Middle East IoT Workshop
- 1. Gemalto Building Trust in the Internet of Things – Middle East Haider Iqbal – Director, Smart Cities 05.04.2018
- 2. Introduction BUILDING TRUST IN THE INTERNET OF THINGS Bringing Trust To The Internet of Things2
- 3. 3 The Internet of Things has great potential Bringing Trust To The Internet of Things
- 4. 4 The Drone Economy With drones, a whole site can be mapped daily, in high detail, for as little as $25 a day. Bringing Trust To The Internet of Things
- 5. 5 The Autonomous Vehicle Autonomous vehicles could save up to 50 minutes a day for drivers Bringing Trust To The Internet of Things
- 6. Bringing Trust To The Internet of Things6 Haider Iqbal Director Smart Cities Enterprise IoT Ecosystems www.linkedin.com/in/haideriqbal
- 7. The Connected World The “things” on our planet are connecting far faster than we can imagine. Bringing Trust To The Internet of Things7 Source: Gartner 2017 1 .7b 2 .1b5 In our daily lives we will depend on the knowledge flowing continuously from the data created by these billions of connected “things” “things” will be connected around the globe in 2018 By 2021 this figure will have reached a staggering 25.1 billion “things” 0
- 8. The two universes of IoT: Consumer & Industrial Bringing Trust To The Internet of Things9 Examples Smart Home, Wearables, Smart Watches, Wrist Bands, Head-mounted Displays, Connected Toys etc. Consumer IoT Examples Smart Manufacturing, Smart Energy, Smart Lighting, Street Lamps, Connected Heavy Trucks etc. Industrial IoT
- 9. The Promise of IoT Increase customer intimacy Bringing Trust To The Internet of Things10 Revenue growth opportunities Improve operational excellence
- 10. Delivering the IoT promise hinges on Trust Traditional boundaries of business are fading Speed of doing business is changing Too many stakeholders in the value chain Surge in data leads to privacy concerns A solid foundation based on trust required Bringing Trust To The Internet of Things11
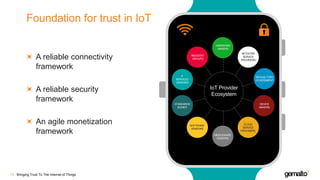
- 11. Foundation for trust in IoT A reliable connectivity framework A reliable security framework An agile monetization framework Bringing Trust To The Internet of Things12 IoT Provider Ecosystem HARDWARE MAKERS INDUSTRY GROUPS IT SERVICES VENDORS STANDARDS BODIES SOFTWARE VENDORS CLOUD SERVICE PROVIDERS MIDDLEWARE VENDORS DEVICE MAKERS REGUALTORS GOVERNMENT NETWORK SERVICE PROVIDERS
- 12. Example of Smart Cities BUILDING TRUST IN THE INTERNET OF THINGS Bringing Trust To The Internet of Things13
- 13. Public vs Private Sector Transformation Bringing Trust To The Internet of Things14 Past Present $100 What you would pay for a rented car on a Saturday, even if you needed it for an hour $7 What car sharing companies like Zipcar would charge for an hour, insurance & gas included US $ 159,000 Price of Univac I mainframe computer in 1951; size of a garage, weighed 29,000 lbs $200 What you can buy a smartphone for, with 1000 times more compute power US $ 3,800 Annual cost for a public university in 1981 US $ 12,800 What it would cost today, though with superior facilities (labs, stadiums etc.) 7.4% That’s the growth in healthcare spending from 1999 to 2009 in Canada; outpacing GDP 40% This is how much some of Canadian provincial budgets consume in healthcare PrivateSectorPublicSector Source: Deloitte It’s no surprise that the overall “trust” in governments is on the decline.
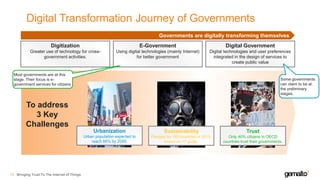
- 14. Digital Transformation Journey of Governments Bringing Trust To The Internet of Things15 Digitization Greater use of technology for cross- government activities. E-Government Using digital technologies (mainly Internet) for better government Digital Government Digital technologies and user preferences integrated in the design of services to create public value Governments are digitally transforming themselves Urbanization Urban population expected to reach 66% by 2050. Sustainability Pledged by 193 countries in 2015, based on 17 goals. Trust Only 40% citizens in OECD countries trust their governments. To address 3 Key Challenges Most governments are at this stage. Their focus is e- government services for citizens Some governments can claim to be at the preliminary stages.
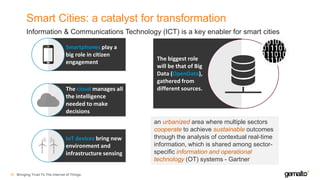
- 15. Smart Cities: a catalyst for transformation Bringing Trust To The Internet of Things16 Information & Communications Technology (ICT) is a key enabler for smart cities Smartphones play a big role in citizen engagement The cloud manages all the intelligence needed to make decisions IoT devices bring new environment and infrastructure sensing The biggest role will be that of Big Data (OpenData), gathered from different sources. an urbanized area where multiple sectors cooperate to achieve sustainable outcomes through the analysis of contextual real-time information, which is shared among sector- specific information and operational technology (OT) systems - Gartner
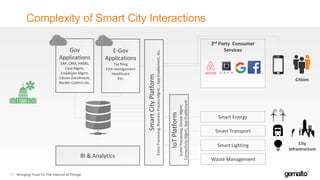
- 16. Complexity of Smart City Interactions Bringing Trust To The Internet of Things17 Citizen Gov Applications ERP, CRM, HRMS, Case Mgmt, Employee Mgmt, Citizen Enrollment, Border Control etc. E-Gov Applications Tax filing Fine management Healthcare Etc. BI & Analytics SmartCityPlatform EventProcessing,BusinessProcessMgmt,,AppEnablement,etc. Smart Energy Smart Transport Smart Lighting Waste Management 3rd Party Consumer Services City Infrastructure IoTPlatform EventProcessing,DeviceMgmt, ConnectivityMgmt,AppEnablement
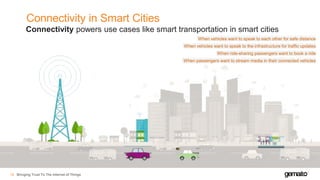
- 17. Connectivity in Smart Cities Bringing Trust To The Internet of Things18 Connectivity powers use cases like smart transportation in smart cities When vehicles want to speak to each other for safe distance When ride-sharing passengers want to book a ride When vehicles want to speak to the infrastructure for traffic updates When passengers want to stream media in their connected vehicles
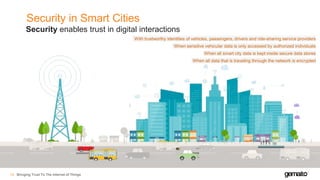
- 18. Security in Smart Cities Bringing Trust To The Internet of Things19 Security enables trust in digital interactions With trustworthy identities of vehicles, passengers, drivers and ride-sharing service providers When all smart city data is kept inside secure data stores When sensitive vehicular data is only accessed by authorized individuals When all data that is traveling through the network is encrypted
- 19. Monetization in Smart Cities Bringing Trust To The Internet of Things20 Monetization fuels growth and cohesion amongst stakeholders When OEM, Cloud Vendors, Software Vendors and Service Providers value each others’ contribution When the ecosystem treats and values data as an asset When enforced intellectual property rights enable innovation When new ecosystem players can enter the market with a quicker time-to-market
- 20. 1st Foundation of Trust: Connectivity BUILDING TRUST IN THE INTERNET OF THINGS Bringing Trust To The Internet of Things21
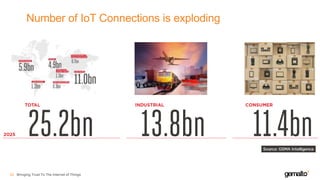
- 21. Number of IoT Connections is exploding Bringing Trust To The Internet of Things22
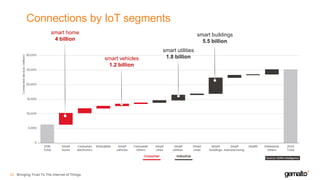
- 22. Connections by IoT segments Bringing Trust To The Internet of Things23 smart buildings 5.5 billion smart home 4 billion smart utilities 1.8 billionsmart vehicles 1.2 billion
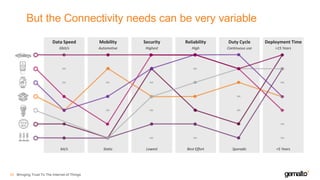
- 23. But the Connectivity needs can be very variable Bringing Trust To The Internet of Things24 Data Speed Gbit/s bit/s Mobility Automotive Static Security Highest Lowest Reliability High Best Effort Duty Cycle Continuous use Sporadic Deployment Time >15 Years <5 Years
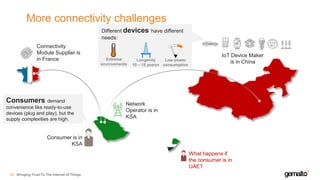
- 24. More connectivity challenges Bringing Trust To The Internet of Things25 Consumer is in KSA IoT Device Maker is in China Network Operator is in KSA Connectivity Module Supplier is in France Consumers demand convenience like ready-to-use devices (plug and play), but the supply complexities are high. What happens if the consumer is in UAE? Different devices have different needs: Low power consumption Extreme environments Longevity 10 – 15 years+
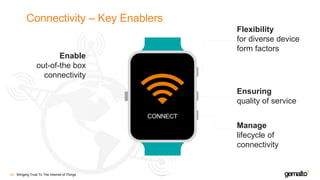
- 25. Connectivity – Key Enablers Bringing Trust To The Internet of Things26 Enable out-of-the box connectivity Flexibility for diverse device form factors Ensuring quality of service Manage lifecycle of connectivity CONNECT
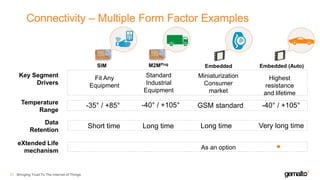
- 26. Connectivity – Multiple Form Factor Examples Bringing Trust To The Internet of Things27 Key Segment Drivers Temperature Range -40° / +105° Fit Any Equipment Standard Industrial Equipment eXtended Life mechanism SIM M2MPlug -35° / +85° Data Retention Long timeShort time Embedded Embedded (Auto) GSM standard -40° / +105° Miniaturization Consumer market Highest resistance and lifetime Very long timeLong time As an option
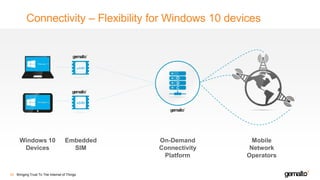
- 27. Connectivity – Flexibility for Windows 10 devices Bringing Trust To The Internet of Things28 Windows 10 Devices Embedded SIM On-Demand Connectivity Platform Mobile Network Operators
- 28. 2nd Foundation of Trust: Security BUILDING TRUST IN THE INTERNET OF THINGS Bringing Trust To The Internet of Things29
- 29. Security tops the list of IoT concerns Bringing Trust To The Internet of Things30 4% 7% 10% 17% 18% 18% 21% 21% 24% 28% 30% 34% Don't know None — we don't have any concerns We can't find the right supplier(s) Lack of executive support Regulatory issues or concerns We don't think that we have an application or process Difficulty and risk of migration or installation Pricing is unclear or complicated Lack of technology maturity Integration challenges Total cost concerns (total cost of ownership) Security concerns What are your firm’s concerns, if any, with deploying M2M/Internet of Things technologies? Source: Forrester’s Global Business Technographics® Networks And Telecommunications Survey, 2015
- 30. Authentication & Privacy Consumers and Enterprises only want authorized entities to have access to their devices or data Secure components and solutions must be embedded into “things” to protect data at rest or in motion Hackers will take advantage, whenever there is a security loophole Bringing Trust To The Internet of Things31 15seconds Time required by a hacker to backdoor a smart thermostat device 75,000 spam emails sent by an internet connected fridge during holiday break 471,000 connected vehicles found vulnerable to cyber attacks
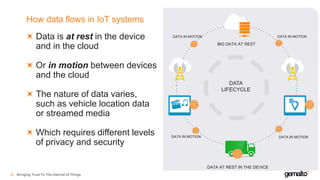
- 31. How data flows in IoT systems Data is at rest in the device and in the cloud Or in motion between devices and the cloud The nature of data varies, such as vehicle location data or streamed media Which requires different levels of privacy and security Bringing Trust To The Internet of Things32 BIG DATA AT REST DATA LIFECYCLE DATA IN MOTION DATA IN MOTION DATA AT REST IN THE DEVICE DATA IN MOTION DATA IN MOTION
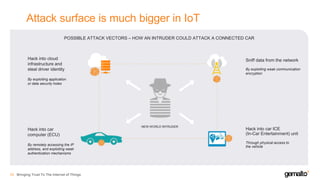
- 32. Attack surface is much bigger in IoT Bringing Trust To The Internet of Things33 NEW-WORLD INTRUDER Hack into cloud infrastructure and steal driver identity By exploiting application or data security holes Sniff data from the network By exploiting weak communication encryption Hack into car ICE (In-Car Entertainment) unit Through physical access to the vehicle Hack into car computer (ECU) By remotely accessing the IP address, and exploiting weak authentication mechanisms POSSIBLE ATTACK VECTORS – HOW AN INTRUDER COULD ATTACK A CONNECTED CAR
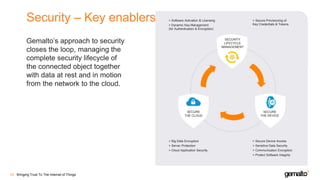
- 33. Security – Key enablers Gemalto’s approach to security closes the loop, managing the complete security lifecycle of the connected object together with data at rest and in motion from the network to the cloud. Bringing Trust To The Internet of Things34 > Software Activation & Licensing > Dynamic Key Management (for Authentication & Encryption) > Secure Provisioning of Key Credentials & Tokens > Big Data Encryption > Server Protection > Cloud Application Security > Secure Device Access > Sensitive Data Security > Communication Encryption > Protect Software Integrity SECURITY LIFECYCLE MANAGEMENT SECURE THE DEVICE SECURE THE CLOUD
- 34. On-Premise and On-Demand 35 ENCRYPTION KEY MANAGEMENT AND PROTECTION IDENTITY AND ACCESS MANAGEMENT • Data-at-rest encryption • Data-in-motion encryption • Enterprise key lifecycle management • High assurance key protection • HSM orchestration and crypto operations • Access management • Multi-factor authentication • PKI credential management Bringing Trust To The Internet of Things
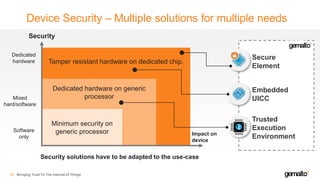
- 35. Device Security – Multiple solutions for multiple needs 36 Tamper resistant hardware on dedicated chip. Dedicated hardware on generic processor Software only Mixed hard/software Dedicated hardware Security Impact on device Minimum security on generic processor Security solutions have to be adapted to the use-case LOGO LOGO IN BLACK LOGO COLOR VERSIONS LOGO ON BLACK Secure Element Embedded UICC Trusted Execution Environment Bringing Trust To The Internet of Things
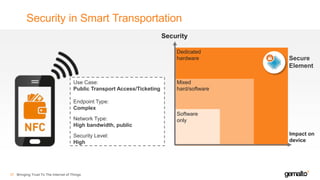
- 36. Security in Smart Transportation 37 Security Impact on device Software only Mixed hard/software Dedicated hardware Use Case: Public Transport Access/Ticketing Endpoint Type: Complex Network Type: High bandwidth, public Security Level: High Secure Element Bringing Trust To The Internet of Things
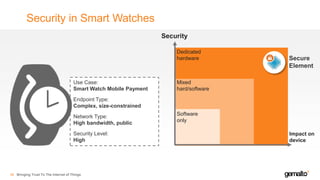
- 37. Security in Smart Watches 38 Security Impact on device Software only Mixed hard/software Dedicated hardware Use Case: Smart Watch Mobile Payment Endpoint Type: Complex, size-constrained Network Type: High bandwidth, public Security Level: High Secure Element Bringing Trust To The Internet of Things
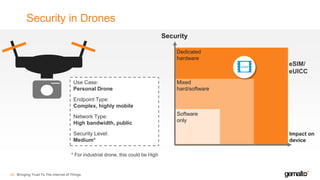
- 38. Security in Drones 39 Security Impact on device Software only Mixed hard/software Dedicated hardware Use Case: Personal Drone Endpoint Type: Complex, highly mobile Network Type: High bandwidth, public Security Level: Medium* eSIM/ eUICC * For industrial drone, this could be High Bringing Trust To The Internet of Things
- 39. Security for Smart Street Lamps 40 Security Impact on device Software only Mixed hard/software Dedicated hardware Use Case: Smart lighting – Street lamp Endpoint Type: Simple, resource constrained Network Type: Low bandwidth, private Security Level: Medium Use Case: Smart lighting – Gateway Endpoint Type: Complex, tamper-proof Network Type: High bandwidth, public Security Level: High LOGO LOGO IN BLACK LOGO COLOR VERSIONS LOGO ON BLACK Trusted Execution Environment Secure Element Bringing Trust To The Internet of Things
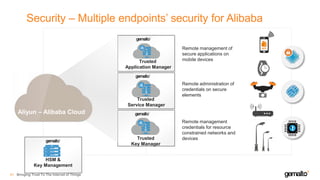
- 40. Security – Multiple endpoints’ security for Alibaba 41 Trusted Application Manager Trusted Service Manager Trusted Key Manager HSM & Key Management Remote management of secure applications on mobile devices Remote administration of credentials on secure elements Remote management credentials for resource constrained networks and devices LOGO LOGO IN BLACK LOGO COLOR VERSIONS LOGO ON BLACK Aliyun – Alibaba Cloud Bringing Trust To The Internet of Things
- 41. 3rd Foundation of Trust: Monetization BUILDING TRUST IN THE INTERNET OF THINGS Bringing Trust To The Internet of Things42
- 42. Digital Transformation is challenging, but crucial Bringing Trust To The Internet of Things43 “The notion that there is huge difference between the industrial world and the software world is no longer valid…. those days are over. In today’s world, everything is software” Jeffrey Immelt former CEO, General Electric
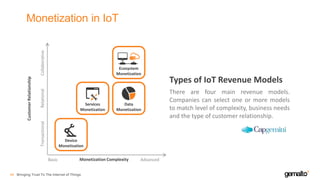
- 43. Monetization in IoT Bringing Trust To The Internet of Things44 Ecosystem Monetization Services Monetization Data Monetization Device Monetization TransactionalRelationalCollaborative CustomerRelationship Monetization ComplexityBasic Advanced Types of IoT Revenue Models There are four main revenue models. Companies can select one or more models to match level of complexity, business needs and the type of customer relationship.
- 44. Monetization in IoT – Device Bringing Trust To The Internet of Things45 How It Works A simple price premium, upfront, for having a connected product. Example: Factory Robot The robot manufacturer could charge a premium for a robot that can connect directly to the production system Ecosystem Monetization Services Monetization Data Monetization Device Monetization TransactionalRelationalCollaborative CustomerRelationship Monetization ComplexityBasic Advanced
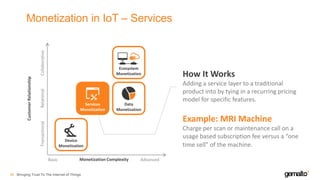
- 45. Monetization in IoT – Services Bringing Trust To The Internet of Things46 How It Works Adding a service layer to a traditional product into by tying in a recurring pricing model for specific features. Example: MRI Machine Charge per scan or maintenance call on a usage based subscription fee versus a “one time sell” of the machine. Monetization ComplexityBasic Advanced Ecosystem Monetization Services Monetization Data Monetization Device Monetization TransactionalRelationalCollaborative CustomerRelationship
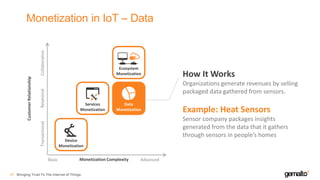
- 46. Monetization in IoT – Data Bringing Trust To The Internet of Things47 How It Works Organizations generate revenues by selling packaged data gathered from sensors. Example: Heat Sensors Sensor company packages insights generated from the data that it gathers through sensors in people’s homes Ecosystem Monetization Services Monetization Data Monetization Device Monetization TransactionalRelationalCollaborative CustomerRelationship Monetization ComplexityBasic Advanced
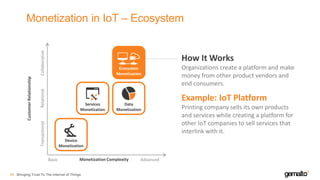
- 47. Monetization in IoT – Ecosystem Bringing Trust To The Internet of Things48 How It Works Organizations create a platform and make money from other product vendors and end consumers. Example: IoT Platform Printing company sells its own products and services while creating a platform for other IoT companies to sell services that interlink with it. Ecosystem Monetization Services Monetization Data Monetization Device Monetization TransactionalRelationalCollaborative CustomerRelationship Monetization ComplexityBasic Advanced
- 48. Monetization – Key Enablers Enable flexible monetization models Bringing Trust To The Internet of Things49 License and entitlement management Secure Software upgrades Device management IoT application development $ 1 $ $ 2 $ 3 $ 4 $ 5
- 49. IoT Monetization (Stryker) Bringing Trust To The Internet of Things50 Customer : Stryker Corps Industry : Medical Devices Country : United States CHALLENGE: Stryker wanted to offer customers more ways to pay, protect their IP and track the performance and use of their products GEMALTO SOLUTION: Transfer of medical device hardware to a services-based model to meet demands of hospitals and surgeons. 1. Expand business models – offering different pricing tiers and selling models 2. See how customers use appliances – to improve products and plan commercial activity 3. Integrate licensing and billing BUSINESS IMPACT
- 50. About Gemalto BUILDING TRUST IN THE INTERNET OF THINGS Bringing Trust To The Internet of Things51
- 51. We enable our clients to deliver trusted digital services Bringing Trust To The Internet of Things52 POWERING CONTACTLESS PAYMENT FROM CARDS, MOBILES AND WEARABLES ENCRYPTING DATA SO THAT IT’S UNUSABLE IN A BREACH CAPTURING BIOMETRIC DATA & VERIFYING IDENTITIES PROTECTING MOBILE BANKING & FUND TRANSFERS DELIVERING HARDWARE AND SOFTWARE TO CONNECT CARS AND OTHER DEVICES PROVIDING LICENSING SOLUTIONS TO PROTECT AND MONETIZE SOFTWARE
- 52. Serving six main markets Bringing Trust To The Internet of Things53 BANKING & PAYMENT ENTERPRISE SECURITY GOVERNMENT MOBILE IoT SOFTWARE MONETIZATION
- 53. We are the world leader in digital security WE’RE UNIQUE. WE’RE GLOBAL. WE’RE INNOVATIVE 54 Bringing Trust To The Internet of Things 3,000R&D ENGINEERS 88 NEW PATENTS FILED IN 2017 AEXLISTED ON EURONEXT AMSTERDAM & PARIS; IN DUTCH AEX STOCK INDEX 180+COUNTRIES WHERE OUR CLIENTS ARE BASED 15,000EMPLOYEES 121NATIONALITIES OF OUR EMPLOYEES €3bn2017 REVENUE +2bn END USERS BENEFIT FROM OUR SOLUTIONS
- 54. Gemalto bringing trust to IoT Bringing Trust To The Internet of Things55 Future-proof solutions Out-of-the-box connectivity Multiple form factors Quality of Service Subscription Management Secure the device | Secure the data | Secure the cloud Monetize Connect Secure Flexible revenue models Licensing and entitlement software IoT application development OTA upgrades
Editor's Notes
- …for most part
- https://hbr.org/cover-story/2017/05/drones-go-to-work
- http://www.mckinsey.com/industries/automotive-and-assembly/our-insights/ten-ways-autonomous-driving-could-redefine-the-automotive-world