Cryptography
- 2. Cryptography (from Greek kryptós, "hidden", + gráphein, "to write"). Cryptography is the practice and study of techniques for secure communication in the presence of third parties (called adversaries). It is about constructing and analyzing protocols that overcome the influence of adversaries. TechKnowXpress Cryptography 2
- 3. There are three eras in the history of Cryptography: The Manual era The Mechanical era The Modern era Manual era refers to Pen and Paper Cryptography and dates back to 2000 B.C.eg : Scytale, Atbash , Caesar, Vigenere. Mechanical era refers to the invention of cipher machines. E.g.: Japanese Red and Purple Machines , German Enigma. The modern era of cryptography refers to computers. There are infinite permutations of cryptography available using computers. E.g.: Lucifer, Rijndael , RSA , ElGamal. TechKnowXpress Cryptography 3
- 4. Cipher: the algorithm that does the encryption. Ciphertext: the encrypted (scrambled) version of the message. Message altered to be unreadable by anyone except the intended recipients. Cryptanalysis: the science of breaking cryptographic algorithms. Cryptanalyst: a person who breaks cryptographic codes; also referred to as “the attacker”. TechKnowXpress Cryptography
- 5. Cryptosystem – The combination of algorithm, key, and key management functions used to perform cryptographic operations. Decryption: the process of converting ciphertext back to the original plaintext. Encryption: scrambling a message or data using a specialized cryptographic algorithm. Initialization Vector – Random values used with ciphers to ensure no patterns are created during encryption. TechKnowXpress Cryptography 5
- 6. Key – Sequence that controls the operation and behavior of the cryptographic algorithm. Keyspace – Total number of possible values of keys in a crypto algorithm. Plaintext – A message in its natural format readable by an attacker. TechKnowXpress Cryptography 6
- 7. Authentication ensures that whoever supplies or accesses sensitive data is an authorized party. Confidentiality assures that only authorized parties are able to understand the data. TechKnowXpress Cryptography
- 8. Integrity ensures that when a message is sent over a network, the message that arrives is the same as the message that was originally sent. Nonrepudiation ensuring that the intended recipient actually received the message & ensuring that the sender actually sent the message. TechKnowXpress Cryptography
- 9. Brute force Trying all key values in the keyspace. Chosen Ciphertext Decrypt known ciphertext to discover key. Dictionary Attack Find plaintext based on common words. Frequency Analysis Guess values based on frequency of occurrence. TechKnowXpress Cryptography 9
- 10. Factoring Attacks Find keys through prime factorization. Replay Attack Repeating previous known values. Side channel attacks use seemingly incidental information that can reveal important information about the key being used. TechKnowXpress Cryptography
- 11. Chosen plaintext attacks The cryptanalyst introduces the plaintext into the system and then watches for how that plaintext will be encrypted. The Allies used this approach in WWII by sending out false messages about allied troop movements. Often the attacker will try to feed a planned sequence of messages that would reveal the most about the way in which the data is being encrypted. TechKnowXpress Cryptography
- 12. Known plaintext attack The attacker has both the ciphertext and the plaintext. The attacker knows the algorithm that was used for the encryption. This is difficult because there are so many keys, but the plaintext information may make experimentation easier than in the previous case. TechKnowXpress Cryptography
- 13. Differential Power Analysis This is an attack on smart cards. A DPA attack analyzes the power output from a processor performing an encryption algorithm in order to get information about the key being used by that algorithm. TechKnowXpress Cryptography
- 14. There are several size of encryption keys: 64 bit encryption 128 bit encryption 256 bit encryption 512 bit encryption 1024 bit encryption Number indicates the size of the key used to encrypt the message. TechKnowXpress Cryptography
- 15. o o o Symmetric Even if an attacker captures the data, the attacker will not be able to manipulate it in any meaningful way. Symmetric algorithms use a single key shared by two communicating parties. The same key is used for both encryption and decryption. Asymmetric Mathematically related key pairs for encryption and decryption. o Public and private keys. o Hybrid Combines strengths of both methods. o TechKnowXpressdistributes symmetric key. Asymmetric o Cryptography 15
- 17. Types of Symmetric Cryptography: Stream-based Ciphers Mixes plaintext with key stream. Good for real-time services. Block Ciphers Substitution and transposition. E.g.: DES, AES. TechKnowXpress Cryptography
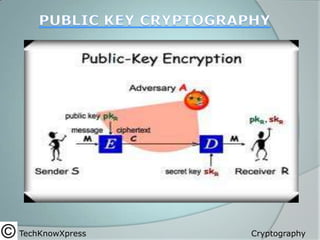
- 18. Public Key Cryptography In public-key cryptosystems, the public key may be freely distributed, while its paired private key must remain secret and is used for decryption. Public-key cryptography can be used for implementing digital signature schemes. TechKnowXpress Cryptography
- 20. Quantum cryptography describes the use of quantum mechanical effects (in particular quantum communication and quantum computation) to perform cryptographic tasks or to break cryptographic systems. TechKnowXpress Cryptography
- 21. The advantage of quantum cryptography is that it allows the completion of various cryptographic tasks that are proven or conjectured to be impossible using only classical communication. For example, quantum mechanics guarantees that measuring quantum data disturbs that data. This can be used to detect eavesdropping in quantum key distribution. TechKnowXpress Cryptography
- 22. Digital signatures can be permanently tied to the content of the message being signed. They cannot then be 'moved' from one document to another, for any attempt will be detectable. RSA and DSA are two of the most popular digital signature schemes. TechKnowXpress Cryptography
- 23. In digital signature schemes, there are two algorithms: one for signing, in which a secret key is used to process the message and one for verification, in which the matching public key is used with the message to check the validity of the signature. TechKnowXpress Cryptography
- 24. Traditionally, a watermark has been used to verify the authenticity of a document. TechKnowXpress Cryptography
- 25. Driver’s Licenses, diplomas, official letterhead were the primary applications of watermarks . More recently, used to track or prevent redistribution of TV logos. TechKnowXpress Cryptography
- 26. Purpose of using: Ensure authenticity of digital goods. Prevent unauthorized use/ensures copyright. Prevent copying. Adding the watermark to the image itself prevents removal by changing the format. E.g. GIF->JPEG. TechKnowXpress Cryptography
- 27. DRM is the practice of imposing technological restrictions that control what users can do with digital media. DRM is a class of controversial technologies that are used by hardware manufacturers, publishers, copyright holders, and individuals with the intent to control the use of digital content and devices after sale. TechKnowXpress Cryptography
Editor's Notes
- Cryptography – Greek for hidden and writing is a means of transforming data in a way that renders it unreadable by anyone except the intended recipient.What was originally used almost exclusively by governments for espionage has become a powerful tool for personal privacy today. Every modern computer system uses modern cryptographic methods to secure passwords stored and provides the trusted backbone for e-commerce (think lock icon).Cryptography fits into the CIA triad, as it can be used to ensure confidentiality and integrity of a message. Some forms also provide for sender authenticity and proof of delivery. But cryptography doesn’t address availability as some other forms of security do. Although forgetting a password for your user account can certainly lead to a denial of service attack. However, cryptography is used in many access control systems
- The history of cryptography begins where many stories of history do…. in ancient Egypt with hieroglyphics.Scytale – Spartan method involved wrapping a belt around a rod of a given diameter and lengthAtbash – Hewbrew cipher which mirrored the normal alphabet (shown in The DaVinci Code)Caesar – Shift all letters by a given number of letters in the alphabetVignère – Use of a key and multiple alphabets to hide repeated characters in an encrypted message
- Just like with many technical topics, Cryptography has its own lingo. Learning and using these terms and their definitions are the key to speaking like a crypto geek.
- Just like with many technical topics, Cryptography has its own lingo. Learning and using these terms and their definitions are the key to speaking like a crypto geek.
- Cryptographic Algorithms generally fall into one of two different categories, or are a combination of both.SymmetricFastOnly provide confidentialityNeed secure channel for key distributionKey management headaches from large number of key pairs to maintain N(N-1)/2That’s over 6.3 million key pairs to let all 3556 Purdue A/P staff members exchange encrypted messagesTo do the same for all students would require over half a billion key pairs!Examples: DES, AES, Blowfish, RC4, RC5AsymmetricLarge mathematical operations make it slower than symmetric algorithmsNo need for out of band key distribution (public keys are public!)Scales better since only a single key pair needed per individualCan provide authentication and nonrepudiationExamples: RSA, El Gamal, ECC, Diffie-Hellman
- Stream Ciphers are fast and easy to implement in hardware.Block ciphers are stronger, but slower and often implemented in hardware.