Ravel: Pinpointing Vulnerabilities
- 1. Pinpointing Vulnerabilities Yue Chen, Mustakimur Khandaker, Zhi Wang Florida State University Pinpointing Vulnerabilities 1
- 2. Question • When an attack is detected, how to locate the underlying vulnerability? 2Pinpointing Vulnerabilities Attack Vulnerability
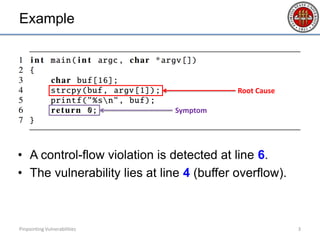
- 3. Example • A control-flow violation is detected at line 6. • The vulnerability lies at line 4 (buffer overflow). 3Pinpointing Vulnerabilities Root Cause Symptom
- 4. Attack Detection v.s. Vulnerability Locating • Control-flow Integrity (CFI) – Detect the control-flow graph violation (e.g., on function returns) • Taint Analysis – Detect tainted data being loaded to PC • System Call Interposition – Detect abnormal syscalls made by the payload Pinpointing Vulnerabilities 4 Manifestation of attack rarely coincides with the vulnerabilities
- 5. Ravel – Three Components • Online attack detector • Record & replay with instrumentation • Offline vulnerability locator Pinpointing Vulnerabilities 5 RAVEL: Root-cause Analysis of Vulnerabilities from Exploitation Log
- 6. Ravel – Strengths 1. Reliably reproduce real-world attacks in the lab environment 2. Low online performance overhead – Locating vulnerabilities is time-consuming 3. Extensible: – New attack detection and vulnerability locating techniques can be easily integrated – (already support a variety of vulnerability locating techniques) Pinpointing Vulnerabilities 6
- 7. Attack Detection • Ravel uses existing attack detection methods – Program crash (or other exceptions) – Abnormal system calls (sequence/arguments) – Control-flow integrity violation (to be included) • New methods can be easily adopted by Ravel Pinpointing Vulnerabilities 7
- 8. Record & Replay • What to record & replay? – All the non-deterministic inputs (e.g., network packets) • Where to record & replay? – Application interface – Library interface – Virtual machine interface – System call interface Pinpointing Vulnerabilities 8
- 9. Record & Replay • What to record & replay? – All the non-deterministic inputs (e.g., network packets) • Where to record & replay? – Application interface – Library interface – Virtual machine interface – System call interface Pinpointing Vulnerabilities 9 More robust against attacks, with low cost
- 10. Record Pinpointing Vulnerabilities 10 System call return values Userspace data structures modified by syscalls Data copied from kernel to userspace Asynchronous signals Special instructions (e.g., RDTSC) Synchronization primitives
- 11. Replay with Instrumentation • Some syscalls replayed without real execution – e.g., gettimeofday • Some syscalls need to be re-executed – e.g., mmap • Replay under a binary translation (BT) engine – BT collects detailed memory accesses by the target – Replay distinguishes syscalls made by the target from those made by BT Pinpointing Vulnerabilities 11
- 12. Vulnerability Locator Data-flow Analysis Race Condition Use-after-free Double-free Integer Errors Pinpointing Vulnerabilities 12
- 13. Data-flow Analysis • Analyze def-use relations between instructions • Define: writes to a memory address • Use: reads from a memory address Pinpointing Vulnerabilities 13 A B write read define use
- 14. Data-flow Analysis • Analyze def-use relations between instructions • Define: writes to a memory address • Use: reads from a memory address Pinpointing Vulnerabilities 14 A B
- 15. Data-flow Analysis • Precompute a data-flow graph (DFG) – DFG: the valid def-use relations in the program – Our prototype uses dynamic analysis – Extra relations regarded as violations • Violation to DFG indicates the vulnerability location – It could be the def or the use, but which one? – Refine the results with heuristics Pinpointing Vulnerabilities 15
- 16. Data-flow Analysis • Precompute a data-flow graph (DFG) – DFG: the valid def-use relations in the program – Our prototype uses dynamic analysis – Extra relations regarded as violations • Violation to DFG indicates the vulnerability location – It could be the def or the use, but which one? – Refine the results with heuristics Pinpointing Vulnerabilities 16
- 17. Data-flow Analysis • Precompute a data-flow graph (DFG) – DFG: the valid def-use relations in the program – Our prototype uses dynamic analysis – Extra relations regarded as violations • Violation to DFG indicates the vulnerability location – It could be the def or the use, but which one? – Refine the results with heuristics Pinpointing Vulnerabilities 17
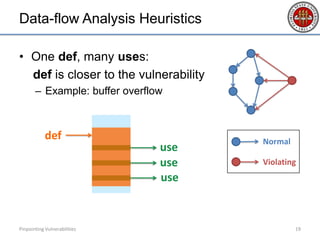
- 18. Data-flow Analysis Heuristics • One def, many uses: def is closer to the vulnerability – Example: buffer overflow Pinpointing Vulnerabilities 18 use use use Normal Violating
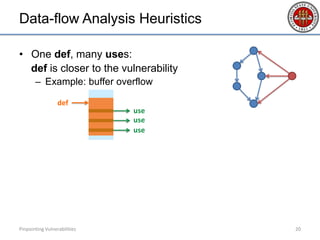
- 19. Data-flow Analysis Heuristics • One def, many uses: def is closer to the vulnerability – Example: buffer overflow Pinpointing Vulnerabilities 19 use def use use Normal Violating
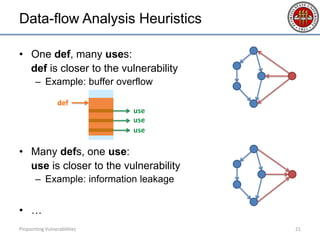
- 20. Data-flow Analysis Heuristics • One def, many uses: def is closer to the vulnerability – Example: buffer overflow • Many defs, one use: use is closer to the vulnerability – Example: information leakage • … Pinpointing Vulnerabilities 20 use def use use
- 21. Data-flow Analysis Heuristics • One def, many uses: def is closer to the vulnerability – Example: buffer overflow • Many defs, one use: use is closer to the vulnerability – Example: information leakage • … Pinpointing Vulnerabilities 21 use def use use
- 22. Integer Errors • Focus on common integer errors – Start from common functions/instructions that take integer operands • E.g., memcpy, recvfrom; movs, stos… – Search backwards for integer errors • Example: memcpy ( void * destination, const void * source, size_t num ); Search from num backwards for integer errors. Pinpointing Vulnerabilities 22
- 23. Integer Errors • Assignment truncation (e.g., 0x12345678 → 0x5678) – To detect: assign from a longer to a shorter integer type • Integer overflow/underflow (e.g., 0xFFFFFFFF + 1) – To detect: check the RFLAGS register • Signedness error (e.g., unsigned_int_var = signed_int_var) – To detect: collect hints from functions and instructions • Instructions: jg, jge, ja, jae, cmovg, cmova, idiv, div, etc. • Functions: memmove, strncat, etc. • Benign integer errors? – Related to a reported vulnerability! Pinpointing Vulnerabilities 23
- 24. Integer Errors • Assignment truncation (e.g., 0x12345678 → 0x5678) – To detect: assign from a longer to a shorter integer type • Integer overflow/underflow (e.g., 0xFFFFFFFF + 1) – To detect: check the RFLAGS register • Signedness error (e.g., unsigned_int_var = signed_int_var) – To detect: collect hints from functions and instructions • Instructions: jg, jge, ja, jae, cmovg, cmova, idiv, div, etc. • Functions: memmove, strncat, etc. • Benign integer errors? – Related to a reported vulnerability! Pinpointing Vulnerabilities 24
- 25. Use-after-free and Double-free • Ravel instruments memory allocation/free functions to track the memory life-time • Use-after-free: freed memory is accessed again • Double-free: memory freed more than once without re-allocation Pinpointing Vulnerabilities 25
- 26. Race Condition • When race condition happens, the execution deviates from the recorded one – as we do not implement strict R&R • When detected, use the happens-before relation to check for race conditions Pinpointing Vulnerabilities 26
- 27. Implementation • Record & replay: – FreeBSD release 10.2 – Kernel modification + small user-space utility • Vulnerability locator: – Extended from Valgrind Pinpointing Vulnerabilities 27
- 28. Evaluation – Effectiveness • Buffer overflow • Integer errors • Information leakage • Use-after-free and double-free • Format string vulnerabilities Pinpointing Vulnerabilities 28
- 29. CVE-2013-2028 of Nginx Pinpointing Vulnerabilities 29
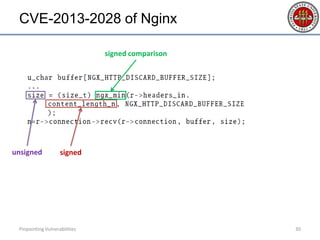
- 30. CVE-2013-2028 of Nginx Pinpointing Vulnerabilities 30 signedunsigned signed comparison
- 31. CVE-2013-2028 of Nginx Pinpointing Vulnerabilities 31 signedunsigned larger than expected signed comparison
- 32. CVE-2013-2028 of Nginx Pinpointing Vulnerabilities 32 signedunsigned larger than expected buffer overflow signed comparison
- 33. CVE-2013-2028 of Nginx Pinpointing Vulnerabilities 33 signedunsigned larger than expected buffer overflow signed comparison Ravel Data-flow Violation Signedness Conflict Memory Exception
- 34. Evaluation – Effectiveness • More examples are in the paper (Heartbleed, etc.) Pinpointing Vulnerabilities 34
- 35. Evaluation – Performance Performance overhead of Ravel’s online components relative to the original FreeBSD system Pinpointing Vulnerabilities 35
- 36. Pinpointing Vulnerabilities Q&A Pinpointing Vulnerabilities 36 http://YueChen.me
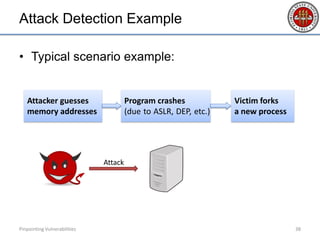
- 38. Attack Detection Example • Typical scenario example: Pinpointing Vulnerabilities 38 Attack Attacker guesses memory addresses Program crashes (due to ASLR, DEP, etc.) Victim forks a new process
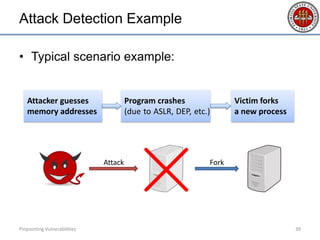
- 39. Attack Detection Example • Typical scenario example: Pinpointing Vulnerabilities 39 Attack Fork Attacker guesses memory addresses Program crashes (due to ASLR, DEP, etc.) Victim forks a new process