, there is no way to prove that John did in fact
send the message.
In situations where there is not complete trust between
sender and receiver, something more than authentication is
needed.
Digital Signatures
Solution to this problem is the digital signature
It has the following properties:
It must verify the author and the date and time of the
signature.
It must to authenticate the contents at the time of the
signature.
It must be verifiable by third parties, to resolve disputes.
Thus, the digital signature function includes the
authentication function
Requirements of digital signature
The signature must be a bit pattern that depends on the
message being signed.
The signature must use some information unique to the
sender, to prevent both forgery and denial.
It must be relatively easy to produce the digital signature.
It must be relatively easy to recognize and verify the digital
signature.
It must be computationally infeasible to forge a digital
signature, either by constructing a new message for an existing
digital signature or by constructing a fraudulent digital
signature for a given message.
It must be practical to retain a copy of the digital signature in
storage.
Digital Signature Process
Two approaches to Digital Signatures
You might also like
- Unit 3 - Part 1 - MACDocument8 pagesUnit 3 - Part 1 - MACsumit morNo ratings yet
- IS - Message Authentication and Hash Functions - 06012015 - 043853AMDocument16 pagesIS - Message Authentication and Hash Functions - 06012015 - 043853AMAbhishek DaveNo ratings yet
- Unit Ii NSDocument26 pagesUnit Ii NSpavinivi27No ratings yet
- cns3 2Document11 pagescns3 2gadidheerajreddy.20.itNo ratings yet
- Network Security Lec 11 (Message Authentication & Hash Functions)Document36 pagesNetwork Security Lec 11 (Message Authentication & Hash Functions)RohFollowerNo ratings yet
- Cns Unit 4 PortalDocument18 pagesCns Unit 4 Portalaravind aravindNo ratings yet
- cns4 1Document12 pagescns4 1gadidheerajreddy.20.itNo ratings yet
- 91542Document16 pages91542logesswari srinivasanNo ratings yet
- Authentication and Hash FunctionDocument14 pagesAuthentication and Hash Functionvaibhavkirar459No ratings yet
- Authentication RequirementsDocument7 pagesAuthentication Requirementssrishtigaikwad19No ratings yet
- CNS Unit 3Document15 pagesCNS Unit 3LOGESH WARAN PNo ratings yet
- Unit - 4 Notes1Document57 pagesUnit - 4 Notes1shaikkhaderbasha2002No ratings yet
- Unit - Iii Authentication: DisclosureDocument18 pagesUnit - Iii Authentication: DisclosureJenny RapperNo ratings yet
- Answer ShrutiDocument6 pagesAnswer ShrutiShruti KapoorNo ratings yet
- Unit-III Digital Signature and AuthenticationDocument27 pagesUnit-III Digital Signature and Authenticationvishnuramrk123No ratings yet
- Module 2Document75 pagesModule 2John VeigasNo ratings yet
- Network Security (Key Management)Document27 pagesNetwork Security (Key Management)RohFollowerNo ratings yet
- Unit-III Digital Signature and AuthenticationDocument25 pagesUnit-III Digital Signature and Authenticationvishnuramrk123No ratings yet
- Unit V CryptoDocument8 pagesUnit V CryptoPriya SNo ratings yet
- Network Security UNIT 2Document30 pagesNetwork Security UNIT 2smitcse2021No ratings yet
- Authentication FunctionsDocument4 pagesAuthentication FunctionsRahul JainNo ratings yet
- CNS Unit 4 NewDocument55 pagesCNS Unit 4 NewChandra BNo ratings yet
- Key Management and DistributionDocument38 pagesKey Management and Distributionabb acNo ratings yet
- Public-Key Cryptography and Message Authentication: Cryptographicandnetwork Security Chapter-3 MessageauthenticationDocument27 pagesPublic-Key Cryptography and Message Authentication: Cryptographicandnetwork Security Chapter-3 MessageauthenticationZoe KhanNo ratings yet
- DocxDocument3 pagesDocxMOUMITA BHATTACHARJEENo ratings yet
- Crime EXTRADocument7 pagesCrime EXTRArohankumar5471No ratings yet
- UNIT 4 NotesDocument74 pagesUNIT 4 Notes4013-Aslin Dhurai CNo ratings yet
- Public Announcement of Public KeysDocument33 pagesPublic Announcement of Public KeysPathak PayhakNo ratings yet
- Unit 3 FreeDocument22 pagesUnit 3 Freeshastiraaj25No ratings yet
- Unit 4 Cryptographic Hash Functions and Digital SignatureDocument118 pagesUnit 4 Cryptographic Hash Functions and Digital Signatureshrestharojesh34No ratings yet
- Public Key-Crypto SystemDocument44 pagesPublic Key-Crypto SystemAnkit RajNo ratings yet
- 3CP01 BVM Notes 2Document18 pages3CP01 BVM Notes 2050tk1krpcNo ratings yet
- YourpptDocument17 pagesYourpptArpithaChamanNo ratings yet
- Is Unit 3 PPT - Part 1Document123 pagesIs Unit 3 PPT - Part 1sheikh Riyaz ul haqNo ratings yet
- Unit 4 (MAC)Document32 pagesUnit 4 (MAC)Tisha NimjeNo ratings yet
- CNS Mid2Document9 pagesCNS Mid2kiranyadav3304No ratings yet
- ECEG-6530 Computer (And Network) Security: Message Integrity, Message Authentication Codes, Signature SchemesDocument190 pagesECEG-6530 Computer (And Network) Security: Message Integrity, Message Authentication Codes, Signature SchemesAbrham GidayNo ratings yet
- Message Authentication CodeDocument6 pagesMessage Authentication CodeAyush KastNo ratings yet
- Lecture - 16 - To 18 - Mac Hash Hmac RsaDocument37 pagesLecture - 16 - To 18 - Mac Hash Hmac Rsasyedrouhanali7No ratings yet
- Unit 3Document226 pagesUnit 3Rohit KoliNo ratings yet
- Network Security (10ec832) : 8th E&CDocument42 pagesNetwork Security (10ec832) : 8th E&CbadboyNo ratings yet
- Lecture 5Document41 pagesLecture 5yeabsiramulualemNo ratings yet
- DCN Unit4Document36 pagesDCN Unit4sandipgawali.mca23No ratings yet
- Module 3 Module 5Document32 pagesModule 3 Module 5TEJASWINI PNo ratings yet
- U-3 CryptoDocument17 pagesU-3 Cryptovinayakvyas7489No ratings yet
- Unit 4. Cryptography and Network Security: Introduction To CryptographyDocument11 pagesUnit 4. Cryptography and Network Security: Introduction To CryptographyVanam AkhilaNo ratings yet
- Exercises 4 (Repaired)Document4 pagesExercises 4 (Repaired)Yoge AndranNo ratings yet
- Cns Unit 3Document35 pagesCns Unit 3hafeezaNo ratings yet
- CBS 416 Assigment SolutionDocument8 pagesCBS 416 Assigment SolutionKuye DamilareNo ratings yet
- Lecture 5Document10 pagesLecture 5AHMED DARAJNo ratings yet
- Computer Network System - IiiDocument29 pagesComputer Network System - IiiSriram SudheerNo ratings yet
- Network Security MACDocument55 pagesNetwork Security MACraj858778No ratings yet
- Asymmetric CryptoDocument6 pagesAsymmetric CryptoAbdulrahman BadeebNo ratings yet
- ASSIGNMENTDocument2 pagesASSIGNMENTNoeme Bichayda BeltranNo ratings yet
- Key ManagementDocument24 pagesKey ManagementSubhiAlkourdeNo ratings yet
- Unit - 2 Part 1 - CNSDocument44 pagesUnit - 2 Part 1 - CNSPushkal KS VaidyaNo ratings yet
- CH 11Document28 pagesCH 11naseriikramudin63No ratings yet
- Cns 3Document40 pagesCns 3gbharothhNo ratings yet
- CISA EXAM-Testing Concept-Digital SignatureFrom EverandCISA EXAM-Testing Concept-Digital SignatureRating: 3.5 out of 5 stars3.5/5 (5)
- PANDA-MINER White PaperDocument42 pagesPANDA-MINER White PaperYuiitsu WintNo ratings yet
- Crypto 2Document10 pagesCrypto 2John QuintalNo ratings yet
- Cryptography & Protocols: Presented By: Dr. S. S. Bedi Department of CSIT, MJP Rohilkhsnd University, BareillyDocument59 pagesCryptography & Protocols: Presented By: Dr. S. S. Bedi Department of CSIT, MJP Rohilkhsnd University, BareillyShreya YadavNo ratings yet
- DocumentDocument56 pagesDocumentJaya SwaroopNo ratings yet
- 4 Key Exchange 1Document34 pages4 Key Exchange 1Yosia RayaNo ratings yet
- Ethics, Computer Crime, and Security: Unit - 5Document17 pagesEthics, Computer Crime, and Security: Unit - 5MD KamaalNo ratings yet
- Creating Hbase Cluster and Replication On AwsDocument30 pagesCreating Hbase Cluster and Replication On AwspinkpantherpremNo ratings yet
- CS5460 ChadMaughan Assignment4Document3 pagesCS5460 ChadMaughan Assignment4the_tigdraNo ratings yet
- Thesis - Jovanovic 2Document216 pagesThesis - Jovanovic 2GahanNo ratings yet
- Encryption and Its Application To E-CommerceDocument13 pagesEncryption and Its Application To E-CommerceAk KumarNo ratings yet
- Cyber Laws-Unit1Document68 pagesCyber Laws-Unit1Kartiki DeshmukhNo ratings yet
- Cryptography, Network Security and Cyber Laws Notes 2019-2020Document26 pagesCryptography, Network Security and Cyber Laws Notes 2019-2020Himanshu KumarNo ratings yet
- Oral Presentation Mod IDEA June 7 2019 2Document46 pagesOral Presentation Mod IDEA June 7 2019 2Rensel RicohermosoNo ratings yet
- Pkcs 7Document29 pagesPkcs 7tranchihuuNo ratings yet
- Frontex PDFDocument51 pagesFrontex PDFIsis VioletaNo ratings yet
- Merchant Integration Guide 2.6Document50 pagesMerchant Integration Guide 2.6ipsoundNo ratings yet
- Unit VDocument17 pagesUnit VVanukuri Gopi ReddyNo ratings yet
- CryptographyDocument21 pagesCryptographyinamdaramena4No ratings yet
- Chapter 5 - Basic CryptographyDocument59 pagesChapter 5 - Basic CryptographymaryaNo ratings yet
- MIPS Based On AESDocument5 pagesMIPS Based On AESSehar ChNo ratings yet
- Project Report For Advanced Encryption System - CompltedDocument90 pagesProject Report For Advanced Encryption System - Compltedshaki_shakkira75% (8)
- IBMcryptoDocument4 pagesIBMcryptorikcurlNo ratings yet
- Diffie HelmanDocument15 pagesDiffie HelmanManal MustafaNo ratings yet
- Enterprise Information Security-12Document10 pagesEnterprise Information Security-12Guillermo ValdèsNo ratings yet
- CISSP Student Guide V2.0Document913 pagesCISSP Student Guide V2.0thetzo83% (6)
- 30 Assignment4 PDFDocument12 pages30 Assignment4 PDFRaghu NangunuriNo ratings yet
- CryptographyDocument3 pagesCryptographyJaymar ChavezNo ratings yet
- CS L03 OSSecurity Rootkits 1598712884023 PDFDocument37 pagesCS L03 OSSecurity Rootkits 1598712884023 PDFamitNo ratings yet
- Unit 1 CSSDocument18 pagesUnit 1 CSS116TanzeelNo ratings yet
- Improving Privacy and Security in Multi-Authority Attribute-Based EncyptionDocument12 pagesImproving Privacy and Security in Multi-Authority Attribute-Based Encyptionselva kumarNo ratings yet