InTech December 2021 - 14
InTech December 2021 - 14
Uploaded by
kaicyemCopyright:
Available Formats
InTech December 2021 - 14
InTech December 2021 - 14
Uploaded by
kaicyemOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Copyright:
Available Formats
InTech December 2021 - 14
InTech December 2021 - 14
Uploaded by
kaicyemCopyright:
Available Formats
CONNECTIVITY AND CYBERSECURITY
At the same time, a new challenge will onto the radar of profiteering hackers, mental stages: endpoint security, cyber-
emerge: How does the factory avoid providing channels to invade systems security, and security management.
obstructing OT control data transmis- or disrupt operations. With cyberat- To enhance OT data security capabil-
sion with the addition of IT data? tacks becoming common, data se- ity, industrial firms should:
Why is this a concern? It is because curity and cybersecurity are emerg- • Apply intrusion protection system
industrial Ethernet networks, the most- ing as required items on every digital (IPS) technology to OT automation
used industrial networks, do not have transformation agenda. To safeguard devices to secure critical infrastruc-
real-time control mechanisms for mass production capacity and keep produc- ture. An industrial-grade IPS moni-
data. The proposed solution has been tion lines safe from data-tampering at- tors data flowing in and out of critical
to have two separate networks for send- tempts, companies must pay attention devices, segregates malicious traffic,
ing images and control commands. The to OT data security. and notifies administrators the instant
advantage is the two streams of data do an anomaly is detected.
not compete for network bandwidth; the • Take advantage of network layering
disadvantage is the cost of network im-
Time-sensitive networking to curb ransomware attacks. Firms
plementation and maintenance doubles. (TSN), the new-generation will benefit from upgrading their
Time-sensitive networking (TSN), the Ethernet switches to managed Ether-
new-generation Ethernet, is designed to
Ethernet, is designed to net switches and activating the layer-
schedule transmissions according to the schedule transmissions ing feature to divide an OT network
importance of the data, ensuring impor- into segments.
tant data reaches the device at the sched-
according to the importance • Use network management software to
uled time. This is what robust OT data of the data, ensuring overcome the interoperability hurdles
transmission capability entails. among various OT communication
In addition, environmental distur-
important data reaches protocols to effectively spot faulty or
bances, such as extreme temperatures the device at the sched- risky devices via visualization.
or electromagnetic waves generated
during the startup of a device, can
uled time. This is what Use the four OT data capabilities
cause network disruptions and the po- robust OT data transmis- As the old saying goes, do not put the
tential for data to be lost. Contingency cart before the horse. It is critical to
plans should be made for all kinds of
sion capability entails. get your priorities straight in industrial
incidents to avoid losing data in transit digital transformation. Do not let poor-
during disturbances. A misconception among businesses quality raw data undermine the results
As an illustration, when a wired or is that mature IT security solutions of your big data analyses.
wireless network is down, the network can be directly replicated in the OT Before trying to source OT data, con-
backup mechanism can immediately world. In reality, security tools meant sider where you are in terms of data ac-
activate another section to resume for IT environments are not entirely quisition, data preparation, data trans-
transmission. Or, when the network is fit for OT system protection. For ex- mission, and data security. Armed with
temporarily congested or disconnect- ample, because OT devices do not run these four capabilities, you will be able
ed, a certain amount of the latest data the operating systems compatible with to tackle the challenges head on and
can be stored locally to ensure the data, antivirus software, installing it on OT leverage high-quality OT data to lay a
if lost, will be retransmitted or retrieved systems is out of the question. Further solid foundation for transformation. n
to avoid delivering fragmented data. complicating the antivirus situation is
the importance of capacity availability
Challenge: Vulnerable data in OT environments; the fear that pro- ABOUT THE AUTHOR
OT data becomes not trustworthy duction capacity will be hurt by data Oliver Wang
mostly from cybersecurity issues. In packets being wrongfully blocked has ( w w w. l i n k e d i n .
the past, OT systems did not need to kept many machines away from anti- c o m / i n / o l i v e r-
be Internet connected and could be virus software solutions. wang-6873a329)
protected simply through physical Another OT data security issue is the is product mar-
controls, such as limiting access to an fact that many manufacturers have de- keting manager,
operational area or banning the use of ployed all devices on the same intranet edge connectivity
USB sticks and personal computers. As for the sake of connection stability and and computing, for
industrial digital transformation takes convenience. However, once ransom- Moxa, where he has worked for more
off, Internet access becomes essential. ware breaks into that environment, it than 15 years. Wang has a degree from
With increased connectivity, all vul- can easily spread throughout the entire the University of California, Berkeley.
nerabilities are suddenly laid bare to system. It is thus recommended to se- Access Moxa’s library of white papers at
ruthless computer viruses or thrust cure OT environments in three incre- https://moxa.com/en/case-studies.
WWW.ISA.ORG INTECH DECEMBER 2021 27
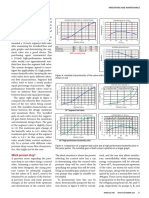
A worksheet that calculates control valve
installed gain can be part of any control valve
selection process.
F
By Jon F. Monsen, or many years, the author has used, This article explains how to use control valve in-
PhD, PE and promoted the use of, control valve stalled gain calculations.
installed flow and gain graphs as part Figure 1 is an example of a properly sized valve
of the control valve selection process (references compared to an oversized valve. One valve man-
1–3). For all those years, the author has had the ufacturer suggests the following gain criteria for
benefit of being associated with a valve manu- installed gain within the specified flow range:
facturer with a publicly available control valve- • Gain > 0.5
sizing application that included installed flow • Gain < 3.0
and gain graphing capability. Users who pre- • As constant as possible
ferred other brands of control valves, and thus • As close to 1.0 as possible
those manufacturers’ control valve-sizing applica- • Gain (max) / Gain (min) < 2.0.
tions, were hesitant to learn to use a new applica- Extremely low gains are undesirable, because
tion to take advantage of the graphing capability. a low gain means when the valve moves, the
Recently, the author published an article that flow does not change by much. It might not be
included detailed instructions for constructing a as obvious why high gains are undesirable. An
Microsoft Excel worksheet (www.control-valve- audio amplifier with a high gain may be desir-
application-tools.com) that generates installed able. But control valves are mechanical devices,
flow and gain graphs in conjunction with valve- and parts that move while in contact with each
sizing calculations made with any valve-sizing other tend to stick when not moving. If a valve,
application. This makes it practical for anyone because it tends to stick when not moving, can
to incorporate graphing installed flow and gain only be positioned within 2 percent of the desired
into their valve selection process (reference 4). position and has a gain of 4, the flow can only
28 INTECH DECEMBER 2021 WWW.ISA.ORG
You might also like
- Using-ISA - IEC-62443-Standards-WP-v1.2 - Establishing Conduits and Zones (May 2014)No ratings yetUsing-ISA - IEC-62443-Standards-WP-v1.2 - Establishing Conduits and Zones (May 2014)12 pages
- Securing Operational Technology: What Is Operational Technology? What Are The Risks?No ratings yetSecuring Operational Technology: What Is Operational Technology? What Are The Risks?9 pages
- Tech Trend Notes: High-Reflect Ance, Dielectric Mirrors Real T Ime Intrusion DetectionNo ratings yetTech Trend Notes: High-Reflect Ance, Dielectric Mirrors Real T Ime Intrusion Detection9 pages
- Toward A Multi-Agent System Architecture For Insight Amp Cybersecurity in Cyber-Physical NetworksNo ratings yetToward A Multi-Agent System Architecture For Insight Amp Cybersecurity in Cyber-Physical Networks5 pages
- A Water Pumping Control System With A Programmable Logic Controller (PLC) PDFNo ratings yetA Water Pumping Control System With A Programmable Logic Controller (PLC) PDF8 pages
- Moxa White Paper - Overcoming Obstacles of Industrial Network ManagementNo ratings yetMoxa White Paper - Overcoming Obstacles of Industrial Network Management9 pages
- An Improved Intrusion Prevention Sytem For Wlan: S V Athawale MapundNo ratings yetAn Improved Intrusion Prevention Sytem For Wlan: S V Athawale Mapund3 pages
- Approach To Auditing Network Security: by S. Anantha SayanaNo ratings yetApproach To Auditing Network Security: by S. Anantha Sayana3 pages
- Rita Secure Communication Protocol: Application To ScadaNo ratings yetRita Secure Communication Protocol: Application To Scada12 pages
- Data Centre Monitoring and Management: e BookNo ratings yetData Centre Monitoring and Management: e Book14 pages
- Why Enterprises Need More Than Firewalls and Intrusion Detection SystemsNo ratings yetWhy Enterprises Need More Than Firewalls and Intrusion Detection Systems6 pages
- Automated Dynamic Firmware Analysis at Scale - A Case Study On Embedded Web InterfacesNo ratings yetAutomated Dynamic Firmware Analysis at Scale - A Case Study On Embedded Web Interfaces12 pages
- Efficient Security For Desktop Data Grid Using Cryptographic ProtocolNo ratings yetEfficient Security For Desktop Data Grid Using Cryptographic Protocol6 pages
- Using ANSI ISA 99 Standards WP May 2012 PDFNo ratings yetUsing ANSI ISA 99 Standards WP May 2012 PDF11 pages
- Database Security Virtualization and Cloud v1.1!03!18 2010No ratings yetDatabase Security Virtualization and Cloud v1.1!03!18 20108 pages
- Thinklogical White Paper: That Was Then and This Is NowNo ratings yetThinklogical White Paper: That Was Then and This Is Now10 pages
- Advantages and Disadvantages of Active vs. Passive Scanning in IT and OT EnvironmentsNo ratings yetAdvantages and Disadvantages of Active vs. Passive Scanning in IT and OT Environments3 pages
- Research and Implementation of The Fault Information PDFNo ratings yetResearch and Implementation of The Fault Information PDF9 pages
- Cyber Security Issues For Protective RelaysNo ratings yetCyber Security Issues For Protective Relays27 pages
- 68.high Speed Pear To Pear Communication & ControlNo ratings yet68.high Speed Pear To Pear Communication & Control6 pages
- 11 Congestion - Control - in - Software - Defined - NetworkNo ratings yet11 Congestion - Control - in - Software - Defined - Network5 pages
- Activity 3: Roll No.-101703036 Group - COE2 Q.1 Problem Statement: A Firm Has A Setup of Manufacturing Consumable ItemsNo ratings yetActivity 3: Roll No.-101703036 Group - COE2 Q.1 Problem Statement: A Firm Has A Setup of Manufacturing Consumable Items9 pages
- Secure-Optimization-Computation-OutsourcingNo ratings yetSecure-Optimization-Computation-Outsourcing14 pages
- Wireless Sensor Network Security Thesis PDF100% (2)Wireless Sensor Network Security Thesis PDF9 pages
- Ensure Nonstop IP Surveillance With An Optimized Industrial Ethernet Network - Remote MagazineNo ratings yetEnsure Nonstop IP Surveillance With An Optimized Industrial Ethernet Network - Remote Magazine4 pages
- Benefits of 61850 - Johannesburg - Brand Et AlNo ratings yetBenefits of 61850 - Johannesburg - Brand Et Al6 pages
- ITIL Helps Keep Network Fit: Cabling InfrastructureNo ratings yetITIL Helps Keep Network Fit: Cabling Infrastructure3 pages
- Case Study Cyber Security Issues For Protective RelaysNo ratings yetCase Study Cyber Security Issues For Protective Relays27 pages
- Security Issues in SCADA Networks: Vinay M. Igure, Sean A. Laughter, Ronald D. WilliamsNo ratings yetSecurity Issues in SCADA Networks: Vinay M. Igure, Sean A. Laughter, Ronald D. Williams9 pages
- Computer Hardware & Networking Unit 03 Part INo ratings yetComputer Hardware & Networking Unit 03 Part I47 pages
- How TSN Guarantees Real-Time Communication For Digital SubstationsNo ratings yetHow TSN Guarantees Real-Time Communication For Digital Substations4 pages
- Computer Science Self Management: Fundamentals and ApplicationsFrom EverandComputer Science Self Management: Fundamentals and ApplicationsNo ratings yet
- Letters: Setting The Standard For Automation™No ratings yetLetters: Setting The Standard For Automation™1 page
- Toaz - Info Instrumentation Amp Control Knowledge Assessment Test PR - Part24No ratings yetToaz - Info Instrumentation Amp Control Knowledge Assessment Test PR - Part241 page
- Toaz - Info Instrumentation Amp Control Knowledge Assessment Test PR - Part22No ratings yetToaz - Info Instrumentation Amp Control Knowledge Assessment Test PR - Part221 page
- Industrial Control Systems Control LOW Moderate High: 5. Supplemental GuidanceNo ratings yetIndustrial Control Systems Control LOW Moderate High: 5. Supplemental Guidance20 pages
- Table Atch1-1. Example Relative Importance of Interdependent SystemsNo ratings yetTable Atch1-1. Example Relative Importance of Interdependent Systems20 pages
- How Do You Feel About Working Nights and Weekends?: HR InterviewNo ratings yetHow Do You Feel About Working Nights and Weekends?: HR Interview8 pages
- Module 1 - Concepts of Data and InformationNo ratings yetModule 1 - Concepts of Data and Information25 pages
- Microsoft Excel 2003: Foundation Level CourseNo ratings yetMicrosoft Excel 2003: Foundation Level Course41 pages
- Constraint Satisfaction Algorithms: Edition of Timetables in The License-Master-Doctorate SystemNo ratings yetConstraint Satisfaction Algorithms: Edition of Timetables in The License-Master-Doctorate System9 pages
- Cambridge IGCSE™: Information and Communication Technology 04171/31 February/March 2022No ratings yetCambridge IGCSE™: Information and Communication Technology 04171/31 February/March 202211 pages
- FS720 Fire Detection System: Commissioning Maintenance TroubleshootingNo ratings yetFS720 Fire Detection System: Commissioning Maintenance Troubleshooting122 pages
- Informe Lab52 Q1 - 2023 - EN - 23-05-2023No ratings yetInforme Lab52 Q1 - 2023 - EN - 23-05-202326 pages
- Designing Memory Array Subsystems CH 12 PDFNo ratings yetDesigning Memory Array Subsystems CH 12 PDF87 pages
- Quickspecs: HP Elitedisplay E233 23-Inch MonitorNo ratings yetQuickspecs: HP Elitedisplay E233 23-Inch Monitor10 pages
- infyQT - Python - Specialization 26th March 2021No ratings yetinfyQT - Python - Specialization 26th March 202118 pages
- Tour Guide Portfolio: Insert The Sub Title of Your Presenta-TionNo ratings yetTour Guide Portfolio: Insert The Sub Title of Your Presenta-Tion28 pages
- Mining Industry Business Plan by SlidesgoNo ratings yetMining Industry Business Plan by Slidesgo58 pages