20230828161124_PPT3-Asset Misappropriation Cases AND Analyses.pptx
- 1. Course : ACCT8011 – Applied Fraud Examination Period : September / February 2020 TOPIC 3 Asset Misappropriation D3255 – Gatot Soepriyanto Ph.D., CA., CPA (Aust.)., CFE
- 2. Learning Objectives • LO3: Analyze fraud cases related to asset misappropriation & corruption scheme
- 3. Outline • Asset Misappropriation • Theft of Cash through Larceny • Theft of Cash through Skimming • Cash Theft through Fraud Disbursement • Theft of Inventory and Other Assets • Case Discussions
- 4. Introduction • Employees, vendors, and customers of organizations have three opportunities to steal assets: (1) they can steal receipts of cash and other assets as they are coming into an organization; (2) they can steal cash, inventory, and other assets that are on hand; or (3) they can commit disbursement fraud by having the organization pay for something it shouldn’t pay for or pay too much for something it purchases. With each of these three types of fraud, the perpetrators can act alone or work in collusion with others. Figure 14.1 outlines the mis- appropriation possibilities.
- 5. • Employees, vendors, and customers of organizations have three opportunities to steal assets: – Steal receipts of cash and other assets as they are coming into an organization – Steal cash, inventory, and other assets that are on hand – Commit disbursement fraud by having the organization pay for something it shouldn’t pay for or pay too much for something it purchases • With each of these three types of fraud, the perpetrators can act alone or work in collusion with others. • Figure 14.1 outlines the misappropriation possibilities. Asset Misappropriations
- 6. CHAPTER 14 6 Figure 14.1 Types of Asset Misappropriations
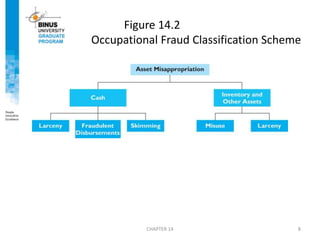
- 7. • Thefts of cash – Larceny (intentionally taking away an employer’s cash without the consent and against the will of the employer) – Skimming (the removal of cash from a victim entity prior to its entry in an accounting system) – Fraudulent disbursements • Thefts of inventory and other assets – Misuse – Larceny • Figure 14.2 illustrates the main elements of Wells’s classification scheme. Asset Misappropriations— Wells’s Classification Scheme
- 8. CHAPTER 14 8 Figure 14.2 Occupational Fraud Classification Scheme
- 9. • When larceny occurs, cash is stolen by employees or others after the cash is recorded in the company’s accounting system. – As a result, larceny schemes are easier to detect than skimming schemes and are far less common. • Cash larcenies can take place in any circumstance in which an employee has access to cash. – Common larceny schemes involve the theft of cash or currency on hand (in a cash register or petty cash box, for example) or from bank deposits. • Cash larcenies are most successful when they involve relatively small amounts over extended periods of time. • With such thefts, businesses often write the small missing amounts off as “shorts” or “miscounts,” rather than as thefts. Theft of Cash through Larceny
- 10. • Skimming is any scheme in which cash is stolen from an organization before it is recorded on the organization’s books and records. • Basic skimming scheme – Taking money from the sale of goods or services but making no record of the sale • More complicated skimming schemes occur when employees – Understate sales and collections by recording false or larger- than-reality sales discounts – Misappropriate customer payments and write off the receivable as “uncollectible” – Embezzle a first customer’s payment and then credit that customer’s account when a second customer pays (a delayed recognition of payment, called lapping) – Work together with customers to allow them to pay later than required or less than required Theft of Cash through Skimming
- 11. • The ACFE found that fraudulent disbursements comprised by far the highest percentage of asset misappropriations. • It identified six cash schemes involving outgoing disbursements of cash. – Billing schemes – Check tampering – Expense reimbursements schemes – Payroll disbursement schemes – Wire transfer schemes – Register disbursement schemes • Table 14.1 summarizes these six disbursement schemes. Cash Theft through Fraudulent Disbursements
- 12. CHAPTER 14 12 Table 14.1 Disbursement Schemes
- 13. • Employee prepares a fraudulent check for his or her own benefit. • Employee intercepts a check intended for another person or entity and converts the check to his or her own benefit. Check Tampering
- 14. • False refunds • False voids Register Disbursement Schemes
- 15. • Setting up dummy companies (shell companies) to submit invoices to the victim organization • Altering or double-paying a nonaccomplice vendor’s statements • Making personal purchases with company funds Billing Schemes
- 16. • Mischaracterizing expenses • Overstating expenses • Submitting fictitious expenses • Submitting the same expenses multiple times Expense Schemes
- 17. • Ghost employees • Falsified hours and salary • Commission schemes • False workers’ compensation claims Payroll Disbursement Schemes
- 18. • Examples – Tyco scandal – Adelphia scandal Executive Cash Frauds
- 19. • A person can misappropriate company assets other than cash in one of two ways. – The asset can be misused (or “borrowed”), or it can be stolen. • Simple misuse is obviously the less egregious of the two types of fraud. – Assets that are misused but not stolen typically include company vehicles, company supplies, computers, and office equipment. – These assets are also used by some employees to conduct personal work on company time. Misuse of Company Assets
- 20. • Noncash types of frauds against organizations – Inventory – Information – Securities • Table 14.2 describes the most common noncash types of frauds against organizations. Theft of Inventory and Other Assets
- 21. CHAPTER 14 21 Table 14.2 Noncash Frauds Against Organizations
- 22. Case Discussion • Case Discussion 1: The case of the disappearing printer ink • Case Discussion 2: Creative Embezzlement • Source: – https://www.fraud- magazine.com/article.aspx?id=4295010667 – https://www.fraud- magazine.com/article.aspx?id=4295013415