Cisco Network Insider: Three Ways to Secure your Network
- 1. 3 Ways to Secure Your Network Presenters: Robb Boyd, Ziad Sarieddine, Beth Barach, Player Pate, Guy Telner June 14, 2016
- 2. What is on my network and why does it matter?
- 3. Stop and contain threats What visibility can help you do See and share rich user and device details Control all access throughout the network from one place
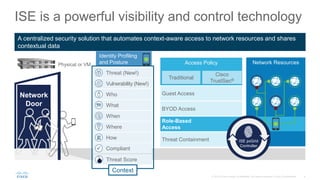
- 4. ISE is a powerful visibility and control technology Network ResourcesAccess Policy Traditional Cisco TrustSec® BYOD Access Threat Containment Guest Access Role-Based Access Identity Profiling and Posture A centralized security solution that automates context-aware access to network resources and shares contextual data Network Door Physical or VM ISE pxGrid Controller Who Compliant What When Where How Context Threat (New!) Vulnerability (New!) Threat Score
- 5. 5© 2016 Cisco and/or its affiliates. All rights reserved.
- 6. 6© 2016 Cisco and/or its affiliates. All rights reserved.
- 7. 7© 2016 Cisco and/or its affiliates. All rights reserved.
- 8. 8© 2016 Cisco and/or its affiliates. All rights reserved.
- 9. 9© 2016 Cisco and/or its affiliates. All rights reserved.
- 10. 10© 2016 Cisco and/or its affiliates. All rights reserved. Coffee break
- 11. 11© 2016 Cisco and/or its affiliates. All rights reserved.
- 12. I have identity & device! I need geo- location & MDM… I have application info! I need location & device-type I have location! I need app & identity… ISE I have sec events! I need identity & device… I have MDM info! I need location… ISE pxGrid Open* sharing to get answers faster. Control to stop threats ISE pxGrid Any-Any Sharing • Publish • Subscribe ISE Sharing • Identity Context ISE Network Control • Adaptive Network Control * IETF Standards Track: Managed Incident Lightweight Exchange (MILE)
- 13. Switch Router Stealthwatch WirelessAD pxGridISENetwork Making visibility more effective through sharing 1. Identify what it is: ISE creates identity context: user, device type, posture, authorization level, location, threat score? 2. Share the identity context ISE shares with behavioral analysis technology “It looks like Kevin on a Lenovo X1 Carbon MS Laptop and he’s clean.” “Hey ISE, let’s put Kevin in quarantine until he cleans up his act” “Looks like Kevin’s laptop has been infected with malware.” 3. Watch the behaviors Monitor device behaviors for anomalies 4. Stop bad things Take action to contain a device through ISE using the network as an enforcer “Hey Stealthwatch, here’s the detail on that IP address you’re asking about.” “Roger that Stealthwatch. Hey network, put Kevin into quarantine until I tell you to let him back on.”
- 14. Cisco Stealthwatch and Cisco ISE pxGrid Real-Time Visibility into All Network Layers • Data intelligence throughout network • Discovery of assets • Network profile • Security policy monitoring • Anomaly detection • Accelerated incident response Cisco® Identity Services Engine Mitigation Action Context Information NetFlow Cisco Stealthwatch
- 15. Cisco Stealthwatch and ISE Integration
- 16. Stealthwatch and ISE Integration
- 17. Visibility Through NetFlow 10.1.8.3 172.168.134.2 Internet Flow Information Packets SOURCE ADDRESS 10.1.8.3 DESTINATION ADDRESS 172.168.134.2 SOURCE PORT 47321 DESTINATION PORT 443 INTERFACE Gi0/0/0 IP TOS 0x00 IP PROTOCOL 6 NEXT HOP 172.168.25.1 TCP FLAGS 0x1A SOURCE SGT 100 : : APPLICATION NAME NBAR SECURE- HTTP RoutersSwitches Visibility into every network conversation: • Every record • Every device • Everywhere
- 18. Conversational Flow Record • Highly scalable (enterprise-class) collection • High compression => long-term storage • Months of data retention When Who Where What Who Security group More context
- 19. Behavioral and Anomaly Detection Model Behavioral Algorithms Are Applied to Build “Security Events” SECURITY EVENTS (94 +) ALARM CATEGORY RESPONSE Addr_Scan/tcp Addr_Scan/udp Bad_Flag_ACK** Beaconing Host Bot Command Control Server Bot Infected Host - Attempted Bot Infected Host - Successful Flow_Denied . . ICMP Flood . . Max Flows Initiated Max Flows Served . Suspect Long Flow Suspect UDP Activity SYN Flood Concern Exfiltration C&C Recon Data hoarding Exploitation DDoS target Alarm table Host snapshot Email Syslog / SIEM Mitigation COLLECT AND ANALYZE FLOWS FLOWS
- 20. Cisco Stealthwatch Demo - Dashboard
- 21. List of Alarms for Data Exfiltration Alarm Triggers
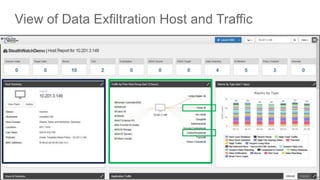
- 22. View of Data Exfiltration Host and Traffic
- 24. Data Exfiltration Traffic Details
- 25. Stealthwatch for Macro-Level Visibility Fight advanced threats with actionable intelligence and analytics • Obtain comprehensive, scalable enterprise visibility and security context • Gain real-time situational awareness of traffic • Benefit from network segmentation • Detect and analyze network behavior anomalies • Easily detect behaviors linked to advanced persistent threats (APTs), insider threats, distributed denial-of- service (DDoS) attacks, and malware • Collect and analyze holistic network audit trails • Achieve faster root cause analysis • Conduct thorough forensic investigations • Accelerate network troubleshooting and threat mitigation • Respond quickly to threats by taking action to quarantine through Cisco® Identity Services Engine • Continuously improve enterprise security posture Monitor Detect Analyze Respond
- 26. Visibility from the Core to the Edge
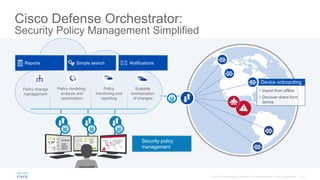
- 27. Cisco Defense Orchestrator: Security Policy Management Simplified Policy change management Policy modeling, analysis and optimization Policy monitoring and reporting Scalable orchestration of changes Simple searchReports Notifications Security policy management • Import from offline • Discover direct from device Device onboarding
- 28. 28© 2016 Cisco and/or its affiliates. All rights reserved. Next Steps For further information on Technology 1 Technology 2 Technology 3 Please visit the Cisco Security page: http://www.cisco.com/c/en/us/products/security/index.html Register for the next event in the Cisco Network Insider series “Cisco Mobility for Hospitality” on June 28 at 10am PT/ 1pm ET https://grs.cisco.com/grsx/cust/grsEventSite.html?EventCode=14207&LanguageId=1&KeyCode= Thank you for your participation!
- 29. Check us out on cisco.com/go/security to learn more about: ISE Stealthwatch Cisco Defense Orchestrator
Editor's Notes
- Visibility is Key to making this a reality.
- And ISE is our identity technology to identify what something is (explain context) and control where it can go (this seems to be a more proper place to discuss CVSS and STIX, but I think it is too much information. Keep your points simple . Notice I added threat score to context. I’m not sure if we can represent it this way (can we share threat score that we take in?) What is Cisco ISE? ISE is a centralized security solution that automates context-aware access to network resources and shares contextual data. Here’s how it works… In reality, you have many different types of users trying to get onto a network. In this case, not a an employee, but also not a guest. The contractor needs access, perhaps only temporarily, to certain network resources in order to do her job effectively and efficiently. ISE collects contextual data from the network (like DHCP, NetFlow, etc.), the type of device, and the user identity (e.g., from Active Directory) and pulls that information in. It also collects context from integrated partners when evaluating posture or compliance. Now, with a contextual identity established, ISE is able to bring together these disparate pieces of data to a single location and make a more fully-informed decision regarding access. ISE now incorporates vulnerability assessment and threat incident intelligence to drive network policy. This also allows ISE to change network privileges dynamically in the event that an endpoint’s threat score changes. Here, the contractor may get access to certain file servers and the employee intranet, but obviously not admin servers, etc. Other examples include: You’re a visitor…you get guest access. You’re a corporate employee on an iPad…you get employee access that varies depending whether your device is a corporate or non-corporate managed asset. And different employees can get access to different parts on the network based on their specific business roles and data requirements. An HR employee will get access to employee personal records, while a finance executive will have access to financial data, but not necessarily HR records. And of course, if you’re using a device that is compromised with malware or just not compliant…you get zero access to the network. By eliminating these unknowns and ensuring device compliance, we’re able to provide the RIGHT level of access to the RIGHT user at the RIGHT time while reducing the overall attack surface by preventing compromised entities from gaining access in the first place. These role-based access policies enabled through segmentations, accomplished either traditionally, or with Cisco’s TrustSec, which allow you to dynamically segment your network without the complexity of VLANs and ACLs. You can also share all the rich contextual information you gather with your other Cisco solutions and your partner ecosystem through pxGrid technology. And the best part – you can deploy ISE with a single physical appliance or run it on a virtual machine. T: With deeper visibility and context, we get more accurate identification, which ensures that users and devices are onboarded seamlessly with greater, more granular security, and your network is protected from threats. <click>
- SCRIPT – Segway from Rob or Ziad So as Ziad was mentioning how ISE can be integrated with other technologies using pxGrid, we also have an integration with Cisco ISE and Stealthwatch via pxGrid to automatically share that data for behavioral analysis So first I’m going to talk a bit about that integration and show how it works and then I’ll talk a bit more about how Steathwatch leverages Neflow to gain visibility into all network layers and look for anamolous behavoiral patterns that it shares with ISE. On the left here you’ll see Cisco ISE which gives you the contextual information as Ziad previously mentioned. Cisco Stealthwatch uses Netflow, as well as IPFIX, jflow, sflow, and collects these flows to establish a baseline of normal network behavior. It not only collects the flows but also has a very extensive Network Behavior and Anomaly detection engine. It creates security events, which are composed of algorithms that analyze flows and activity looking for certain patterns. Events feed into high level alarm categories; which can generate an alarm and alarms can be created manually as well All the security events in alarm categories can be responded to through to the user interface, and snapshot views that describe host behavior - it can also be sent in a syslog message to a SIEM Mitigation can also happen by initiating a command back to an inline device such as Cisco ISE to stop the traffic as close to the host as possible And I’ll show you how this works
- So right from within the Cisco Stealthwatch Management console an action can be taken You’ll notice that within this host report for this particular alarm there is a Quarantine button right within the Stealthwatch management console. After investigating this alarm if the user decides that this user should be quarantined for further investigation they can simply click the button right from within the Stealthwatch management console.
- Once the Stealthwatch user clicks the quarrantine button a message is automatically sent to ISE to quarantine this user and host for further investigation. The user can then go into their ISE management console for deeper investigation of the user and incident Additionally, Stealthwatch stores network flow information for forensic purposes so deeper investigation can be done into this incident on the Stealthwatch side as well.
- So now that we’ve seen the Stealthwatch and ISE integration, I’m going to talk a bit more about how Stealthwatch leverages your network as a security sensor and then walk through a demo of how you can drill into an event such as data exfiltration happening on your network. So as I am sure you are aware Cisco Netflow Provides flow information A trace of every conversation in your network An ability to collect records everywhere in your network (switch, router, or firewall) Cisco Stealthwtach takes all of this netflow collection and turns it into visibility into your network to find those users out of policy or bad actors who have stolen your users credentials and are trying to breach your network Stealthwatch can look at both north-south as well as east-west communication across the network.
- Cisco Steathwatch takes these Netflow records and gives you detailed visibility into the conversation that is happening with every user across the entire network It tells you when and how long a conversation has started, what user is having that conversation, who that user is talking to on what protocol and IP address You can also gain detailed information about that user such as what group that user has been assigned to in order to determine if that user is acting out of policy. This is a highly scalable solution that retains and stores netflow in order to accelerate incident response and investigation
- Host behavior is compared to behavior today vs. historic behavior – if host behavior changes, security events will begin to be triggered. As security events are being detected ,points are being assigned to one or more alarm categories to build a reputation score of suspicious behavior The concern index is a method to identify which host is acting most suspicious and displays the host in a stacked rank order of greatest to least threat All the security events in alarm categories can be responded to through to the user interface, and snapshot views that describe host behavior - it can also be sent in a syslog message to a SIEM As I mentioned previously, Mitigation can also happen by initiating a command back to an inline device such as Cisco ISE or even to a Firewall to stop the traffic as close to the host as possible
- So let’s take a look into the Stealthwatch Management Console – particularly an event of data exfiltration. Here you’re seeing the dashboard of all of the alarms – these alarms are generated by Stealthwatch and users can also set thresholds for when and what triggers an alarm
- So let’s take a look into a list for a particular IP address that has 5 data exfiltration alarms tied to it You’ll note from the box around the details that this alarm was triggered because the rule that was set, was that anything over 500K points should trigger an alarm. These alarms were triggered because that limit was exceeded
- So we can see the host summary in the blue box – the host name, groups the host is associated with, where it is located, what policies have been violated and its MAC address ISE is gives us deep contextual information as Ziad previously mentioned. In the green box we can see the peers associated with this host group as well as where the traffic is going to – considering it is going to China and Russian Federation we may want to look more deeply into those hosts
- To get more details into these suspicious network conversations you build a flow query. You start the query by running a flow table to find the conversation in your network. You can edit the filters to change between hosts, for example, inside to outside the network. You can search for user names within a flow, or mac address, search specific date ranges and specific ports You can also search for flows that crosses specific interfaces on your network, have specific routing tags such as TrustSec IDs, or other traffic criteria
- This is an example of some flow query results that are filtered on the drill down into the detail about China You will notice these give you details about the conversation on the network that has been happening with China – in the far right hand side of the screen in the blue box it tells you who this host has been talking to including the IP address in China The far left green box tells you when this conversation took place The red box tells you who was having this conversation, in this place Ken from workstation 149 and also where this took place, on ip address 10.201.3.149
- So in closing Stealthwatch gives you need visibility with actionable intelligence and analytics To Monitor, Detect Analyze and respond to network threats.
- As important as it is to get visibility at the edge of your network …visibiluty into your security posture across your branch or retail locations is also critical
- As security devices multiply across your network, policy change requests continue to flood in making policy management nearly impossible. One hasty change can lead to an unwanted chain reaction exposing your entire company to a potential security threat. As a network administrator, you need a simple centralized solution to manage all your security policies and strengthen your security across your entire network. Introducing Cisco Defense Orchestrator, a new cloud-based security policy management solution for Cisco security products. Now you can cut through the complexity and manage all your security policies from one place. CDO’s comprehensive view provides easy optimization, configuration and management of policies across different security devices, whether you have dozens or thousands of locations. Easily spot misconfigurations and inconsistencies across devices and make policy changes quickly. Finally see and understand your overall security posture without having to be a security expert. Reduce risk and deploy new devices faster by creating standardized policy templates that establish consistent security configurations. Modeling changes before deployment helps you understand their security implications to your network. Changes are made either in real time or offline, and verified to ensure that right changes have been made. Visualize how your policy enforcement is working with combined information about top applications, destinations, categories, attacks and risks. Quickly and easily take advantage of new next generation firewall capabilities without adding complexity to your operations. Our cloud-based solution reduces time to deployment, cuts capital costs and scales seamlessly as your business grows.