Cyber Security
- 2. E – Learning Course Information 1. To promote information security awareness in the area of: i. Introduction to information security; ii. Social engineering; iii. Malware; iv. Mobile security & social media; and v. Responsible browsing. 2. To serve as an induction course for new Axiata employees. 3. To serve as a refresher course for existing Axiata employees. OBJECTIVES
- 3. OBJECTIVES 1. Understand information security, its importance and the role you have to play to protect our information security. 2. Recognise the many forms of social engineering, its potential impacts and how to stay vigilant against it. 3. Be aware of the different types of malware and signs of malware infection, and ways to prevent exposing your device to malware. 4. Understand mobile security, identify common mobile devices and mobile security attacks, and ways to reduce risk of mobile security attacks. 5. Recognise the importance of responsible browsing, understand safe browsing practices and practise safe sharing on social media. Why Is This Course Important? Upon completion of this course, participants will be able to: Let’s begin.
- 4. 1 2 3 4 5 Course Content Introduction to Information Security Social Engineering Mobile Security and Social Media Responsible Browsing Malware 6 Assessment
- 6. PEOPLE. Our people working across the Axiata Group. Even with the absence of malicious intent, often times, information security is compromised due to employees’ lack of understanding on how to work in a secure manner. But where does our biggest threat come from? Why Do We Care? Estimates upwards of 250 billion dollars of loss associated with Cyber Crime! Every year, the Director of National Intelligence publishes an unclassified “Worldwide Threat Assessment.” The year 2018 report was published listing “Cyber” is the first (and greatest) threat listed. Information Security What is it? All the processes and practices we implement to protect networks, computers, applications and data from attacks on the C-I-A triad (Confidentiality, Integrity, and Availability).
- 7. You can ensure you play your part in protecting our information by: Keeping to our values. Keeping vigilant and diligent. Keeping hold of our valuables. Keeping it confidential. Keeping us all safe. How Do I Play My Part and How Will I Help? You will be helping Axiata to: Protect information from a range of threats. Ensure business continuity. Minimise potential financial loss. Optimise return on investments. Increase business opportunities.
- 8. Always logoff or lock your system even if you leave for a short time. Keep systems patched and up to date. Use strong passwords and protect your passwords. Encrypt sensitive files to ensure confidentiality of data. Watch what you share and be cautious of what information you put out there. Never let someone have access to your system with your credentials. Be wary of individuals looking for information or access to the building. Disable unsecured mechanisms. If something feels wrong or uncomfortable, trust your instinct and ask for help. Report any potential breach to your security team. Good Information Security Practices 1 2 3 4 5 6 7 8 9 10
- 10. • Social engineering is the act of manipulating people into disclosing private information and sometimes it involves breaking normal security procedures. • It relies heavily on manipulating human emotions, such as guilt and fear. • It exploits our natural tendency to trust others. • It is very common because it is much easier to trick a person into disclosing his or her credentials than hacking into his or her account. Social Engineering?
- 11. Common Social Engineering Attacks Phishing Phishing is a technique of fraudulently obtaining private information. Phishing refers to the use of emails that appear to originate from a trusted source to trick a user into entering his or her login credentials, ATM card’s PIN number or credit card number at a fake website. Phishing emails typically look very convincing and contains a link to fake web pages with seemingly legitimate company logos and addresses. While spear phishing and phishing are similar in the sense that both attacks involve sending emails to trick users into providing information, the key difference is that spear phishing involves sending highly customised emails to a few specific users whereas phishing involves sending generic emails to a broad number of users. This means that spear phishing email is more strategic and specific with its choice of targets. Hence, spear phishing attacks are known to have higher rate of success than phishing attacks. Spear Phishing
- 12. Common Social Engineering Attacks Vishing, otherwise known as voice phishing, is the practice of using the telephone to impersonate a known individual to gain access to sensitive information. Typically, the victim receives a call with a voice message disguised as a communication from a financial institute or government agency. 3. Vishing 4. Tailgating Tailgating is the practice of following someone through a security controlled door without showing or using the required ID pass. A tailgater may request the target to hold the door, stating that he or she forgot to bring his or her ID along. The target typically complies to the tailgater’s request out of good faith and common courtesy without verifying if the tailgater is allowed on premises. z
- 13. Limit what you share online • Without prior information, social engineers are unable to establish a solid pretext to trick you. • Set your social media accounts private • Accept friend requests from people you know in real life • Refrain from posting sensitive information online. Think before you click Do not click, forward or respond to phishing emails. Challenge tailgaters Politely reject requests from tailgaters to hold the door and direct them to register at the reception counter instead. Think before you speak Do not disclose your personal information to unknown caller. Be aware, connect with care Do not connect unfamiliar physical media to the organisation’s network. Defending Against Social Engineering Attacks
- 14. Practise laptop security • Secure your laptop to your workstation with a cable lock. • Never leave your laptop in your vehicle. • Press “Ctrl” and “L” to lock your laptop screen when it is not in use. Follow Axiata Policy and Procedures Read, understand and follow Axiata’s policy and procedures. When in doubt, report to IT helpdesk! Keep your software up-to-date Software updates involves security patches that fixes security vulnerabilities. Defending Against Social Engineering Attacks
- 15. Malware
- 16. What is Malware? Malicious software. Executes without your permission. Tricks you into thinking it’s something else. Works to remain unnoticed. Compromise computer functions. Steal data. Bypass access controls. Harms the host computer.
- 17. Stealing data, monitoring user activity, modifying files - these are one of the few things a malware can do. Being aware of their tactics is the first line of defense! The list below depicts some of the common malwares. Trojan Bot RAT Common Malwares Bots are software programs created to automatically perform specific operations such as video gaming, internet auctions and online contests. A Trojan disguises itself as a normal file or program to trick users into downloading and installing malware. It is typically bundled with games. RAT (short for remote access Trojan) is a malware program that includes a back door for administrative control over the target computer.
- 18. Pop-ups that asks you to download antivirus software or offer freebies. Antivirus software and firewalls have been disabled without your consent. Computer is running slower than usual. Emails/messages being sent automatically without user’s knowledge. Computer has been crashing or freezing lately. Detecting Malwares Detecting malware is not an easy task. Anti-virus software are rarely 100% accurate at detecting malware because malwares are designed to self-update and continually hides its presence whenever they start getting detected. If your computer is acting “funny”, it may be infected with malware. The most common indicators of a malware attack include:
- 19. Preventing Malwares Prevention is better than cure. As malwares are getting harder to detect and new threats are seen on a regular basis, you must be extra cautious in reducing the risk of getting malware attacks on your computer. Listed below are a few key recommendations to prevent malwares. Installing protection software Update your operating system Securing your network • Important updates for your system are packed with bug fixes, virus protection, and lots of other important things to keep your device clean. • Ensure your network needs a strong password to connect. • Do not broadcast your network name. • Provide a separate network for guests. When you suspect a malware infection, report to your IT security team immediately before the problem gets worst! • This protection is a must-have first step in keeping your computer virus free. • Ensure that you keep your software up to date too.
- 20. Mobile Security
- 21. What is Mobile Security? Also known as wireless security. Serves as a protection of smartphones, tablets, laptops and other portable computing devices and the networks they connect to from threats and vulnerabilities. A means by which a mobile device can authenticate users and protect or restrict access to data stored on the device. Common Mobile Devices in the Workplace Laptops Bluetooth devices Smartphone BYOD (Bring Your Own Device) Tablets
- 22. Common Attacks Theft / Gaining Physical Access Data Interception Insider Threats Malware Eavesdropping
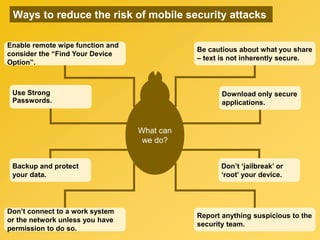
- 23. Ways to reduce the risk of mobile security attacks What can we do? Use Strong Passwords. Enable remote wipe function and consider the “Find Your Device Option”. Backup and protect your data. Don’t connect to a work system or the network unless you have permission to do so. Download only secure applications. Be cautious about what you share – text is not inherently secure. Don’t ‘jailbreak’ or ‘root’ your device. Report anything suspicious to the security team.
- 25. What is Responsible Browsing? Browsing habits that protect your personal information and online activity from cyber criminals, while being accountable for the impacts of your browsing habits towards Axiata's information security. What are Safe Browsing Practices? • All information shared on the internet are easily accessed by the public within a single click, which makes the internet a risky place. • Cyber criminals often lurk behind the scenes while internet users browse online, prying to steal sensitive information and execute other malicious activities. • Hence, it is important to understand and follow certain safeguards in order to defend ourselves from the schemes of cyber criminals. • These safeguards are known as safe browsing practices, which are simple tips you can take to keep your online activity safe from cyber criminals. • The next few pages show some examples of safe browsing practices.
- 26. Create Secure & Unique Passwords. • Creating strong passwords make it difficult for cyber criminals to crack the password. A strong password should have a mix of the following: • Upper case; • Lower case; • Number; and • Special character. • Example of a weak password versus a strong password is as below: Weak Password Strong Password • ThisPasswordIsStrong Th1sPa55wordisStr0ng
- 27. Staying Safe while using Public Wi-Fi • Verify your connection. • Be sure to ask the employee what the actual public Wi-Fi is to avoid connecting to a bogus network. • Avoid checking sensitive data. • Hold off on login to your social media, email and especially your financial accounts while on public Wi-Fi. • Turn off sharing. • Be sure to turn off sharing while you are on public Wi-Fi. If you leave it on while in a public place, cyber criminals can easily gain access to sensitive personal information and fields. • Use a VPN. • If you need to check sensitive data like your banking account while on public Wi-Fi, use a virtual private network or a VPN. Even if a cyber criminal positions himself in the middle of your connection, your data will be strongly encrypted. • Turn your Wi-Fi off when you’re done. • Even if you haven't actively connected to your network, the Wi-Fi hardware and your computer can still be transmitting data with any network in range. If you are through using the internet, ensure that your Wi-Fi is turned off.
- 28. Avoid Unsecured Websites • Websites with secured connection will have URLs that start with “https.” instead of “http://”. • The “s” suffix indicate that the website information is secured and encrypted. This security is provided by a SSL certificate, which certifies that sensitive information entered into that site is secured. • Without a SSL certificate, that information is highly vulnerable to be exposed and easily accessible by cybercriminals. • Identify a padlock symbol in the browser window frame, which appears when you attempt to log in to your existing accounts or register new accounts. You can click on the padlock icon to verify that your connection is secure.
- 29. Keep Browser Up-to-date • Most updates will include security patches. New patches are often released to fix existing vulnerabilities in browser software, so having the most up-to- date versions is critical. • If you're not installing those updates, you may leave yourself and Axiata vulnerable to new threats that pop up constantly. • Therefore, always make it a point to update your browser and leave no room for any form of security vulnerabilities.
- 30. Importance of Responsible Browsing • Browsing without caution can put Axiata at risk of all sorts of dangers, which includes identity theft, data theft and even computer damage. • Sensitive information (e.g. credit card number, bank accounts, IC number & mobile number) could be stolen & used for malicious purposes. • It can be used to make fraudulent purchases, sign up new credit cards, and even apply for government benefits. IDENTITY THEFT • Files from your computer such as photographs, videos and documents are stolen & then sold for illicit purposes. DATA THEFT • Viruses are sent to computers to cause damage and make them inoperable. COMPUTER DAMAGE • Experiencing data breach will not only give us a bad reputation and affect our business operations, it will also compromise our customer’s trust towards us. • Losing our customer’s trust is the last thing we want to see happening, which is why everyone in Axiata play an essential role in practicing browsing habits that will improve the security of your online activities.
- 31. Assessment