Automotive Hacking
- 1. Automotive Hacking Under The Hood: How Hackers Can Remotely Hack Your Car?
- 2. Automotive Hacking Under The Hood: How Hackers Can Remotely Hack Your Car?
- 3. Cyber criminals working for enemy states could ‘kill millions’ by remotely hacking cars, warns expert Justin Cappos, Computer Scientist New York University
- 4. Vehicular Automation • Vehicular Automation involves the use of mechatronics, artificial intelligence, and multi- agent system to assist a vehicle's operator. • These features and the vehicles employing them may be labelled as intelligent or smart. • A vehicle using automation for difficult tasks, especially navigation, may be referred to as semi- autonomous. • A vehicle relying solely on automation is consequently referred to as robotic or autonomous.
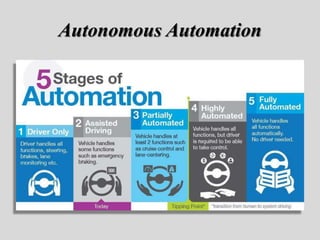
- 7. Autonomy levels Autonomy in vehicles is often categorized in six levels: The level system was developed by the Society of Automotive Engineers (SAE). • Level 0: No automation. • Level 1: Driver assistance - The vehicle can control either steering or speed autonomously in specific circumstances to assist the driver. • Level 2: Partial automation - The vehicle can control both steering and speed autonomously in specific circumstances to assist the driver. • Level 3: Conditional automation - The vehicle can control both steering and speed autonomously under normal environmental conditions, but requires driver oversight. • Level 4: High automation - The vehicle can complete a travel autonomously under normal environmental conditions, not requiring driver oversight. • Level 5: Full autonomy - The vehicle can complete a travel autonomously in any environmental conditions.
- 9. Vehicle Automation • Vehicle automation has been one of the fundamental applications within the field of intelligent transportation systems (ITS) since the start of ITS research in the mid-1980s. • For most of this time, it has been generally viewed as a futuristic concept that is not close to being ready for deployment. • However, recent development of “self-driving” cars and the announcement by car manufacturers of their deployment by 2020 show that this is becoming a reality.
- 11. Automotive Hacking • Automotive hacking is the exploitation of vulnerabilities within the software, hardware, and communication systems of automobiles.
- 12. Automotive Hacking • Modern automobiles contain hundreds of on-board computers processing everything from vehicle controls to the infotainment system.
- 14. Automotive Hacking • These computers, called Electronic control units (ECU), communicate with each other through multiple networks and communication protocols including the Controller Area Network (CAN) for vehicle component communication such as connections between engine and brake control; Local Interconnect Network (LIN).
- 15. Electronic control units (ECU)
- 16. Electronic control units (ECU)
- 17. Automotive Hacking • For cheaper vehicle component communication such as between door locks and interior lights; • Media Oriented Systems Transport (MOST) for infotainment systems such as modern touchscreen and telematics connections; and • FlexRay for high-speed vehicle component communications such as active suspension and active cruise control data synchronization.
- 18. Media Oriented Systems Transport (MOST)
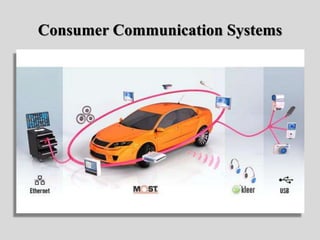
- 19. Automotive Hacking • Additional consumer communication systems are also integrated into automobile architectures including Bluetooth for wireless device connections, 4G Internet hotspots, and vehicle Wi-Fi.
- 22. Automotive Hacking • The integration of these various communications and software systems leaves automobiles vulnerable to attack. • Security researchers have begun demonstrating the multitude of potential attack vectors in modern vehicles, and some real-world exploits have resulted in manufacturers issuing vehicle recalls and software updates to mobile applications.
- 24. Automotive Hacking • Manufacturers, such as John Deere, have used computer systems and Digital Rights Management to prevent repairs by the vehicle owners, or by third parties, or the use of aftermarket parts. • Such limitations have prompted efforts to circumvent these systems, and increased interest in measures such as Motor Vehicle Owners' Right to Repair Act.
- 26. Automotive Hacking • Any car built after 2005 is an 'open door' to hackers and could be remotely controlled to obliterate 'millions of civilians', a researcher has found. • Even some vehicles up to 17 years old could be vulnerable to attack and unless car makers fix the problem deaths in the next five years are inevitable. • Hackers may already be causing accidents without authorities knowing.
- 27. Hackers may already be causing accidents without authorities knowing
- 28. Automotive Hacking • The warning was made by Justin Cappos, a computer scientist at New York University. • Dr Cappos says this vulnerability should be treated as an ‘urgent' national security issue’.
- 29. Justin Cappos, a computer scientist at New York University says this vulnerability should be treated as an ‘urgent' national security issue’.
- 30. Automotive Hacking • Once in the car, Dr Cappos warned hackers can send messages that stop the brakes working and turn of power steering.
- 31. Automotive Hacking • 'Components in cars are not good at understanding where messages come from and whether they are authentic.' • In 2016 hackers showed how they were able to take control of a Jeep Cherokee when it was moving at high speed.
- 33. Automotive Hacking • Charlie Miller and Chris Valasek, who now work for Uber, sent false messages to its internal network, overriding the correct ones. • That allowed them to do terrifying things such as making the vehicle turn sharply while it was speeding down a country road.
- 35. Research • In 2010, security researchers demonstrated how they could create physical effects and undermine system controls by hacking the ECU. • The researchers needed physical access to the ECU and were able to gain full control over any safety or automotive system including disabling the brakes and stopping the engine
- 36. hacking the ECU
- 37. Research • In a follow-up research paper published in 2011, researchers demonstrated that physical access is not even necessary. • The researchers showed that “remote exploitation is feasible via mechanics tools, CD players, Bluetooth, cellular radio...and wireless communication channels allow long distance vehicle control, location tracking, in-cabin audio exfiltration and theft”. • This means that a hacker could gain access to a vehicle's vital control systems through almost anything that interfaces with the automobile's systems.
- 38. Remote Exploitation Is Feasible Via Mechanics Tools, CD Players, Bluetooth, Cellular Radio...And Wireless Communication Channels
- 39. Fiat Chrysler UConnect • UConnect is Fiat Chrysler's Internet- connected feature which enables owners the ability to control the vehicle's infotainment/navigation system, sync media, and make phone calls. • It even integrates with the optional on-board WiFi.
- 40. UConnect is Fiat Chrysler's Internet-connected feature which enables owners the ability to control the vehicle's infotainment/navigation system
- 41. Fiat Chrysler UConnect • However, susceptibilities in Fiat Chrysler’s UConnect system, available on over 1.4 million cars, allows hackers to scan for cars with the system, connect and embed malicious code, and ultimately, commandeer vital vehicle controls like steering and brakes.
- 42. UConnect system
- 43. General Motors OnStar RemoteLink App • The OnStar RemoteLink app allows users the ability to utilize OnStar capabilities from their Android or iOS smartphones. The RemoteLink app can locate, lock and unlock, and even start your vehicle.
- 44. General Motors OnStar RemoteLink App
- 45. General Motors OnStar RemoteLink App • The flaw in General Motors’ OnStar RemoteLink app, while not as extreme as UConnect, allows hackers to impersonate the victim in the eyes of the RemoteLink app. • This means that the hackers can access all of the features of the RemoteLink app available to the victim including locating, locking and unlocking, and starting the engine
- 46. Hackers can access all of the features of the RemoteLink app available to the victim including locating, locking and unlocking, and starting the engine
- 47. Keyless Entry • The security researcher Samy Kamkar has demonstrated a device that intercepts signals from keyless-entry fobs and would allow an attacker to unlock doors and start a car's engine.
- 48. Security Researcher Samy Kamkar Has Demonstrated A Device That Intercepts Signals From Keyless-entry Fobs And Would Allow An Attacker To Unlock Doors And Start A Car's Engine
- 49. Case Study : Hackers Remotely Kill a Jeep on the Highway • It was the summer of 2015, Andy Greenberg was driving a Jeep Cherokee in downtown St. Louis. • The vents started blasting cold air at the maximum setting, the radio was blaring at full volume, and the windshield wipers turned on.
- 50. Case Study : Hackers Remotely Kill a Jeep on the Highway • renowned hackers Charlie Miller and Chris Valasek describe how they compromised the Jeep Cherokee via a vulnerability in Uconnect, the vehicle's Internet-connected entertainment system.
- 51. Case Study : Hackers Remotely Kill a Jeep on the Highway
- 52. Case Study : Hackers Remotely Kill a Jeep on the Highway • The flaw in Uconnect lets anyone with the car's IP address to gain access from anywhere in the country. Miller and Valasek were then able to send commands to the engine and wheels through the car's internal Controller Area Network (CAN).
- 53. Case Study : Hackers Remotely Kill a Jeep on the Highway
- 54. Case Study: Your Car Could Be the Next Ransomware Target • Cybersecurity experts say there are plenty of vulnerabilities for enterprising ransom- seeking hackers, unless automakers act
- 55. Case Study: Your Car Could Be the Next Ransomware Target • The reason cars are such inviting targets for ransomware hackers is that they’re increasingly computerized. • And as automakers have transferred more and more functions to processors, they've neglected to install the same levels of security found in other modern device ssuch as phones and laptops.
- 56. Case Study: Your Car Could Be the Next Ransomware Target
- 57. Case Study: Your Car Could Be the Next Ransomware Target • “Once you connect the car to the internet, the entire vehicle becomes a threat surface. If the auto industry doesn’t adapt, we’ll continue to see mistakes and potential vulnerabilities for things like ransomware to take place,” says Craig Hurst, executive director of the Future of Automotive Security Technology Research (FASTR)
- 58. Case Study: Your Car Could Be the Next Ransomware Target
- 59. Case Study: Your Car Could Be the Next Ransomware Target • The FBI issued a warning last year for the auto industry to be ever-vigilant about developing cybersecurity as autonomous technology advances and as cars become ever-more connected. • And multiple academic and industry consortiums and partnerships, as well as for-profit corporations, are working on the concern. • One possible scenario involves hackers installing malware into a vehicle's operating system, perhaps through an unprotected internet connection, and locking out the driving functions.
- 60. Case Study: Your Car Could Be the Next Ransomware Target • A driver might find his or her car unable to start. A message pops on the control screen with instructions for how to pay a ransom to make the vehicle start again. • “Cars are becoming computers on wheels,” says Jake Fisher, director of automotive testing at Consumer Reports. “As the technologies are added, manufacturers will have to consider all the possibilities. • We support the new technology, we’re just making sure that it is added in a responsible way.”
- 61. Case Study: Your Car Could Be the Next Ransomware Target
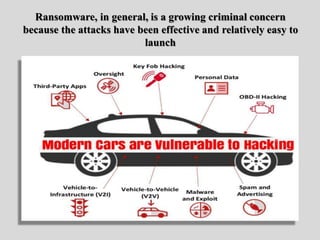
- 62. Ransomware, in general, is a growing criminal concern because the attacks have been effective and relatively easy to launch
- 63. FBI issued a warning against threats related to connected vehicle technologies in modern vehicles
- 64. Attacker Model • The types of attackers that are likely to be present in an automated vehicle system • Internal Versus External: The internal attacker is an authenticated member of the network that can communicate with other members. • The external attacker is considered by the network members as an intruder and, hence, is limited in the diversity of attacks. • Nevertheless, she/he can eavesdrop on the communication
- 66. Attacker Model • Malicious Versus Rational: A malicious attacker seeks no personal benefits from the attacks, and aims to harm the members or the functionality of the network. • Hence, she/he may employ any means disregarding corresponding costs and consequences. • On the contrary, a rational attacker seeks personal profit and, hence, is more predictable in terms of attack means and attack target.
- 68. Attacker Model • Active Versus Passive: An active attacker can generate packets or signals to perform the attack, whereas a passive attacker only eavesdrops on the communication channel (i.e., wireless or in-vehicle wired network). • Local Versus Extended: An attacker can be limited in scope, even if she/he controls several entities (vehicles or base stations), which make him/her local. • An extended attacker controls several entities that are scattered across the network, thus extending his/her scope.
- 70. Attacker Model • Intentional Versus Unintentional: An intentional attacker generates attacks on purpose, whereas an unintentional attack is a cyber incident that could be generated by faulty sensors or equipments.
- 71. 9 Terrifying Ways Hackers Can Control Your Car • Cyber security researchers Charlie Miller of Twitter and Chris Valasek of IOActive used the latest hacking techniques to hack in to the electrical systems of a Jeep Cherokee. They were able to do this without direct physical access to the vehicle.
- 72. 9 Terrifying Ways Hackers Can Control Your Car • Using the Internet they were able to gain wireless control of the Jeep Cherokee giving them access to the Jeep’s entertainment system, enabling them to relay commands to its dashboard functions, steering, brakes and transmission, and they were able to do all of this remotely 10 miles away from the vehicle's location.
- 73. 9 Terrifying Ways Hackers Can Control Your Car! • Finding any car via GPS coordinates • Because Uconnect computers are linked to the Internet via Sprint’s mobile network, hackers can use a Sprint mobile device as a Wi-Fi hot spot, along with a laptop, to scan for possible vulnerable targets on the Internet. Once an appropriate target has been found, they are then able to retrieve information about that vehicle, such as its vehicle identification number, make, model, IP address, and most scarily, its GPS coordinates. • Once the hacker has the GPS coordinates of the target vehicle, they can then input this data into Google Maps and track its general location by placing markers onto the map as the vehicle travels.
- 74. Sprint Drive: the all-in-one vehicle hotspot, tracker.
- 75. Finding any car via GPS coordinates
- 76. 9 Terrifying Ways Hackers Can Control Your Car! • Turning on your car Stereo system remotely • Imagine you found yourself driving down the motorway at night alone when suddenly the radio switched on at full volume, seemingly changing stations with you unable to control it or switch it off, I think you’d be forgiven for thinking you were about to be abducted by aliens, but this is one of the many ways that hackers can manipulate your vehicle via this exploit. • Apart from the obvious distraction issues, these types of attacks could be used to harass and intimidate people and when you are not aware of who is controlling the radio this could becomes quite frightening for some people.
- 77. Turning on your car Stereo system remotely
- 78. 9 Terrifying Ways Hackers Can Control Your Car! • Hacking Car Air Conditioning System • While not the most terrifying aspect of this hack, it’s also possible to control the vehicles air- conditioning system by remotely pumping air at full blast in to the target vehicle. Again, this would be something of a distraction to drivers, especially when travelling at high speed. • This may not seem all that scary but imagine driving on a very cold winters day, early in the morning and being blasted by cold air with no ability to stop it.
- 79. Hacking Car Air Conditioning System
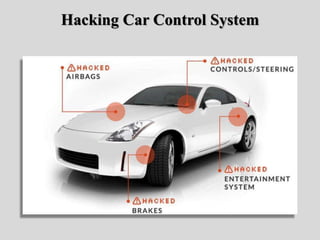
- 80. 9 Terrifying Ways Hackers Can Control Your Car! • Hacking Car Control System • It’s a beautifully sunny day and your travelling at 70mph down the motorway when suddenly your washer fluid starts to continuously spray your windscreen while your wipers swish from left to right uncontrollably at full speed. • While struggling to see through your windscreen, all confused and a little jumpy, that’s when your transmission unexpectedly cuts out and your vehicle stops responding to your accelerator.
- 81. Hacking Car Control System
- 82. 9 Terrifying Ways Hackers Can Control Your Car! • As the vehicle begins to lose speed rapidly, you’re terrified to see in your rear view mirror cars, lorries and other motor vehicles beginning to rapidly pile up behind you, swerving and honking their horns when trying to avoid your sudden speed decrease. • Well, using this vulnerability, this is exactly what could happen if a hacker gained control of your vehicle.
- 83. 9 Terrifying Ways Hackers Can Control Your Car! • Shut down you Car Engine • While your vehicle is in motion, hackers also have the ability to completely and fully kill the engine. Leaving you unable to control your vehicle safely without restarting the engine. • If this command was given at a critical moment during your journey, this could cause a dangerous incident. • Imagine being on a busy motorway roundabout when this hack kicks in.
- 84. Shut down you Car Engine
- 85. 9 Terrifying Ways Hackers Can Control Your Car! • Hacking Car Brakes • If you’re not already a little worried, then imagine a hacker being able to abruptly engage the breaks of your vehicle while you’re in motion? • This is where things begin to get really dangerous. Having the ability to track a vehicle on the move and then suddenly engage the braking system is quite terrifying. • Speeding down the motorway at 70mph when your brakes unexpectedly and violently kick in is an extremely dangerous prospect for you and other motorists.
- 87. 9 Terrifying Ways Hackers Can Control Your Car! • Failing your Car Brakes • This part of the hack is probably the scariest of the lot and it’s a horrifying thought that a compromised vehicle could have its brakes completely disabled by some anonymous hacker miles away in a remote location while the driver is helpless to stop it. • This scenario is all too real though and Miller and Valasek have demonstrated this with chilling precision. • Once the hacker has control of the system, there’s nothing to stop them causing a major incident.
- 88. Failing your Car Brakes
- 89. 9 Terrifying Ways Hackers Can Control Your Car! • Threatening the Car Driver through Display Screen • Miller and Valasek have also been able to send images remotely to the in-car digital display. You can certainly see how this could be abused and cause issues for the occupants of the vehicle.
- 90. Threatening the Car Driver through Display Screen
- 91. 9 Terrifying Ways Hackers Can Control Your Car! • Hacking Car Steering System • While travelling at slower speeds and only while reversing, the hack allows for the control of the vehicles steering. • Even though this hack only works at slower speeds, this is still a dangerous prospect for both the occupants and pedestrians.
- 92. Hacking Car Steering System
- 93. 9 Terrifying Ways Hackers Can Control Your Car! • The list of commands a hacker can issue when in control of a compromised vehicle is not limited to those listed above. • They are also able to manipulate digital readouts for speed and fuel consumption, honk the horn, query the vehicle for information and unlock it. • As hacking techniques get more sophisticated and pervasive, and as vehicle systems become more integrated in to the ‘Internet of Things’, it doesn’t become difficult to imagine that future hacks could gain more and more control over a vehicles functions.
- 94. 9 Terrifying Ways Hackers Can Control Your Car! • Miller and Valasek aren’t the only ones working on pointing out these vulnerabilities. • There has been other research conducted, such as that undertaken by researchers at the University of Washington and the University of California who were able to wirelessly disable locks and brakes on a Sedan. • There’s even a ‘Car Hackers Handbook’ out there.
- 96. Steps To Protect Your Car From Hacks
- 97. Steps To Protect Your Car From Hacks • Keep in touch with your car’s manufacturer • Update your car’s software • Store your keyless remote in the fridge (or faraday bag) • Turn off your car’s Bluetooth and Wi-Fi when not in use • Hide your car’s Wi-Fi password • Scan USB drives before plugging them into your car
- 98. Steps To Protect Your Car From Hacks • Keep in touch with your car’s manufacturer • Give your auto manufacturer your contact information so they can reach you about software updates or vehicle recalls if necessary. • Or be proactive, and check the National Highway Traffic Safety Administration (NHTSA) recall page. Just enter your vehicle identification number (VIN) there to see if there’s been a recall for your vehicle.
- 99. Keep in touch with your car’s manufacturer
- 100. Steps To Protect Your Car From Hacks • Update your car’s software • Outdated software can contain bugs that hackers can exploit to steal your private data or take control of your car. • So just as you’d check your computer for software updates, be sure to keep an eye out for notices from your auto manufacturer, and bring your car in for updates as soon as they’re available.
- 101. Update your car’s software
- 102. Steps To Protect Your Car From Hacks • Store your keyless fob in the fridge • Or get a faraday bag. • Because in a matter of seconds, thieves can break into your car by amplifying the signal from your keyless remote and tricking the car into thinking you’re nearby. • If Your Keyless Fob Is In A Faraday Bag (Or Your Refrigerator), Then Its Signal Will Be Blocked, Preventing Criminals From Hacking Open Your Car Doors.
- 103. Store your keyless fob in the fridge Or get a faraday bag
- 104. Steps To Protect Your Car From Hacks • Turn off your car’s Bluetooth and Wi-Fi when not in use • An open wireless connection could allow criminals to walk up to an unpatched car, connect to its entertainment system, and take control of one or more parts of the vehicle
- 105. Turn off your car’s Bluetooth and Wi-Fi when not in use
- 106. Steps To Protect Your Car From Hacks • The FBI warns, “Vulnerabilities may exist within a vehicle’s wireless communication functions, within a mobile device – such as a cellular phone or tablet connected to the vehicle via USB, Bluetooth, or Wi-Fi – or within a third-party device connected through a vehicle diagnostic port. In these cases, it may be possible for an attacker to remotely exploit these vulnerabilities and gain access to the vehicle’s controller network or to data stored on the vehicle.” • So if you’re not using your car’s Bluetooth or Wi-Fi, it’s best to switch them off.
- 107. Steps To Protect Your Car From Hacks • Hide your car’s Wi-Fi password • This one’s simple. If your car has its own Wi- Fi, be sure to keep the password hidden. Leaving it in your glovebox could expose you to attack if your car is ever broken into.
- 108. Hide your car’s Wi-Fi password
- 109. Steps To Protect Your Car From Hacks • Scan USB drives before plugging them into your car • An infected USB drive could contain malicious code designed to compromise your car. So be sure to scan any USB drive before plugging it into your car.
- 110. Scan USB drives before plugging them into your car
- 111. Conclusion • These types of attacks are only likely to get more varied and sophisticated and with some 470,000 plus estimated Crysler vehicles already vulnerable to these types of attack, not to mention the very real possibility of other manufacturers models also being vulnerable to similar exploits it’s extremely important that both the auto industry and customers take note. • Crysler has issued a security patch which can be downloaded at their website by entering your Vehicle Identification Number (VIN) but this is a manual process that requires you to download the patch and update your Uconnect System via a USB drive. Alternatively, you can take your car to a dealer to get the update.
- 113. Conclusion • This type of patching requires that the customer be aware of the vulnerability though, which means that moving forward, the responsibility for updating the security of the vehicles electronic system lies with customers. • There needs to be a better, more secure way of automating vehicle updates on these types of systems. • In a hyper connected world, cyber attacks and cyber threats are an ever-growing concern for businesses and consumers alike and the research conducted by Miller and Valasek highlights the need for more individuals to be working in IT security jobs, specifically cyber security.
- 114. In a hyper connected world, cyber attacks and cyber threats are an ever-growing concern
- 115. Terminology • Automation: The use of electronic or mechanical devices to replace human labor, in this case, to replace the human labor applied to driving a road vehicle.
- 116. Terminology • Autonomous Automation: Vehicle automation based entirely on information acquired from sensors onboard the vehicle, without active communication or cooperation with other entities
- 118. Terminology • Cooperative Automation: Vehicle automation that incorporates information communicated from the roadway infrastructure or other vehicles and that may also involve active negotiation of manoeuvres with other vehicles.
- 120. Terminology • Dynamic Driving Task: All of the real-time functions required to operate a motor vehicle in on-road traffic • object and event detection, recognition, and classification; • object and event response; • real-time mission planning; • steering, turning, lane keeping, and lane changing; • acceleration and deceleration; • enhancing conspicuity (lighting, signaling, gesturing, etc.
- 121. Terminology • Infrastructure sign: Road sign (static or dynamic) installed by road operator or government agencies to inform drivers.
- 122. Terminology • Machine vision: Video image processing used for object detection (road, obstacles, road signs, etc.).
- 123. Terminology • GPS: Global Positioning System used for localization and positioning on the integrated map. • We assume that the vehicle includes multiple GPS 2 (e.g., one GPS for navigation display and one for automation)
- 124. GPS: Global Positioning System
- 125. Terminology • In-vehicle Devices: It includes hand-held devices brought by users. It can be connected to the infotainment system via Bluetooth, Wifi, Zigbee, or universal serial bus. • This can represent an after-market device, a smartphone, or a tablet
- 126. In-vehicle Devices
- 127. Terminology • Acoustic Sensor: Acoustic sensor that recognizes a trained/known signal. For example, a crash sound sensor detects a collision faster than an airbag sensor
- 128. Terminology • Radar: Active system that uses return of microwave radiation (radio waves) to detect objects. • Lidar (light detection and ranging): Active system that uses return of infrared (IR) or visible light instead of radio waves to detect objects.
- 129. Radar
- 130. Lidar
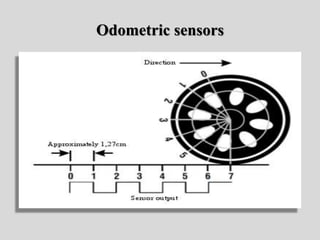
- 131. Terminology • In-vehicle sensors: Any on-board sensors that give information about the internal state of the vehicle (rotational speed of a wheel, tire pressure, etc.). • Odometric sensors: Wheel encoders and inertial sensors (accelerometers, gyroscope, etc.) used for inertial odometric navigation.
- 132. In-vehicle sensors
- 133. Odometric sensors
- 134. Samy Kamkar American researcher • A hacker made a $30 gadget that can unlock many cars that have keyless entry • https://www.businessinsider.in/latest/a-hacker-made-a-30-gadget-that-can- unlock-many-cars-that-have-keyless-entry/articleshow/48377988.cms
- 135. Security Researchers Charlie Miller and Chris Valasek • Chris Valasek and Charlie Miller: How to Secure Autonomous Vehicles • https://threatpost.com/chris-valasek-and-charlie-miller-how-to- secure-autonomous-vehicles/134937/
- 136. Justin Cappos, Computer Scientist, New York University • Cyber criminals working for enemy states could ‘kill millions’ by remotely hacking cars, warns expert • https://engineering.nyu.edu/news/cyber-criminals-working- enemy-states-could-kill-millions-remotely-hacking-cars- warns-expert
- 137. Books: Hacking Connected Cars: Tactics, Techniques, and Procedures
- 138. The Car Hacker's Handbook
- 139. FBI, Motor Vehicles Increasingly Vulnerable to Remote Exploits • Federal Bureau of Investigation, the Department of Transportation and the National Highway Traffic Safety Administration. • https://www.ic3.gov/media/2016/160317.aspx
- 140. Policing in smart cities • Bureau Of Police Research And Development • https://bprd.nic.in/WriteReadData/CMS/Policing%20in%20Smart%20Cities.pdf
- 141. References • Automotive hacking • https://en.wikipedia.org/wiki/Automotive_hacking • Car hacking threatens vision of connected mobility • https://www.ft.com/content/163f08c6-6ce3-11e9-9ff9-8c855179f1c4 • Carhacked! (9 Terrifying Ways Hackers Can Control Your Car) • https://purplegriffon.com/blog/carhacked-9-terrifying-ways-hackers-can- control-your-car • Car Hacks and How to Protect Yourself • https://www.kaspersky.com/resource-center/threats/car-hacks-and-how-to- protect-yourself • Hackers Remotely Kill a Jeep on the Highway—With Me in It • https://www.wired.com/2015/07/hackers-remotely-kill-jeep-highway/ • How Hackers Exploit Automotive Software to Overtake Cars • https://www.securitymagazine.com/articles/91192-how-hackers-exploit- automotive-software-to-overtake-cars • Researchers are sounding the alarm on a little-known risk of connected cars • https://www.fastcompany.com/90383517/researchers-are-sounding-the-alarm- on-a-little-known-risk-of-connected-cars
- 142. Thanks…