Security and compliance in Office 365 -Part 1
- 1. Security and Compliance in Office 365 – Part 1 ReinventingProductivity:Trust By Vignesh Ganesan – Technical Manager (SharePoint & Office 365)
- 2. Welcome
- 3. @sharepointnerd vignesh.ganesan.14 /Vignesh Ganesan vigganesan89@gmail.com https://vigneshsharepointthoughts.com Active Blogger on C Sharp Corner , European SharePoint Community, Collab 365 & HubFly Blogsite Organizer of SharePoint & Office 365 nerds meetup group - Bangalore Who’s this guy? Vignesh Ganesan Technical Manager-SharePoint & Office 365
- 4. This evening , we will discuss … Understanding the Threat Landscape Office 365 & Digital Transformation What’s a Modern Workplace? What’s the problem that we’re currently facing in a cloud first mobile first world ? Office 365 -Defense in depth multi-dimensional approach to customer environment Office 365 – Security and Compliance offerings CASB-Cloud Access Security Broker SIEM vs MDR vs CASB Recap Conclusion
- 5. Which one is the hacker?
- 8. Office 365 Helps Lead This Transformation
- 9. The Modern Workplace The Classic Workplace The Digital Transformation
- 10. What does a Modern Workplace look like ?
- 12. IN THE PAST, THE FIREWALL WAS THE SECURITY PERIMETER devices datausers apps On-premises / Private cloud
- 13. On-premises
- 14. THE PROBLEM The security organizations need must be integrated with the productivity tools user use Productivity Security On-premises OR It’s a delicate balance
- 15. Information Rights Management The market is segmented and confusing Mobile Device & Application Management Cloud Access Security Broker SIEM Data Loss Prevention User & Entity Behavioral Analytics Mobile Data Loss Prevention Threat Detection Identity governance Single- sign on Cloud Data Loss Prevention Conditional access Discovery Cloud visibility Secure collaboration Cloud anomaly detection Identity & Access Management The market is segmented and confusing
- 16. Identity & Access Management Mobile Device & Application Management Data Loss Prevention User & Entity Behavioral Analytics Cloud Access Security Broker Information Rights Management Protect at the front door Detect & remediate attacks Protect your data anywhere Cloud Access Security Broker Mobile Device & App Management Identity & Access Management User & Entity Behavioral Analytics Data Loss Prevention Information Protection
- 17. Mobile-first, cloud-first reality Mobile devices 72% of the U.S. workforce will be mobile by 2020, relying on devices other than their laptop to be productive. 72% 1/3 Shadow IT By 2022, a third of successful attacks experienced by enterprises will be on their shadow IT resources. Data breaches 63% of confirmed data breaches involved weak, default, or stolen passwords. 63%
- 18. Let’s get into the details now ….
- 19. DEFENSE IN DEPTH MULTI-DIMENSIONAL APPROACH TO CUSTOMER ENVIRONMENT Physical controls, video surveillance, access control Edge routers, firewalls, intrusion detection, vulnerability scanning Dual-factor authentication, intrusion detection, vulnerability scanning Access control and monitoring, anti-malware, patch and configuration management Secure engineering (SDL), access control and monitoring, anti-malware Account management, training and awareness, screening Threat and vulnerability management, security monitoring, and response, access control and monitoring, file/data integrity, encryption Facility Network perimeter Internal network Host Application Admin Dat a
- 20. Always Available Near your users Always Secured
- 22. PHYSICAL SECURITY Perimeter security Fire Suppression Multi-factor authentication Extensive monitoring Seismic bracing 24x7 onsite security staff Days of backup power Tens of thousands of servers
- 23. NETWORK Backend server and storage Front end server storage Firewall Layer of separation Edge router protection User
- 24. HOST/APPLICATION
- 25. ‘LOCK BOX’ ZERO ACCESS PRIVILEGE & ROLE BASED ACCESS Grants least privilege required to complete task. Verify eligibility by checking if 1. Background check completed 2. Fingerprinting completed 3. Security training completed Request Approve Request with reason Zero standing privileges Temporar y access granted Manager Just in time access High entropy passwords
- 26. Administrators Automatic account deletion Unique accounts Zero access privileges Security Development Cycle Annual training Background checks Screening
- 27. Data Customer data isolation Data encryption Operational best practices
- 28. CUSTOMER DATA ISOLATION Customer A Designed to support logical isolation of data that multiple customers store in same physical hardware. Intended or unintended mingling of data belonging to a different customer/tenant is prevented by design using Active Directory organizational units 28 Customer B
- 29. Data at Rest Disks encrypted with Bitlocker Encrypted shredded storage Data in-transit SSL/TLS Encryption Client to Server Server to Server Data center to Data center( for DR purposes ) AES 265 User Encryption
- 30. ENCRYPTED SHREDDED STORAGE A B C D Key Store A B C D Content DB A B C D E
- 31. Intelligence powered insights Reduce total cost of ownership Protection beyond Office 365 Areas of Focus
- 32. Security & Compliance Center Office 365 Cloud App Security Data Loss Prevention Office Message Encryption Exchange Online Protection Office 365 Advanced Threat Protection Office 365 Threat Intelligence Advanced Data Governance Advanced eDiscovery Compliance Manager Office 365 Security & Compliance Offerings * = new and updated capabilities
- 33. With A Focus on Addressing Cyber Threats 4 billion 39 seconds3 $6 trillion 1.37 billion With A Focus on Addressing Cyber Threats
- 36. Office 365 Security and Compliance Center Powerful for experts, and simple for generalists to use Scenario oriented workflows with cross-cutting policies spanning features Powerful content discovery across Office 365 workloads Proactive suggestions leveraging Microsoft Security Intelligence Graph NEW Reports with issue call out and recommended remediation's NEW Configuration improvement suggestions NEW More alerts and digest reports
- 37. Office 365 Advanced Threat Protection Office 365 Advanced Threat Protection secures your entire Office 365 environment from today’s most advanced and sophisticated threats
- 38. effectiveness latency 2014 AV Engines = 3rd Party Threat Protection = Office 365 ATP 100% 0% Safe Attachments Safe Links 20152016 Heuristic Clustering Reputation Blocking Zero-Hour Auto-purge Safe Links for Office Clients Office 365 Malicious Content Detection Linked Content Detonation slow fast Dynamic Email Delivery 2017 Type Blocking Document Preview Enhanced URL Detonation Phish ML Models Threat Intelligence Malware Phish Quarantines Intelligent Security Graph H2 ATP for files in SPO, ODB, and Teams Outlook Native Link Rendering Explorer Internal Safe Links WDAV+WDATP Endpoint Protection
- 39. Threat Intelligence Office 365 hosts one of the largest enterprise email services and productivity suites in the world, and manages content created on millions of devices. In the course of protecting this information, Microsoft has built a vast repository of threat intelligence data, and the systems needed to spot patterns that correspond to attack behaviors and suspicious activity. Threat Intelligence leverages the Microsoft Intelligent Security Graph, which analyzes billions of data points from Microsoft global data centers, Office clients, email, user authentications, signals from our Windows and Azure ecosystems and other incidents that impact the Office 365 ecosystem. NEW Threat Tracker NEW Threat Trend Insights NEW New real-time activity (user/content) intelligence
- 40. Data Loss Prevention Detect sensitive information across Office 365 Choose from 80+ sensitive information types – or create your own Customize policies, exclusions and actions Block accidental sharing and educate users View and monitor reports, alerts, events NEW Custom sensitive information types NEW HIPAA sensitive information types NEW Large dictionary support
- 41. Detect ProtectClassify Monitor C L O U DD E V I C E S O N P R E M I S E S Scan & detect sensitive data based on policy Classify data and apply labels based on sensitivity Apply protection actions, including encryption, access restrictions Reporting, alerts, remediation Azure Information Protection Comprehensive protection of sensitive data throughout the lifecycle – inside and outside the organization
- 42. Data governance challenges In the modern world of digital communication, the amount of electronic data grows exponentially, leading the company to do a daunting job of deciding what to keep and what not to keep – not to expose their organizations to unwanted risks without proactive data retention policies.
- 43. What is Data Governance ?in Office 365? Advanced data governance enables our customers to achieve organizational compliance by intelligently leveraging machine assisted insights to find, import, classify, set policy and take action on the data that is most important to them IT Administrator Compliance Officer Records Manager Information Worker Building Blocks of Office 365 Data Governance: Personas of Office 365 Data Governance:
- 44. Office 365 Data Governance framework Import • Intelligent import of on-premises Microsoft and 3rd party data Classification, Policy & Sensitive Types • Manual and auto- classification of content to apply right governance policies Retention, Archival & Disposition • System enforced lifecycle, disposition workflows and defensible deletion process Dashboard, Insights & Reporting • Monitoring, reports and intelligent trend identification and suggestions Audit, Supervision & Defensibility • Data investigations, forensics, automated audit alerts and notifications
- 45. Secure Score Insights into your security position One place to understand your security position and what features you have enabled. Guidance to increase your security level Learn what security features are available to reduce risk while helping you balance productivity and security.
- 46. Microsoft 365 provides an information protection strategy to help with the GDPR
- 47. Compliance Manager An intelligent score assessing your compliance posture against evolving regulations Recommended actions to improve your data protection capabilities Streamlined workflow and audit-ready reports Compliance Manager Preview is a dashboard that provides a summary of your data protection and compliance stature and recommendations to improve data protection and compliance. This is a recommendation, it is up to you to evaluate its effectiveness in your regulatory environment prior to implementation. Recommendations from Compliance Manager Preview should not be interpreted as a guarantee of compliance.
- 49. Employees want to work from mobile devices
- 50. Intune helps with that
- 51. Microsoft Enterprise Mobility + Security Apps Risk MICROSOFT INTUNE Make sure your devices are compliant and secure, while protecting data at the application level AZURE ACTIVE DIRECTORY Ensure only authorized users are granted access to personal data using risk-based conditional access MICROSOFT CLOUD APP SECURITY Gain deep visibility, strong controls and enhanced threat protection for data stored in cloud apps AZURE INFORMATION PROTECTION Classify, label, protect and audit data for persistent security throughout the complete data lifecycle MICROSOFT ADVANCED THREAT ANALYTICS Detect breaches before they cause damage by identifying abnormal behavior, known malicious attacks and security issues ! Device ! Access granted to data CONDITIONAL ACCESS Classify LabelAudit Protect ! ! Location
- 52. IF Privileged user? Credentials found in public? Accessing sensitive app? Unmanaged device? Malware detected? IP detected in Botnet? Impossible travel? Anonymous client? High Medium Low User risk 10TB per day THEN Require MFA Allow access Deny access Force password reset****** Limit access High Medium Low Session risk CONDITIONAL ACCESS
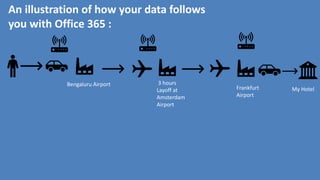
- 54. Bengaluru Airport 3 hours Layoff at Amsterdam Airport Frankfurt Airport My Hotel An illustration of how your data follows you with Office 365 :
- 55. CASB – Cloud Access Security Broker : A CASB helps IT departments monitor cloud service usage and implement centralized controls to ensure that cloud services are used securely. What does a CASB do? CASBs provide a solution to many of the security problems posed by the use of cloud services – both sanctioned and unsanctioned. They do this by interposing themselves between end users – whether they are on desktops on the corporate network or on mobile devices connecting using unknown networks – or by harnessing the power of the cloud provider's own API. Gartner suggests that CASBs should offer organizations: Visibility into cloud usage throughout the organization A way to ensure and prove compliance with all regulatory requirements A way to ensure that data is stored securely in the cloud A satisfactory level of threat protection to ensure that the security risk of using the cloud is acceptable
- 56. Six CASB vendors to consider
- 58. Microsoft Cloud App Security Discover and assess risks Control access in real time Detect threats Protect your information Identify cloud apps on your network, gain visibility into shadow IT, and get risk assessments and ongoing analytics. Manage and limit cloud app access based on conditions and session context, including user identity, device, and location. Identify high-risk usage and detect unusual behavior using Microsoft threat intelligence and research. Get granular control over data and use built-in or custom policies for data sharing and data loss prevention. Threat detection: Microsoft Intelligent Security Graph, Office ATP Information Protection: Office 365 & Azure Information Protection Identity: Azure AD and Conditional Access To your cloud appsExtend Microsoft security + more
- 59. A comprehensive, intelligent security solution that extends the visibility, real-time control, and security you have in your on-premises network to your cloud applications ControlDiscover Protect
- 60. SIEM –Security Incident Event Management
- 61. MDR-Managed Detection and Response
- 62. Customer Lockbox in Office 365
- 63. Microsoft Enterprise Mobility + Security Technology Benefit E3 E5 AzureActive Directory PremiumP1 Secure single sign-on to cloud and on-premises app MFA, conditional access, and advanced security reporting ● ● AzureActive Directory PremiumP2 Identity and access management with advanced protection for users and privileged identities ● MicrosoftIntune &ConfigMgr Mobile device, app, and PC management to protect company apps and data ● ● AzureInformationProtectionP1 Encryption for all files and storage locations Cloud-based file tracking ● ● AzureInformationProtectionP2 Intelligent classification and encryption for files shared inside and outside your organization ● MicrosoftCloudAppSecurity Enterprise-grade visibility, control, and protection for your cloud applications ● MicrosoftAdvancedThreat Analytics Protection from advanced targeted attacks leveraging user and entity behavioral analytics ● ● Identity and access management Unified Endpoint Management Information protection Threat protection EMS –Licensing Details
- 64. Recap: Understanding the Security Landscape Office 365 & Digital Transformation What’s a Modern Workplace? What’s the problem that we’re currently facing in a cloud first mobile first world ? Office 365 -Defense in depth multi-dimensional approach to customer environment Office 365 – Security and Compliance offerings CASB-Cloud Access Security Broker
- 65. RED TEAM VS BLUE TEAM
- 68. Conclusion: “You have to evaluate security & compliance not as an expense, but as a money saver. Sure, managing compliance takes resources, but it’s nowhere near as expensive as the costs associated with a breach” Tech Community :_ https://techcommunity.microsoft.com/t5/Security-Privacy-Compliance/ct-p/SecurityPrivacyCompliance Trust Center :_ https://products.office.com/en-in/business/office-365-trust-center-security Office 365 Trust Center :_ https://products.office.com/en-in/business/office-365-trust-center-welcome Top 10 security and privacy features in Office 365 :_ https://products.office.com/en-in/business/office-365-trust-center-top- 10-trust-tenets-cloud-security-and-privacy Red Team and Blue Team in Microsoft :_ https://channel9.msdn.com/Shows/Azure-Friday/Red-vs-Blue-Internal-security- penetration-testing-of-Microsoft-Azure
- 69. What’s coming next ? Part 2: Exchange Online Protection Office 365 Advanced Threat Protection Office 365 Threat Intelligence GDPR-Compliance Manager Tool Part 3: Data Loss Prevention Office Message Encryption Office 365 Customer Key Azure Information Protection Part4: Advanced Data Governance Advanced eDiscovery Microsoft Cloud App Security CASB , SIEM & MDR
- 70. Thankyou….
Editor's Notes
- 17
- Microsoft Worldwide Partner Conference 2016
- The Secure Score is a numerical summary of your security posture within Office 365 based on system configurations, user behaviour and other security related measurements; it is not an absolute measurement of how likely your system or data will be breached; rather, it represents the extent to which you have adopted security controls available in Office 365 which can help offset the risk of being breached. No online service is completely immune from security breaches; the Secure Score should not be interpreted as a guarantee against security breach in any manner.
- 51
- 58