Fog Computing
- 2. CONTENTS Abstract Introduction Existing System Proposed System Characteristics of Fog Computing Cloud Vs. Fog Scenarios Architecture Applications Examples of Fog Computing Advantages Disadvantages Future Enhancement Conclusion References
- 3. • FOG Computing is an advanced or extended version of cloud computing where the computing takes place at the edge of the network. There are many companies currently spending a lot of research on this topic like Cisco etc. • It is similar to cloud computing, but is far denser in geographical distribution and location and its proximity to end users is more, which means they provide a faster end-user experience than cloud computing and have better performance. • The questions about its complexity, practical feasibility, cost and performance are arising in different research communities. There is also a major concern about it's reliability or durability in performing all sorts of operations performed by cloud computing systems. ABSTRACT
- 4. INTRODUCTION • CISCO recently delivered the vision of Fog computing to enable applications on billions of connected devices to run directly at the network edge. Customers can develop, manage and run software applications on Cisco framework of networked devices, including hardened routers and switches. Cisco brings the open source Linux and network operating system together in a single networked device. • Fog computing, also known as fog networking, is a decentralized computing infrastructure in which computing resources and application services are distributed in the most logical, efficient place at any point along the continuum from the data source to the cloud. The goal of fog computing is to improve efficiency and reduce the amount of data that needs to be transported to the cloud for data processing, analysis and storage. This is often done for efficiency reasons, but it may also be carried out for security and compliance reasons.
- 6. • A simple three level hierarchy as shown in above figure. • In this framework, each smart things and intefaces is attached to one of Fog devices. Fog devices could be interconnected and each of them is linked to the Cloud. Contd…
- 7. • Cloud computing has provided many opportunities for enterprises by offering their customers a range of computing services. Current “pay-as- you-go” Cloud computing model becomes an efficient alternative to owning and managing private data centers for customers facing Web applications EXISTING SYSTEM
- 8. DISADVANTAGES Existing data protection mechanisms such as encryption was failed in securing the data from the attackers. It does not verify whether the user was authorized or not. Cloud computing security does not focus on ways of secure the data from unauthorized access.
- 9. • Unlike traditional data centers, Fog devices are geographically distributed over heterogeneous platforms, spanning multiple management domains. Cisco is interested in innovative proposals that facilitate service mobility across platforms, and technologies that preserve end-user and content security and privacy across domains. PROPOSED SYSTEM
- 10. ADVANTAGES Fog can be distinguished from Cloud by its proximity to end-users. The dense geographical distribution and its support for mobility. It provides low latency, location awareness, and improves quality-of- services(Qos) and real time applications.
- 11. CHARACTERISTICS OF FOG COMPUTING Edge location, location awareness, and low latency : Fog computing support endpoints with finest services at the edge of the network. Geographical distribution : The services and application objective of the fog is widely distributed. Support for mobility : Using LISP protocol fog devices provide mobility techniques like decouple host identity to location identity. Real time interactions : fog computing requires real time interactions for speedy service. Heterogeneity : Fog nodes can be deployed in a wide variety of environments. Interoperability : Fog components must be able to interoperate in order to give wide range of services like streaming.
- 12. CLOUD vs. FOG Fog – Solution to Cloud’s Limitations • Reduction in data movement across the network resulting in reduced congestion. • Elimination of bottlenecks resulting from centralized computing systems. • Improved security of encrypted data as it stays closer to the end user.
- 13. CLOUD vs. FOG
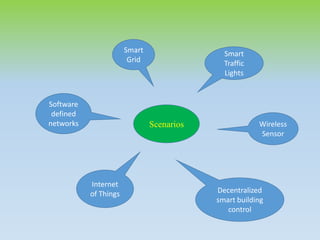
- 14. Scenarios Smart Grid Internet of Things Decentralized smart building control Software defined networks Smart Traffic Lights Wireless Sensor
- 15. The design of fog architecture or the key components of fog architecture are discussed below: • Heterogeneous Physical Resources • Fog Abstraction Layer • Fog Service Orchestration Layer •Foglet Software Agent •Distributed Database •Policy-Based Service Orchestration ARCHITECTURE OF FOG TECHNOLOGY
- 16. Components in Fog architecture
- 17. • Heterogeneous Physical Resources: Heterogeneous in nature, ranging from high-speed links connecting enterprise data centers and the core to multiple wireless access technologies towards the edge. 3G/4G, LTE, Wi-Fi etc. • Fog Abstraction Layer: A uniform and programmable interface for seamless resource management an d control. The layer provides generic APIs for monitoring, provisioning and controlling physical resources such as CPU, memory, network and energy.
- 18. • Fog Service Orchestration Layer: Provides dynamic, policy-based life-cycle management of Fog services. Managing services on a large volume of Fog nodes with a wide range of capabilities is achieved with the following technology and components: Foglet Software Agent, Distributed Database, persistent storage to store policies and resource meta-data, Policy-Based Service Orchestration, provides policy-based service routing, i.e., routes an incoming service request to the appropriate service instance that confirms to the relevant business policies.
- 19. Smart Grid: Fog computing allows fast, machine-to-machine (M2M) handshakes and human to machine interactions (HMI), which would work in cooperation with the cloud. Decentralized Smart Building Control: Wireless sensors are installed to measure temperature, humidity, or levels of various gaseous components in the building atmosphere. Information can be exchanged among all sensors in the floor and the reading can be combined to form reliable measurements. Smart Cities: Fog computing would be able to obtain sensor data on all levels, and integrate all the mutually independent network entities within. Health Care: The cloud computing market for healthcare is expected to reach $5.4 billion by 2017, according to a Markets and Markets report, and fog computing would allow this on a more localized level.
- 20. • Tech giants Cisco and IBM are the driving forces behind fog computing, and link their concept to the emerging Internet of Things (IoT). • Fog has a direct correlation with IoT. • According to CISCO, the important areas where fog would play a vital role are the following : APPLICATIONS OF FOG
- 22. Connected cars Fog computing is ideal for Connected Vehicles (CV) because real-time interactions will make communications between cars, access points and traffic lights as safe and efficient as possible. At some point in time, the connected car will start saving lives by reducing automobile accidents. Fog computing will be the best option for all internet connected vehicles because fog computing gives real time interaction.
- 23. Connected Vehicles communicating each other
- 24. In this subsection, we take Man-in-the-middle attack as an example to expose the security problems in Fog Computing. In this attack, gateways serving as Fog devices may be comprised or replaced by fake ones. Man-In-The-Middle Attack:
- 25. Fog can be distinguished from Cloud by its proximity to end-users. The dense geographical distribution and its support for mobility. It provides low latency, location awareness, and improves quality-of- services (QoS) and real time applications. ADVANTAGES Existing data protection mechanisms such as encryption was failed in securing the data from the attackers. It does not verify whether the user was authorized or not. Cloud computing security does not focus on ways of secure the data from unauthorized access. DISADVANTAGES
- 26. Future work will expand on the Fog computing paradigm in Smart Grid. In this scenario, two models for Fog devices can be developed. Independent Fog devices consult directly with the Cloud for periodic updates on price and demands, while interconnected Fog devices may consult each other. Next, Fog computing based SDN in vehicular networks will receive due attention. FUTURE ENCHANCEMENT
- 27. Fog computing advantages for services in several domains, such as Smart Grid, wireless sensor networks, Internet of Things (IoT) and software defined networks (SDNs). We examine the state- of-the-art and disclose some general issues in Fog computing including security, privacy, trust, and service migration among Fog devices and between Fog and Cloud. CONCLUSION
- 28. References http://www.webopedia.com/TERM/F/fog-computing.html http://internetofthingsagenda.techtarget.com/definition/fog-computing- fogging http://www.westbaseuk.com/news/fog-computing-vs-cloud-computing-whats- the-difference/ http://www.cisco.com/c/en_in/solutions/internet-of-things/iot-fog- applications.html