Don’t Fly Blind – Gain AWS Visibility to Ensure Security and Optimise Operations - Splunk
- 1. Don’t Fly Blind Richard Smith Senior Manager, Global Strategic Alliances Splunk
- 2. For UsersLeader in Cloud ● Attracted to AWS as it’s fast, reliable and expansive ● Trusted to run business critical workloads AWS Platform
- 3. • Build single pane of glass across ALL elements of delivery • Provide agile and flexible PLATFORM to describe all data on AWS • Provides visibility for security and business outcomes 4 Opportunities
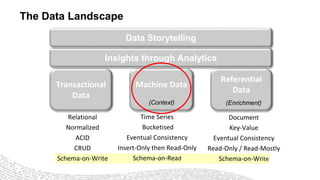
- 4. Transactional Data Machine Data Referential Data Insights through Analytics Data Storytelling Relational Normalized ACID CRUD Schema-on-Write Time Series Bucketised Eventual Consistency Insert-Only then Read-Only Schema-on-Read Document Key-Value Eventual Consistency Read-Only / Read-Mostly Schema-on-Write (Context) (Enrichment) The Data Landscape
- 5. Big Data Comes from Machines Volume | Velocity | Variety | Variability GPS, RFID, Hypervisor, Web Servers, Email, Messaging, Clickstreams, Mobile, Telephony, IVR, Databases, Sensors, Telematics, Storage, Servers, Security Devices, Desktops 7
- 6. Splunk Approach to Machine Data Traditional Splunk Search Schema at Read Structured RDBMS SQL Schema at Write ETL Universal Indexing Volume Velocity Variety Unstructured Outcome Less time Data Preparation Leads to Agile, Data focused monitoring and analytics Ask any question of your data
- 7. 9 Turning Machine Data Into Business Value Index Untapped Data: Any Source, Type, Volume Online Services Web Services Servers Security GPS Location Storage Desktops Networks Packaged Applications Custom ApplicationsMessaging Telecoms Online Shopping Cart Web Clickstreams Databases Energy Meters Call Detail Records Smartphones and Devices RFID On- Premises Private Cloud Public Cloud Ask Any Question Application Delivery Security, Compliance and Fraud IT Operations Business Analytics Industrial Data and the Internet of Things
- 8. 10 Splunk App for AWS EC2 EMR Kinesis R53 VPC ELB S3 CloudFront CloudTrail CloudWatch Redshift SNS API Gateway Config RDS CF IAM Lambda Explore Analyse Dashboard Alert Act AWS Data Sources End State: Comprehensive AWS Visibility
- 10. CONFIDENTIAL. INTERNAL USE ONLY. Demo 1 Optimising Operations through Visibility into AWS Data
- 11. Security Intelligence and Visibility “You can’t protect what you can’t see.” Best Practices for Securing Workloads in Amazon Web Services Gartner, April 2015 Neil MacDonald, Greg Young “Security monitoring will make or break a technology risk management program.” “Security requires visibility.” Assessing the Risk: Yes, the Cloud Can Be More Secure Than Your On-Premises Environment IDC, July 2015 Pete Lindstrom Amazon Web Services “Intro to AWS Security” 2015 AWS Summit Series
- 12. Threat Evolution Threat Type Complexity & Time Virus, spyware Phishing, malware Targeted attacks Malicious users APTs Signature Object analysis Machine-learning, behavior models and anomaly detection Scale&Depth Antivirus Email Filters/Threat Lists WAF/IDP/IDS SIEM/Security Analytics Behavioral Analysis/Machine Learning Now
- 13. Modern Cyber Security Requirement: Analyse All Data • Keep up with new technology data sources • Investigate not only security data – but where else did an attack go • Get a single view of the truth – all investigators see the same data
- 14. App Servers Network Threat Intelligence Firewall Web Proxy Internal Network Security Endpoints Splunk as the Security Nerve Center Identity
- 15. 17 ROOT CAUSE AND ISSUE RESOLUTION PROACTIVE MONITORING AND REAL- TIME ALERTING DELIVER BETTER QUALITY CODE FASTER CLOUD APP AND INFRASTRUCTURE MONITORING MOBILE APP TROUBLE SHOOTING USER & USAGE ANALYTICS Platform for Application Delivery and IT Operations
- 16. Reduce business impact with Shorter and Fewer Outages TOP 4 Value Drivers for IT Ops Root Cause Analysis Up to 30% unknown root causes, causing incidents to recur Incident Troubleshooting Lengthy log analysis done manually Incident Triage All hands on deck, taking up 30 to 40 minutes Before Splunk Service Restoration Fix is implemented Fix is implemented Failure detection Customer often informs IT #1 Better detection customer is notified by IT With Splunk #2 Faster triage often conducted by 1st level staff without all hands on deck #3 Faster investigation (MTTI) through rapid log search and correlation conducted in conjunction by different teams (everyone looks at the same data) #4 Faster and more comprehensive root cause analysis reduces incident recurrence
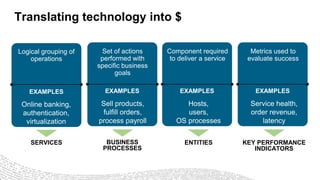
- 17. Translating technology into $ Logical grouping of operations Online banking, authentication, virtualization EXAMPLES SERVICES Set of actions performed with specific business goals Sell products, fulfill orders, process payroll EXAMPLES BUSINESS PROCESSES Component required to deliver a service Hosts, users, OS processes EXAMPLES ENTITIES Metrics used to evaluate success Service health, order revenue, latency EXAMPLES KEY PERFORMANCE INDICATORS
- 18. What is Splunk IT Service Intelligence? Machine Learning-Powered, Analytics-Driven IT Operations Simplify service operations Prioritise incidents with context Redefine the role of IT Combine events & metrics across silos with ease, flexibility & scale in days Unify siloed monitoring Leverage machine learning to detect anomalies & highlight events that matter Deliver business & service context to prioritise incident investigation & action Support decisions & communicate results with powerful service-level insights
- 19. Aggregating Multiple Data types to provide Service Health Scores A health score is a score from 0-100 (0 = critical and 100 = normal) that helps determine the health of a service. It is calculated based on importance and status (e.g., green, orange, red) of all KPIs, once every minute.
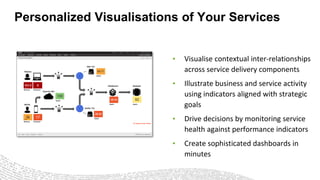
- 20. Personalized Visualisations of Your Services • Visualise contextual inter-relationships across service delivery components • Illustrate business and service activity using indicators aligned with strategic goals • Drive decisions by monitoring service health against performance indicators • Create sophisticated dashboards in minutes
- 21. Delivering Business Level Visibility from IT Data
- 22. CONFIDENTIAL. INTERNAL USE ONLY. Demo 2 Service Intelligence and Optimisation
- 23. How FINRA Uses Splunk Cloud for Security • Transforms third-party threat intelligence information into security alerts • Leverages the Splunk App for AWS • Extends solution to report on AWS Cost Optimisation “Splunk Cloud gives you applications which let you get huge amounts of value from your data.” — Sr. Director of Information Security
- 24. Building a Lean SOC in the Cloud with Splunk Enterprise Security • Replaced traditional SIEM with Splunk Enterprise Security in the Cloud • Intrinsic risk-score based correlation has been pivotal in several security incidents • IT Operations and IT Security collaborate in one platform, together • Monitor Entire AWS environment with Splunk App for AWS
- 25. Cloud – The Customer Advantage ● Instant access to infrastructure and software • Faster POC • Faster deployment • Faster time-to-value ● No need for in-house expertise ● For many customers, Splunk Cloud is lower TCO than deploying in-house ● Easy scalability – scales to 10TB/day+ “My team can focus on security events, not infrastructure.” - CISO “We’re a bank. We don’t want to be in the business of running a data center.” - CISO “At least 50% lower TCO compared to deploying an on-premises SIEM.” - CIO
- 26. The Power of Splunk – TOTAL VISIBILITY 28 SEARCH AND ANALYSE EVERYTHING COLLECT DATA FROM ANYWHERE GAIN REAL-TIME OPERATIONAL INTELLIGENCE
- 27. Easy to Try & Get Started 29 FREE CLOUD TRIAL VISIT SPLUNK AT AWS SUMMIT STAND EXPLORE THE VALUE OF OPERATIONAL INTELLIGENCE WITH YOUR AWS PARTNER 1 2 3
- 28. Thank you!