Blockchain meetup
- 1. Location: QuantUniversity Meetup November 14th 2017 Boston, MA Blockchain Technology Workshop 2017 Copyright QuantUniversity LLC. Presented By: Duru Turkoglu, PhD www.QuantUniversity.com
- 2. Blockchain Technology Cryptocurrencies, Applications, Limitations
- 3. • Public • Distributed • Immutable • Trustless What is Blockchain? Open to everybody Audited by everybody Append only No central authority Blockchain is an accounting system that is: Briefly: Distributed Ledger Introduced by: Bitcoin
- 4. • 1970s/80s --- Public key cryptography • Guardtime --- Application of public key cryptography • 1990 --- Digicash/ecash • 1992/1997 --- Hashcash/Proof-of-work • 1998 --- b-money, bitgold History of Blockchain
- 5. • 2008 --- Satoshi Nakamoto, creator of the Bitcoin Network Think: Store of value • 2013 --- Vitalik Buterin, creator of the Ethereum Network Think: Smart contracts and Worldwide computer • 2017 --- ERC20 Tokens/ICOs using the Ethereum Platform First ICO actually took place in 2013 Think: Stocks/assets (not fully clarified yet) • Ongoing --- Private blockchains, State channels, etc. History of Blockchain
- 6. Ownership Easy to Verify and Hard to Fabricate Ledger Easy to Transact and Hard to Modify Essential Qualities of a Functioning Ledger
- 7. Cash How do you make people believe that some cash out there is yours? Verifying Ownership Bearer’s Instrument If you have it in your wallet, then it is yours!
- 8. Cash What if you have a LOT of cash? It would be very hard/risky to carry it. Verifying Ownership ? Bearer’s Instrument If you have it in your wallet, then it is yours!
- 9. Cash What if you have a LOT of cash? It would be very hard/risky to carry it. Verifying Ownership Place it in a Trust The bank has your funds, but you can withdraw!
- 10. Car & Home What about other kinds of physical assets, such as cars, real estate, etc? Verifying Ownership Government Record Ownership is registered with DMV and Recorder’s Office.
- 11. Verifying Ownership Conventional Methods Rely on a Single Trusted Party • Banks, government offices, etc. • Problems arise when trust is broken: ▫ Access may be restricted or denied ▫ Prone to mistakes in recordkeeping ▫ Bank runs result in loss of funds (due to fractional reserve) • Transfer of ownership may require multiple parties involved • High transaction fees to be paid to each party involved Blockchain does not place trust in a single entity
- 12. Double Spending Cash in Wallet Can you double spend the cash in your wallet? NO! (Unless you are a magician) Issues Cannot transact with large amounts. Actually, you can but very risky.
- 13. Cash in Bank Account Can you double spend the funds in your bank account. No, banks do not clear funds twice, but you can try! Double Spending Issues Transaction fees are high. Clearance of funds may take several days.
- 14. Car & Home Can you double sell a car? Or a house? No! (In general) Fraudulent sales exist! Double Spending Issues Many parties are involved to prevent such fraudulent sales. Very high transaction fees.
- 15. Double Spending Conventional Methods Are Prone to Such Frauds • If the amount is too small there is no incentive (e.g., cash) • There are prevention methods for larger amounts/real assets ▫ Central parties managing the funds disallow double spend ▫ Third intermediary parties check validity of ownership • Requires trust in central or intermediary parties • Transfer of ownership may require multiple parties involved • High transaction fees to be paid to each party involved Blockchain prevents double spend via its ledger
- 16. Transactions and Ledger Physical Cash Very easy transactions. Very hard to modify ledger. Need physical exchange. Issues Theft is relatively easy. Physical cash is not the only source of money.
- 17. Fiat Money Relatively easy to transact within the same bank but not so easy with others. Hard to modify ledger from outside. Transactions and Ledger Issues Transaction fees are high. Money supply can be diluted relatively easily.
- 18. Car & Home Not very easy transactions. Relatively hard to modify ledger from outside. Transactions and Ledger Issues Many parties are involved in transactions leading to high fees.
- 19. Transactions and Ledger Conventional Methods • I Blockchain is not easy to modify Transactions require some time
- 21. Easy to Verify Hard to Fabricate
- 22. Story: Alice would like to send a very important message to Bob. She wants him to know that it is indeed her who sent the message. How can Alice accomplish this? Answer: One way functions and public key cryptography! Private and public keys to encrypt and to decrypt. Applications: Communications of any kind: internet, military, etc. Developments in cryptography created the field of computer science back in the 1940s. Public Key Cryptography
- 23. Illustration: • Alice produces private and public keys. • She publishes her public key to everyone. • Private key encrypts, public key decrypts. • Nobody can produce the same encryption without knowing the private key of Alice. Alice sends a message M to Bob: She encrypts M using her own private key: M ⟶ MA Bob decrypts the message from Alice: He decrypts message using Alice’s public key: MA ⟶ M Public Key Cryptography
- 24. Guarantees: Using Alice’s private key ensures that message is sent by Alice. Nobody else could have written it! Digital signatures: Encryption using a private key is called a “digital signature”. Digital signatures are enforceable in a court of law! Alice cannot claim that she did not send the message. Application in blockchain: Digital signatures are used to authenticate ownership. Payment addresses are generated by public keys. Public Key Cryptography
- 25. Verifying Ownership in Blockchain Public Key Cryptography to Prove Ownership • User creates a pair of public and private keys • Public key to generate and publish payment addresses • Private key to digitally sign for the funds in those addresses
- 26. Verifying Ownership in Blockchain Security of Public Key Cryptography • Brute force is a possible attack, but infeasible in general • One-way functions for encrypting, cannot invert the function • Best to avoid spending from the same address many times • It is extremely hard to forge a signature even with observation • If your private key is exposed, your address is compromised . . .
- 27. Verifying Ownership in Blockchain Anybody Can Verify Ownership in a Transaction • Address of the funds being spent unlocks the transaction • Verification similar to the process between Alice and Bob • Nobody else but the owner of the address must have signed • Owning an address is equivalent to owning its private key • If your private key is exposed, ownership is lost forever As long as the private keys are secured It is practically impossible for someone to steal
- 28. Easy to Transact Hard to Modify
- 29. Consists of several computers called nodes Each node has its own private memory Nodes communicate with each other by messages Network structure is not known in advance Distributed Systems Nodes in the network may fail or may exhibit malicious behavior
- 30. Client-server: Designated servers accept clients Three-tier/n-tier: More organized structure Peer-to-peer: Every node can be a server or a client Distributed Systems Computation by a master node or by using a shared database Blockchain itself is the shared database
- 31. Consensus required: • Who holds correct data • Who can make changes • How are these rules enforced between nodes Let's not forget, there may be malicious nodes Distributed Systems Blockchain approach: Publicly verifiable data requires (hard) proof Tampering with data becomes exponentially harder as time passes
- 32. Advantages: • No need to trust any particular (central) node • Collective computation effort more powerful than what can be done by one central entity • Rules to be agreed on collectively • More resilient to certain forms of attacks Challenges: • Scalability in the number of transactions • Providing incentives for honest behavior and/or penalties for malicious behavior Distributed Systems
- 33. • Block number (height) • Latest transactions • Resulting changes to data • Pointer to previous block • Proof of validity Structure of the Blockchain …
- 34. • Each block stores a list of transactions • Similar to chain of title in real estate trxs, if we assume one trx per block. • For correctness, the entire chain must be valid Structure of the Blockchain
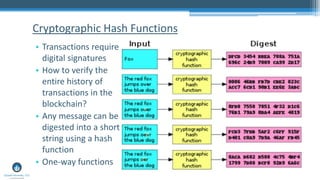
- 35. • Transactions require digital signatures • How to verify the entire history of transactions in the blockchain? • Any message can be digested into a short string using a hash function • One-way functions Cryptographic Hash Functions
- 36. • Cryptocurrency Bitcoin, Ethereum, Litecoin, etc. There are over 1000 different altcoins • Smart contracts Legal contracts which are enforced automatically • Asset management • Identity verification, notary, voting • Decentralized exchanges • Many more… Applications of Blockchain Technology
- 37. Cryptography & Distributed Systems Main Components of Blockchain
- 38. Story: Alice would like to send a very important message to Bob. She wants him to know that it is indeed her who sent the message. How can Alice accomplish this? Answer: One way functions and public key cryptography! Private and public keys to encrypt and to decrypt. Applications: Communications of any kind: internet, military, etc. Developments in cryptography created the field of computer science back in the 1940s. Public Key Cryptography
- 39. Illustration: • Alice produces private and public keys. • She publishes her public key to everyone. • Private key encrypts, public key decrypts. • Nobody can produce the same encryption without knowing the private key of Alice. Alice sends a message M to Bob: She encrypts M using her own private key: M ⟶ MA Bob decrypts the message from Alice: He decrypts message using Alice’s public key: MA ⟶ M Public Key Cryptography
- 40. Guarantees: Using Alice’s private key ensures that message is sent by Alice. Nobody else could have written it! Digital signatures: Encryption using a private key is called a “digital signature”. Digital signatures are enforceable in a court of law! Alice cannot claim that she did not send the message. Application in blockchain: Digital signatures are used to authenticate ownership. Payment addresses are generated by public keys. Public Key Cryptography
- 41. Verifying Ownership in Blockchain Public Key Cryptography to Prove Ownership • User creates a pair of public and private keys • Public key to generate and publish payment addresses • Private key to digitally sign for the funds in those addresses
- 42. Verifying Ownership in Blockchain Security of Public Key Cryptography • Brute force is a possible attack, but infeasible in general • One-way functions for encrypting, cannot invert the function • Best to avoid spending from the same address many times • It is extremely hard to forge a signature even with observation • If your private key is exposed, your address is compromised . . .
- 43. Verifying Ownership in Blockchain Anybody Can Verify Ownership in a Transaction • Address of the funds being spent unlocks the transaction • Verification similar to the process between Alice and Bob • Nobody else but the owner of the address must have signed • Owning an address is equivalent to owning its private key • If your private key is exposed, ownership is lost forever As long as the private keys are secured It is practically impossible for someone to steal
- 44. • Transactions require digital signatures • How to verify the entire history of transactions in the blockchain? • Any message can be digested into a short string using a hash function • One-way functions Cryptographic Hash Functions
- 45. Cryptography: • Validity of transactions can be verified quickly • Ownership is tied to the private keys • Each block can be digested into a string which proves the validity of the entire history Distributed Systems: • Trustless distributed public ledger • Creating a block is hard, so it is much harder to modify earlier blocks in the blockchain • Constantly audited by peers Main Components of Blockchain
- 46. Smart Homes, Smart Cars: • Ownership information can be recorded on the blockchain • Exchange of the ownership, money, keys (authority to use), can be transferred in the same single transaction • Crucial information related to the asset can also be recorded on the blockchain: past insurance claims, previous owners • Very reliable: any crucial information recorded on the blockchain cannot be modified later Applications of Blockchain Technology
- 47. Identity, Notary, Voting: • Self identifying information is required in any business transaction: photo ID, passport, etc • This information can be stored on the blockchain and the proof of identity can be produced without any government backing • One can prove identity by just simply using the private key • Claims about the identify of Satoshi Nakamoto was made based on the use of one of his/their private keys Applications of Blockchain Technology
- 48. Decentralized Exchanges: • Exchange of two assets is generally carried out by a trusted third party that acts as escrow • Central entity controlling the exchange can be the subject of an attack resulting in the loss of deposits • Such incidents can be eliminated via exchanging the assets by using an escrow for the transaction on the blockchain itself • Swap will be carried out when both parties sign the transaction Applications of Blockchain Technology
- 49. Private Blockchain: • Even though the main motivation to introduce the blockchain technology was to remove trust, settings where there is a trusted entity can still enjoy the benefits of using a blockchain • Automated maintenance and auditing of records • No need for consensus. The blockchain is truly an append only ledger. Once written, the past is indeed set in stone • Requires full trust in the centralized node(s) issuing the blocks Applications of Blockchain Technology
- 50. 50 • Coming in 2018 to Boston, NYC, Chicago, San Francisco and online! • Sign up at www.analyticscertificate.com/Blockchain-ML for updates! Blockchain workshop
- 51. 51 Q&A
- 52. Thank you members and CIC! Checkout our programs at: www.analyticscertificate.com Sri Krishnamurthy, CFA, CAP Founder and CEO QuantUniversity LLC. srikrishnamurthy www.QuantUniversity.com Information, data and drawings embodied in this presentation are strictly a property of QuantUniversity LLC. and shall not be distributed or used in any other publication without the prior written consent of QuantUniversity LLC. 52