iot_basic_1.pptx
- 1. IoT IoT product development life cycle
- 2. The IoT Product life cycle • There are four stages to the IoT product life cycle. These are • Design, • Deployment, • ongoing Management, and • Decommissioning.
- 4. Design • Design is the first stage of the life cycle but likely the most important one. • In this stage, the developers have to consider requirements from the next three stages of the product life cycle to ensure that the product can easily support each stage. • In many cases, the product is not brand new, and instead is an enhancement to a previous generation product. • Therefore, developers have to consider how to best bridge new functionalities and the existing code base without compromising performance and security. • Developers have to also carefully weigh “make versus buy” considerations. • While many OEMs are starting to lean towards the “buy” scenario to speed up time to market, this path isn’t without its own set of challenges. • In a noisy IoT marketplace filled with many options for both hardware and software solutions, OEMs must be discerning when it comes to selecting the right partners.
- 5. Deployment • Deployment is the second stage of the product life cycle, and itself can come in a few phases such as • proof-of-concepts, pilots, and commercial roll out. • Deployments of IoT solutions are much more complex than traditional products, as there are many more stakeholders involved. • For example, a deployment at an electric utility may involve the OEM, the utility provider, a systems integrator, an independent software vendor (ISV), and the public utility commission. • They may all have the need to have access to the product at the various phases of deployment; as such, • the right level of user authorization needs to be provided. • Initial provisioning and configuration of the platform in the field needs to be quick and seamless. • Modelling the deployment and activation after smartphones and other consumer products can ensure ease of use and deployment at scale.
- 6. Ongoing Management • Ongoing Management is the third stage of the product life cycle, and likely the longest one. • During this stage, multiple stakeholders may need to access the device to be able to monitor its status, provide maintenance, provide updates, and optimize its performance – all without sending someone on site. • In fact, for many industrial customers, one of the most critical drivers of the value in IoT is the ability to use a device’s data to make decisions regarding its performance.
- 7. Decommissioning • Finally, the last stage of the product life cycle is Decommissioning. • This stage is typically overlooked in many product designs. • OEMs need to carefully consider and plan for the product’s end-of- life at the design stage. • End users and other stakeholders have to be able to quickly and securely remove a device from service and onboard a new one. • While it may seem counterintuitive for an OEM to develop a design for making it easier for an end user to decommission their product and move into a newer model, this has been done very intelligently by companies like Samsung and Apple. • By making it easier for their customers to transition from one product model to another, they have created another reason for their customers to continue to invest in their products time and time again.
- 8. IoT(internet of things) enabling technologies • IoT(internet of things) enabling technologies are • Wireless Sensor Network • Cloud Computing • Big Data Analytics • Communications Protocols • Embedded System
- 10. 1. Wireless Sensor Network(WSN) : A WSN comprises distributed devices with sensors which are used to monitor the environmental and physical conditions. A wireless sensor network consists of end nodes, routers and coordinators. End nodes have several sensors attached to them where the data is passed to a coordinator with the help of routers. The coordinator also acts as the gateway that connects WSN to the internet. Example – • Weather monitoring system • Indoor air quality monitoring system • Soil moisture monitoring system • Surveillance system • Health monitoring system
- 12. 2. Cloud Computing : It provides us the means by which we can access applications as utilities over the internet. Cloud means something which is present in remote locations. With Cloud computing, users can access any resources from anywhere like databases, webservers, storage, any device, and any software over the internet. Characteristics – • Broad network access • On demand self-services • Rapid scalability • Measured service • Pay-per-use
- 13. • Provides different services, such as – • IaaS (Infrastructure as a service) Infrastructure as a service provides online services such as physical machines, virtual machines, servers, networking, storage and data center space on a pay per use basis. Major IaaS providers are Google Compute Engine, Amazon Web Services and Microsoft Azure etc. Ex : Web Hosting, Virtual Machine etc. • PaaS (Platform as a service) Provides a cloud-based environment with a very thing required to support the complete life cycle of building and delivering West web based (cloud) applications – without the cost and complexity of buying and managing underlying hardware, software provisioning and hosting. Computing platforms such as hardware, operating systems and libraries etc. Basically, it provides a platform to develop applications. Ex : App Cloud, Google app engine • SaaS (Software as a service) It is a way of delivering applications over the internet as a service. Instead of installing and maintaining software, you simply access it via the internet, freeing yourself from complex software and hardware management. SaaS Applications are sometimes called web-based software on demand software or hosted software. SaaS applications run on a SaaS provider’s service and they manage security availability and performance. Ex : Google Docs, Gmail, office etc.
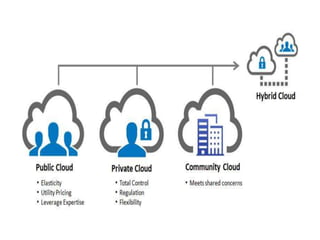
- 15. • Cloud computing supports four basic deployment models. These models differ in the way how the cloud is built and who are using the resources in the cloud. The four cloud deployment models are: • Public cloud • Private cloud • Community cloud • Hybrid cloud
- 17. • In a public cloud the resources are shared between several users. • Public cloud is generally maintained by the cloud service provider. • The management of the resources is taken care by the cloud service provider. • In a private cloud all the resources are used by a single organization. • Such organization has the complete control on the cloud and can follow all the necessary regulations. • Private cloud offers greater flexibility when compared to the public cloud.
- 18. • A community cloud is one whose resources are shared by two or more companies having shared goals. • Such clouds are generally used for conducting collaborated research. • A combination of the previous three clouds is a hybrid cloud. • Big companies generally use hybrid cloud. The companies generally store the sensitive data in the private cloud and other non-sensitive data in the public cloud.
- 19. 3. Big Data Analytics : It refers to the method of studying massive volumes of data or big data. • Collection of data whose volume, velocity or variety is simply too massive and tough to store, control, process and examine the data using traditional databases. • Big data is gathered from a variety of sources including social network videos, digital images, sensors and sales transaction records. • Several steps involved in analyzing big data – • Data cleaning (Data cleaning is the process of fixing or removing incorrect, corrupted, incorrectly formatted, duplicate, or incomplete data within a dataset) • Munging (Data munging is the initial process of refining raw data into content or formats better-suited for consumption by downstream systems and users) • Processing • Visualization Examples – • Bank transactions • Data generated by IoT systems for location and tracking of vehicles • E-commerce and in Big-Basket • Health and fitness data generated by IoT system such as a fitness bands
- 20. • The data analytics framework consists of six steps namely: collection, cleaning, integration, analysis, visualization and alerting.
- 21. 4. Communications Protocols : They are the backbone of IoT systems and enable network connectivity and linking to applications. Communication protocols allow devices to exchange data over the network. • Multiple protocols often describe different aspects of a single communication. A group of protocols designed to work together is known as a protocol suite; when implemented in software they are a protocol stack. They are used in • Data encoding • Addressing schemes
- 22. 5. Embedded Systems : It is a combination of hardware and software used to perform special tasks. It includes microcontroller and microprocessor memory, networking units (Ethernet Wi-Fi adapters), input output units (display keyword etc. ) and storage devices (flash memory). It collects the data and sends it to the internet. Embedded systems used in Examples – • Digital camera • DVD player, music player • Industrial robots • Wireless Routers etc.
- 23. Internet of Things - Technology and Protocols • IoT primarily exploits standard protocols and networking technologies. • However, the major enabling technologies and protocols of IoT are RFID, NFC, low-energy Bluetooth, low-energy wireless, low-energy radio protocols, LTE-A, and WiFi-Direct. • These technologies support the specific networking functionality needed in an IoT system in contrast to a standard uniform network of common systems.
- 24. NFC and RFID • RFID (radio-frequency identification) and NFC (near-field communication) provide simple, lowenergy, and versatile options for identity and access tokens, connection bootstrapping, and payments. • RFID technology employs 2-way radio transmitter-receivers to identify and track tags associated with objects. • NFC consists of communication protocols for electronic devices, typically a mobile device and a standard device.
- 25. • Low-Energy Bluetooth (BLE) • This technology supports the low-power, long-use need of IoT function while exploiting a standard technology with native support across systems. • Low-Energy Wireless (LoRaWAN) • This technology replaces the most power hungry aspect of an IoT system. Though sensors and other elements can power down over long periods, communication links (i.e., wireless) must remain in listening mode. Low-energy wireless not only reduces consumption, but also extends the life of the device through less use.
- 26. • Radio Protocols • ZigBee, Z-Wave, and Thread are radio protocols for creating low- rate private area networks. These technologies are low-power, but offer high throughput unlike many similar options. This increases the power of small local device networks without the typical costs. • LTE-A • LTE-A, or LTE Advanced, delivers an important upgrade to LTE technology by increasing not only its coverage, but also reducing its latency and raising its throughput. It gives IoT a tremendous power through expanding its range, with its most significant applications being vehicle, UAV, and similar communication. • WiFi-Direct • WiFi-Direct eliminates the need for an access point. It allows P2P (peer-to-peer) connections with the speed of WiFi, but with lower latency. • WiFi-Direct eliminates an element of a network that often bogs it down, and it does not compromise on speed or throughput.