Computer security overview
- 1. COMPUTER SECURITY COMPUTER SECURITY - OVERVIEW
- 2. CONTENT 1.1 COMPUTER SECURITY 1.2 KEY SECURITY CONCEPTS 1.3 SECURITY TERMINOLOGY 1.4 VULNERABILITY 1.5 THREATS 1.6 ATTACKS 1.7 ATTACK SURFACES 1.8 THREAT CONSEQUENCES 1.9 COUNTERMEASURES 1.10 CYBERCRIME INCIDENTS IN OMAN 1.11 SECURITY TECHNOLOGIES IN USE - GLOBAL 2 COMPUTER SECURITY OVERVIEW
- 3. 1.1 COMPUTER SECURITY: • Computer security is the ability of a computer system to protect information with respect to confidentiality and integrity. • Computer security is often associated with three core areas, summarized with the CIA acronym: • Confidentiality (ensuring that information is not accessed by unauthorized individuals) • Integrity (ensuring that information is not altered by unauthorized individuals) • Availability (ensuring that the information concerned is readily accessible to the authorized individuals at all times) 3 COMPUTER SECURITY OVERVIEW
- 4. 1.2 KEY SECURITY CONCEPTS 4 1. Confidentiality: Preserving authorized restrictions on information access and disclosure. 2. Integrity: Guarding against improper information modification or destruction. 3. Availability: Ensuring timely and reliable access to and use of information. 4. Authenticity: The property of being genuine and being able to be verified and trusted; confidence in the validity of a transmission, a message, or message originator. 5. Non-Repudiation: is a way to guarantee that the sender of a message cannot later deny having sent the message and that the recipient cannot deny having received the message. COMPUTER SECURITY OVERVIEW
- 5. 1.3 SECURITY TERMINOLOGY 1. Adversary (threat agent) - An entity that attacks, or is a threat to, a system. 2. Attack -An assault on system security that derives from an intelligent threat; a deliberate attempt to evade security services and violate security policy of a system. 3. Countermeasure - An action, device, procedure, or technique that reduces a threat, a vulnerability, or an attack by eliminating or preventing it, by minimizing the harm it can cause. 4. Risk - An expectation of loss expressed that a particular threat will exploit a particular vulnerability with a particular harmful result. 5 COMPUTER SECURITY OVERVIEW
- 6. 5. Security Policy - A set of rules and practices that specify how a system or an organization provides security services to protect sensitive and critical system resources. 6. Threat - A potential for violation of security, which exists when there is a circumstance, capability, action, or event that could breach security and cause harm. 7. Vulnerability - Flaw or weakness in a system's design, implementation, or operation and management that could be exploited to violate the system's security policy. 6 COMPUTER SECURITY OVERVIEW
- 7. 1.4 VULNERABILITY • A vulnerability is a weakness in the security system (for example, in procedures, design, or implementation), that might be exploited to cause loss or harm. • System resource vulnerabilities may – Be corrupted – Become leaky – Become unavailable • Corrupted: Does the wrong thing or gives wrong answers. (Loss of Integrity) • Leaky: Someone who should not have access to the information will avail. (Loss of Confidentiality) • Unavailable: Otherwise very slow. e.g. using the system / network impossible. (Loss of availability) 7 COMPUTER SECURITY OVERVIEW
- 8. 1.4.1 TYPES OF VULNERABILITIES • Hardware Vulnerabilities – adding devices, changing them, removing them, intercepting the traffic to them, or flooding them with traffic until they can no longer function. (many other ways to harm the hardware). • Software Vulnerabilities – Software can be replaced, changed, or destroyed maliciously, or it can be modified, deleted, or misplaced accidentally. Whether intentional or not, these attacks exploit the software's vulnerabilities. • Data Vulnerabilities – data have a definite value, even though that value is often difficult to measure. 8 COMPUTER SECURITY OVERVIEW
- 9. 1.5 THREATS • A threat to a computing system is a set of circumstances that has the potential to cause loss or harm. • We can view any threat as being one of four kinds: interception, interruption, modification, and fabrication. 9 COMPUTER SECURITY OVERVIEW
- 10. • An interception means that some unauthorized party has gained access to an asset. • In an interruption, an asset of the system becomes lost, unavailable, or unusable. • If an unauthorized party not only accesses but tampers with an asset, the threat is a modification. • Finally, an unauthorized party might create a fabrication of counterfeit objects on a computing system. 10 COMPUTER SECURITY OVERVIEW
- 11. 1.6 ATTACKS 11 COMPUTER SECURITY OVERVIEW
- 12. 1.6.1 CLASSIFICATION OF ATTACKS BASED ON THE ORIGIN • Inside attack: Initiated by an entity inside the security perimeter (“Insider”). • Outside attack: Initiated from outside the perimeter, by an unauthorized or illegitimate user of the system ("outsider"). 1.6.2 TYPES OF ATTACKS: • Active attack: Attempts to alter system resources or affect their operation. • Passive attack: attempts to learn or make use of information from the system but does not affect system resources 12 COMPUTER SECURITY OVERVIEW
- 13. PASSIVE AND ACTIVE ATTACKS - DIFFERENCES 13 Passive Attack Active Attack Attempts to learn or make use of information from the system but does not affect system resources. Attempts to alter system resources or affect their operation. Eavesdropping on, or monitoring of, transmissions. Involve some modification of the data stream or the creation of a false stream. Goal of attacker is to obtain information that is being transmitted Goal of attacker is to damage any system. Two types: 1. Release of message contents 2. Traffic analysis Four categories: 1. Replay 2. Masquerade 3. Modification of messages 4. Denial of service COMPUTER SECURITY OVERVIEW
- 14. 1.7 ATTACK SURFACES 14 • Consist of the reachable and exploitable vulnerabilities in a system. • Three types of attack surfaces 1. Network Attack Surface - Vulnerabilities over an enterprise network, wide-area network, or the Internet 2. Software Attack Surface - Vulnerabilities in application, utility, or operating system code 3. Human Attack Surface - Vulnerabilities created by personnel or outsiders, such as social engineering, human error, and trusted insiders. COMPUTER SECURITY OVERVIEW
- 15. 1.8 Threat Consequences RFC 2828 describes four kinds of threat consequences and kinds of attacks that result: 15 1. Unauthorized disclosure 1. Exposure 2. Interception 3. Inference 4. Intrusion 2. Deception 1. Masquerade 2. Falsification 3. Repudiation 3. Disruption 1. Incapacitation 2. Corruption 3. Obstruction 4. Usurpation 1. Misappropriation 2. Misuse COMPUTER SECURITY OVERVIEW
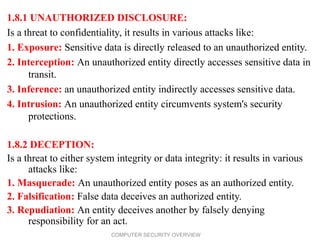
- 16. 1.8.1 UNAUTHORIZED DISCLOSURE: Is a threat to confidentiality, it results in various attacks like: 1. Exposure: Sensitive data is directly released to an unauthorized entity. 2. Interception: An unauthorized entity directly accesses sensitive data in transit. 3. Inference: an unauthorized entity indirectly accesses sensitive data. 4. Intrusion: An unauthorized entity circumvents system's security protections. 1.8.2 DECEPTION: Is a threat to either system integrity or data integrity: it results in various attacks like: 1. Masquerade: An unauthorized entity poses as an authorized entity. 2. Falsification: False data deceives an authorized entity. 3. Repudiation: An entity deceives another by falsely denying responsibility for an act. 16 COMPUTER SECURITY OVERVIEW
- 17. 1.8.3 DISRUPTION: Is a threat to availability or system integrity: it results in various attacks like: 1. Incapacitation: Prevent/interrupt system operation by disabling a system component 2. Corruption: adversely modifying system functions or data 3. Obstruction: interrupts delivery of system services by hindering system operation. 1.8.4 USURPATION: Is a threat to system integrity: it results in various attacks like: 1. Misappropriation: unauthorized logical or physical control of a system resource. 2. Misuse: Causes system to perform a function or service detrimental to security. 17 COMPUTER SECURITY OVERVIEW
- 18. 1.9 COUNTERMEASURES • Countermeasures is any means used to deal with security attacks • Goal is to minimize risk given constraints • May result in new vulnerabilities • Countermeasure can be devised to – Prevent a particular type of attack – Detect the attacker and the type of attack – Recover from the effects of the attack 18 COMPUTER SECURITY OVERVIEW
- 19. 1.10 CYBERCRIME INCIDENTS IN OMAN • The increase in the number of internet usage and online transactions has increased the number of cybercrime incidents in Oman. • As per the annual report of ITA 2012: • # of malicious attempts against secure government portals that were prevented and analyzed was 97,322. • Compared to 2011, there was an increase of 13.5% reported incidents. • There was 200% increase in malware attacks in 2012, compared to 2011. 19 COMPUTER SECURITY OVERVIEW
- 20. 20 Number and classification of incidents – 2012 (Source: ITA Annual report 2012) COMPUTER SECURITY OVERVIEW
- 21. • As per the ITA annual report 2013: • 1,084,369 malicious attempts against government portals. • 19,171 malicious attempts against government networks were prevented and analyzed. • It has scanned 9,890 IPs and discovered 25,827 vulnerabilities. • 10,940 spywares were analyzed. • 941,079 malicious wares were analyzed. • 659,090 web violations were analyzed and prevented. 21 COMPUTER SECURITY OVERVIEW
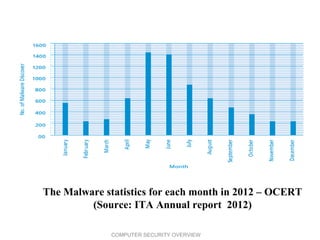
- 22. 22 The Malware statistics for each month in 2012 – OCERT (Source: ITA Annual report 2012) COMPUTER SECURITY OVERVIEW
- 23. 1.11 SECURITY TECHNOLOGIES IN USE -GLOBAL 23 COMPUTER SECURITY OVERVIEW
Editor's Notes
- Network security attacks can be classified as passive attacks and active attacks . A passive attack attempts to learn or make use of information from the system but does not affect system resources. An active attack attempts to alter system resources or affect their operation. Passive attacks are in the nature of eavesdropping on, or monitoring of, transmissions. The goal of the attacker is to obtain information that is being transmitted. Two types of passive attacks are release of message contents and traffic analysis. The release of message contents is easily understood. A telephone conversation, an electronic mail message, and a transferred file may contain sensitive or confidential information. We would like to prevent an opponent from learning the contents of these transmissions. A second type of passive attack, traffic analysis , is subtler. Suppose that we had a way of masking the contents of messages or other information traffic so that opponents, even if they captured the message, could not extract the information from the message. The common technique for masking contents is encryption. If we had encryption protection in place, an opponent might still be able to observe the pattern of these messages. The opponent could determine the location and identity of communicating hosts and could observe the frequency and length of messages being exchanged. This information might be useful in guessing the nature of the communication that was taking place. Passive attacks are very difficult to detect because they do not involve any alteration of the data. Typically, the message traffic is sent and received in an apparently normal fashion and neither the sender nor receiver is aware that a third party has read the messages or observed the traffic pattern. However, it is feasible to prevent the success of these attacks, usually by means of encryption. Thus, the emphasis in dealing with passive attacks is on prevention rather than detection. Active attacks involve some modification of the data stream or the creation of a false stream and can be subdivided into four categories: replay, masquerade, modification of messages, and denial of service. Replay involves the passive capture of a data unit and its subsequent retransmission to produce an unauthorized effect. A masquerade takes place when one entity pretends to be a different entity. A masquerade attack usually includes one of the other forms of active attack. For example, authentication sequences can be captured and replayed after a valid authentication sequence has taken place, thus enabling an authorized entity with few privileges to obtain extra privileges by impersonating an entity that has those privileges. Modification of messages simply means that some portion of a legitimate message is altered, or that messages are delayed or reordered, to produce an unauthorized effect. For example, a message stating, “Allow John Smith to read confidential file accounts” is modified to say, “Allow Fred Brown to read confidential file accounts.” The denial of service prevents or inhibits the normal use or management of communications facilities. This attack may have a specific target; for example, an entity may suppress all messages directed to a particular destination (e.g., the security audit service). Another form of service denial is the disruption of an entire network, either by disabling the network or by overloading it with messages so as to degrade performance. Active attacks present the opposite characteristics of passive attacks. Whereas passive attacks are difficult to detect, measures are available to prevent their success. On the other hand, it is quite difficult to prevent active attacks absolutely, because to do so would require physical protection of all communications facilities and paths at all times. Instead, the goal is to detect them and to recover from any disruption or delays caused by them. Because the detection has a deterrent effect, it may also contribute to prevention.
- Figure 1.8here, also from the CSI/FBI Computer Crime and Security Survey for 2006, indicates the types of security technology used by organizations to counter threats. Both firewalls and anti-virus software are used almost universally. This popularity reflects a number of factors: • The maturity of these technologies means that security administrators are very familiar with the products and are confident of their effectiveness. • Because these technologies are mature and there are a number of vendors, costs tend to be quite reasonable and user-friendly interfaces are available • The threats countered by these technologies are among the most significant facing security administrators.