Multicastingand multicast routing protocols
- 1. 1
- 2. Submitted To: Submitted By: Date: 2
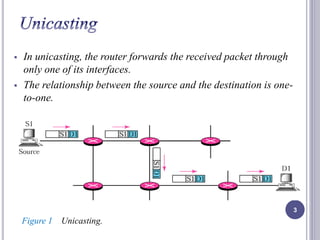
- 3. In unicasting, the router forwards the received packet through only one of its interfaces. The relationship between the source and the destination is one-to- one. Figure 1 Unicasting. 3
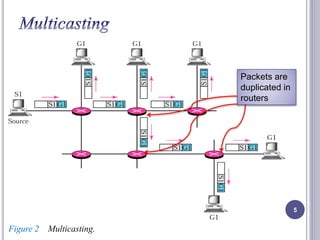
- 4. In multicast communication, there is one source and a group of destination. In multicasting, the router may forward the received packet through several of its interfaces. The source address is a unicast address, but destination address is a group address. 4
- 5. Packets are duplicated in routers Figure 2 Multicasting. 5
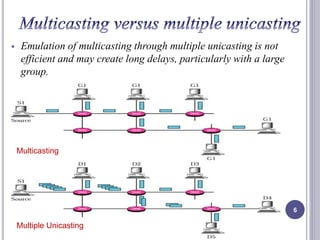
- 6. Emulation of multicasting through multiple unicasting is not efficient and may create long delays, particularly with a large group. 6 Multicasting Multiple Unicasting
- 7. One-to-many: Scheduled audio-video distribution (lectures, business TV) Push media (news headlines, weather updates, radio broadcast) File distribution and caching (web site content, file-based updates) Announcements (network time, session schedules) Monitoring (stock prices, telemetry) Many-to-many: Multimedia conferencing (audio/video, whiteboards) Synchronized resources (shared distributed databases) Concurrent processing (distributed parallel processing) Collaboration (shared document editing) Distance learning (one-to-many + feedback) Chat groups 7
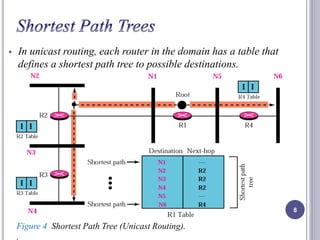
- 8. In unicast routing, each router in the domain has a table that defines a shortest path tree to possible destinations. 8 Figure 4 Shortest Path Tree (Unicast Routing). .
- 9. Basic requirements of multicast routing: Every group member should receive only one copy of the sent packet. Nonmembers must not receive a copy. A packet must not visit router more than once (no loops). Paths from the source to each destination must be optimal (shortest path). In multicast routing, each involved router needs to construct a shortest path tree for each group. Multicast trees (with source at the root and the group members being lives) are called spanning trees. The optimal tree is called shortest path spanning tree. 9
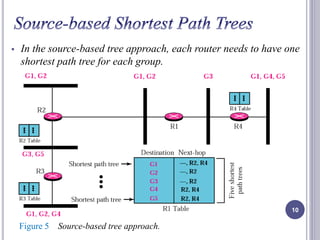
- 10. In the source-based tree approach, each router needs to have one shortest path tree for each group. 10 Figure 5 Source-based tree approach.
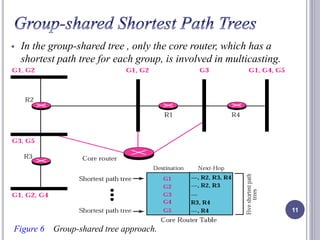
- 11. In the group-shared tree , only the core router, which has a shortest path tree for each group, is involved in multicasting. 11 Figure 6 Group-shared tree approach.
- 12. In multicast routing, Packets from remote sources will only be forwarded by IP routers onto a local network only if they know there is at least one recipient for that group on that network. Internet Group Management Protocol (IGMP) Used by end hosts to signal that they want to join a specific multicast group. Used by routers to discover what groups have interested member hosts on each network to which they are attached. Implemented directly over IP. 12
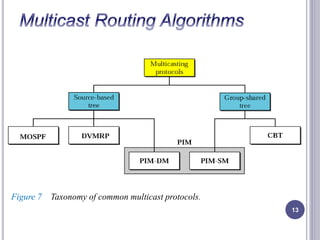
- 13. 13 Figure 7 Taxonomy of common multicast protocols.
- 14. Multicast link state routing is a direct extension of unicast routing, uses the source-based tree approach. Every router creates n (n is the number of groups) shortest path trees, using Dijkstra’s algorithm. Problem with this protocol is the time and space needed to create and store that much trees. MOSPF(Multicast Open Shortest Path First) It used multicast link state routing to create source-based trees. It calculates trees on demand. 14
- 15. Multicast distance vector routing uses source-based trees, but the router never actually makes a routing table. The trees are evanescent, that is after a packet is forwarded the table is destroyed. To accomplish the routing, multicast distance vector algorithm uses a process based on one of the four decision-making strategies. Flooding. Reverse Path Forwarding (RPF). Reverse Path Broadcasting (RPB). Reverse Path Multicasting (RPM). 15
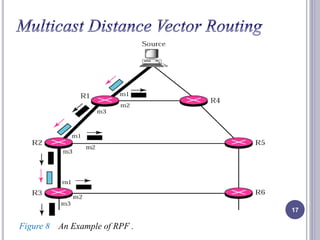
- 16. Flooding: In flooding, a router receives a packet and sends it out to every interface except the from which it was received. Flooding broadcasts packets not multicast. It creates loops in the systems. Reverse Path Forwarding (RPF): RPF eliminates the loops in the flooding process. In RPF , a router forwards only one copy of a packet that has traveled the shortest path from the source to the router. To checkout if the packet has come though its shortest path RPF uses unicast routing table. 16
- 17. 17 Figure 8 An Example of RPF .
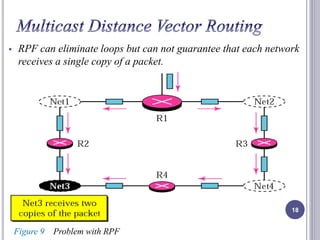
- 18. RPF can eliminate loops but can not guarantee that each network receives a single copy of a packet. 18 Figure 9 Problem with RPF
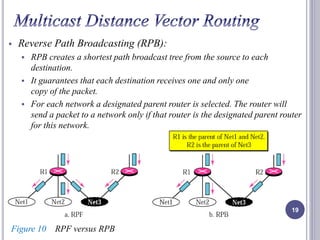
- 19. Reverse Path Broadcasting (RPB): RPB creates a shortest path broadcast tree from the source to each destination. It guarantees that each destination receives one and only one copy of the packet. For each network a designated parent router is selected. The router will send a packet to a network only if that router is the designated parent router for this network. 19 Figure 10 RPF versus RPB
- 20. Truncated RPB (TRPB): Both, RPF and RPB broadcast the packets. Consequently a network that doesn't contain the multicast group will receive the packet, and the second layer of each host in the network will decide whether to deliver or to drop the packet, based on the MAC address. Which is very inefficient. In TRPB a designated parent router can determine (via IGMP) whether members of a given multicast group are present on the router sub-network or not. If this sub-network is a leaf sub-network (it doesn't have any other router connected to it) the router will truncate the spanning tree. 20
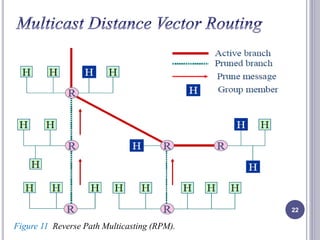
- 21. Reverse Path Multicasting (RPM): RPM adds pruning and grafting to RPB to create a multicast shortest path tree that supports dynamic membership changes. Pruning: The router sends a prune message to the upstream router ,so that the upstream router can stop sending multicast messages for this group though that interface. Grafting: The graft message forces the upstream router to resume sending the multicast messages. 21
- 22. 22 Figure 11 Reverse Path Multicasting (RPM).
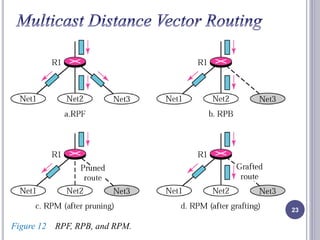
- 23. 23 Figure 12 RPF, RPB, and RPM.
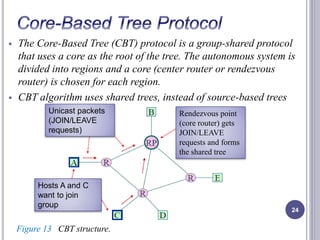
- 24. The Core-Based Tree (CBT) protocol is a group-shared protocol that uses a core as the root of the tree. The autonomous system is divided into regions and a core (center router or rendezvous router) is chosen for each region. CBT algorithm uses shared trees, instead of source-based trees 24 Rendezvous point (core router) gets JOIN/LEAVE requests and forms the shared tree Unicast packets (JOIN/LEAVE requests) Hosts A and C want to join group Figure 13 CBT structure.
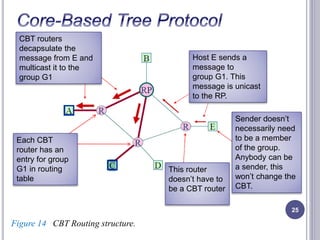
- 25. 25 Host E sends a message to group G1. This message is unicast to the RP. CBT routers decapsulate the message from E and multicast it to the group G1 Sender doesn’t necessarily need to be a member of the group. Anybody can be a sender, this won’t change the CBT. This router doesn’t have to be a CBT router Each CBT router has an entry for group G1 in routing table Figure 14 CBT Routing structure.
- 26. Advantages: Smaller routing tables (only one entry per group). Senders do not need to join a group to send messages. Simple and robust (only core router maintains connectivity). Disadvantages: Shared trees are not as optimal as source-based trees. Core routers can become bottlenecks. A single point of failure. 26
- 27. Protocol Independent Multicast (PIM) is the name given to two independent multicast routing protocols: Protocol Independent Multicast, Dense Mode (PIM-DM), and Protocol Independent Multicast, Sparse Mode (PIM-SM). Dense mode (PIM-DM): Uses source-based trees. PIM-DM uses RPF and pruning/grafting strategies to handle multicasting. It is independent from the underlying unicast protocol. Used in a dense multicast environment, such as a LAN environment. Sparse mode (PIM-SM): Uses shared trees. PIM-SM is used in a sparse multicast environment such as a WAN. PIM-SM is similar to CBT but uses a simpler procedure. 27
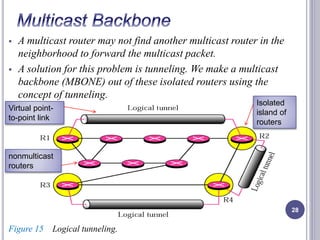
- 28. A multicast router may not find another multicast router in the neighborhood to forward the multicast packet. A solution for this problem is tunneling. We make a multicast backbone (MBONE) out of these isolated routers using the concept of tunneling. 28 Virtual point-to- point link Isolated island of routers nonmulticast routers Figure 15 Logical tunneling.
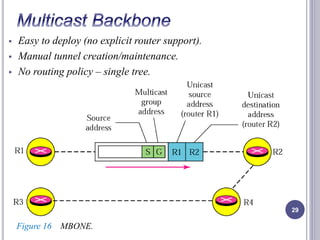
- 29. Easy to deploy (no explicit router support). Manual tunnel creation/maintenance. No routing policy – single tree. 29 Figure 16 MBONE.
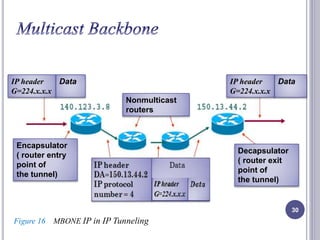
- 30. 30 IP header G=224.x.x.x Data Nonmulticast routers IP header G=224.x.x.x Data Encapsulator ( router entry point of the tunnel) Decapsulator ( router exit point of the tunnel) Figure 16 MBONE IP in IP Tunneling
- 31. 31