IBM and BeyondTrust Presents: Protecting Your Sensitive Data in the Cloud
- 1. Protecting Your Sensitive Data in the Cloud Ed Bottini Global Cloud Computing Ecosystem Manager IBM Jim Zierick EVP Strategy and Corporate Development BeyondTrust June 26, 2012 © 1985-2012 BeyondTrust Software, Inc. All rights reserved
- 2. Agenda • IBM Smart Cloud Offering • The State of the Cloud • Cloud Security Best Practices • BeyondTrust Cloud Security • Next Steps • Q&A 2 © 1985-2010 BeyondTrust Software, Inc. All rights reserved
- 3. Enterprises intend for cloud to improve their business capabilities How Important are the Following Objectives for Adopting Cloud? % of Respondents Increased collaboration with external partners 62% Competitive/cost advantages thru vertical integration 57% New delivery channels/markets 56% New/enhanced revenue streams 54% Competitive differentiation thru specialization 51% Rebalanced mix of products/services 46% Flexible pricing models 43% Business Capabilities Internal Efficiencies Important or Very Important Source: 2011 IBM/EIU Cloud Survey Results, Q5: How Important are the Following Objectives for Adopting Cloud?, n= 572 3 Close to half (42%) of organizations surveyed plan to harness 3 © 2012 IBM Corporation cloud for radical business model innovation within three years
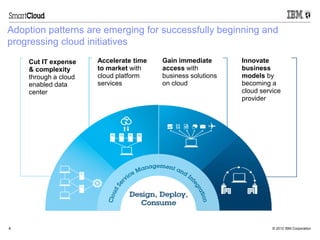
- 4. Adoption patterns are emerging for successfully beginning and progressing cloud initiatives Cut IT expense Accelerate time Gain immediate Innovate & complexity to market with access with business through a cloud cloud platform business solutions models by enabled data services on cloud becoming a center cloud service provider 4 © 2012 IBM Corporation
- 5. IBM offers clients choice of cloud delivery models… FOUNDATION SERVICES SOLUTIONS Private & Hybrid Managed Services Business Solutions Cloud Enablement Infrastructure & Platform Software & Business Technologies as a Service Process as a Service Commitment to open standards and a broad ecosystem 5 © 2012 IBM Corporation
- 6. SERVICES Client Industry Data and Workplace Security Resilience Enterprise Partner defined services analytics services services services applications services services services Application Services Application Application Application Application Integration Lifecycle Resources Environments Management Enterprise Enterprise+ Infrastructure Management Security Payment and Availability and Platform and Support Billing Performance Enterprise Enterprise Enterprise data center A B Managed private cloud Hosted private cloud Shared cloud services 6 © 2012 IBM Corporation
- 7. Transforming Application Lifecycle Management leveraging Cloud & ecosystem partner services Project Requirement Design Development Test Deployment Production Initiation Analysis Defects loaded in Rational Quality Manager and tracked Maintain through application life cycle Application Virtualization Defect Analysis Code Analysis & Reporting Mobile Device Testing Performance Testing Services Workload Portability Testing Solutions Community of Partners Application Virtualization Testing on Devices 7 © 2012 IBM Corporation
- 8. IBM has built and ecosystem to enhance our capabilities and deliver client value Cloud Application Providers Cloud Services Solution Providers Client Industry Data and Workplace Security Resilience Enterprise Partner defined services analytics services services services applications services services services Application Services Cloud Technology providers Application Application Application Application Integration Lifecycle Resources Environments Management Enterprise Enterprise+ Cloud Infrastructure Providers Infrastructure Management Security Payment Availability and Platform and Support and Billing Performance Enterprise Enterprise Enterprise data center A B Managed private cloud Hosted private Shared cloud services cloud Cloud Builders 8 © 2012 IBM Corporation
- 9. #1 Concern When Moving to the Cloud Security is the #1 concern when moving deployments to the Cloud Poneman’s Surveys concluded that: • 79% of respondents believe that being able to efficiently manage security in the cloud is critical. • 42% of respondents indicated they would not know if their organizations' cloud applications or data was compromised by a security breach or data exploit IDC Enterprise Panel Survey on Cloud challenges 9 © 1985-2010 BeyondTrust Software, Inc. All rights reserved
- 10. Top threats to Cloud Computing Per Cloud Security Alliance’s “Top Threats to Cloud Computing (March 2010) – Abuse & Nefarious Use of Cloud Computing – Insecure Interfaces and APIs – Malicious Insiders – Shared Technology Vulnerabilities – Data Loss/Leakage – Account or Service Hijacking 10 © 1985-2010 BeyondTrust Software, Inc. All rights reserved
- 11. The Evolving Threat Landscape Boldness and inventiveness of hackers is outrunning companies’ ability to deal with them. Theft of intellectual property from U.S. companies is occurring at a rate of $200B a year. “Organizations continue to struggle with excessive user privilege as it remains the primary attack point for data breaches and unauthorized transactions.” ~ Mark Diodati, Burton/Gartner Group • Cost of security operations outstripping IT budget growth • Threat surface increases with every new user and every new technology – Acceleration of APT activities – BYOD/’Consumerization’ of IT a fact of life now – Virtualization and the Private Cloud blur create gaps for attack • Challenges in distinguishing between ‘potential’ and ‘real’ threats 11 © 1985-2010 BeyondTrust Software, Inc. All rights reserved
- 12. The Problem is Broad and Deep • The threat from attacks is a statistical certainty and businesses of every type and size are vulnerable. • Organizations are experiencing multiple breaches: 59 percent had two or more breaches in the past 12 months. • Only 11 percent of companies know the source of all network security breaches. 12 © 1985-2010 BeyondTrust Software, Inc. All rights reserved
- 13. Demystifying Cloud Security You can’t secure ‘The Cloud.’ There is no ‘The Cloud.’ If you don’t have a robust security program, cloud computing will make it worse.” Christopher Hoff – Founding member and technical advisor to the Cloud Security Alliance 13 © 1985-2010 BeyondTrust Software, Inc. All rights reserved
- 14. Impact of Cloud Computing Cloud Computing Reality – Public, Hybrid or Private • Increasing scale – from thousands to tens of thousands servers • Increasing complexity makes configuration and change management challenging – Complex directory structures are a major pain point • Reliability is critical to realizing operational improvement 14 © 1985-2010 BeyondTrust Software, Inc. All rights reserved
- 15. Rethink Existing Controls for Clouds What’s the same – Many technical controls are the same What’s different – Massively automated, virtualized, multi-tenant environment – Complex supply chain, multiple-domain security concerns Necessitates some shifts in security strategy – New controls (hypervisor integrity monitoring) – Process-related controls (application and data governance) 15 © 1985-2010 BeyondTrust Software, Inc. All rights reserved
- 16. Best Practice For Cloud Security Full Life-Cycle Control of Privileged Users Requirements: Account for All Privileged Users Manage Provisioning/De-Provisioning Privileged Credentials Implement a “Least Privilege” based Control System Monitor and Reconcile Privileged Activity Maintain a High Quality Audit Repository Automate Compliance Reporting 16 © 1985-2010 BeyondTrust Software, Inc. All rights reserved
- 17. Requirements For Enterprise Grade Cloud Security • Scalable, enterprise grade fabric • Seamless integrations with on-premise and cloud directories • Allow admins to manage policies not infrastructure • Dynamically react to changes in virtual environment • Quantifiable performance metrics of how it’s performing 17 © 1985-2010 BeyondTrust Software, Inc. All rights reserved
- 18. Cloud Security with BeyondTrust BeyondTrust allows companies to extend existing security infrastructure, policies and compliance reporting to their private, public and hybrid clouds such that it is • Scalable • Elastic • Easily installed • Easily managed 18 © 1985-2010 BeyondTrust Software, Inc. All rights reserved
- 19. The BeyondTrust Vision Security in Context Public, Private and Hybrid Our threat management and policy Cloud Computing Security enablement solutions provide zero-gap visibility and actionable intelligence to reduce Server & Desktop, Physical & Virtualization Windows, Linux, risks and close security gaps by integrating Unix providing Security in Context across vulnerabilities, privilege and data. Network • Solutions for infrastructure, endpoints, Device Security data and applications • Support for physical, virtual, public, Data Security private and hybrid cloud environments & Leak Prevention • Allows IT governance to strengthen security, improve productivity, drive Governance, Risk compliance and reduce expense & Compliance 19 © 1985-2010 BeyondTrust Software, Inc. All rights reserved
- 20. Context-Aware Security Intelligence Complete Risk Management for both Internal and External Threats Discovery of all internal and external vulnerabilities and threats Prioritization of risk according to threats, resources, privileges, etc. Threat-aware mitigations and preventative measures including Patch Management, Least Privilege, DLP and Endpoint protection. Continuous monitoring and measurement of threat posture Automated compliance reporting 20 © 1985-2010 BeyondTrust Software, Inc. All rights reserved
- 21. Context-Aware Security Intelligence Benefits Comprehensive preventative intelligence BeyondTrust allows you to discover all your security weaknesses across vulnerabilities, privilege and data and provides you with the security intelligence you need to protect business assets from cyber attacks. Fully automated and integrated; less resource intensive BeyondTrust automates the full spectrum of ongoing assets discovery, assessments, policy and compliance enforcement for your entire IT infrastructure across Desktop, Servers, Mobile, Virtual, Database and Cloud. Flexible and Scalable Our solutions support distributed deployment across the largest organizations around the globe. 21 © 1985-2010 BeyondTrust Software, Inc. All rights reserved
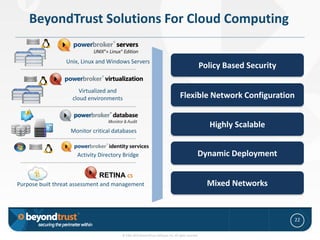
- 22. BeyondTrust Solutions For Cloud Computing Unix, Linux and Windows Servers Policy Based Security Virtualized and cloud environments Flexible Network Configuration Highly Scalable Monitor critical databases Activity Directory Bridge Dynamic Deployment RETINA CS Purpose built threat assessment and management Mixed Networks 22 © 1985-2010 BeyondTrust Software, Inc. All rights reserved
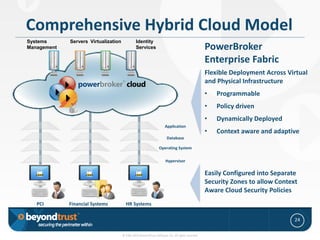
- 23. Comprehensive Hybrid Cloud Model Systems Servers Virtualization Identity Management Services PowerBroker Enterprise Fabric Flexible Deployment Across Virtual and Physical Infrastructure • Programmable • Policy driven • Dynamically Deployed Application • Context aware and adaptive Database Operating System Hypervisor Easily Configured into Separate Security Zones to allow Context Aware Cloud Security Policies PCI Financial Systems HR Systems 24 © 1985-2010 BeyondTrust Software, Inc. All rights reserved
- 24. Next: Learn More About Secure Cloud Deployments BeyondTrust Resources IBM Resources Free product evaluation Learn more about Free whitepaper: IBM SmartCloud Elevating Cloud Enterprise and Sign Security Up for an Account with Privilege Delegation Find both here: Visit: www.beyondtrust.com/SmartCloud www.ibm.com/buycloud 25 © 1985-2010 BeyondTrust Software, Inc. All rights reserved
- 25. Thank You Join the Conversation! 800-234-9072 818-575-4000 www.beyondtrust.com © 1985-2012 BeyondTrust Software, Inc. All rights reserved