.conf Go Zurich 2022 - Security Session
- 1. © 2022 SPLUNK INC. Security Session October 4th, Zurich
- 2. © 2022 SPLUNK INC.
- 3. © 2022 SPLUNK INC. Speaker Security Advisor Le-Khanh Au Manager Sales Engineering | Alps Security Spearhead Juerg Fischer
- 4. © 2022 SPLUNK INC. Agenda Cyber Security Resilience PMI Story: Application Monitoring at Scale Top 3 CISO priorities Conclusion
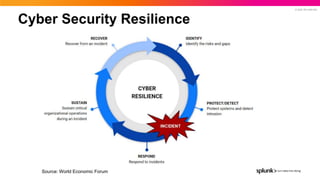
- 5. © 2022 SPLUNK INC. Cyber Security Resilience Source: World Economic Forum
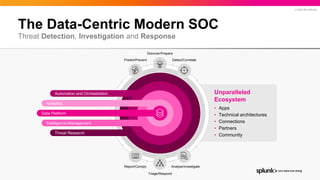
- 6. © 2022 SPLUNK INC. The Data-Centric Modern SOC Threat Detection, Investigation and Response Data Platform Intelligence Management Threat Research Analytics Automation and Orchestration Detect/Correlate Predict/Prevent Discover/Prepare Analyze/Investigate Report/Comply Triage/Respond Unparalleled Ecosystem • Apps • Technical architectures • Connections • Partners • Community
- 7. © 2022 SPLUNK INC. Application Monitoring at Scale
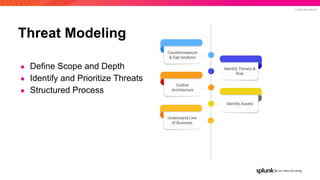
- 8. © 2022 SPLUNK INC. Threat Modeling ● Define Scope and Depth ● Identify and Prioritize Threats ● Structured Process Identify Assets Identify Threats & Risk Understand Line of Business Countermeasure & Gap Analysis Outline Architecture
- 9. © 2022 SPLUNK INC. Challenge ● Complex Process ● Lack of Engagement ● Asset Repository & Scoping ● Legacy Systems
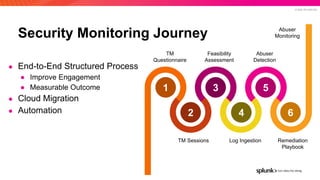
- 10. © 2022 SPLUNK INC. Security Monitoring Journey ● End-to-End Structured Process ● Improve Engagement ● Measurable Outcome ● Cloud Migration ● Automation 3 1 5 2 4 6 TM Questionnaire Feasibility Assessment Abuser Detection TM Sessions Log Ingestion Remediation Playbook Abuser Monitoring
- 11. © 2022 SPLUNK INC. Self-service Splunk Infrastructure ● Cloud-native Ingestion Pipelines ● Alert Creation/Management Pipelines ● Community Contribution ● Traceability
- 12. © 2022 SPLUNK INC. ● Structured Process ● Automation & Self-service Model Take-aways
- 13. © 2022 SPLUNK INC. Top 3 CISO priorities
- 14. © 2022 SPLUNK INC. CISO Prio 1
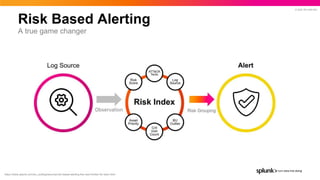
- 15. © 2022 SPLUNK INC. Risk Based Alerting A true game changer https://www.splunk.com/en_us/blog/security/risk-based-alerting-the-new-frontier-for-siem.html
- 16. © 2022 SPLUNK INC. How Does This Look in Practice? With risk-based alerting, these events become context that informs high-fidelity alerts Risk Incident Rule: Generate alert for any user or system that exceeds a risk score of 100 in a 24 hour period Aggregated user risk score >100 ALERT With one click, view all of the risk events that contribute to the alert Potential spearphishing observed 10 pts Suspicious command disabling controls 15 pts Suspicious Powershell observed 20 pts AWS ACLs opened up all access 10 pts AWS user provisioning observed 15 pts AWS buckets created 15 pts AWS permanent creation observed 20 pts 6:55AM 6:58AM 7:03AM 1:55PM 2:03PM 2:07PM 2:15PM
- 17. © 2022 SPLUNK INC. CISO Prio 2
- 18. © 2022 SPLUNK INC. Use Case Development CIS Top 20 Controls Recommended set of actions for cyber defense that provide specific and actionable ways to stop today's most pervasive and dangerous attacks Different Frameworks/Process Flows MITRE ATT&CK MITRE ATT&CK® is a globally-accessible knowledge base of adversary tactics and techniques based on real-world observations. Customer specific use cases To organize use cases, a use case framework should be used. Such frame- works enable control over use cases and provide insight into identify how well an organization is capable of defending against cyber threats. Content Description 01 - Inventory of Authorized and Unauthorized Devices Actively manage (inventory, track, and correct) all hardware devices on the network so that only authorized devices are given access, and unauthorized and unmanaged devices are found and prevented from gaining access. 02 - Inventory of Authorized and Unauthorized Software Actively manage (inventory, track, and correct) all software on the network so that only authorized software is installed and can execute, and that unauthorized and unmanaged software is found and prevented from installation or execution. 03 - Secure Configurations for Hardware and Software Establish, implement, and actively manage (track, report on, correct) the security configuration of mobile devices, laptops, servers, and workstations using a rigorous configuration management and change control process in order to prevent attackers from exploiting vulnerable services and settings.
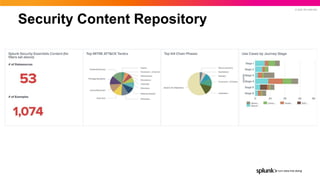
- 19. © 2022 SPLUNK INC. Security Content Repository
- 20. © 2022 SPLUNK INC. Prescriptive Content What To Do Next? Security Essentials understands what data you have, and what content you already use. It uses that to recommend
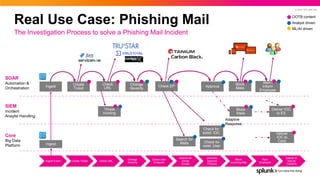
- 21. © 2022 SPLUNK INC. Deliver IOC to ES Alert / Inform Employee Change Severity Check EP Search for Mails Approve Block Mails Check URL Real Use Case: Phishing Mail The Investigation Process to solve a Phishing Mail Incident Core Big Data Platform SIEM Incident Anaylst Handling SOAR Automation & Orchestration Ingest Threat Hunting Check for exiist. IOC Check for exist. User OOTB content Analyst driven ML/AI driven Ingest Event Create Ticket Check URL Change Severity Check User Endpoint Search for similar Emails (Human) Approve Process Block incoming Mail Alert Employes Deliver to Splunk Core/ES Ingest Create Ticket Deliver IOC to Core Block Mails Adaptive Response
- 22. © 2022 SPLUNK INC. Security PVP - Your Security Maturity Index, Search, Monitor & Alert Level 1 ● Use of Pre-built Content ● Centralized Retention and Visibility for all Data ● Security Monitoring Dashboards ● Alerting ● Basic Reporting ● Ad-Hoc Investigation and Incident Response ● Historical Data Analysis 55% Normalize, Correlate & Risk Level 2 ● Data Normalization ● Security Use Case Library ● Risk Awareness and Alert Prioritization ● Threat Intelligence ● Information and Event Correlation ● Notable Event Management ● Triage & Investigation Workflows 50% Collaborate, Hunt & ML Level 3 ● Risk Based Alerting ● Insider Threat Detection ● Semi-Automated Playbooks (Orchestration & Response) ● Pre-Built Machine Learning security content ● Threat Hunting ● Continuous Use Case development ● Incident Collaboration 26% Simulate, Respond & Fully Automate Level 4 ● Risk Reporting ● Full Playbook Automation ● Custom Machine Learning security content ● Stream Processing and stream Analytics ● Attack Simulation ● Effective collaboration & integration with other teams or tools ● Breach Response 36% Security Maturity Reactive Proactive 42% green - implemented | orange - to be implemented medium term | red - highly recommended for the security posture xx% - Maturity today
- 23. © 2022 SPLUNK INC. CISO Prio 3
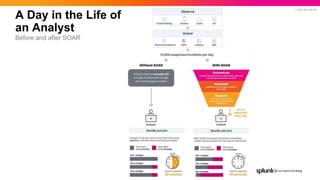
- 24. © 2022 SPLUNK INC. A Day in the Life of an Analyst Before and after SOAR
- 25. © 2021 SPLUNK INC. © 2022 SPLUNK INC. 97%agree that a SOAR allowed for increased workload maintaining the same number of staff
- 26. © 2022 SPLUNK INC. Conclusion
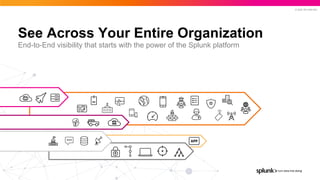
- 27. © 2022 SPLUNK INC. See Across Your Entire Organization End-to-End visibility that starts with the power of the Splunk platform
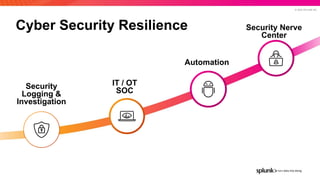
- 28. © 2022 SPLUNK INC. Cyber Security Resilience Security Logging & Investigation IT / OT SOC Automation Security Nerve Center © 2022 SPLUNK INC.
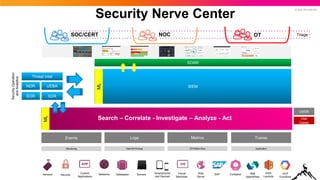
- 29. © 2022 SPLUNK INC. Monitoring Net/OS/Virt/App CPU/Mem/Disc Events Logs Metrics Application Traces Databases Networks Servers Virtual Machines Smartphones and Devices Custom Applications Security Web Server Sensors SAP Container IBM OpenWhisk AWS Lambda GCP Functions SIEM SOAR SOC/CERT Triage EDR NDR XDR UEBA Security Operation and Analytics NOC OT CMDB Threat Intel Use Cases ML ML Security Nerve Center Search – Correlate - Investigate – Analyze - Act
- 30. © 2022 SPLUNK INC. Databases Networks Servers Virtual Machines Smartphones and Devices Custom Applications Security Web Server Sensors SAP Container IBM OpenWhisk AWS Lambda GCP Functions SIEM SOAR SOC/CERT Triage EDR NDR XDR UEBA Security Operation and Analytics NOC OT CMDB Threat Intel Use Cases ML ML Security Nerve Center Search – Correlate - Investigate – Analyze - Act Monitoring Net/OS/Virt/App CPU/Mem/Disc Events Logs Metrics Application Traces
- 31. © 2022 SPLUNK INC. Databases Networks Servers Virtual Machines Smartphones and Devices Custom Applications Security Web Server Sensors SAP Container IBM OpenWhisk AWS Lambda GCP Functions SIEM SOAR SOC/CERT Triage EDR NDR XDR UEBA Security Operation and Analytics NOC OT CMDB Threat Intel Use Cases ML ML Security Nerve Center Search – Correlate - Investigate – Analyze - Act Monitoring Net/OS/Virt/App CPU/Mem/Disc Events Logs Metrics Application Traces
- 32. © 2022 SPLUNK INC. Monitoring Net/OS/Virt/App CPU/Mem/Disc Events Logs Metrics Application Traces Databases Networks Servers Virtual Machines Smartphones and Devices Custom Applications Security Web Server Sensors SAP Container IBM OpenWhisk AWS Lambda GCP Functions SIEM SOAR SOC/CERT Triage EDR NDR XDR UEBA Security Operation and Analytics NOC OT CMDB Threat Intel Use Cases ML ML Security Nerve Center Search – Correlate - Investigate – Analyze - Act
- 33. © 2022 SPLUNK INC. Thank You!