5G SA security: a comprehensive overview of threats, vulnerabilities and remediations
- 1. 5G SA security: a comprehensive overview of threats, vulnerabilities and remediations
- 2. Speakers Chief Technology Officer Dmitry Kurbatov – dmitry.kurbatov@positive-tech.com Since 2018 CTO at Positive Technologies. In charge of developing products and services for mobile network security analysis and visibility. Joined Positive Technologies in 2010 as an information security expert. Managing Director SEA Suen Kar Nyan – suen.kar@positive-tech.com Has 20+ years’ experience in Telecommunications Industry. Joined Positive Technologies early 2021 with previous roles in Mobile Operator, Network Equipment Vendors and BSS/OSS solution vendors
- 3. 18 years of experience in R&D for enterprise cybersecurity services and products 9 years of dedication to telecom cybersecurity 2 R&D centers in Europe 41countries where we have done projects 60 assessments per year are performed by our experts for telecom companies 5G cybersecurity leader Positive Technologies is a leading global provider of cybersecurity solutions for telecom & mobile operators, a pioneer in signaling security research and active contributor to industry standards. 1st Telecom Cybersecurity Vendor We are the only company in the world focused on end-to-end cybersecurity for mobile operators Company Profile Tier-1 Signaling Firewall 2018 - 2021
- 4. Analytics and Research Responsible disclosure — responsible attitude 2014 Signaling System 7 (SS7) security report 2014 Vulnerabilities of mobile Internet (GPRS) 2016 Primary security threats to SS7 cellular networks 2017 Threats to packet core security of 4G network 2017 Next-generation networks, next-level cybersecurity problems (Diameter vulnerabilities) 2018 SS7 Vulnerabilities and Attack Exposure Report 2018 Diameter Vulnerabilities Exposure Report 2019 5G Security Issues 2020 SS7 network security analysis report 2020 Security assessment of Diameter networks 2020 Threat vector: GTP. Vulnerabilities in LTE and 5G networks 2020 5G Standalone Core Security research
- 5. Our Daily Routine Source: Positive Technologies, cumulative data of public whitepapers 2015-2019
- 6. And Disappointing Conclusions Source: Positive Technologies, cumulative data of public whitepapers 2015-2019
- 7. Most of networks are currently running non-standalone 5G, which are based on previous-generation 4G LTE infrastructure Source: Positive Technologies, Threat vector: GTP. Vulnerabilities in LTE and 5G networks 2020
- 8. These non-standalone 5G networks are at risk of attacks because of long-standing vulnerabilities in the Diameter and GTP protocols Source: Positive Technologies, Threat vector: GTP. Vulnerabilities in LTE and 5G networks 2020
- 9. We are approached by many customers asking to test their 5G How to protect transition from 4G to 5G? Source: Ericsson Mobility Report 2020
- 10. But how will it look like after transition is over?
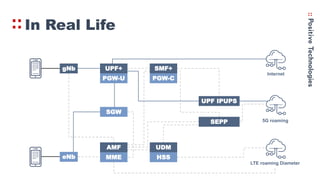
- 12. In Real Life gNb eNb UPF+ PGW-U SGW AMF MME SMF+ PGW-C UDM HSS UPF IPUPS SEPP Internet 5G roaming LTE roaming Diameter
- 13. Threat Vectors gNb eNb PGW-U SGW AMF MME SMF+ PGW-C UDM HSS SEPP Internet 5G roaming LTE roaming Diameter UPF IPUPS UPF+
- 14. gNb UPF SMF Internet Requesting a service Getting content How It Works SMF - Session Management Function UPF - User Plane Function gNb - Base station for radio access
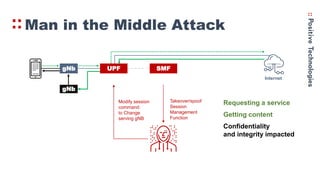
- 15. gNb UPF SMF Internet Man in the Middle Attack Takeover/spoof Session Management Function Modify session command: to Change serving gNB gNb Fake gNb is a simple host recording traffic
- 16. gNb UPF SMF Internet Takeover/spoof Session Management Function Modify session command: to Change serving gNB gNb Requesting a service Getting content Confidentiality and integrity impacted Man in the Middle Attack
- 17. MITM - Is It Critical? YES - This attack is remote YES - Goal of an attack is to steal data destined to you YES - It leaves no traces
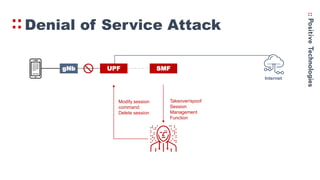
- 18. Denial of Service Attack gNb UPF SMF Internet Takeover/spoof Session Management Function Modify session command: Delete session UPF forgets about UE ?
- 19. Denial of Service Attack gNb UPF SMF Internet Takeover/spoof Session Management Function Modify session command: Delete session
- 20. DoS - Is It Critical? YES - In connected world DoS affects critical business functions YES - Consumers and businesses won't tolerate this YES - DoS can be used to masquerade another illegitimate activity
- 21. The story doesn't end there There are other vulnerabilities identified: Denial of service via PFCP Session Modification Request Registering a rouge NF via HTTP/2 Obtaining and deleting the NF profile Subscriber authentication vulnerabilities Subscriber profile disclosure via UDM PDU session creation
- 22. Why? Protocol in use — PFCP is pretty much like GTP, that proved to be vulnerable
- 23. Why? Protocol in use — PFCP is pretty much like GTP, that proved to be vulnerable Network exposure due to misconfiguration is a common problem
- 24. Why? Protocol in use — PFCP is pretty much like GTP, that proved to be vulnerable 5G SA will always work in parallel with LTE which expands attack surface Network exposure due to misconfiguration is a common problem
- 25. Let’s treat this as a warning 1-10-100 Rule Remediation costs more than prevention. The cost of fixing bad data is an order of magnitude greater than the cost of stopping at source. Failure costs more than remediation. The costs of remediation are insignificant compared to leaving bad data in place. 1 PREVENTION 10 REMEDIATION 100 FAILURE
- 26. Let’s treat this as a warning 1-10-100 Rule Remediation costs more than prevention. The cost of fixing bad data is an order of magnitude greater than the cost of stopping at source. Failure costs more than remediation. The costs of remediation are insignificant compared to leaving bad data in place. Our focus should be on prevention. 1 PREVENTION 10 REMEDIATION 100 FAILURE
- 27. MNO cybersecurity challenges The network core, signaling, and IT infrastructure are all becoming one. Security teams will need to analyze and tackle unprecedented challenges. While supporting the latest technologies, MNOs will still need to maintain backward compatibility (2G–5G). The difficulty of managing a sprawling infrastructure, plus constant changes, means vulnerabilities will inevitably appear. In the absence of action, network security will quickly deteriorate. The black market for digital services is growing. So is the skill level of attackers. Thwarting lone attackers and organized professionals takes constant monitoring of their changing tactics and tools. Defenders must be prepared to take effective measures. MNOs have to follow an ever-increasing list of regulatory requirements from industry (GSMA) and government (GDPR, ENISA, FCC). The increasing complexity of infrastructure is making security harder to manage. MNOs acutely need to automate enforcement of internal security policies, standards, and best practices. Companies are desperate for highly skilled security pros, but have a hard time finding them. Telecom systems are growing in number and complexity, meaning that automation of security management and outside experts are the only way to meet the need. Ongoing convergence. 2G–5G maintenance & IT silos Increasing compliance burden: national, sectoral, internal Cybersecurity skills shortage 1.8 million unfilled cybersecurity positions by 2022* Evolving criminal techniques MNOs lose $28 billion* annually due to fraud * Per CFCA Global Telecom Fraud Survey * Up 20% from 1.5 million in 2015, according to the Center for Cyber Safety and Education.
- 28. How PT helps Non-stop analysis of changes in product and service configurations. We can secure the full telecom stack: 2G–5G, signaling, virtualization, OSS/BSS, and more. Our products are the linchpin of 24x7 telecom security operations centers. Our experts at telecom lab work 24x7. All the expertise is incorporated into our services and constantly delivered in our products. Our services help to pinpoint non-compliance and develop short-term and long-term security improvement plans. With our products, MNOs can perform uninterrupted monitoring to check compliance with industry and government requirements and internal security policies. Our products solve many tasks automatically, while our virtual team of experts is always ready to help. Ongoing convergence. 2G–5G maintenance & IT silos Increasing compliance burden: national, sectoral, internal Cybersecurity skills shortage Evolving criminal techniques Automated checks, regular & on-demand Expert assessments & continuous protection Leading security products: up-to-date 24x7 Virtual team 24x7
- 29. Take a comprehensive security approach: positive-tech.com/products/ positive-tech.com/services/ Learn more about telecom security: positive-tech.com/articles/ New Webinar program Learn More from our experts with more at positive-tech.com contact@positive-tech.com @positive-tech Positive Technologies Positive Technologies in social media: